Cryptominer ‘mshelper’ Targets macOS: What You Need to Know
Posted on
by
Jay Vrijenhoek
Discussions of a CPU consuming process, called “mshelper,” have surfaced on the Apple support forums and Reddit. Users mentioned their fans spinning unusually fast, computers running hotter than usual and performance taking a hit as a result of the mshelper process. Upon further investigation, this process turns out to be a cryptominer for macOS. Intego VirusBarrier detects and eradicates this malware as OSX/mshelper.
This isn’t the first time unwanted cryptomining malware have been found running on Macs—and likely won’t be the last time either. You may recall a recent Intego YouTube video in which we discuss how to avoid cryptomining malware and protect your Mac:
The video explains how you can tell if your Mac is infected, such as high CPU usage, and outlines steps you can take to remove persistent cryptomining malware.
If you find mshelper running on your Mac, you’ll want to remove it immediately to avoid further system degradation. Here’s how the mshelper cryptominer works and how to remove it from your system.
What is the infection vector?
That is still unknown, but all of the usual suspects can be the culprit here. Twice this new mshelper process has popped up where logs indicate Adobe Flash Player was recently installed. This does not mean mshelper comes from a fake Adobe Flash Player installer, but it is the number one suspect at the moment. (RELATED: Why BitTorrent Sites Are a Malware Cesspool.)
What does mshelper do?
The reason so much processing power is used by mshelper is because the process is a cryptocurrency miner. It uses your Mac’s horsepower to crunch numbers and mine Monero cryptocurrency for whomever created the malware. Spreading the mining process over hundreds or even thousands of computers increases the odds of the malware author to make money, but going about it the way mshelper does meant the exercise was doomed from the start.
By consuming the maximum amount of processing power, mshelper was, of course, destined to be detected very soon. It doesn’t care if you are using your Mac and need the processing power for other tasks, and it doesn’t lurk in hiding and wait for your Mac to be idle before mining. Instead, it starts mining full blast and doesn’t stop until the victim removes it from their Mac. In testing, at minimum mshelper used 50% of the available processor cores at all times.
A LaunchDaemon is installed that ensures the miner starts after a logout or reboot, and mshelper maintains a connection with xmr-us-east1.nanopool[.]org on TCP port 14444. Connections to other IP addresses and hosts were also observed, one of them being 100.ip-142-44-242[.]net on the same TCP port number.
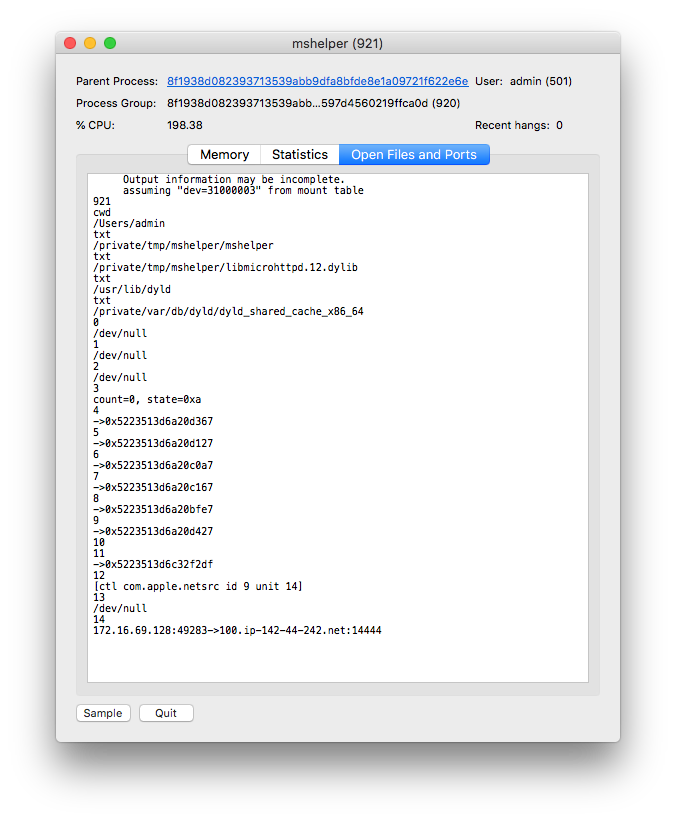
Should Mac users be concerned about mshelper?
While mshelper is mostly harmless, the biggest concern is how it lands on a system. A fake Adobe Flash Player, infected installer that came from a BitTorrent website, or even a hijacked legitimate installer that came from the original source are all potential infection vectors. As the infection vector is unknown, one should follow best security practices and have anti-virus and firewall protection installed on their system to stop malware in its tracks.
How to tell if your Mac is infected (and removal instructions)
The biggest giveaway indicating your Mac is infected with mshelper is the sudden increase in fan noise or heat, as the processor is tasked with mining Monero. An impact in CPU performance will also likely be noticeable. Luckily, mshelper is nothing sophisticated and is fairly easy to get rid of.
First, open Applications > Utilities > Activity Monitor. Click in the search field at the top right side of the window and type in mshelper. If mshleper is running on your system, it will show in the list and can be seen using a decent chunk of processing power.
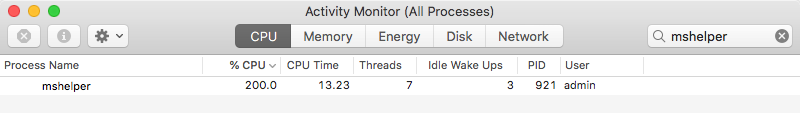
Highlight the mshelper process by clicking on it once, and then click the X button above it to stop the process.
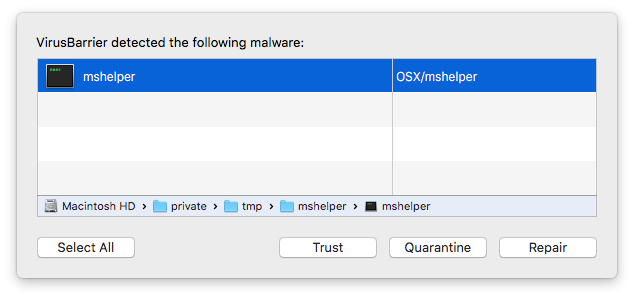
With the processor back under your control, it’s time to track down the components and remove them. For Intego VirusBarrier users, this is as simple as running a scan of the system and removing all the mshelper components that the anti-virus detects, identified as OSX/mshelper.
For those that do not use VirusBarrier and want to manually check for infection, here is the list of components to look for:
Library > LaunchDaemons > com.pplauncher.plist (file)
Library > Application Support > pplauncher (folder)
private > tmp > mshelper (folder) this is a temporary directory mshelper is installed in but should still be checked.
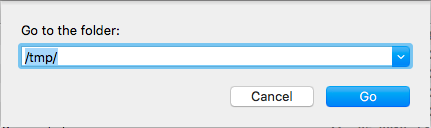
The private and tmp directories are hidden by macOS, so to search there you will have to use “Go to Folder” from the Finder’s Go menu. Then simply type the following:
/private/tmp/
or
/tmp/
Both commands will land you in the same folder. Now you can search for the mshelper folder and delete it.
If any of the above components were found, delete them and empty your Mac’s Trash. Now simply restart your Mac, and the irregular processor / fan behavior should be back to normal.
How to protect yourself from mshelper
When the infection vector is known for a particular strain of malware, it’s easy to say, “Avoid this document” or “never open this installer.” In this case, the source of mshelper is unknown, but we still feel it’s important to issue a general warning for Mac users, even if the infection vector is currently unknown. This circles back to the often mentioned layered security and best practices to harden your Mac. In a nutshell, these are:
Use an antivirus solution
Malware comes in all shapes and sizes and a good antivirus solution will catch them as soon as their signatures are known.
Use a firewall
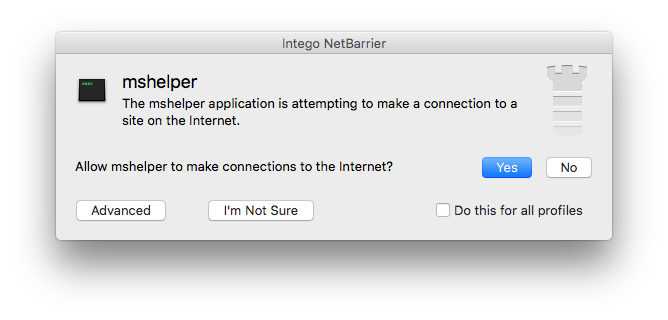
A good firewall monitors not just the incoming traffic, but the outgoing traffic as well. Malware will always call home sooner or later, and a firewall can catch this connection request and alert you about it. In the case of mshelper, Intego NetBarrier alerted me to its presence before I even had a chance to scan the test system.
Only install software from its original source
Whether installing Adobe Flash Player, Adobe Photoshop, Microsoft Office or a browser extension, always be sure to get it from the original source. If a website prompts you to install a software update, make note of it and close the window. Then go to the source and download the latest update to your software, if one is indeed available. Using the built-in updater most applications now have is also a good option.
Discontinuing the use of Adobe Flash Player is not only a good idea in terms of security, but it also makes the fake browser popups stating you need to update Flash Player obviously fake. As you don’t have Adobe Flash Player installed, any prompt for a Flash Player update will be fake!
Have something to say about this story? Share your comments below!