Malware + Recommended + Security News
Fake Flash Player Update Infects Macs with Scareware [Updated]
Posted on
by
Graham Cluley
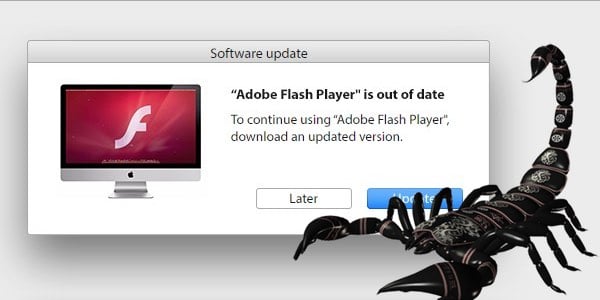
Anyone who has been using computers for any length of time should (hopefully) be aware of the endless ritual of updating Adobe Flash against security vulnerabilities. Even if you don’t run Flash on your computer, you’ve surely seen the many headlines in the tech media over the years of the importance of keeping Adobe Flash (and its Acrobat PDF Reader stablemate) updated to protect against malicious attack.
So, what better way to trick someone into having their computer infected than by disguising it as an actual Adobe Flash update?
That’s precisely what criminals are doing now, in their attempts to infect Apple Mac users with scareware.
The first sign you will see that criminals are interested in infecting your Mac OS X computer is if you see a pop-up like this appear while you are browsing the web:
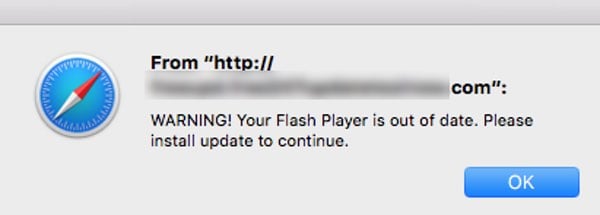
Following the phoney alert’s advice to download an Adobe Flash update from a site you have never heard of is, of course, unwise.
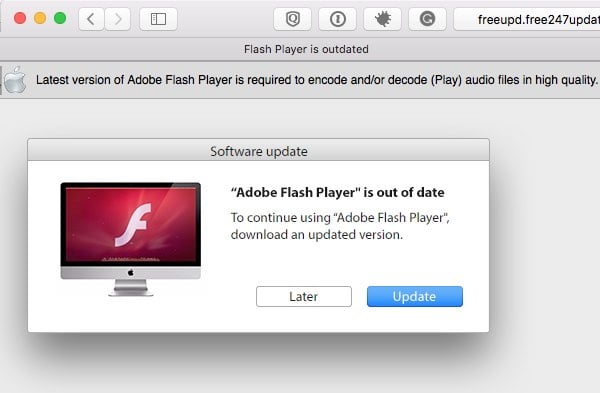
The beauty of this approach, from the criminals’ point of view, is that the attack doesn’t rely upon any software vulnerability or exploit. Instead, social engineering is being used to trick the unsuspecting user into unwittingly downloading and running a bogus version of Adobe Flash — designed to infect their computer with scareware.
Johannes Ullrich of the SANS Institute’s Internet Storm Center first reported on the threat, noting that the scareware’s installer was digitally signed with a valid Apple developer certificate, issued to one Maksim Noskov.
The fact that the scareware installer was signed with an Apple developer certificate is important, because it allows the malware to bypass a key defence that is built into modern versions of OS X.
In an attempt to prevent malicious code from infecting computers running OS X, by default the operating system only allows you to run programs that have been downloaded from the official App Store or that have come from “identified developers.”
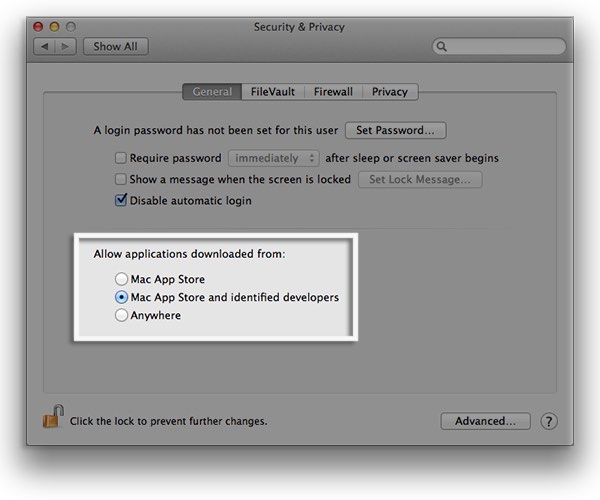
By using a valid Apple developer certificate, the scareware dupes OS X into believing that it can be trusted and the code is allowed to execute.
As we have previously reported, there are ways to exploit vulnerabilities in OS X Gatekeeper to allow malicious code to slide past Apple’s defences — but the easiest way is seemingly simple to sign your code with a valid developer certificate.
Intego VirusBarrier with current virus definitions protects Mac users against this malware, detected as OSX/InstallMiez (and it is probable that some other varients can be picked up as OSX/InstallCore). In all, Intego’s research team say that they have found 492 occurrences of malware using the identifier and developer ID, dating back to at least April 2015.
The installers used in the attacks, however, are prone to change — meaning that at any time what they offer to install may be different. Commonly, however, they have been seen offering a variety of products including freeware, shareware and open source tools.
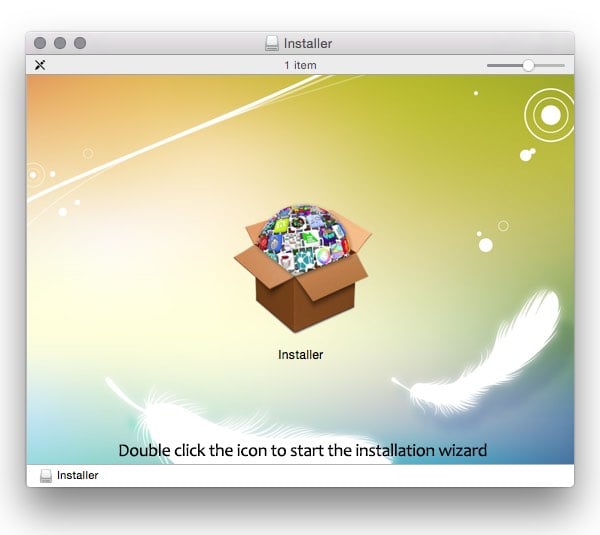
With a click or two, the installation has begun.
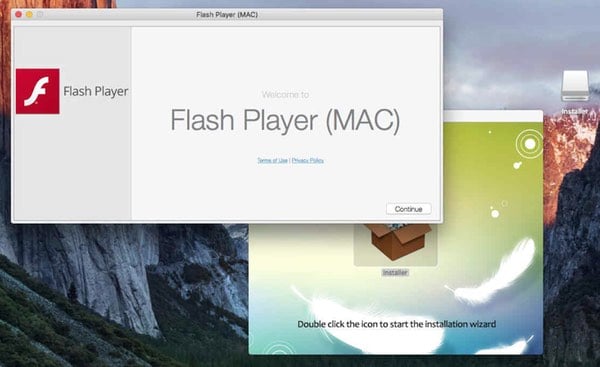
It may surprise some to hear that in this particular attack, a genuine version of Adobe Flash is downloaded in the background onto Macs alongside the malware — presumably in an attempt to appear more legitimate to any user who begins to suspect something fishy is afoot.
After the malicious installer is run, the user is prompted to continue with the installation of the legitimate version of Flash.
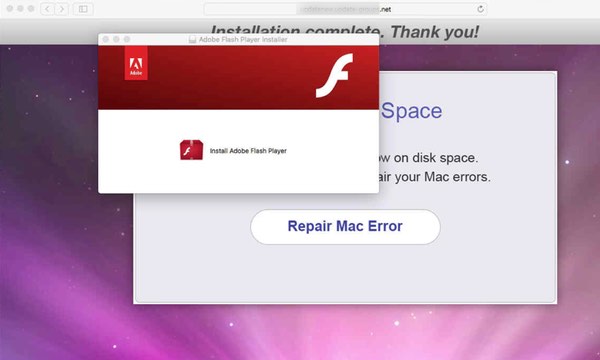
Finally, at the end of this process, scareware or other potentially unwanted applications have been installed on the user’s computer and will pop up bogus security warnings, redirect victims to web pages of the attackers’ choosing, or install malicious browser extensions.
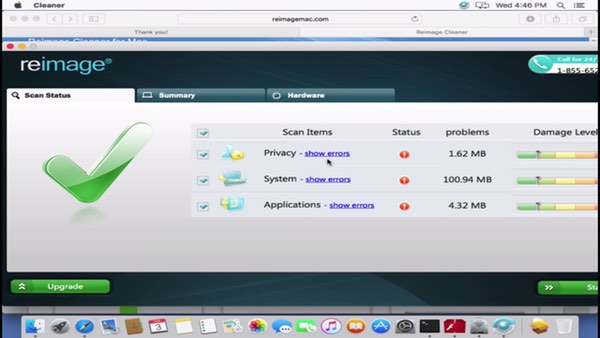
You should always be suspicious if a program suddenly tells you that you have a myriad of security problems on your computer, especially if you never installed the program in the first place! Always be on the look out for dodgy apps, and if you ever want to update Flash — make sure you’re getting the updates directly from Adobe’s own site rather than a web page created by scammers.
Editor’s Update — Feb. 8, 2016:
We have received a number of comments from customers confused about how to remove the scareware if infected, and so we updated this article for clarity and conciseness. Intego customers have been protected since April, 2015. When Intego VirusBarrier real-time scanning is enabled with up-to-date malware definitions, the anti-virus software will detect and eraticate this malware, identified as OSX/InstallMiez.
Editor’s Update — Feb. 10, 2016:
We have heard from several customers concerned after encountering pop-ups in the wild. You can encounter the “out of date” Flash pop-ups and be fine so long as you do not choose to install them. If you ignore the pop-ups (nothing gets downloaded), then nothing bad will happen. For Intego VirusBarrier customers who have real-time scanning enabled, sometimes it will detect the DMG file directly, but other times it may detect something inside the DMG file in which real-time scanning will not activate unless you open the installer to start the installation process.
A number of customers have also contacted us in reference to other pop-ups that appear in the Safari browser. What you may be encountering are variants of the pop-up alert scam we see happening a lot right now. For more details about this pop-up alert scam, see our Knowledge Base article.