Apple + Intego + Recommended + Security & Privacy
The Year in Mac Security 2016
Posted on
by
Jay Vrijenhoek

As we enter 2017, we all tend to look back on the good and the bad experienced during another trip around the sun. And for Mac users, there were plenty of bad things that happened in 2016 related to security threats, but also some good things that happened on the privacy front.
Some of the bad news was just the reality of being a computer user in today’s digital world, including new threats targeting Macs, malware infections, fresh vulnerabilities in third-party software, plug-in security issues, and data breaches. You can’t hold those against Apple. Some people get infected by malware, other people avoid it. On the contrary, there was some good news as Apple’s release of macOS Sierra implemented several new security features and plugged security holes.
What’s changed since our previous installment on the state of Mac security at the beginning of 2016? Truth be told, 2016 was a busy year. This article is a summary of the year’s security issues that affected Macs. Read on to discover the worst Mac threats in 2016, along with some of Apple’s more notable security improvements over the year.
Mac Malware

The year in malware was kicked off early in 2016 by the discovery of InstallCore, a fake Flash Player update that, once installed, used scare tactics to try and get money out of users to fix various system problems. Scareware is a very effective method of getting to a user’s wallet or potentially cause a malware infection. In fact, one of the most well known scareware campaigns targeting Macs is still Mac Defender, discovered by Intego nearly 5 years ago.
Shortly after InstallCore made its rounds, OS X malware identified as OceanLotus made the spotlight. Initially discovered in 2015, the Mac version of this malware did not get any stage time until February 2016. Using a fake Flash Player update and spread through watering holes and spear-phishing, the malware installed a LaunchAgent on infected systems and awaited instructions from a command-and-control server. At the time of testing, these servers appeared to be offline, most likely discontinued after the first report of OceanLotus by researchers at Qihoo 360.
In March, a new version of Hacking Team’s Remote Control System was uncovered. This not only showed that Hacking Team was still in business, despite their not so great year in 2015, but also that new malware delivery mechanisms were under development. Known as Crisis or Morcut, the malware did not pose a significant threat and was easily removed from an infected system. It was a reminder, however, that companies like these are still out there working hard to undermine the security of your Mac.
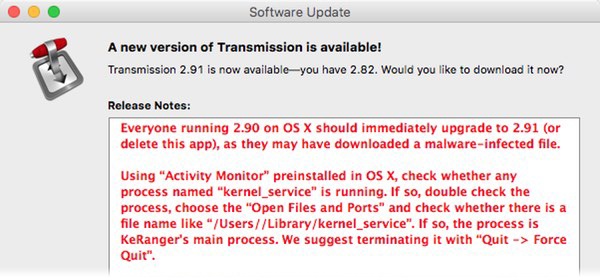
The myth that Macs can’t get viruses still persists even in 2016, but most people know by now it’s just that, a myth. Having said that, for many years Mac users could proudly boast that ransomware does not exist for Macs. However, in early March that all changed as the first ever ransomware for Mac, KeRanger, was discovered. Hackers planted an altered installer of the BitTorrent client Transmission that had the ransomware hidden inside of it. Once installed, the ransomware laid dormant for 3 days, but then it would awaken and start encrypting files and demand one bitcoin payment to get the encrypted data back.
Merely a month later, another InstallCore variant was found to use a fake Flash Player update to install Potentially Unwanted Programs (PUP’s), like MegaBackup, ZipCloud and MacKeeper.
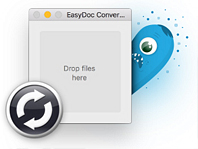 Then in July, a piece of malware named Eleanor, posing as a file converter application, installed a backdoor on infected systems that enabled an attacker to have full access to the operating system, webcam and more.
Then in July, a piece of malware named Eleanor, posing as a file converter application, installed a backdoor on infected systems that enabled an attacker to have full access to the operating system, webcam and more.
Adwind RAT, a remote access trojan was discovered in August. Though the infection risk was low, it was notable because it was written in Java, which made it cross-platform. Adwind RAT was spread via a spam email campaign.
The same month, BitTorrent client Transmission made the news again, this time spreading malware, named Keydnap, capable of stealing the contents of a Mac’s keychain. Once again, hackers replaced the legitimate download of the app with a modified one just like it did with the KeRanger ransomware in March. Transmission decided that twice was enough and moved their website and files to GitHub to prevent future attacks on their server.
In September, Intego learned of a potential new Adwind RAT being spread via email. Opening a backdoor on infected systems, this version posed no immediate threat. It has not been seen since and clearing an infected system was an affected Mac user needed to do. Unfortunately, however, we may not have seen the last of Adwind.
Also in September, Intego learned of another trojan posing as a fake Flash Player installer. This malware variant shared similarities with a previously found iWorm trojan, and while this may have been a proof-of-concept (PoC) not causing any grief at the time, Intego added it to its VirusBarrier anti-virus definitions to protect its customers from any possible future encounters.
A cross-platform backdoor, called Mokes, for OS X that can take screenshots of an infected Mac as well as steal Office documents, record keystrokes and capture audio and video was discovered as well. As if September was not already interesting enough, a trojan called Komplex was discovered to spread via spear phishing. Posing as a fake Russian aerospace program information PDF attachment, once opened, Komplex installs files and was able to download, execute or delete files. Luckily, the command-and-control server it contacted did not instruct the trojan to do anything after installing itself.
In October, Intego’s malware researchers discovered a new fake Flash Player installer, identified as SilverInstaller, which behaved differently from other installers of its kind. SilverInstaller appeared to use new techniques to avoid detection. Intego later uncovered more details and fount the malware was more sophisticated than previously thought, as it was attempting to avoid detection by malware researches by looking for common analysis tools and techniques.
Didn’t Apple Fix All This with Gatekeeper?
What does all of the Mac malware from 2016 have in common? It’s all signed by valid developer ID’s. This is done to circumvent Gatekeeper, one of macOS’s built-in defense layers.
According to Apple, “Gatekeeper helps protect your Mac from apps that could adversely affect it,” and “The Developer ID allows Gatekeeper to block apps created by malware developers and verify that apps haven’t been tampered with since they were signed.”
 With malware being signed by a Developer ID, Gatekeeper will not block it from running. Instead, it will give the default warning that the app was downloaded from the Internet and to proceed with caution, a warning Mac users are now so used to it is often given barely a glance. Gatekeeper only becomes useful if malware is discovered, reported and the offending Developer ID is blocked. This will cause the application to be blocked and unable to install. The problem with this is that it only works for new installations after the Developer ID is blocked, and so anyone that already has the malicious application installed is not protected by this as the application will continue to run.
With malware being signed by a Developer ID, Gatekeeper will not block it from running. Instead, it will give the default warning that the app was downloaded from the Internet and to proceed with caution, a warning Mac users are now so used to it is often given barely a glance. Gatekeeper only becomes useful if malware is discovered, reported and the offending Developer ID is blocked. This will cause the application to be blocked and unable to install. The problem with this is that it only works for new installations after the Developer ID is blocked, and so anyone that already has the malicious application installed is not protected by this as the application will continue to run.
Because it takes time for a malicious application to be reported and for Apple to revoke the Developer ID, signing malware with such an ID typically guarantees infected users for days (or even weeks) before the ID is blocked. This makes Gatekeeper a good idea but not something to rely on as your only layer of protection, because there are easy ways around it. Of course, Gatekeeper is just one layer, it works hand in hand with XProtect that is designed to flag and block known malware and vulnerable plug-in versions.
XProtect received several updates in 2016. For El Capitan and Sierra, there were at least 12 updates, and they included some of the following:
- Adobe Flash Player, which is frequently patched and updated to fix serious vulnerabilities, had older versions blocked 7 times
- 13 pieces of malware were added to the block list
- 11 Safari extensions were blocked
To put this in contrast, Intego added over 5,000 malware signatures to VirusBarrier.
Since we’re talking about Apple, let’s see what they did to make their operating systems more secure in 2016.
macOS Vulnerabilities
OS X El Capitan, at version 10.11.2 going into 2016, received four point updates and three security updates after macOS Sierra was released. Addressing a combined 215 CVE’s in 2016. macOS 10.12 Sierra, released in September and updated twice since, addressed 158 CVE’s. OS X 10.10 Yosemite received seven security updates in 2016, patching 62 vulnerabilities, and OS X 10.9 Mavericks received four security updates, patching 53 vulnerabilities.
With the release of macOS Sierra, support for Mavericks was dropped, causing its users to miss out on the security update that specifically patched the vulnerabilities, nicknamed Trident, exploited by the Pegasus spyware. Even though the security update was released on September 1 and macOS Sierra was not released until September 20, Apple chose not to offer the full patch to its Mavericks users. While a Safari update that was available for Mavericks addressed part of the vulnerabilities, it did not patch all of it.
Speaking of software vulnerabilities, Apple updated Safari eight times and patched 89 vulnerabilities, bringing us from version 9.0.3 to 10.0.2 .
macOS Sierra itself implemented several new security features and enhancements, such as the Gatekeeper option to allow unsigned applications to open from anywhere, Path Randomization, the removal of the weak RC4 cipher suite and Auto Unlock, among other Sierra security and privacy features.
Along with macOS Sierra came Safari 10.0. Its biggest security feature was the disabling of plug-ins by default. This meant that Flash Player, Silverlight, Java and other plug-ins need to be manually enabled first before they work. As vulnerabilities in plug-ins are often exploited, this was a big security step in the right direction.
Plug-in Security Issues
Something that makes any system administrator, tech support or security researcher cringe is the mention of Adobe Flash Player. Often updated but never secure, it is typically a security risk to have it installed. Even with browsers now disabling Flash Player and other plug-ins by default, having it installed means you are more likely to fall for fake Flash Player update scams. If you don’t have Flash Player installed, you’ll know that any site prompting you for an update is bogus.
![]() Flash Player was updated several times over the year year and, at the time of writing this article, racked up over 260 vulnerability entries with the majority related to code execution. The amount of CVE’s is not necessarily a bad thing. Apple, for example, had 215 CVE’s listed for OS X at the time of writing and 161 CVE’s for iOS. What should be watched is the severity of these vulnerabilities; when it comes to severity, Flash Player has far more than OS X or iOS.
Flash Player was updated several times over the year year and, at the time of writing this article, racked up over 260 vulnerability entries with the majority related to code execution. The amount of CVE’s is not necessarily a bad thing. Apple, for example, had 215 CVE’s listed for OS X at the time of writing and 161 CVE’s for iOS. What should be watched is the severity of these vulnerabilities; when it comes to severity, Flash Player has far more than OS X or iOS.
On the severity of vulnerabilities, the worst is known as a “0-day,” which is a vulnerability that is being actively exploited by bad guys and that has no fix available. Flash Player had six of those by my count, which is pretty significant. It had them in 2015, 2014, 2013 and most likely before that, too. There is no reason to think this will get any better in 2017, so the recommendation to uninstall Flash Player and never look back remains a good one.
While Flash Player grabs the majority of headlines due to security flaws, other plug-ins were not without their issues. Microsoft started the year by patching a Silverlight 0-day vulnerability that was discovered in 2015 as a result of the Hacking Team leaks. Silverlight doesn’t make the news often, but it is a favorite among exploit kits, just like Flash Player, Acrobat Reader and Java.
Adobe discontinued Adobe Reader X (version 10.x) over a year ago, meaning, “Adobe will no longer provide any updates or address any existing bugs or security issues in the software.” Switching to Acrobat Reader DC was recommended, but not many people got the memo as Adobe Reader X is still very common on a lot of systems, which makes it a very attractive target.
Third-Party Software and Macs
![]() We already mentioned some of the third-party software woes experienced during 2016, such as EasyDoc Converter (distributing Eleanor) and Transmission (distributing KeRanger). Other well known software made headlines, too. Skype for Mac was found to have a backdoor that had been around for at least 5 years. Those are the kind of vulnerabilities that make excellent 0-days, and this may very well have been one without anyone knowing. Skype addressed the vulnerability, and so the good news is that the latest version of Skype is backdoor free.
We already mentioned some of the third-party software woes experienced during 2016, such as EasyDoc Converter (distributing Eleanor) and Transmission (distributing KeRanger). Other well known software made headlines, too. Skype for Mac was found to have a backdoor that had been around for at least 5 years. Those are the kind of vulnerabilities that make excellent 0-days, and this may very well have been one without anyone knowing. Skype addressed the vulnerability, and so the good news is that the latest version of Skype is backdoor free.
Microsoft’s Office 2011 and 2016 also received several security updates, patching remote code execution and memory corruption vulnerabilities.
Whether it’s the operating system, a plug-in or third-party software, security bugs and vulnerabilities will always be there. After all, code is written by humans and humans make mistakes. Therefore, it’s imperative to keep your software current with the latest available updates as this is the biggest step you can take to improve your security.
Data Breaches
From apparently harmless attacks, like those done by hacking group OurMine, to more serious players like Fancy Bear, and to the biggest breach of all time at Yahoo, 2016 was an interesting year.
OurMine, a hacking group that breaks into accounts and leaves a message, stating, “Don’t worry we are just testing your security,” managed to compromise the Quora account of Google CEO, Sundar Pichai, and the Twitter account of FaceBook CEO, Mark Zucherberg. Spotify founder, Daniel Ek, Amazon CTO, Werner Vogels, and actor Channing Tatum were some of their other targets.
 Russian hacking group Fancy Bear broke into the World Anti-Doping Agency (WADA) database and released medical records of U.S. athletes. You may recall the name Fancy Bear as their group was found to be responsible for the Komplex trojan mentioned earlier. This hack not only showed that the Olympics may as well show big “made possible by banned substances” banners, but also pointed out the flawed therapeutic use exemption (TUE) system. Oh and, of course, it upset a lot of athletes.
Russian hacking group Fancy Bear broke into the World Anti-Doping Agency (WADA) database and released medical records of U.S. athletes. You may recall the name Fancy Bear as their group was found to be responsible for the Komplex trojan mentioned earlier. This hack not only showed that the Olympics may as well show big “made possible by banned substances” banners, but also pointed out the flawed therapeutic use exemption (TUE) system. Oh and, of course, it upset a lot of athletes.
In December, LinkedIn’s Lynda.com was hacked by an “unauthorized third party” that accessed a database that included some learning data. Contact information and which courses were viewed for 55,000 accounts were listed as the only compromised data.
Moving on to some larger scale hacks, the bitcoin exchange BitFinex was hacked by unknown attackers and their digital wallet was made $70 million lighter. The incident is still being investigated.
Point of Sale (PoS) systems were again a popular target this year. A Russian organized cybercrime group breached hundreds of computer systems at software giant Oracle Corp, compromising a customer support portal for companies using Oracle’s MICROS PoS credit card payment systems. MICROS, a huge vendor in the global sale of PoS systems, is used at over 330,000 cash registers world wide. The scale of the hack is still unknown, as is the time it first started. HEI Hotels and Resorts found twenty of its hotels, including Marriot, Hyatt and Intercontinental, infected with malware on their payment systems. These systems were used at restaurants, bars, spas and shops. Hackers may have gotten away with customer names, account numbers, credit card expiration dates and verification codes.
Hacked email accounts were a common theme in 2016. The biggest breach was reserved for Yahoo. After revealing a 2014 hack affected more than 500 million user accounts, they found an older breach in 2013 compromised over 1 billion user accounts. While technically a breach from three years ago, it was not discovered until recently, which means the hackers may have had access to all of the accounts for years.
Privacy Issues
The biggest story this year was Apple’s defense of security and privacy, when it refused to cooperate with the FBI’s request to build a custom iOS version that circumvents several important security features. In a message to its customers, Apple wrote:
[T]he U.S. government has asked us for something we simply do not have, and something we consider too dangerous to create. They have asked us to build a backdoor to the iPhone. […] In the wrong hands, this software — which does not exist today — would have the potential to unlock any iPhone in someone’s physical possession. […] We are challenging the FBI’s demands with the deepest respect for American democracy and a love of our country. We believe it would be in the best interest of everyone to step back and consider the implications. While we believe the FBI’s intentions are good, it would be wrong for the government to force us to build a backdoor into our products. And ultimately, we fear that this demand would undermine the very freedoms and liberty our government is meant to protect.
The issue caused mix reactions.
For instance, at a time when many supported Apple’s decision, then-Republican presidential candidate Donald Trump called for a boycott of Apple until they helped the FBI unlock the iPhone belonging to a terrorist. His comments came as the U.S. Department of Justice filed a motion seeking to force Apple to comply with a judge’s order for the company to unlock the iPhone, igniting a showdown between the Obama administration and Silicon Valley over security and privacy. As the story goes, the FBI found a different way to get the information they were after, without Apple’s help, and stopped pressuring Apple. A big win for the privacy and security of Apple customers.
 Yahoo made headlines several times in 2016, and the previously mentioned data breaches were just a part of their news coverage. In October, a story broke revealing Yahoo had been scanning customer emails on behest of the federal government. This was not mentioned as a breach, because Yahoo built and implemented the scanning software themselves. Not even Yahoo’s own security team knew about this until after the program went live and made them believe they got hacked. Reportedly this course of events caused Yahoo’s own cyber security chief Stamos to quit and move to FaceBook a month later.
Yahoo made headlines several times in 2016, and the previously mentioned data breaches were just a part of their news coverage. In October, a story broke revealing Yahoo had been scanning customer emails on behest of the federal government. This was not mentioned as a breach, because Yahoo built and implemented the scanning software themselves. Not even Yahoo’s own security team knew about this until after the program went live and made them believe they got hacked. Reportedly this course of events caused Yahoo’s own cyber security chief Stamos to quit and move to FaceBook a month later.
In April, WhatsApp finished migrating all of its users over to Open Whisper Systems’ standard-setting encryption. With a billion people using WhatsApp, this suddenly caused a fair percentage of the world’s population to start messaging securely, whether they knew it or not.
This includes chats, group chats, attachments, voice notes, and voice calls.
This makes WhatsApp a solid messenger that is both secure and private regardless of it being owned by Facebook, which is not exactly known for being privacy conscious.
DDoS Attacks
From attacks that crippled parts of the internet to attacks with a specific target, Distributed Denial of Service (DDoS) has a name. Say hello to the Mirai botnet.
Mirai, malware that hijacks IoT devices, is not the largest botnet out there, but nevertheless it has been responsible for the largest DDoS attack recorded. In September, it was targeted at the website of security journalist Brian Krebs and was recorded at 620 Gbps of traffic per second. The attack caused Krebs’ site to go offline for a while as Akamai, who successfully mitigated the attack, asked Krebs to seek protection elsewhere. A few days later, 1.1Tbps of traffic was directed at French-based hosting provider OVH via multiple simultaneous attacks, and in October the source code for Mirai was released online, making it available to anyone that wants to use it.
Just a few days later, a whopping 1.2Tbps directed at Dyn brought down much of America’s Internet. Dyn, a company that controls much of the Internet’s domain name system (DNS) infrastructure, was under attack for most of the day. This resulted in the websites of Twitter, the Guardian, Netflix, Reddit, CNN and many others.
Botnets are nothing new, but Mirai is mostly made up of IoT devices. The IoT is growing at an enormous pace, giving malware, like Mirai, more ammunition every month and every year.
Manufacturers need to step up and secure the IoT devices that they supply, and/or release updated firmware to devices already out there. This would greatly reduce the efficacy of botnets like Mirai. Users who purchase IoT devices must learn that “plug and play,” while easy, often brings security risks. Change the default name/password on any new devices, and if that’s not possible, return the device and purchase one that is better secured.
Encryption by Default
As mentioned earlier, WhatsApp rolling out end-to-end encryption by default and Apple fighting off the FBI’s demand for a weakened iOS, were important moments this year. Constant reminders in the news about hacks, breaches and surveillance along with industry and government calls to use HTTPS sped up the adoption of encryption. The Internet Security Research Group (ISRG)’s Let’s Encrypt helped secure over 21 million websites, most of which never had certificates before.
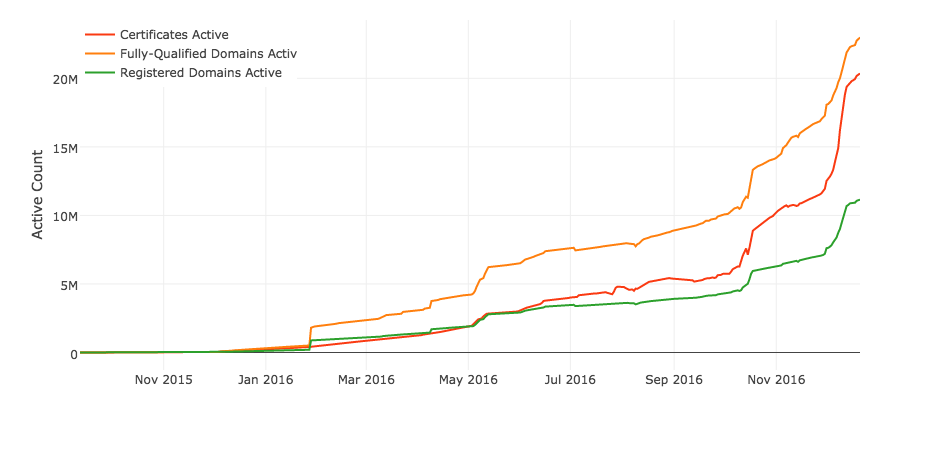
Wordpress.org, OVH, Shopify, Tumblr and Squarespace are some of the many hosting providers that chose to make HTTPS the default. From metrics collected by Mozilla, close to 50% of all page loads were done over HTTPS. Thus, 2016 was a good year for encryption!
Encrypting content matters, regardless of the size or popularity of a site or service. Of course, Intego protects its website, blog and Mac anti-virus software update streams with encryption to ensure your privacy and security when using our services.
Summary
As you have seen, 2016 was a very eventful year for Mac malware and security issues. Not only was the first Mac ransomware discovered during the year, hidden inside an altered installer of the BitTorrent client Transmission, but the persistence of fake Flash Player installers plagued Mac users; furthermore, many operating system and third-party software vulnerabilities were found that compromised the security of Macs.
A great number of these operating system flaws pave the way for unseen malware attacks. Some of them are such that merely visiting a booby-trapped webpage can compromise a Mac. This underscores the importance of security software that protects not only from malware but also from web threats and many other kinds of menaces that target Macs. It also highlights the need to keep software up-to-date.
Both for macOS and for third-party software, Mac users should make sure to have the latest versions of software at all times, because some programs—such as Java and Adobe Flash Player—are easy to attack with known exploits circulating in the wild.
As always, Intego is at the forefront in protecting Mac users from the dangers of the Internet. With its Malware Research Team continuously monitoring the threats to Mac users, Intego Mac Premium Bundle proves, yet again, to be the best security with layers of protection against malware and network threats. Malware writers have Mac users in their crosshairs, and Intego helps protect Macs from all types of security threats.