Viruses, Worms, and Spyware—Oh My! A Look at Malware Terminology
Posted on
by
Kirk McElhearn

When you read about computer security and malware, the terminology can be dizzying. You may feel that you’ve entered a world with some very strange words whose meanings you can only guess at. In order to help you understand malware, here’s a look at the most common terms used to describe malicious software that can harm your computer and mobile device, and threaten your security and privacy.
Read on for a comprehensive look at malware terminology, including viruses, worms, spyware, and all the other dangers that threaten your Mac and your data.
Malware Terminology
Malware is the blanket term for all malicious software. It’s a convenient word, because it can be used for any of the categories I discuss below. Sometimes, a specific piece of malware can be made up of more than one of these categories, so using the blanket term is economical, and makes things easy to understand. In addition, some of these terms describe the way malware is distributed, others the way they propagate, and others the type of actions they perform. Users don’t always need to know exactly what type of malware has infected their device. Since certain terms used to name malware explain how the software is installed, this can be useful to understand how users can protect themselves. (See phishing, Trojan horse, etc.)
What is a Computer Virus?

A virus on a computer is a specific type of malware that self-replicates, like the similarly-named infectious agents in humans and animals. Like a living virus, computer viruses attach themselves to hosts in order to move around and reproduce. The term virus indicates the means of replication, not the way the malware acts on a computer. Viruses used to travel on floppy disks and CD-ROMs; now they move around over the Internet, hiding inside files and applications, or spread via infected USB sticks. The term virus is often used as a blanket term, while the word malware is generally more appropriate. And, because historically viruses were the first type of malware that attacked personal computers, the security industry often uses the term “anti-virus” for software that detects and eradicates malware.
Example: A proof of concept virus, identified as Multi/Clapzok.A, targeted Windows, Linux and OS X 32-bit executables.
What is a Worm?

On a computer, a worm is similar to a virus, in that it replicates itself. But unlike viruses, worms don’t need to be attached to other files. They often replicate over networks, rendering them particularly dangerous.
Example: The “Oompa-Loompa” worm, discovered by Intego on February 16, 2006 and identified as OSX/Oomp.A, targeted Mac OS X users via iChat instant messenger.
What is a Trojan Horse?

A Trojan horse, or simply Trojan, is a type of malware that is disguised as a useful piece of software or data file. It may actually perform actions on a computer that are or seem legitimate, but will install malware or perform malicious actions. A Trojan horse may also be legitimate software that has been altered to install malware. The name comes from the wooden horse that the Greeks made to attack the city of Troy. Obviously, the people in that city didn’t know that they shouldn’t open unsolicited attachments.
Example: The Ventir Trojan, identified by Intego VirusBarrier as OSX/Ventir, used a dropper program (e.g. Trojan horse) to infect Macs.
What is Ransomware?

Ransomware is a type of malware that locks a computer or hijacks a user’s files until a ransom is paid. It can be installed by a Trojan horse, or downloaded when visiting a malicious website. Ransomware is big business, with cyber-criminals making a lot of money from users who need to access their files. These people often have sophisticated fulfillment setups, with call centers and customer support to take payments. The best prevention against ransomware, other than using anti-malware software, is to regularly back up your files, so you always have a copy of them available.
Example: KeRanger, detected by Intego VirusBarrier as OSX/KeRanger, was the first major macOS ransomware.
What is a Botnet?

A botnet is a network of computers whose access has been compromised, and that are controlled remotely. These individual computers are often called bots or zombies. Botnets are generally used to send spam emails, or to launch denial of service attacks, where thousands of computers block a website or server by flooding that server with more requests than it can handle.
Example: iWorm, detected as OSX/iWorm, is a sophisticated botnet that used Reddit to communicate to infected Macs.
What is a Keylogger?

A keylogger, or keystroke logger, is a type of malware that records all keystrokes that a user types on their computer. A keylogger can also be a hardware device, connected somewhere between a keyboard and a computer. Keyloggers can record all sorts of personal information, such as user names, passwords, credit card numbers, and personal documents such as emails and reports. Keyloggers can be useful to obtain information that can be later used to access a user’s online accounts, or for espionage.
Example: Spyware called OSX/Dockster.A included a keylogger component that recorded an affected user’s typing.
What is a Rootkit?

A rootkit is software that gives a malicious user “root access,” or total control over a computer. It can be installed via a Trojan horse, through a phishing attack, or in other ways. A rootkit is a virtual backdoor, and when installed on a computer, malicious users can control the computer and access all its files. Rootkits often mask their presence, or the presence of other malware.
Example: A Trojan dropper threat, detected by Intego VirusBarrier as OSX/Crisis, would drop a rootkit to hide itself.
What is a Backdoor, and What is a RAT?

A backdoor is a way to access a computer or device without authentication. It may provide access to encrypted files without requiring a user’s password or passcode, or it may offer a means of accessing all the files on a computer. In some cases, manufacturers or developers create intentional backdoors so they can restore access to users who are locked out of a system, or to reset a device to factory settings.
A RAT, short for remote administration tool or remote access Trojan, is a type of backdoor that gives an attacker similar remote control, data exfiltration, and spying capabilities, and often includes a keystroke logger.
Example: Mac malware identified as OSX/Eleanor masqueraded as a file converter app and would open a backdoor on infected Macs to steal data, execute code, and more. There are many examples of Mac RATs, such as OSX/CrossRAT (part of a global cyber-espionage campaign) and OSX/EvilOSX (an open-source RAT that anyone can download and customize).
What is Spyware?

Spyware is malicious software that spies on a user. It may record keystrokes (i.e. keylogger) such as user names and passwords, track user activity on the internet, or activate the camera or microphone on a computer to see or hear what the user is doing.
Example: Spyware ported from Windows to OS X, identified as OSX/XSLCmd, included key logging and screen capturing capabilities.
What is Adware?

Adware is software that causes advertisements to be displayed on a computer’s desktop or in a web browser, in order to generate income from these ads being shown. Some free software displays ads, and is technically not adware; the term is generally used for malicious software, which users cannot remove easily.
Example: A shady adware installer, detected as OSX/Okaz.A, was discovered embedded in fake software downloaded from Softonic.
Phishing vs. Spear Phishing

Phishing occurs when cyber-criminals send emails that look exactly like those from real companies—banks, PayPal, Amazon, Apple, and others—to trick you into logging into your account through poisoned links. These links take you to websites that look real, but that are designed simply to harvest your credentials: your user names, passwords, and credit card numbers. Phishing may also take you to a website designed to install malware on your computer, such as ransomware, spyware, adware, and so on.
Spear phishing is a kind of phishing that is generally targeted at a specific person, and isn’t as random as phishing. It purports to come from someone you know: a business you work with, or a person in your contacts. Its goal is, like phishing, to obtain information about you, such as your user name and password to online accounts, or to your user account on your computer.
Example: Scammers found a way to generate a vast number of phishing websites all designed to steal Apple IDs and passwords.
Exploits vs. Vulnerabilities vs. Zero-Day Flaws

An exploit is what malicious users leverage to take advantage of vulnerabilities. It could be a piece of software or code injected into web pages that allows malicious users to gain access to a computer or to its files. Exploits often use vulnerabilities to install malware such as Trojan horses, ransomware, and more.
A vulnerability is a flaw or weakness in an operating system or application that allows malicious users to gain access to a computer, or to infect files. A vulnerability could be the result of a bug or of poor design. Vulnerabilities in web browsers and plug-ins, such as Adobe Flash, are often targeted, since this software is so widely used.
A zero-day vulnerability is one that has been recently discovered, but not yet corrected by a software developer. The term comes from the idea that the developer has zero days to correct the vulnerability before malicious users begin to exploit it. Software updates are required as soon as possible to protect against these vulnerabilities.
Malware vs. Vulnerabilities
The difference between malware and vulnerabilities is the difference between software made with the intent to cause harm, and the absence of security in a product. Malware is something you can see, interact with, and analyze, whereas a vulnerability is a weakness in software or hardware that can be exploited by malware or a hacker. That may sound a bit esoteric, so let’s break down the differences even further.
Take a look at the below infographic for a more detailed look at the differences between malware and vulnerabilities:
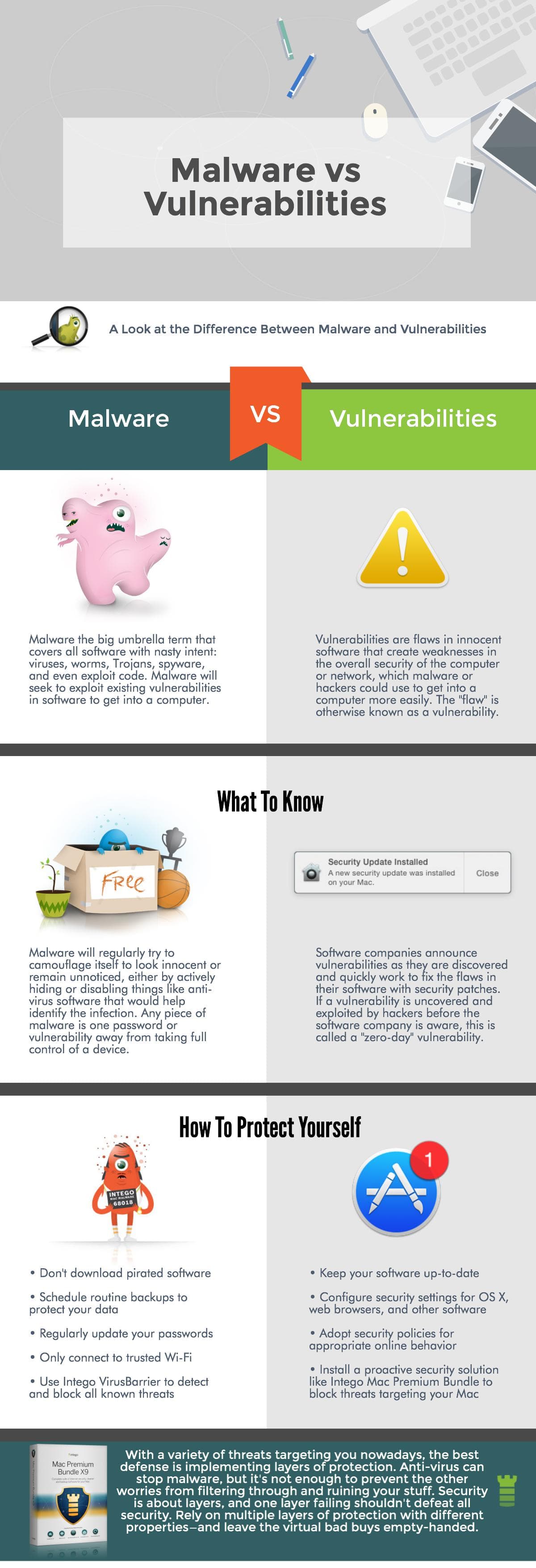
No matter how savvy a Mac user is, any piece of malware is one password or vulnerability away from taking over your machine. Security is about layers, and one layer failing shouldn’t defeat all security; therefore, it’s imperative to rely on multiple layers of protection with different properties. Regularly updating third-party software and passwords, scheduling routine backups, and running a trusted macOS security solution with real-time antivirus protection should be an essential part of your security strategy.
Mac Premium Bundle X9 is the most complete Mac security solution providing multiple layers of protection. It boasts real-time antivirus scanning and anti-phishing features, and a two-way firewall with anti-spyware measures to protect outgoing data sent from your Mac. It even includes a Mac cleaner to optimize your Mac, and Intego Personal Backup for a layer of ransomware protection. Mac Premium Bundle fortifies your Mac with layers of protection against all different types of malware.
This story comes to you as part of our Think Security series helping students and parents prepare for back to school, with educational guides and Mac tips and tricks.