Uptick in Malware and Vulnerabilities: What You Need to Know
Posted on
by
Jay Vrijenhoek
Intego has seen a recent increase in malware that affects Apple products, and while these threats are currently low risk, there are few things you need to be aware of so you can stay protected.
The recent uptick in malware began over the summer with the discovery of Eleanor, a piece of malware that opens a backdoor on OS X masquerading as a file converter app. Less than a month later followed the discovery of Adwind RAT, a remote access trojan targeting OS X.
That same month, we learned of the Pegasus exploit affecting iOS, giving those who targeted and infected an iOS device full access over its contents; Apple patched the same flaws in OS X about a week later. Though no in the wild exploit like Pegasus is known to target OS X, it is not a stretch to think it may have been out there.
August was a busy month as the Keydnap malware was found to hitch a ride on the Transmission application, stealing the OS X keychain contents from those infected.
That’s just the kind of trouble that was out there for OS X and iOS users in the last two months. Luckily, Apple patched the vulnerabilities that allowed Pegasus to run and Intego protects its customers from the above mentioned malware.
While there currently appears to be no active malware out there that can pose a threat, Intego is following several potential threats. Following are a few of these potential threats that Mac users need to be aware of.
Potential new Adwind RAT
Early September we learned of a file being distributed through email that, when opened, opens a backdoor on an OS X system and keeps an active connection to a remote server. It also creates a LaunchAgent to keep itself alive if a user logs out or restarts the computer. The process that runs in the background identifies itself as “StreamMainer,” which is a name that has been linked to Adwind in the past.
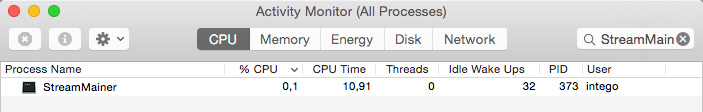
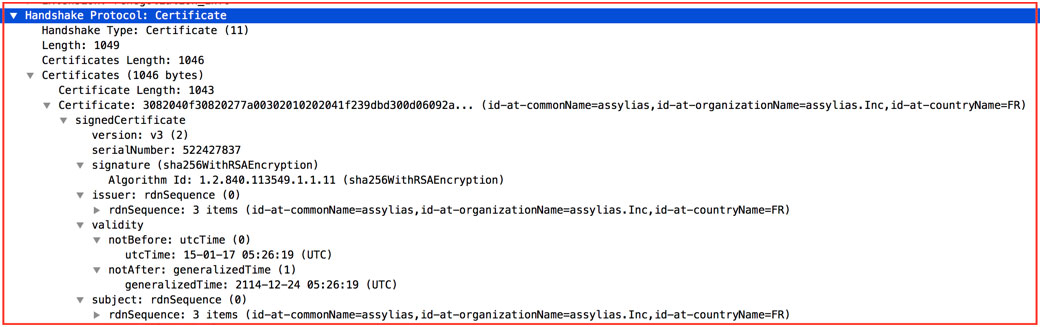
Traffic that was monitored between the backdoor and the server showed a certificate by “assylias.Inc,” which was also an indication this may be a version of Adwind.
Installing
When the malicious file is opened, Java installs files in the following locations:
- /.test.txt
- /Users/$USER/Library/LaunchAgents/org.Dell.plist
- /Users/$USER/.Dell (containing the following files:)
- /Dell
- /ID.txt
- /YTyiNIrqiic (containing the following files:)
- /SdtnKbfLft.AEFCU
- rGeLnFsWWp.AEFCU
How to know if your Mac is infected
From the Finder menu “Go”, select “Go to Folder” and copy/paste each of the following paths (replace $USER with your own home folder name):
- /Users/$USER/Library/LaunchAgents/org.Dell.plist
- /Users/$USER/Dell/
- /.test.txt
If the files or folders are found, your Mac is probably infected. Move the files to your trash and restart your Mac, then empty the trash and check the locations again. Your Mac should now be clear of Adwind RAT.
There is no indication at this time that the backdoor it creates is being used to steal data (or even if this malicious file is being actively spread online). As a precaution, Intego VirusBarrier detects this as Java/Adwind, so Intego users will be protected from it or whatever it may become.
iWorm dubbed as fake Flash Player
Intego has also learned of a Trojan posing as a fake Flash Player installer; a sneaky little bug that saw previous iterations open a backdoor on an infected system and steals files among other things. This particular version does not appear to activate the backdoor though, and in fact, the installation fails.
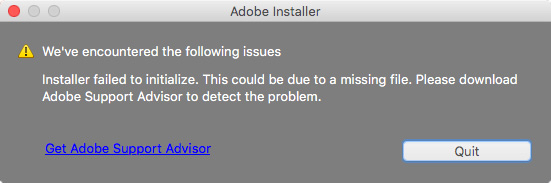
This could just be a Proof of Concept or the beginning of a functional Trojan horse. It is currently not known how (or even if) this Trojan is spreading in the wild, but VirusBarrier is ready for any potential encounters and detects it as OSX/iWorm.
“Mokes ” Malware
This week a backdoor for OS X was discovered. This cross platform malware is able to infect Windows and Linux systems as well, though an OS X sample of this backdoor was only recently uncovered. Mokes can take screenshots of an infected system as well as steal Office documents, record keystrokes, capture audio and video and execute commands.
Installing
When executed for the first time, the malware copies itself to the first available of the following locations, in this order:
- /Users/$USER/Library/App Store/storeuserd
- /Users/$USER/Library/com.apple.spotlight/SpotlightHelper
- /Users/$USER/Library/Dock/com.apple.dock.cache
- /Users/$USER/Library/Skype/SkypeHelper
- /Users/$USER/Library/Dropbox/DropboxCache
- /Users/$USER/Library/Google/Chrome/nacld
- /Users/$USER/Library/Firefox/Profiles/profiled
Corresponding to that location, it creates a LaunchAgent to achieve persistence on the system, so restarting the Mac will have no effect on its functionality.
How to know if your Mac is infected
From the Finder menu “Go,” select “Go to Folder” and copy/paste each of the above mentioned paths (replace $USER with your own home folder name). Again, if the files are found you are probably infected with Mokes. Remove the files and restart your Mac, then check for these files again to make sure they were properly deleted.
How this malware spreads is currently unknown, but if it finds its way onto your system, Intego VirusBarrier will detect it as OSX/Mokes and swiftly kick it to the curb.
Not every piece of malware is worthy of news coverage, but no news does not always mean good news. Intego’s malware team is hard at work analyzing potential threats every day of the week to make sure end users are protected.
While it’s certainly good to know your Mac antivirus software has your back, you can take some additional steps to protect yourself.
- Only download software from the official source. To use iWorm as an example, if a website prompts you for a Flash Player update (some even start the download without asking), ignore it. You hopefully don’t even have Flash Player installed at this point, but if you do, go to the Adobe website to see if a new Flash Player version is available. More useful tips can be found here. The same goes for Java and other plug-ins you may have installed.
- Make sure the official source of your software has a good reputation. This typically rules out MacUpdate, download.com, Softonic and bit torrent sites. If you find a website that lists files available for download, research that website. The first page of search results is usually a good testimony to the reputation of that website.
- Keep your operating systems and applications up to date. Using The App Store on both your Mac and iPhone you can keep your applications (and the system itself on the Mac) up to date. Updates and security patches serve an important purpose so it is recommended to install them when you can.
- Use caution when connected to networks that are not your own. See this guide on how to protect your Mac or iPhone when connecting to public Wi-Fi networks.
- You guessed it: Implement a solid backup strategy to keep your data safe. Be it from malware, ransomware or hardware failure, a smart backup system is always a good idea.