Recommended + Security & Privacy + Security News
macOS Sierra 10.12: Vulnerability Fixes and Security Enhancements
Posted on
by
Jay Vrijenhoek

This week Apple released macOS Sierra to the public and, apart from some nice new features, it includes fixes for 65 security vulnerabilities and some tweaks to the operating system itself to improve security as well. A separate Safari 10 update was also released, which fixes 21 vulnerabilities, and is included with macOS Sierra 10.12.
As an added bonus, the list of vulnerability fixes in iOS 10 was amended to show 28 additional vulnerabilities that were addressed in the release. Apple did not release these details until Sierra was released, likely because both operating systems shared the same flaws. Publishing details on the flaws that were addressed in iOS 10 would have given those with malicious intent a nice roadmap of what to exploit in OS X.
Vulnerabilities Patched in macOS Sierra
- apache_mod_php – Allows Apache to interpret PFP files. This module received 16 fixes that were addressed by updating the PHP version to 5.6.24 to avoid arbitrary code execution.
- Application Firewall – The firewall in your System Preferences > Security & Privacy pane. A local user may have been able to cause a denial of service so this was addressed to make sure it won’t happen again.
- ATS – Stands for Apple Type Services which handles fonts on your Mac. Processing a maliciously crafted font file may have lead to arbitrary code execution. This was addressed by improving memory handling.
- Bluetooth – A memory corruption was addressed to prevent an application from executing arbitrary code with kernel privileges.
- CoreCrypto – Provides implementations of low level cryptographic primitives. Vulnerable code was removed to avoid applications being able to execute arbitrary code.
- CoreDisplay – A user with screen sharing access may have been able to view another user’s screen. Fixed by the improvement of session tracking.
- Date & Time Pref Pane – A malicious application may have been able to determine a user’s current location. Fixed by the improvement of validation.
There are many more entries on the list, but the trend is arbitrary code execution. In plain english, someone can run code on your Mac and give it commands to do something it should not be doing. Something you don’t want. This is why installing Mac OS upgrades and Security Updates is always a good idea. It’s nice of Apple to list all the vulnerabilities that were addressed, but this also, as mentioned earlier, gives someone with malicious intent a good idea of what to exploit on systems that are not updated.
For those not familiar with reading Apple Security bulletins, the addressed vulnerabilities mention “Available for: OS X El Capitan v10.11.6,” but this means the vulnerability was found in OS X El Capitan and fixed only if you update to macOS Sierra. The wording can make someone believe the fix applies to El Capitan as well. El Capitan itself did not receive any security updates, but will likely see some released alongside future Sierra updates (10.12.1, 10.12.2, and so forth) to cover some critical vulnerabilities.
Security was also implemented in the form of new features.
New Security Features in macOS Sierra
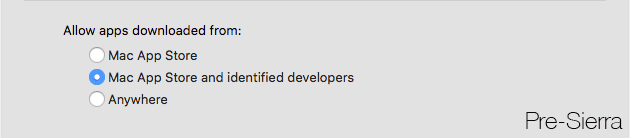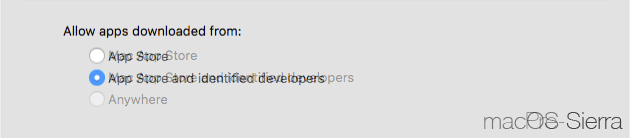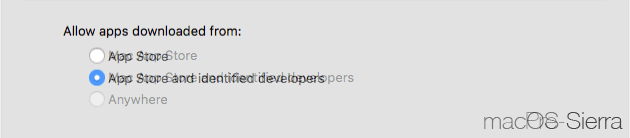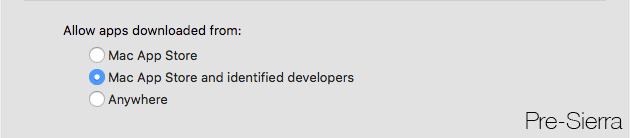
Gatekeeper
The option to allow unsigned applications has been removed from the System Preferences > Security & Privacy pane.
You can still get unsigned applications to open via other means, but this prevents unskilled users from accidentally (or intentionally, without realizing the possible consequences) set the “Anywhere” option.
Another new Gatekeeper feature is called Path Randomization. This feature is designed to prevent repackaging attacks or “dynamic library hijacks” (PDF), where a legit app can be tricked into loading malicious contents. Now an application is taken from its current location, placed in a random location on your Mac’s hard drive and executed from there. This way the application does not have access to potentially hidden and malicious resources that came in the container. dmg, zip and ISO files are good examples of such a container.
Differential Privacy
As the name implies, this is more a privacy feature than a security feature, but a nice one nevertheless. Basically this allows Apple to collect usage patterns that can help them improve products and services, without compromising individual privacy. This is done using machine learning and artificial intelligence on your Mac, so only anonymized usage statistics are sent to Apple. Helping Apple to improve their products will ultimately benefit us as users and now we get to do it while keeping our privacy.
Auto Unlock
Your Mac will unlock when you walk up to it and it will lock when you walk away — simply by wearing your Apple Watch.
Weak cipher suite removed
The RC4 cipher is a stream that’s used to negotiate an encryption between your browser and the website you visit. Several exploits are known that make the RC4 cipher insecure and no longer trusted, so Apple dropped it. The same goes for SSLv3, a cryptographic protocol that was found to be vulnerable.
Safari 10
Apple Pay on the web
Use your TouchID enabled iOS device or Apple Watch to pay online. With Apple Pay, your credit card number is not being stored or shared and transaction information is not kept — overall a faster and more secure process. For more information about Apple Pay, have a look here.
Web plugins disabled by default
Adobe Flash Player, Java and other plug-ins that can be exploited to load malicious content on your Mac are now disabled by default, but can be clicked by the user to activate.
Intego’s Mac security software has been updated to be fully compatible with macOS Sierra as well.