Meltdown and Spectre: What Apple users need to know
Posted on
by
Joshua Long
You’ve probably heard something about “Meltdown” and “Spectre,” perhaps even in the mainstream media, and you likely heard that it has something to do with an Intel security flaw.
But do you know how it affects your Apple devices—your Mac, iPhone, iPad, iPod touch, Apple Watch, or Apple TV—and what actions you may need to take to stay safe?
Never fear, that’s why we’re here! It’s a complex problem, but we’ll break it down and share the main tidbits about these vulnerabilities you need to know as a user of Apple products.
What are Meltdown and Spectre?
On Monday, January 1, 2018, a developer blog, called “python sweetness,” brought to light an issue in which “there is presently an embargoed security bug impacting apparently all contemporary CPU [central processing unit] architectures that implement virtual memory, requiring hardware changes to fully resolve.”
 The Register published an article the following day that emphasized the design flaw with regard to Intel processors, and from there snowballed into a worldwide discussion about a serious flaw in Intel CPUs that had major security implications.
The Register published an article the following day that emphasized the design flaw with regard to Intel processors, and from there snowballed into a worldwide discussion about a serious flaw in Intel CPUs that had major security implications.
Macs, along with the vast majority of the world’s Windows and Linux PCs, use Intel processors.
As more information came to light in the subsequent days, it became clear that more than just Intel CPUs are affected; there are also implications for other processor architectures, including AMD processors as well as ARM-based processors like those found in Apple’s iPhones and iPads.
It turns out that Intel and a handful of software development giants, among them Apple, Microsoft, and the Linux kernel developers, have known about the design flaw since at least November 2017 and have been working behind the scenes to prepare for a coordinated public disclosure and remediation of the issue. (At least, that was the plan until “python sweetness” and The Register brought the issue out of obscurity and into the public spotlight.)

“Meltdown” and “Spectre” are nicknames for techniques that can enable an attacker to access computer memory that shouldn’t be accessible; this is accomplished by abusing a technology called “speculative execution.”
Speculative execution is a processing feature that enables computing devices to run faster by predicting what will happen next in an app, and preemptively working toward multiple possible outcomes all at once.
The end result of leveraging Meltdown and Spectre could include leaks of sensitive data such as passwords and credit card information, among other things.
What do all these names mean?
A vulnerability may be known by many names.
Perhaps the broadest term for the vulnerabilities in question would be “speculative execution vulnerabilities.”
“Meltdown” and “Spectre” are the main names that have caught on in association with this bug; each of these are unique and will be described further in their own sections below.
When the story broke, it was at first being discussed online under the name KPTI in reference to Kernel Page-table Isolation (formerly called KAISER), a feature of the Linux kernel that mitigates the Meltdown vulnerability.
There’s also a not-safe-for-work nickname that was reportedly conceived by the Linux kernel team: F***WIT (which stands for “Forcefully Unmap Complete Kernel With Interrupt Trampolines”).
You may also see references to “CVE” numbers associated with these bugs. CVE stands for Common Vulnerabilities and Exposures, and CVE numbers are used for the purpose of tracking the same bug across multiple vendors and media outlets, as bugs tend to be described in many different ways and may have various nicknames.
What is Meltdown?
Meltdown is the nickname for one of two major categories of exploits at this time. It may also be referred to as the “rogue data cache load” technique, or CVE-2017-5754.
Successful exploitation could allow an attacker’s code running in a user-privileged app to read kernel (superuser-privileged) memory.
Apple said that its own analysis suggested that the Meltdown exploitation technique “has the most potential to be exploited” as compared with the Spectre exploitation techniques.
What is Spectre?
The other exploitation techniques are known collectively as Spectre (sometimes spelled Specter). The two techniques may be referred to as “bounds check bypass” or CVE-2017-5753, and “branch target injection” or CVE-2017-5715.
From Apple’s public statement:
“Analysis of these techniques revealed that while they are extremely difficult to exploit, even by an app running locally on a Mac or iOS device, they can be potentially exploited in JavaScript running in a web browser. Apple will release an update for Safari on macOS and iOS in the coming days to mitigate these exploit techniques.”
In other words, Web pages in an unpatched browser can potentially exploit Spectre.
Is my Apple device safe from Meltdown?
If your Apple device is running one of the following operating systems, you’re already (at least partially) protected against Meltdown attacks:
- macOS 10.13.2 or later
- iOS 11.2 or later
- tvOS 11.2 or later
- watchOS
 It’s important to note that Apple often releases security-only updates for the two previous versions of macOS, in this case Sierra and El Capitan. However, Apple has not given any indication that updates for Sierra or El Capitan are forthcoming.
It’s important to note that Apple often releases security-only updates for the two previous versions of macOS, in this case Sierra and El Capitan. However, Apple has not given any indication that updates for Sierra or El Capitan are forthcoming.
Thus, if you have an older version of macOS (or OS X), you’ll need to upgrade to macOS High Sierra version 10.13.2 or later to protect against Meltdown attacks. (You may need to first find out whether your Mac can be upgraded.)
Apple has indicated that macOS High Sierra version 10.13.3 is in the works and will include further protections against Meltdown attacks, so be sure to install it when it becomes available.
 According to Apple, “Apple Watch is not affected by either Meltdown or Spectre.”
According to Apple, “Apple Watch is not affected by either Meltdown or Spectre.”
Apple specifically claims “watchOS did not require mitigation” for Meltdown, while “watchOS is unaffected by Spectre.”
The company has not offered further explanation as to why watchOS, which shares much of its codebase with iOS, allegedly does not require mitigations.
Is my Apple device safe from Spectre?
In short: no, not yet (see editor’s update below for details).
![]() Apple is planning to release a Safari update for both macOS and iOS “in the coming days,” so stay tuned for that. Once the updates are available, you’ll find the Mac update in the Mac App Store app under Updates, and you’ll find the iOS update in the Settings app under General > Software Update.
Apple is planning to release a Safari update for both macOS and iOS “in the coming days,” so stay tuned for that. Once the updates are available, you’ll find the Mac update in the Mac App Store app under Updates, and you’ll find the iOS update in the Settings app under General > Software Update.
If you use a third-party browser such as Firefox or Chrome, you’ll want to install any new updates that get released this month.
Firefox 57.0.4 is already out and includes mitigations for Spectre. You can check for updates by going to the Firefox menu and selecting About Firefox, or you can download a fresh copy of the app.
Meanwhile, Google isn’t planning to update Chrome until around January 23, according to Fortune. However, Chrome users who wish to be protected can follow a manual process to enable a Spectre mitigation (note, however, that doing so will increase Chrome’s memory consumption by about 10–20%).
Until Apple and Google release patches, it’s probably safest to use Firefox 57.0.4 or later on your Mac, and avoid using Safari or Chrome for now.
As for iOS devices (iPhone, iPad, and iPod touch), there doesn’t seem to be a safe alternative browser, so you’ll just have to wait patiently for Apple’s forthcoming update. If you’re concerned, you may wish to avoid logging into sites or entering any passwords or sensitive information in Safari or other mobile browsers for iOS, and instead opt to use your Mac for Web browsing until Apple updates iOS.
Editor’s Update, January 8: Apple has released security updates for macOS High Sierra, Safari and iOS to mitigate Spectre.
macOS High Sierra 10.13.2 Supplemental Update includes security improvements to Safari and Webkit to mitigate the effects of Spectre (CVE-2017-5753 and CVE-2017-5715). Apple notes, “Installing macOS High Sierra 10.13.2 Supplemental Update will update Safari to version 11.0.2 (13604.4.7.1.6) or version 11.0.2 (13604.4.7.10.6).”
Safari 11.0.2 is available for OS X El Capitan 10.11.6, macOS Sierra 10.12.6, and macOS High Sierra 10.13.2.
To check the version of Safari installed on your Mac:
- Open Safari
- Choose Safari > About Safari
iOS 11.2.2 is available for iPhone 5s and later, iPad Air and later, and iPod touch 6th generation. “iOS 11.2.2 includes security improvements to Safari and Webkit to mitigate the effects of Spectre,” according to Apple’s security notice.
Will Apple update Macs’ EFI firmware?
It remains to be seen whether Apple will release EFI firmware updates for Macs to more fully address the issue closer to the hardware level.
Noting that Apple did not say anything about EFI in its public statement, we reached out to Apple to inquire about whether EFI updates are forthcoming. Apple’s Todd Wilder responded with the following statement:
“We no longer distinguish between EFI updates and OS updates for the Mac. We will be applying mitigations wherever in the stack it is necessary, and customers will receive those updates in the form of macOS updates.”
In other words, if Apple does decide that it’s necessary to release EFI firmware updates for any Macs, those updates would be bundled with a future version of macOS High Sierra or later, rather than published as a distinct and separate update.
Will my device be slower after I update?
 Early reports suggested that by disabling speculative execution functionality, certain system functions may be anywhere from 5 to 30 percent slower.
Early reports suggested that by disabling speculative execution functionality, certain system functions may be anywhere from 5 to 30 percent slower.
Apple claims that its Meltdown and Spectre mitigations do not cause such serious performance degradation.
According to Apple, the Meltdown mitigations already in place in macOS 10.13.2, iOS 11.2, and tvOS 11.2 “resulted in no measurable reduction in … performance.”
However, Apple indicates that its upcoming mitigations for Spectre in Safari may have a performance impact of less than 2.5% in one particular benchmark, while other benchmarks see no measurable reduction in performance.
In short, your Apple device probably won’t feel slower as a result of Apple’s Meltdown and Spectre mitigations. (Your iOS device might, however, feel slower for other reasons.)
Is there anything else I should know?
Absolutely. First of all, this is a developing story, so expect further plot twists. It’s very likely that we still don’t know all of the ramifications of the flaws in speculative execution processor technology.
 There’s a special episode of the Intego Mac Podcast coming next Wednesday, January 10, in which Kirk McElhearn and I further discuss the topic and explain what speculative execution means. Be sure to subscribe now in iTunes/Podcasts or in your favorite podcatcher to make sure you get the Meltdown/Spectre episode when it becomes available.
There’s a special episode of the Intego Mac Podcast coming next Wednesday, January 10, in which Kirk McElhearn and I further discuss the topic and explain what speculative execution means. Be sure to subscribe now in iTunes/Podcasts or in your favorite podcatcher to make sure you get the Meltdown/Spectre episode when it becomes available.
If you own or support any Windows systems (including if you run Windows on your Mac, either via Boot Camp or via virtual machine software such as VMware Fusion, Parallels Desktop, or Oracle VirtualBox), be sure to install the latest Windows updates from Microsoft. ![]() Note that systems running Windows 7 (or Server 2008 R2) or Windows 8.1 (or Server 2012 R2) may need to manually download and apply the patch, since it may not appear in Windows Update; meanwhile, Windows 10 (and Server 2016) users should get the update as part of the usual patch cycle. Make sure your Windows anti-virus is fully up to date before you install the Windows patches.
Note that systems running Windows 7 (or Server 2008 R2) or Windows 8.1 (or Server 2012 R2) may need to manually download and apply the patch, since it may not appear in Windows Update; meanwhile, Windows 10 (and Server 2016) users should get the update as part of the usual patch cycle. Make sure your Windows anti-virus is fully up to date before you install the Windows patches.
Windows PCs may also need BIOS/UEFI firmware updates in order to be better protected. Not all PC manufacturers have given information about which PC models will be receiving updates, and some older PCs simply won’t be getting BIOS updates. If you’re running Windows via a virtual machine on your Mac, check with your VM vendor to see whether a new version may be needed (VMware has released a public statement, but Parallels and Oracle have not yet).
Additional Resources
If you’d like to learn more about the speculative execution vulnerabilities, the following resources may be useful:
- Apple has issued a statement titled “About speculative execution vulnerabilities in ARM-based and Intel CPUs”
- https://meltdownattack.com is the “official” Meltdown and Spectre information site
- Bleeping Computer and Forbes have both attempted comprehensive lists of vendor updates, although neither list is complete (neither links to BIOS updates, for example)
Final Thoughts
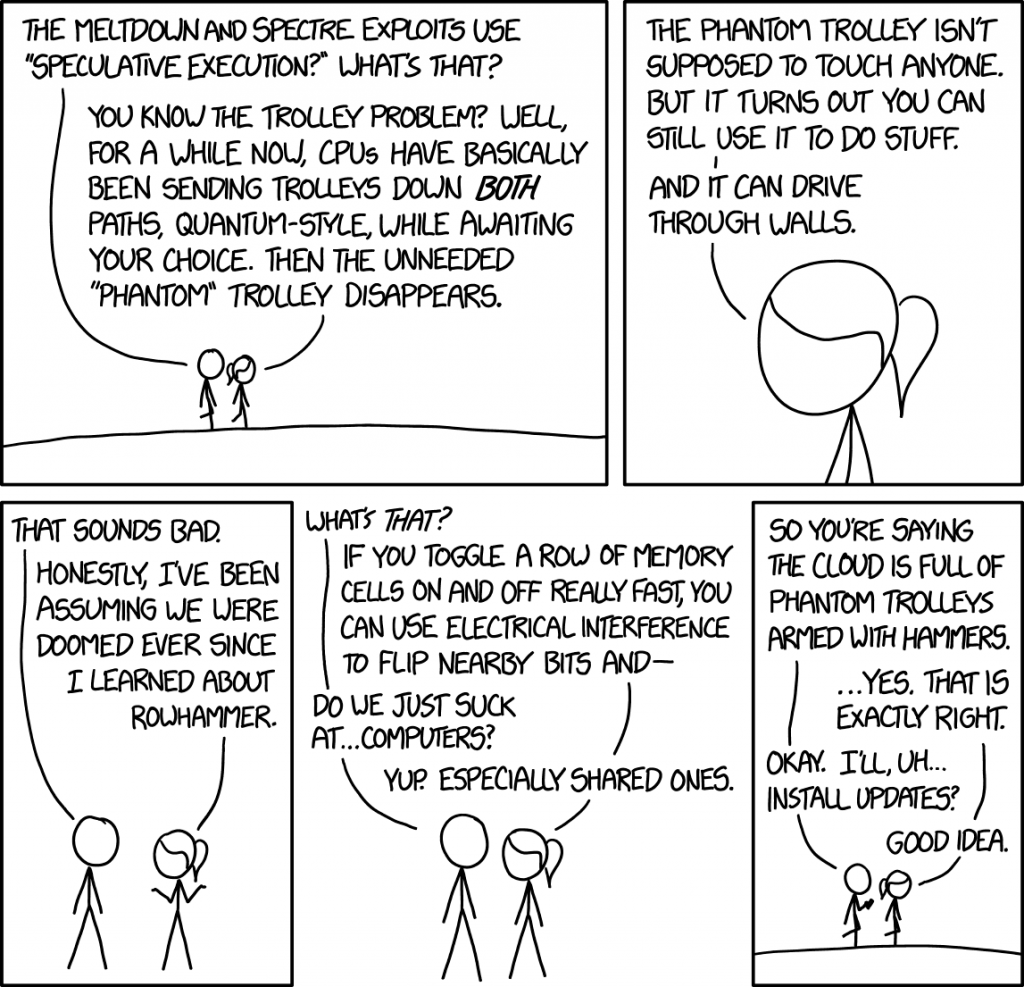
Image credit: xkcd #1938 by Randall Munroe
The world’s public knowledge about speculative execution vulnerabilities is only just beginning to blossom. As more brilliant minds begin exploring potential avenues for exploitation, it’s likely that more patches will be needed, so subscribe to The Mac Security Blog, the Intego Mac Podcast, and Intego’s YouTube channel to make sure you don’t miss any important news!
What are your thoughts?
We’d love to hear your comments!
Why do you suppose Apple used different language about watchOS, saying that it “did not require mitigation” for Meltdown, while it “is unaffected by Spectre”?
Are there any other potential impacts of Meltdown and Spectre about which you feel Apple product users should be aware?
Discuss in the comments below, and be sure to share this article with your friends.
And after you listen to the upcoming podcast, feel free to write in with questions; you could win a $25 gift certificate or another great prize! For details, subscribe and listen to the upcoming January 10 episode.
Intel processor image credit: Intel in Deutschland. Meltdown and Spectre logos by Natascha Eibl via meltdownattack.com.