Do Macs need antivirus software? Debunking macOS malware myths
Posted on
by
Kirk McElhearn and Joshua Long
 One of the most common questions Intego receives is whether Macs need antivirus software. Naturally, it’s fair for you to assume that our opinion may be a bit biased—not just because Intego offers antivirus software as well as a full security suite to protect Macs, but also because our malware researchers are at the front line, and regularly discover new malware that targets the Mac.
One of the most common questions Intego receives is whether Macs need antivirus software. Naturally, it’s fair for you to assume that our opinion may be a bit biased—not just because Intego offers antivirus software as well as a full security suite to protect Macs, but also because our malware researchers are at the front line, and regularly discover new malware that targets the Mac.
But if you want to make your own informed decision about whether Macs need antivirus software, you’ll need to examine the facts. Let’s explore such topics as what built-in protection macOS offers, what types of threats it can and cannot stop, and several common myths about antivirus software.
First, let’s get some terminology out of the way. While the industry still talks about “anti-virus” software, there hasn’t been a virus that affects the Mac in a very long time (unless you count Microsoft Office macro viruses). However, malware—which is the broad category for any malicious software designed to do things such as damage or steal files, spy on a user by recording photos, videos, or keystrokes, or usurp a user’s identity—is rampant on both Windows and Mac.
Mac malware is continually increasing
 Malware specifically targeting the Mac has been increasing significantly in recent years. According to the latest security report from AV-TEST, an independent malware research institute, “the number of malware programs for Apple‘s operating system macOS has almost tripled. While the share of Mac malware [compared to Windows malware] is still quite low, there were nearly 100,000 samples found that affect Macs in 2018.”
Malware specifically targeting the Mac has been increasing significantly in recent years. According to the latest security report from AV-TEST, an independent malware research institute, “the number of malware programs for Apple‘s operating system macOS has almost tripled. While the share of Mac malware [compared to Windows malware] is still quite low, there were nearly 100,000 samples found that affect Macs in 2018.”
More recent reports have suggested that 1 in every 10 Macs contains OSX/Shlayer malware in particular, and that the total number of Mac malware threats rose 400% in 2019 and now outpaces Windows for per-endpoint malware infections by an almost 2:1 ratio.
As Windows has become more secure and Macs have increased in popularity, many cybercriminals have seen an opportunity to expand the scope of their attacks. Mac users tend to be much more complacent, since the platform has a very good reputation for security. But while the Mac is perceived to be relatively safe from some perspectives, it certainly has its flaws; no platform can be 100% secure.
Today’s malware differs from what we worried about in the early days of computing. Early viruses generally just deleted files or displayed strange screens or windows, but today’s malware is designed by cybercriminals who are in it for the money. Whether through stealing your credentials for a website or service, infecting your computer with ransomware, or installing cryptocurrency miner software, one of the main motivators for most malware makers is to make money.
Cryptocurrency miners are an interesting example of a legitimate technology that has been turned into something that’s either malicious or undesirable (the latter is often abbreviated PUP or PUA, for potentially unwanted program or app). Cryptojacking software uses a computer’s processor or graphics card to “mine” for Bitcoin, Monero, or other cryptocurrency, without the knowledge or explicit consent of the user. The more devices can be hijacked for this purpose, the more money the perpetrators can make. And in some cases cryptojacking is done via JavaScript code embedded within a web page, so merely visiting a compromised site could lead to a drive-by attack.
While it is helpful to advise people to only download software from reliable websites, avoiding malware is not as simple as abiding by that rule. There have been cases where developers’ websites have been hacked and their software has been infected with malware (e.g. Transmission—twice, HandBrake, and Elmedia Player), and other cases where software distribution sites have been tricked into distributing malware, or may have distributed PUPs unknowingly. And while Apple’s Mac App Store is generally considered to be safe, there have been incidents where App Store apps were also laden with malware or PUPs (e.g. Calendar 2 and several apps that exfiltrated users’ browser history).
Intego regularly discovers new malware, and very recently, there were several new threats found. But beyond malware specific to macOS, there are new types of vulnerabilities, such as Meltdown and Spectre, which exploit weaknesses in the processors that run Macs, which in some cases can be easily targeted. As we wrote in our explainer about these vulnerabilities, “The end result of leveraging Meltdown and Spectre could include leaks of sensitive data such as passwords and credit card information, among other things.” Some Apple updates have partially mitigated the risk of these vulnerabilities, but newer devices aren’t completely impervious to such attacks, and many older devices aren’t protected at all. As malware creators continue to search for vulnerabilities, they will find others, and targeting the hardware instead of the operating system makes these vulnerabilities much more serious and difficult to protect against. But “anti-virus” software can often detect attempts to exploit known vulnerabilities, and can quarantine apps that try to do so (see the Malware category on the Intego Mac Security Blog for examples of other Mac malware that has been found).
Gatekeeper: Apple’s app verification protection
While macOS contains some protection against certain types of malware and PUPs that you may encounter, this protection is limited. Gatekeeper is one of Apple’s technologies designed to protect you from potentially malicious apps. The Mac’s Security & Privacy settings allow you to limit the installation of apps to just those apps downloaded from the App Store, or to the App Store and developers who have added an Apple-approved code signature to their apps.
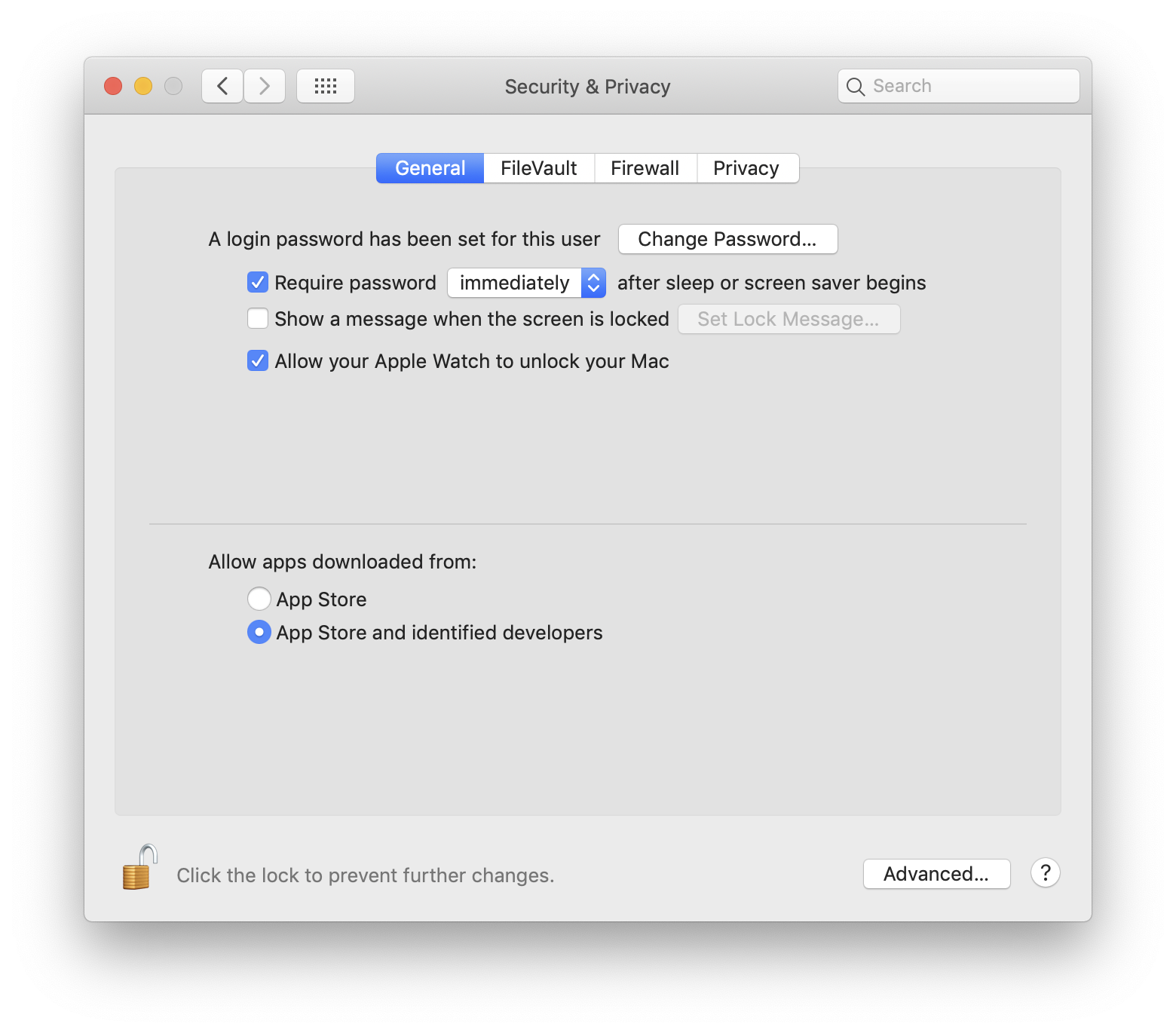
It’s possible to override these settings. If an app is blocked, you can Control-click it and choose Open, and you’ll be shown a dialog asking you to confirm your action. Once you have done this, you won’t be asked again when you re-launch the app.
Security researchers occasionally discover vulnerabilities that allow software to bypass Gatekeeper. Apple patched the most recent Gatekeeper bypass about two months after it was discovered, but it’s just a matter of time before someone finds another way around it.
XProtect: Apple’s malware detection engine
Another technology in macOS is known in the industry as XProtect (nicknamed after the XProtect.plist data file in macOS). Apple does not use this name on their website, but rather talks about File Quarantine and Known Malware Detection, and has in the past called it the Safe Downloads List (an ironic misnomer, since the XProtect data file could more accurately be described as a list of unsafe files). This is a rudimentary, signature-based tool that detects certain specific types of malware after it has been downloaded onto your Mac, and warns you if you’ve downloaded something that Apple considers potentially dangerous. Apple also has a background utility called the Malware Removal Tool (MRT) to delete malicious software that may already be on your Mac. Apple has also used MRT to disable non-malicious but vulnerable software, in the case of the recent Zoom vulnerability, which we discussed on episode 92 of the Intego Mac Podcast.
When you download a file with Apple’s Safari, Messages, or Mail apps (or certain other apps that are properly configured, like many third-party web browsers), a quarantine bit is set. This tells macOS to check the file using the XProtect signatures at the time the file is opened. However, Apple’s quarantine system only tags files downloaded with those specific apps. If you download files with another browser, from an FTP or other file server, or via cloud storage software like Dropbox or Google Backup and Sync, then this protection does not come into play. Also, while updates to XProtect are automatically installed by default on Macs, some people may turn off the automatic update feature and not get the updates in a timely manner. (You can learn all about macOS software updates in this article.) Moreover, Apple often takes a long time before they add signatures to XProtect, and they only include signatures for a handful of strains of malware, whereas Intego updates its malware signatures as soon as new threats are discovered and detects all known Mac malware (as confirmed by multiple independent tests).
Now that we’ve looked at the built-in malware defenses in macOS and some of their limitations, let’s examine some common myths about Mac malware and third-party antivirus software.
Myth #1: Malware only comes from “shady” sites
Many computer users—perhaps especially Mac users—believe the myth that if you simply avoid less-reputable places on the Internet—such as torrent sites, porn sites, illegal gambling sites, or sites distributing copyright-violating content, illegal copies of software, or “cracks”—you’ll be able to completely avoid any malware infections. Ah, if only it were that simple!
Unfortunately, this is not the reality. Although it’s true that malware is often distributed through such sites, there are many other ways for malware to get onto your Mac.
Perhaps the most surprising example is that malware distributors often buy expired domains, or hack into vulnerable sites, and set up pages that rank near the top of Google search results for particular search keywords—and then when unsuspecting victims click on such a link, it will redirect to a site designed to deceive people into thinking they have outdated software (typically Adobe Flash Player) or that their computer is infected with malware, and these sites can download malware or PUPs onto the victim’s Mac, often in the form of a Trojan horse cleverly disguised as a legitimate app or updater.
That’s just one of many ways that malware can get into Macs; there are also exploits, targeted attacks, and more. But hopefully this illustrates one of the reasons why we need anti-malware software: the bad guys will stop at nothing to infect your Mac. No matter how careful you are about what types of sites you visit and what software you download, you could get hit with a drive-by attack just by visiting a website.
Myth #2: I’m not worth targeting
Sometimes users make the mistake of assuming that their computer is only likely to get a malware infection if they’re specifically targeted by an attacker. Although targeted attacks really do happen, most malware makers don’t limit their attacks to a particular person or group; instead, they’re happy to infect anyone and everyone they can, because most malware has a financial motivation—which means that, generally speaking, the more victims get infected, the more money the malware maker can make.
Myth #3: Antivirus software will make my Mac slower
A decade or longer ago, the argument that antivirus software could slow down your Mac certainly may have had some merit, in some cases. But modern Macs generally have plenty of resources (processing power, memory, and disk speed) to allow antivirus software to protect you without any noticeable detriment to the Mac’s speed.
Myth #4: Antivirus software will make my Mac less secure, or less stable
Some pundits allege that running antivirus software makes computers less secure or less stable, citing examples of antivirus software that was found to have vulnerabilities, false-positive detections, or other flaws (never mind that in virtually every case, such flaws were fixed very quickly after being discovered).
This is a perilously flawed argument. It’s akin to refusing to use seatbelts or airbags just because of extremely rare cases where they caused injury, while completely ignoring the fact that both seatbelts and airbags have saved thousands of lives and continue to save lives every day. Similarly, using antivirus software is far safer than not using any.
By protecting yourself, you protect others
Biological vaccinations can protect against potentially fatal diseases, and although we often think of them as protecting only the recipient of the vaccine, they also protect those who are not vaccinated because they reduce the opportunities for diseases to spread. Similarly, using anti-malware software on your Mac helps protect the people you interact with. If you can ensure that all your files are safe, then the people with whom you share files won’t get infected. This is not only important in a business environment where files you receive and share may eventually be used on many computers, but also in your home environment and among your friends. The more people there are who protect their computers against malware, the safer everyone is.
Although the total quantity of malware samples that affects Macs is still much lower than for Windows, the actual level of risk is much closer than one might assume. Macs are just as susceptible to infection as Windows PCs—and one could argue that Macs are actually more susceptible, since recent versions of Windows come with more robust anti-malware capabilities than macOS.
In our modern era where most Macs no longer have a removable media drive built in, we may not have to worry about floppy disks or even CDs or DVDs as vectors for malware anymore, but files you download, and websites you visit, can be weaponized by cybercriminals to target your Mac. And the best way to protect yourself is to install anti-malware software on your Mac.
How can I learn more?
 Each week on the Intego Mac Podcast, Intego’s Mac security experts discuss the latest Apple news, security and privacy stories, and offer practical advice on getting the most out of your Apple devices.
Each week on the Intego Mac Podcast, Intego’s Mac security experts discuss the latest Apple news, security and privacy stories, and offer practical advice on getting the most out of your Apple devices.
On episode 97, Kirk and Josh did a deep-dive discussion on whether Macs need antivirus software. Later, in episode 255, they talked about Apple’s targeted (but extremely limited) scanning for a few specific types of Mac malware. Be sure to follow the podcast to make sure you don’t miss any episodes!
You can also subscribe to our e-mail newsletter and keep an eye here on The Mac Security Blog for the latest Apple security and privacy news. And don’t forget to follow Intego on your favorite social media channels: ![]()
![]()
![]()
![]()
![]()
![]()
![]()