New ‘Komplex’ Trojan Malware Targeting Macs [Updated]
Posted on
by
Jay Vrijenhoek
A new OS X malware has been discovered by security researchers from Palo Alto Networks. The malware, named “Komplex,” is a Mac Trojan created by the Sofacy Group and is apparently targeting the aerospace industry.
During analysis, the researchers found that Komplex malware was used in the past by exploiting a MacKeeper vulnerability. However, this new Komplex Trojan is targeting Macs by way of email attachments. Here’s what you need to know to stay safe!
What is the infection vector?
Komplex ends up on a user’s system through spear phishing, a method used by cyber criminals to get a victim to open an email with a malicious attachment, and masks as a Russian aerospace program information PDF.
The person who receives the email may think they are opening a PDF file with future plans for the Russian aerospace program, but in fact, it is a Trojan that will install files on the system and connect to a remote command & control (c&c) server. An actual PDF with said Russian aerospace details is opened in Preview, but this is just a decoy. This PDF is not downloaded but is part of the malicious attachment and is written in place.
Where does Komplex install?
The Trojan waits for an Internet connection and attempts to send a GET request to Google to confirm it’s not running in an anti-analysis/sandbox environment. After confirming an active Internet connection, the Komplex payload begins carrying out its main functionality. Several files are placed on the system upon install and then moved to their final locations, which are:
• /Users/$USER/Library/LaunchAgents/com.apple.updates.plist
• /Users/Shared/.local/kextd
Files are initially placed in /Users/Shared/, but are moved to their final destination:
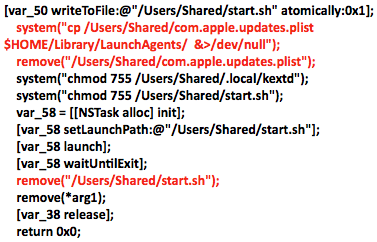
Once all components are in place and Komplex is up and running, it can download, install and execute additional malware, as well as delete files.
While Komplex installs, the following pop-up may appear:
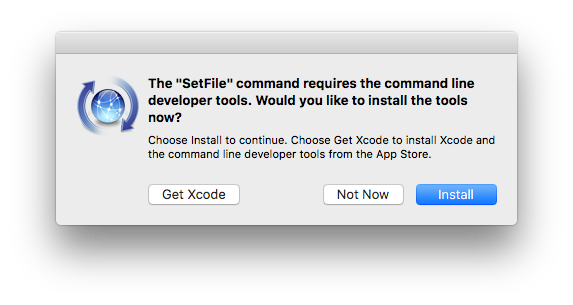
It’s important to note that regardless of which button is clicked, the malware will install. This warning is triggered by the binder (the executables responsible for installing the malware), which uses the SetFile command.
Should Mac users be concerned?
While Komplex does not appear to be doing anything malicious after installing itself, this can change instantly if the Sofacy Group decides to send commands for the C&C servers to relay. The risk here is currently for those working in the aerospace industry, but this technique can be used against OS X and macOS users anywhere.
As mentioned above, Komplex was used in the past by exploiting a MacKeeper vulnerability against Mac users. Another tool that Komplex shares a significant amount of functionality and traits with, called Carberp, was also used in past attacks against Windows systems.
The report mentions, “In addition to shared code and functionality, we also discovered Komplex command and control (C2) domains that overlapped with previously identified phishing campaign infrastructures associated with the Sofacy Group,” and “A benefit of retaining many of the same functionalities within the Windows and OS X Trojans is that it would require fewer alterations to the C2 server application to handle cross-platform implants,” which makes it easier for Sofacy Group to adapt and release future malware.
The Sofacy Group, also known as Fancy Bear, Pawn Storm, APT28 and Sednit has been active for years and has attacked government agencies in Eastern Europe and the West as well as several media organizations. They are believed to be behind the data breach at the National Committee of the Democratic Party and most recently the hacking of the world anti-doping agency. A group like this is not likely to go away any time soon, so more malware from them can be expected.
What steps can Mac users take to protect their computers?
If infected, Mac users can manually remove the Komplex files to clean up the infection. From the Finder menu “Go,” select “Go to Folder” and copy/paste each of the following paths (replace $USER with your own home folder name):
• /Users/$USER/Library/LaunchAgents/com.apple.updates.plist
• /Users/Shared/.local/kextd
If the files are found, your Mac is probably infected. Move the files to your trash and restart your Mac, then empty the trash and check the locations again. Your Mac should now be clear of Komplex.
Intego VirusBarrier detects all known components of Komplex malware, identified as OSX/Komplex. Intego is still investigating; we will update this story when new information is available.
This story has been updated.