Anti-hack feature comes to iOS 11.4.1… but is it good enough?
Posted on
by
Joshua Long

Earlier this week, Apple released security updates for all of its major operating systems: macOS, iOS, watchOS, and tvOS.
Interestingly, iOS 11.4.1 includes a surprise: USB Restricted Mode—a somewhat controversial security feature that Apple describes in a separate support article.
What Is USB Restricted Mode?
USB Restricted Mode was first introduced in the iOS 12 beta at Apple’s WWDC event in early June. (Related: Why iOS 12 Is Huge for Security and Privacy)
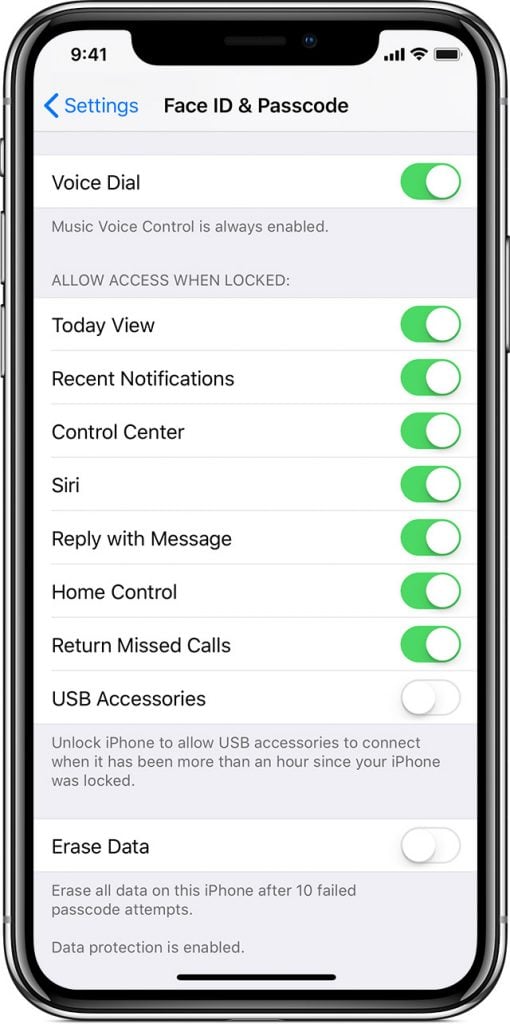
USB Restricted Mode is enabled by default in iOS 11.4.1 and later. Image: Apple
By default, iOS 12—and now iOS 11.4.1—purposely block access to USB devices connected to an iPhone after it has been locked for at least one hour, or if the phone has been put into Emergency SOS mode. After one of those conditions has been met, connecting a device to the Lightning port requires unlocking the phone before the connected device will work.
 Apple made this change to improve the physical security of the iPhone (as well as the iPad and iPod touch). With iOS 11.4 and earlier, it was possible for an attacker to connect a password-cracking tool such as Grayshift’s GrayKey to an iOS device, potentially allowing the attacker to try to brute-force crack the device’s PIN or passcode so that personal data could be extracted from the device.
Apple made this change to improve the physical security of the iPhone (as well as the iPad and iPod touch). With iOS 11.4 and earlier, it was possible for an attacker to connect a password-cracking tool such as Grayshift’s GrayKey to an iOS device, potentially allowing the attacker to try to brute-force crack the device’s PIN or passcode so that personal data could be extracted from the device.
What’s the Controversy?
Although USB Restricted Mode may sound like a great thing to security-conscious consumers and privacy advocates, some worry that the feature could potentially prevent law enforcement agencies from obtaining access to encrypted information on a suspect’s iOS device after having legally obtained a warrant, or to stop an impending terrorist attack.
![]() The GrayKey device in particular is supposedly only sold to law enforcement and intelligence agencies. Grayshift competitor Cellebrite offers a mail-in password cracking service for iOS devices, marketed toward the same audience.
The GrayKey device in particular is supposedly only sold to law enforcement and intelligence agencies. Grayshift competitor Cellebrite offers a mail-in password cracking service for iOS devices, marketed toward the same audience.
Apple maintains that the new feature is designed to defend customers “against hackers, identity thieves and intrusions into their personal data,” and that the company has “the greatest respect for law enforcement, and we don’t design our security improvements to frustrate their efforts to do their jobs.”
But Does USB Restricted Mode Actually Work?
There is some debate, however, about whether USB Restricted Mode actually protects anyone sufficiently at all.
 Digital forensics company ElcomSoft reports that by simply attaching certain dongles to an iOS device’s Lightning port within one hour of the last time the device was unlocked is all it takes to prevent USB Restricted Mode from becoming activated.
Digital forensics company ElcomSoft reports that by simply attaching certain dongles to an iOS device’s Lightning port within one hour of the last time the device was unlocked is all it takes to prevent USB Restricted Mode from becoming activated.
Dongles capable of defeating USB Restricted Mode reportedly include Apple’s own Lightning to USB 3 Camera Adapter, which Apple sells for only US$39. ElcomSoft speculates and plans to confirm that cheaply manufactured third-party products—which they say can cost less than $3—may work just as well.
Depending on the situation, your device may be well enough protected from certain attacks regardless of this workaround. If an attacker steals your phone after it has already been locked for an hour, or if you have a chance to press your iPhone’s Emergency SOS button combination before an attacker can steal the phone or attach a dongle to it, then USB Restricted Mode will engage and you’ll be protected.
For law enforcement and intelligence agencies, there may be yet another loophole that could give them legal permission to start breaking into a device within an hour of the last time it was unlocked. Data recovery company DriveSavers recently reported that agencies can search a device without a warrant if there are “exigent circumstances,” meaning that a reasonable person would conclude “that a warrantless search or entry… was necessary to prevent physical harm to the officers or other persons, the destruction of relevant evidence, the escape of a suspect, or some other consequence improperly frustrating legitimate law enforcement efforts.”
 We’ve talked about iPhone password cracking, Cellebrite, GrayKey, USB Restricted Mode, and related topics on several recent episodes of the Intego Mac Podcast: March 7, April 27, July 6, and July 13. Be sure to subscribe to make sure you don’t miss future discussions on this topic.
We’ve talked about iPhone password cracking, Cellebrite, GrayKey, USB Restricted Mode, and related topics on several recent episodes of the Intego Mac Podcast: March 7, April 27, July 6, and July 13. Be sure to subscribe to make sure you don’t miss future discussions on this topic.
Other New Apple Security Updates
 Aside from iOS 11.4.1 and other OS updates, Apple also released updates for Safari for Mac, as well as the company’s notable Windows software: iTunes and iCloud for Windows, as well as Wi-Fi drivers for Boot Camp which finally mitigate the KRACK vulnerabilities that came to light way back in October 2017.
Aside from iOS 11.4.1 and other OS updates, Apple also released updates for Safari for Mac, as well as the company’s notable Windows software: iTunes and iCloud for Windows, as well as Wi-Fi drivers for Boot Camp which finally mitigate the KRACK vulnerabilities that came to light way back in October 2017.
For more technical details about the vulnerabilities patched in the latest security updates, you can review the following Apple support articles:
- Wi-Fi Update for Boot Camp 6.4.0
- iOS 11.4.1
- tvOS 11.4.1
- watchOS 4.3.2
- macOS High Sierra 10.13.6, Security Update 2018-004 Sierra, Security Update 2018-004 El Capitan
- Safari 11.1.2
- iCloud for Windows 7.6
- iTunes 12.8 for Windows
How Can I Learn More About Apple Security?
Whenever there’s something noteworthy about an Apple security update, or any other Apple-related security news worth mentioning, Intego has you covered! Be sure to subscribe to The Mac Security Blog, the Intego Mac Podcast, and the Intego YouTube channel to stay informed about the latest Apple security news.
GrayKey photo via Thomas Reed.