Caution! These Black Friday “deals” may be bad for your security
Posted on
by
Joshua Long

Each year, retailers announce door-busting deals on items they think will attract customers to their stores the day after the U.S. Thanksgiving holiday. Black Friday is one of the most popular shopping days of the year. Along with its neighbor Cyber Monday extending into Cyber Week, these shopping days (and any “early Black Friday” deals) ostensibly initiate the Christmas holiday shopping season in the United States and elsewhere.
(Keep reading—we have a special 2024 year-end discount for first-time buyers of Intego software.)
Electronic gadgets are typically among the most sought-after items. As I began to casually browse some early Black Friday deals this year, I noticed the continuation of a disturbing trend that I’ve observed in previous years.
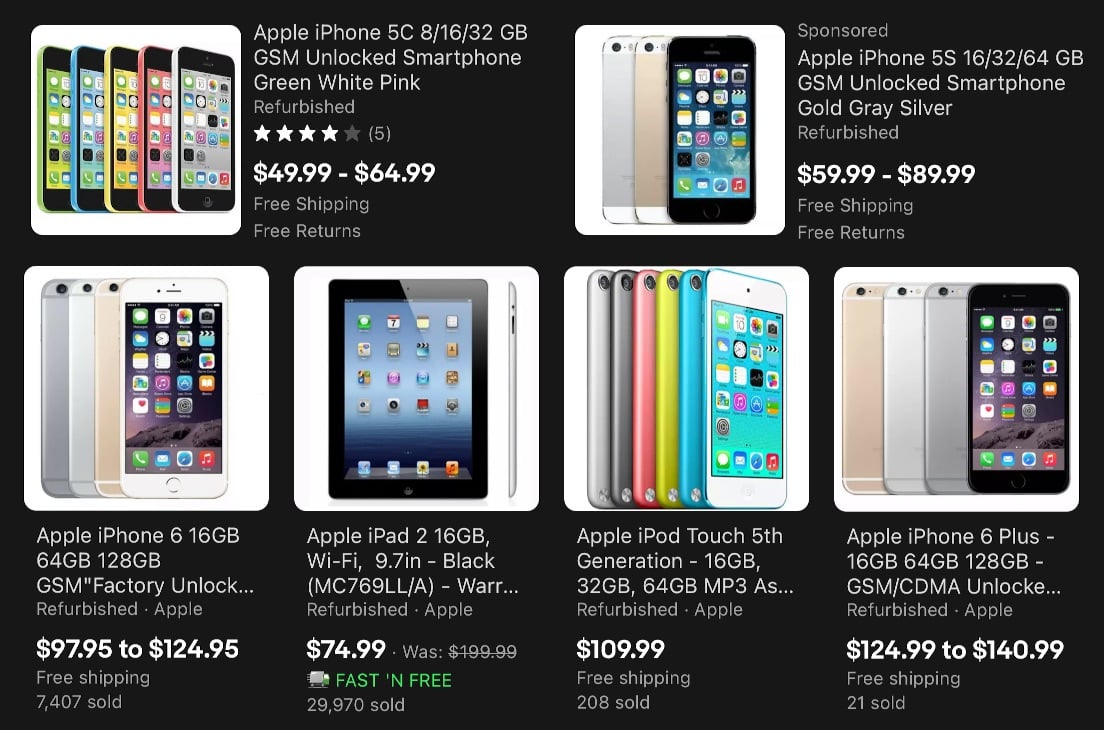
Many retailers sell old, vulnerable Apple devices

At one particular retailer, one of the “deals” was a heavily discounted iPhone 5c, for less than $50. And as I kept browsing, I saw more apparent bargains for other old iPhones and iPads, including an iPad 2 for less than $75.
What could possibly be worrisome about deeply discounted, years-old Apple devices, you might ask?
For one thing, many of these devices are no longer receiving any operating system updates or security patches from Apple. Anyone who buys an iPhone 5c, even if it’s brand new and unopened, will forever be stuck with iOS 10.3.3, which has hundreds of known security vulnerabilities that Apple will never patch—including Spectre, KRACK, and many others—and lacks new security features such as USB Restricted Mode, camera and microphone in-use indicators, etc. An iPad 2 is even worse, being limited to iOS 9.3.6.
But it’s not merely the ancient iPhone 5c and iPad 2 that you should avoid. Many newer Apple devices are vulnerable as well.
One particularly notable issue (because of a hardware flaw that cannot be fixed with an iOS update) is that any iPhone or iPad with an Apple A5 through A11 Bionic processor is vulnerable to checkm8, an “unpatchable bootrom exploit.” This means that someone with physical access to your device can install malware, or in some cases* can unlock the device and access all your data. We discussed this on episode 103 of the Intego Mac Podcast (jump ahead to 10:15 in the player below to hear that conversation).
Devices vulnerable to checkm8 include the following models that were originally released between 2011 and 2019:
- all models of iPhone from 4S through 8 & X, incl. the 1st-gen SE (2016)
- all models of iPad from 2 through 7th-gen (2019)
- iPad Air (2013) and iPad Air 2 (2014)
- all models of iPad mini from the 1st-gen through 4 (2015)
- all iPad Pro 9.7-in. & 10.5-in., and the 1st- & 2nd-gen 12.9-inch (2015, 2017)
- all models of iPod touch from 5th-gen through 7th-gen (the current model)
*The most vulnerable models in the list above are all those with a processor older than A7 and thus do not include the Secure Enclave, specifically: iPhone 4S, 5, and 5c, iPad 2 through 4th-gen, iPad mini 1st-gen, and all models of iPod touch listed above.
 Warning! These “bargain” devices are unsafe to use online.
Warning! These “bargain” devices are unsafe to use online.
Which iPhones and iPads are safe, if I find a good price?
Even if you’re planning to use an iOS device mostly offline, many modern apps in the App Store will refuse to run on old versions of iOS. So even if you’re not particularly concerned about security, it’s still a good idea to get a device that’s capable of upgrading to iOS 14 or iPadOS 14 (the current operating systems).
Ideally, if you want to buy an Apple mobile device on sale this holiday season, and security and privacy are important to you, you should seek a device that can run iOS 14 or iPadOS 14 and is NOT vulnerable to checkm8. Thus, the following models are currently the safest:
- iPhone XR & XS or later, incl. the 2nd-gen SE (2020)
- iPad 8th-gen (the current model)
- iPad Air 3rd-gen or later
- iPad mini 5th-gen (the current model)
- iPad Pro 3rd-gen or later
Unfortunately, even the current model of iPod touch (7th-gen, released in 2019) is vulnerable to checkm8.
Older Android devices may also be vulnerable
It’s not just Apple devices about which consumers should be cautious.
 If you’re in the market for an Android tablet or smartphone, you may find some that come with Android 7 (Nougat) or older versions that are no longer getting security updates. The current version is Android 11, which may not be compatible with every discounted smartphone or tablet. Check with the device manufacturer to find out whether they support upgrading to the current version of the Android 11 operating system.
If you’re in the market for an Android tablet or smartphone, you may find some that come with Android 7 (Nougat) or older versions that are no longer getting security updates. The current version is Android 11, which may not be compatible with every discounted smartphone or tablet. Check with the device manufacturer to find out whether they support upgrading to the current version of the Android 11 operating system.
Never buy an outdated Wi-Fi router
 Consumers should also be cautious about older models of home Wi-Fi routers, which also tend to go on sale around Black Friday. Your router is hardware that stands between everything on your home network and the public Internet, so it’s critically important to choose a router that won’t put you at risk. Try to choose a brand name that you recognize and trust, if possible. Also, it’s helpful to know that the latest wireless standard is Wi-Fi 6 (802.11ax). Although “AX” router models tend to be more expensive, they’re almost certainly new enough that the manufacturer should still support them.
Consumers should also be cautious about older models of home Wi-Fi routers, which also tend to go on sale around Black Friday. Your router is hardware that stands between everything on your home network and the public Internet, so it’s critically important to choose a router that won’t put you at risk. Try to choose a brand name that you recognize and trust, if possible. Also, it’s helpful to know that the latest wireless standard is Wi-Fi 6 (802.11ax). Although “AX” router models tend to be more expensive, they’re almost certainly new enough that the manufacturer should still support them.
 Not every manufacturer is selling Wi-Fi 6 routers yet, though. The previous wireless standard was 802.11ac Wave 2 (sometimes called Wi-Fi 5), and it’s quite likely that you’ll see a lot of them on sale this year. Be careful, because some “AC” routers may be old models that don’t get firmware updates from the manufacturer anymore, which could make them dangerous to use. For example, avoid getting any Apple AirPort Base Stations (AirPort Express, AirPort Extreme, or AirPort Time Capsule), which Apple no longer sells, never went beyond 802.11ac Wave 1 at best, and last got a firmware update in mid-2019 (about 1.5 years ago).
Not every manufacturer is selling Wi-Fi 6 routers yet, though. The previous wireless standard was 802.11ac Wave 2 (sometimes called Wi-Fi 5), and it’s quite likely that you’ll see a lot of them on sale this year. Be careful, because some “AC” routers may be old models that don’t get firmware updates from the manufacturer anymore, which could make them dangerous to use. For example, avoid getting any Apple AirPort Base Stations (AirPort Express, AirPort Extreme, or AirPort Time Capsule), which Apple no longer sells, never went beyond 802.11ac Wave 1 at best, and last got a firmware update in mid-2019 (about 1.5 years ago).
Many IoT devices have weak security
 Cheap or off-brand “Internet of Things” (IoT) devices—such as Internet-enabled baby monitors, security cameras, coffee makers, and other products that connect to your Wi-Fi network—frequently have poor security. Sometimes they can be easy for hackers to exploit, and in some extreme cases they may wind up getting infected and becoming part of a botnet. In other words, it could become a zombie, part of a legion of compromised devices that does an attacker’s bidding, unbeknownst to you.
Cheap or off-brand “Internet of Things” (IoT) devices—such as Internet-enabled baby monitors, security cameras, coffee makers, and other products that connect to your Wi-Fi network—frequently have poor security. Sometimes they can be easy for hackers to exploit, and in some extreme cases they may wind up getting infected and becoming part of a botnet. In other words, it could become a zombie, part of a legion of compromised devices that does an attacker’s bidding, unbeknownst to you.
As with routers, try to choose brand names you recognize and trust whenever possible, and also try to select products that have a high number of mostly positive reviews. (And, if it’s a product with Internet capabilities that seem much more gimmicky than useful or practical, consider getting a non-connected version instead, or simply don’t connect it to your Wi-Fi network, just to play it safe.)
What’s the takeaway?
If you get nothing else out of this article, please take to heart the following advice:
Resist the urge to buy any Internet-enabled device on impulse. Do your proverbial homework first. Make sure the product and its manufacturer have good reputations and a track record of taking security seriously. Also try to confirm that the device is still receiving frequent firmware or operating system updates from the manufacturer.
If you’re not sure how to research this yourself, a good place to start is to check whether the manufacturer is still advertising or directly selling the device on the official company site. If you’re still uncertain, ask a knowledgeable IT person for help identifying whether or not a product is from a reputable company and likely to be safe.
 Unfortunately, most consumers have little if any concept of how dangerous it is to use products that will have perpetual zero-day vulnerabilities. Using discontinued or unpatched Internet-enabled devices is a bit like driving at high speeds daily without ever wearing a seatbelt; it’s dangerous, and sooner or later, you’re likely to get hurt. That’s why one of our goals at Intego is to help educate consumers and give them the knowledge and tools they need to stay safe online.
Unfortunately, most consumers have little if any concept of how dangerous it is to use products that will have perpetual zero-day vulnerabilities. Using discontinued or unpatched Internet-enabled devices is a bit like driving at high speeds daily without ever wearing a seatbelt; it’s dangerous, and sooner or later, you’re likely to get hurt. That’s why one of our goals at Intego is to help educate consumers and give them the knowledge and tools they need to stay safe online.
And on that note, you can help be part of the solution. Please take a moment to share this article to help your friends and loved ones stay safe!
Intego’s Black Friday deals for 2024
Here are all of our Black Friday deal links for this year—valid from Monday, November 25 through Sunday, December 1, 2024:
- First-time buyers (and past customers with expired subscriptions) can get tremendous savings on Intego’s Mac Premium Bundle X9, the world’s leading Mac antivirus, firewall, and utility suite.
- You can also save on Intego Antivirus for Windows, offered at an astoundingly low price.
- And further protect yourself with Intego Privacy Protection VPN for Mac and Windows using our insanely great discount!
Remember to use these links to maximize your savings, and be sure to share these deals with your friends and family so they can save big as well!
How can I learn more?
For additional tips about shopping safely online, see our related article:
8 essential tips to stay safe shopping online on Cyber Monday and Cyber Week
 On this week’s episode of the Intego Mac Podcast (episode 163), we discussed how to make good choices about buying on-sale electronic devices. Be sure to subscribe to make sure you never miss the latest episode!
On this week’s episode of the Intego Mac Podcast (episode 163), we discussed how to make good choices about buying on-sale electronic devices. Be sure to subscribe to make sure you never miss the latest episode!
Also subscribe to our e-mail newsletter and keep an eye here on The Mac Security Blog for updates.
You can also subscribe to our e-mail newsletter and keep an eye here on The Mac Security Blog for the latest Apple security and privacy news. And don’t forget to follow Intego on your favorite social media channels: ![]()
![]()
![]()
![]()
![]()
![]()
![]()