Handbrake’s Server Compromised, Download Installs Complex Trojan
Posted on
by
Jay Vrijenhoek
Handbrake, a popular open source video encoder, posted on its forums this weekend saying that their mirror download server was compromised. Anyone who downloaded Handbrake between May 2 and May 6 potentially grabbed a version that was infected with malware. Intego VirusBarrier anti-virus identifies and eradicates this malware as OSX/Proton.B.
What is the infection vector?
Only those that downloaded Handbrake from their mirror server (download.handbrake.fr) received the malicious application. It was not distributed on any other websites.
How does Proton install?
The Handbrake application arrives in a .dmg file as expected, and upon opening the file, nothing suspicious can be seen. The user will drag Handbrake to their Applications folder and launch it.
At this point, the application does something unusual, which will immediately stick out to long time Handbrake users: It asks for administrator privileges. Under the guise of needing to install additional codecs, a malicious payload is installed instead.
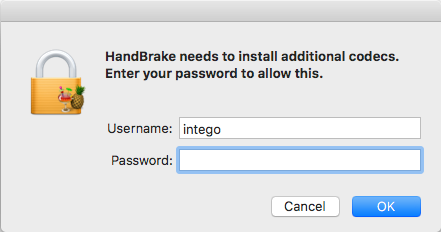
Once the password is entered, Handbrake will launch and it appears to be business as usual. In the background, however, a backdoor was installed, named “activity_agent.” The backdoor was observed contacting 85.17.25.66, which is the IP address that hosts the handbrake website. The compromised server could have been used as a Command and Control (C&C) server as well.
The backdoor application activity_agents is placed in Users > *your user* > Library > RenderFiles, and it is kept alive through restarts with a simple LaunchAgent.
Keychain data, Safari stored form data, and Safari cookies are collected, compressed and stored on the system for later upload. The activity_agent does not appear to upload or download any data during our testing. Google Chrome, Firefox, Opera and likely other browsers are raided for sensitive information.
Should Mac users be concerned about Proton?
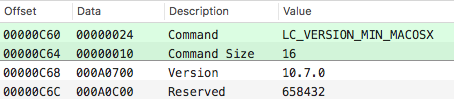
The malicious payload runs on any Mac with OS X 10.7 or newer.
At the time of writing, the malware does not appear capable of uploading the sensitive user data to its server, but we should assume that it did successfully do so in the May 2-6 timeframe. Handbrake offers the following advice in its forum post:
Based on the information we have, you must also change all the passwords that may reside in your OSX KeyChain or any browser password stores.
Good advice seeing as all the stored names, passwords, form data, and more, could now be in the hands of the bad guys.
Handbrake notified Apple whom late afternoon added the signature to its XProtect database as OSX.Proton.B. Unfortunately, even with the latest XProtect update in place, Proton still installed and ran just fine, though some other researchers have reported that XProtect did in fact stop the DMG from being opened. However, without a server to offload its collected data to, it is currently not a major threat.
What is worrying, however, is the way the attackers went about this. As with Transmission, not once but twice, the download server was compromised and the application available for download was replaced with a malicious one. Going after servers, which are typically not updated or patched as often as they should be, will result in less users downloading your malware, but the fact that it comes from a trusted source will make those users not suspicious at all. If a user is not suspicious, they won’t go looking for malware, and malware that goes undetected longer is typically more successful.
If this becomes a trend, and even the servers of the trusted source can no longer be trusted, we may very well be in trouble.
One way to verify if the file you downloaded is the real deal, is by comparing checksums. In Handbrake’s case, they maintain a page that lists all the checksums for available downloads, so anyone can verify the download is compromised. In reality, very few people actually do this, and a lot of websites that distribute software don’t even offer these checksums for you to verify. Apple used to offer these checksums on their downloads page, but has since stopped doing so as well.
For websites that do offer these checksums, verification is easy. Open the Terminal application (Applications > Utilities) and type the following (include a space at the end):
openssl sha1
Now, simply drag and drop the downloaded file onto the Terminal window and hit enter. In the case of the malicious Handbrake download, this is the result:
intego$ openssl sha1 /Users/intego/Desktop/HandBrake-1.0.7.dmg SHA1(/Users/intego/Desktop/HandBrake-1.0.7.dmg)= 0935a43ca90c6c419a49e4f8f1d75e68cd70b274
According to the Handbrake website the SHA1 checksum for this download should be “75c6204d7bd7d9c6e5b1fedb56697ae2f3857789,” they clearly do not match up. If any user got infected with Proton through Handbrake, they did not run this simple security check.
How to tell if your Mac is infected (and removal instructions)
Open Activity Monitor and search for a process named “Activity_agent.” If this process is running, your Mac is infected.
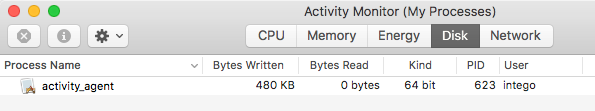
Click the process, and then close it with the X button in the menu bar.
To clear the infection off your Mac, browse to the following folders and trash the following files:
- Applications – Delete the Handbrake application.
- Users > *you* > Library > VideoFrameworks – Delete this folder and everything in it
- Users > *you* > Library > RenderFiles – Delete the activity_agent application
- Users > *you* > Library > LaunchAgents – Delete “fr.handbrake.activity_agent.plist” and “fr.handbrake.activity_agent.plist-e“
- Users > *you* > Library > Caches > fr.handbrake.activity_agent – Delete the folder
With those files deleted, empty the trash and restart your Mac. Double-check the same locations again after the restart to ensure the infection is indeed cleared. If a warning shows that some items cannot be deleted, because they are in use, you’ll be able to empty the trash after the restart.
For Intego’s Mac anti-virus customers, protection comes in the form of updated malware definitions, which will detect and remove all of the Proton files. Proton components are detected by Intego VirusBarrier as OSX/Proton.B.
How to protect yourself from Proton
When the official server of the trusted source has been compromised, and the malware is coded to act much like the real application, there is very little to warn you something is amiss. Verifying your downloads will be the only way you can be sure the download was not compromised. Using the built-in updater, if an application provides one, is typically the best way to receive updates for an application.
There is much still to be discovered about Proton.B as it is far more complex than it appears. This malware is still under investigation and as new details emerge we will update this story.