Apple + Intego + Recommended + Security & Privacy
A look back at the top Mac security stories of 2017
Posted on
by
Joshua Long

So much happened in the realm of Apple security this past year! We’re still catching up after all the major goings-on this month (which we’ll cover soon in our January month in review) and we’ve finally found the time to publish our year-in-review article in which we look back at the top Mac security stories of 2017.
Read on to learn about the worst Mac threats that emerged this past year—we’ve hand-picked two major stories from each month in 2017—along with some honorable mentions of impactful Mac security news you may have missed.
January
Main article: Month in Review: Apple Security in January 2017
 New Mac Malware: ClientCapture/Fruitfly Discovered
New Mac Malware: ClientCapture/Fruitfly Discovered
A university IT administrator found some strange network traffic coming from a Mac Pro, and found some previously unknown Mac malware. Evidently installed as part of a targeted attack, the malware (variously known as ClientCapture, Fruitfly, and Quimitchin) may have existing on the university’s computer for years before being discovered.
“Meitu” Mobile App Has Privacy Risks
Meitu, a seemingly innocuous iOS app that transformed selfies into “paintings” with large eyes, made its way into the App Store years ago, but rose in popularity in January.
![]() At the height of its popularity, researcher Jonathan Zdziarski discovered that it contained “at least half a dozen” analytics and tracking packages, implying that the Chinese developers may have been selling data about the app’s users without their knowledge.
At the height of its popularity, researcher Jonathan Zdziarski discovered that it contained “at least half a dozen” analytics and tracking packages, implying that the Chinese developers may have been selling data about the app’s users without their knowledge.
This was a good reminder that just because an app is in the App Store doesn’t necessarily mean that it respects your privacy.
February
Main article: Month in Review: Apple Security in February 2017
New Mac Malware: Filecoder/Findzip Ransomware, Sofacy XAgent, iKitten, EmPyre Word Macro, PROTON RAT
A virtual tital wave of Mac malware spilled forth in February, with brand new ransomware disguising itself as an Adobe Premiere Pro CC or Microsoft Office 2016 crack, Fancy Bear APT-related malware, Keychain-stealing iKittens, a Microsoft Word macro virus, and a remote access Trojan (RAT) found on a Russian cybercrime message board.
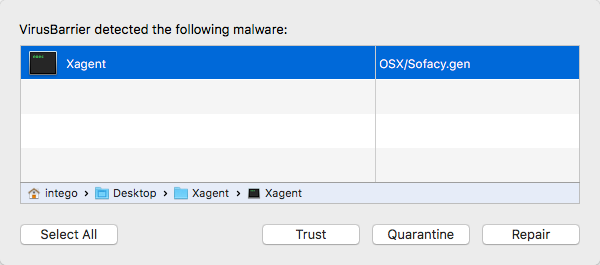
Intego VirusBarrier detects Sofacy XAgent
iCloud Was Storing “Deleted” Safari History
Forbes revealed that a tool called Phone Breaker, developed by a company in Russia, could recover ostensibly deleted Safari browser history from as far back as November 2015. Shortly after the Forbes article was published, known-affected iCloud accounts began to have their old “deleted” Safari browsing history actually disappear, presumably because Apple had begun cleaning out the old data that Phone Breaker had been able to dredge up.
March
Main article: Month in Review: Apple Security in March 2017
 WikiLeaks’ Vault 7 and DarkMatter Disclosures
WikiLeaks’ Vault 7 and DarkMatter Disclosures
WikiLeaks published alleged U.S. Central Intelligence Agency documents containing attacks against software and hardware from the likes of Apple, Cisco, Google, Microsoft, and Samsung, some of which were supposedly used by the CIA a decade or longer ago.
Reportedly the leaks showed that the CIA had allegedly at one point been in development of iPhone and Mac rootkits. By the time the alleged leaked documents were revealed to the public, Apple had already patched many of the vulnerabilities described therein.
Mac Hackers Get Root at Pwn2Own
Each year at the CanSecWest security conference, hackers compete for cash prizes and geek cred in the Pwn2Own hacking competition.
Awesome pwnage with @_niklasb #pwn2own 🙂 pic.twitter.com/Zk0empswbW
— Samuel Groß (@5aelo) March 15, 2017
On the first day of Pwn2Own, researchers Samuel Groß and Niklas Baumstark chained together multiple exploits to “get root” (obtain full administrator privileges) on a MacBook Pro, and they earned style points by displaying “pwned by niklasb & saelo” across the Touch Bar.
April
Main article: Month in Review: Apple Security in April 2017
Unofficial App Store Hidden in an App Store App
An unofficial app store was reportedly available within an app in Apple’s official App Store.
A Japanese-language app that claimed to have been a household financial helper program was, in fact, a subversive way of getting an unofficial Mandarin Chinese-language app store past Apple’s vetting process, and it allowed modified or unauthorized apps to be installed without jailbreaking.
Like the Meitu app back in January, this was a second example showing that one should exercise caution even when installing apps from the App Store; Apple doesn’t necessarily catch everything that may be hiding within an app.
Unicode Implementation Issue Facilitates Phishing
Many major Web browser apps, including Firefox, Chrome, and Opera, were displaying internationalized domain name (IDN) characters in a way that could allow attackers to register a domain such as xn--80ak6aa92e.com and have it appear in the address bar as apple.com, for example.
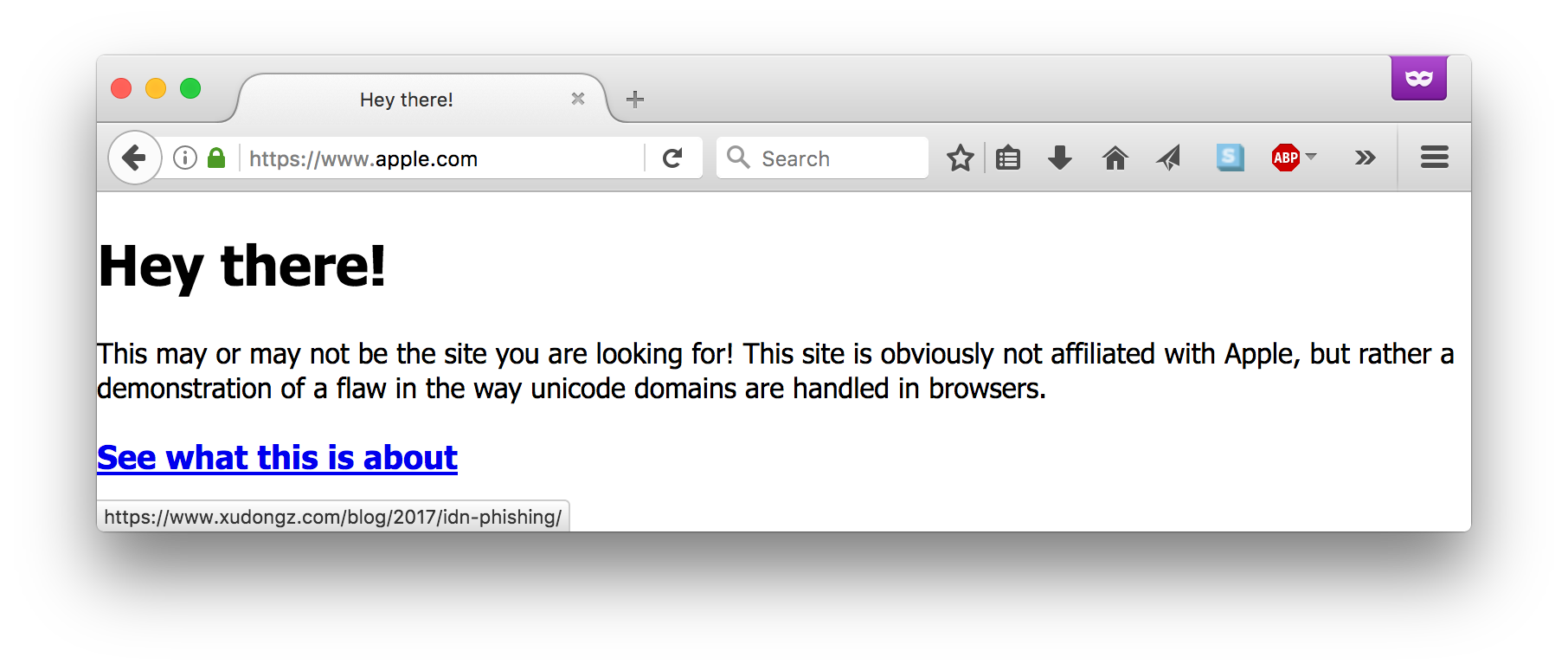
Firefox displays this site as “apple.com” rather than “xn--80ak6aa92e.com”
Chrome and Opera have both changed the way they display such domain names to help avoid phishing attacks. Safari was never affected. Firefox, however, continues to display similar domain names in a misleading way by default—even in 2018; see the steps outlined in our April 2017 article to learn how to change that behavior.
(Runner Up) Find My Mac Easily Disabled with Physical Access
Honorable mention goes to a report from The Mac Observer that Apple’s Find My Mac feature could be easily bypassed by simply restarting a Mac holding down Command-Option-P-R. To prevent a thief from being able to disable Find My Mac using this method, you can set a firmware password (https://support.apple.com/en-us/HT204455) that you’ll have to type each time you boot your Mac.
May
Main article: Month in Review: Apple Security in May 2017
New Mac Malware OSX/Proton.B Distributed Via HandBrake Download Server
 The official download server of video-encoding software Handbrake was compromised, and the official Handbrake site distributed a Trojanized version of the software for about five days.
The official download server of video-encoding software Handbrake was compromised, and the official Handbrake site distributed a Trojanized version of the software for about five days.
The infected version of Handbrake prompted users to enter a password to “install additional codecs,” and if users fell victim, a malicious payload was installed instead. That payload would then send a copy of the user’s Keychain and sensitive browser data to the perpetrator behind the malware.
Other New Mac Malware: OSX/Dok Distributed Via Phishing Campaign; “Snake” Ported from Windows
OSX/Dok was new malware that was distributed via e-mail attachments. It came in two forms: the first variant was designed to spy on a victim’s Internet traffic, and the second variant was a full-fledged remote access Trojan (RAT) that attempted to steal Keychains, iOS backups, iMessage chat history, and more from infected Macs. Both malware variants are detected and eradicated by Intego VirusBarrier as OSX/Dok.A and OSX/Dok.B.
 Malware known by the names Snake, Turla, and Uroburos was ported from Windows to Mac. The Mac version of the malware was found inside a compromised Abode Flash Player installer.
Malware known by the names Snake, Turla, and Uroburos was ported from Windows to Mac. The Mac version of the malware was found inside a compromised Abode Flash Player installer.
June
Main article: Month in Review: Apple Security in June 2017
New Mac Ransomware and Spyware — as a Service
A site on the Dark Web was discovered that enabled would-be attackers to purchase off-the-shelf spyware or ransomware and tailor it to their own desires. Intego detects the malware as OSX/MacSpy.A and OSX/MacRansom.A, respectively.
New Mac Malware: OSX/OceanLotus Returns with New Variant
OceanLotus is corporate and industrial espionage malware that originated on Windows in 2015, and later came to Mac in 2016. In June 2017, a new Mac version was found that disguised itself as a Microsoft Word .docx document.
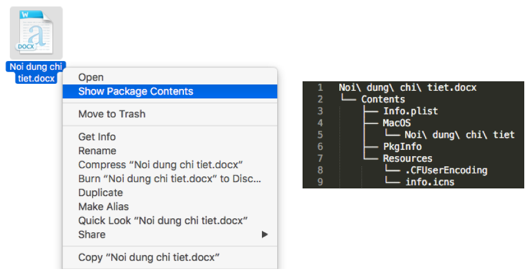
Look out! That’s a malicious app, not a Word file. Image credit: Palo Alto Networks
(Runner Up) Scam Software Reportedly Earned Huge Revenue in iOS App Store
Honorable mention goes to a report published on Medium alleging that nefarious iOS developers had been getting fishy apps past App Store reviewers, gaming Apple’s advertising system, and then scamming App Store customers into incredibly expensive, auto-renewing, questionable services.
This was a third example in 2017 that clearly demonstrates that users cannot simply trust everything they find in the App Store.
July
Main article: Month in Review: Apple Security in July 2017
New Mac Malware: OSX/FruitFly.B and OSX/FlashyComposer.A
New variants of the Fruitfly malware were discovered in the wild with the capabilities of taking screenshots, recording keystrokes, taking pictures with the webcam, and more.
Backdoor malware originally discovered in 2013 dubbed OSX/Leverage also resurfaced, and is detected under the new name OSX/FlashyComposer due to its new delivery method, being disguised as an Adobe Flash Player installer.
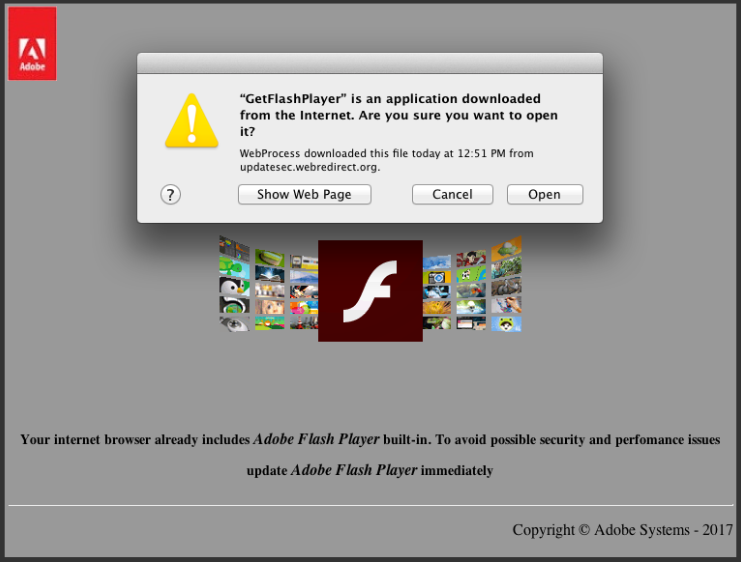
The malicious code attempts to download and install a fake Flash update. Image credit: Volexity.
Apple Mitigates Broadpwn for iOS and macOS Sierra
Apple patched the Broadpwn vulnerability, a memory corruption issue that could allow a nearby attacker to exploit a flaw in Broadcom wireless hardware to execute arbitrary code on the wireless chip.
The bug was patched for macOS Sierra and the latest versions of iOS, watchOS, and tvOS. However, Apple opted to not patch Broadpwn for the two previous versions of macOS at the time: El Capitan and Yosemite. This has been a disturbing trend for Apple, delaying or avoiding patching certain serious vulnerabilities for the two previous versions of macOS that are ostensibly still receiving security updates.
Apple didn’t patch Broadpwn for its AirPort wireless base station products until December 2017.
August
Main article: Month in Review: Apple Security in August 2017
Touch ID Secure Enclave Processor Firmware Allegedly Decrypted
A hacker claimed to have decrypted and then published online the firmware for Apple’s Secure Enclave Processor (SEP), along with the decryption key and tools for working with them.
An Apple spokesperson sought to ease fears about fingerprints and passwords stored on devices with Touch ID potentially being less safe, stating, “There are a lot of layers of security involved in the SEP, and access to firmware in no way provides access to data protection class information.”
New Mac Malware: OSX/Pwnet.A, OSX/Mughthesec.A
A supposed hack for a Counter-Strike game turned out instead to be OSX/Pwnet.A, malware that installed a cryptocurrency miner.
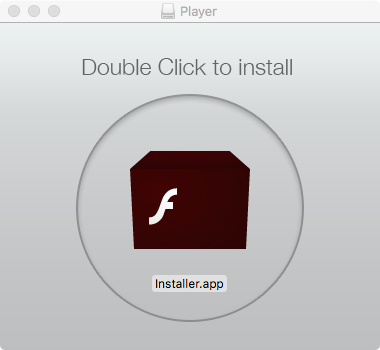
Mughthesec masquerades as a Flash Player installer. Image credit: Patrick Wardle
OSX/Mughthesec.A was new malware disguised as a Flash Player installer. What it actually did was install adware and other potentially unwanted programs on a victim’s Mac.
September
Main article: Month in Review: Apple Security in September 2017
Major vulnerabilities that affected Apple products: BlueBorne, DolphinAttack
An IoT security company published information about serious Bluetooth vulnerabilities collectively dubbed BlueBorne.
Apple devices running the latest versions of iOS or tvOS, or any version of macOS or watchOS, are not known to be vulnerable to BlueBorne attacks. However, several old models of iPhone, iPad, iPod touch, and Apple TV that cannot be upgraded to the latest version of iOS or tvOS remain vulnerable to exploitation.
Six researchers at a Chinese university found that all of the biggest-name speech recognition systems on the market, including Apple’s Siri, were vulnerable to something the researchers called DolphinAttack: playing back spoken commands in an inaudibly high pitch so as to have them executed via “Hey Siri” without the user even being aware of it.
macOS High Sierra also launched with serious vulnerabilities of its own (in SKEL, Keychain)
Mac security researcher Patrick Wardle found two serious vulnerabilities in the newly released macOS High Sierra: a flaw in a new feature called User-Approved Kernel Extension Loading, as well as a vulnerability that could allow malware to steal all of a user’s Keychain passwords; Apple patched the latter bug in October.
Later in the year, we would learn of other serious vulnerabilities that were High Sierra exclusives, including multiple password vulnerabilities exploitable through System Preferences.
(Runner Up) Your Mac’s Firmware May Be Outdated

These Macs are more likely to have outdated firmware. Images: Apple via EveryMac
Honorable mention goes to a report from Duo Security warning that many Macs’ firmware was outdated. Apple bundles EFI firmware updates with macOS updates, but sometimes the firmware update procedure fails and leaves Macs with an outdated version that may contain security vulnerabilities. Duo Security released an app called EFIgy to help users assess the state of their Macs’ UEFI firmware.
October
Main article: Month in Review: Apple Security in October 2017
Wi-Fi KRACK Attacks affect Apple products
 A security researcher found a number of related Wi-Fi vulnerabilities collectively called KRACK Attacks (short for key reinstallation attacks) that could allow an attacker to glean information from nearby Wi-Fi networks.
A security researcher found a number of related Wi-Fi vulnerabilities collectively called KRACK Attacks (short for key reinstallation attacks) that could allow an attacker to glean information from nearby Wi-Fi networks.
Many Apple products were affected, and Apple released patches for its operating systems at the end of October. However, Apple waited until December to finally mitigate against KRACK Attacks for its AirPort wireless base station products (along with certain specific models of iOS, tvOS, and watchOS products).
Eltima Software Infected with OSX/Proton.C Malware
Following in the footsteps of Handbrake in May (and Transmission twice in 2016), yet another software developer’s download server was compromised in October and began distributing Trojanized versions of the company’s software.
 Eltima Software’s Elmedia Player and Folx were found to temporarily contain a new variant of OSX/Proton malware that could give the attacker control over an infected Mac and steal the victim’s passwords, cryptocurrency wallets, browsing history and login data, and more.
Eltima Software’s Elmedia Player and Folx were found to temporarily contain a new variant of OSX/Proton malware that could give the attacker control over an infected Mac and steal the victim’s passwords, cryptocurrency wallets, browsing history and login data, and more.
(Runner Up) iOS developer warns of two potential attacks
Honorable mention goes to iOS developer Felix Krause’s warnings about two potential concerns with iOS devices: the ability for apps to replicate the appearance of Apple ID authentication dialog boxes (which could aid in phishing attacks) or to secretly spy on a user via the device’s camera whenever an app is in the foreground.
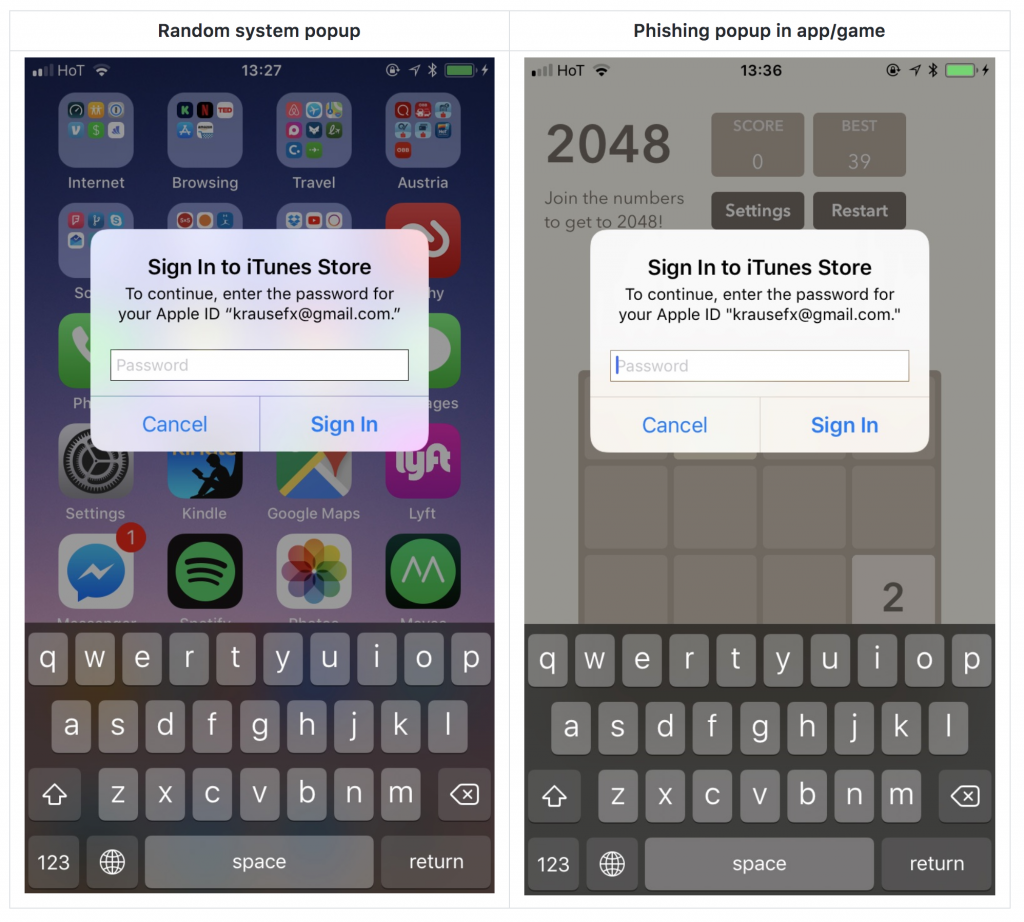 iOS apps can maliciously simulate Apple ID prompts. Image: Krause
iOS apps can maliciously simulate Apple ID prompts. Image: Krause
Also, Intego launched a new audio podcast (the Intego Mac Podcast) as well as a new YouTube video series in October; be sure to subscribe if you haven’t already!
November
Main article: Month in Review: Apple Security in November 2017
 I Am Root: Major Root-Access Flaw in High Sierra
I Am Root: Major Root-Access Flaw in High Sierra
A serious vulnerability was discovered in macOS High Sierra that could allow a local attacker with physical access to a Mac (and in some cases, even attackers with remote access over a network) to enable the Mac’s “root” account (a powerful UNIX administrator account that’s disabled by default in macOS) with a password of the attacker’s choosing.
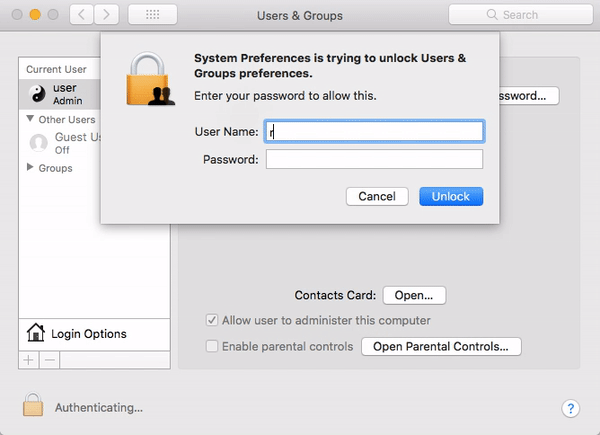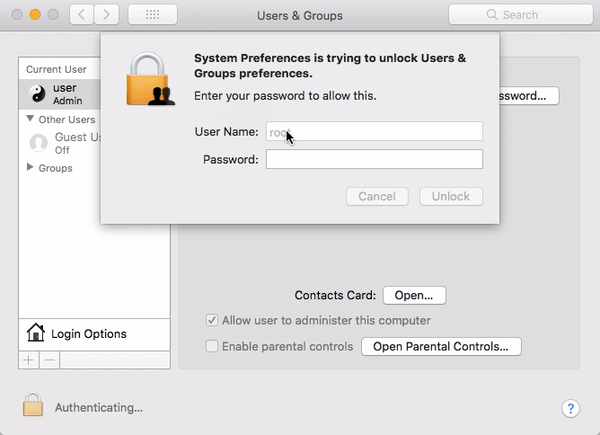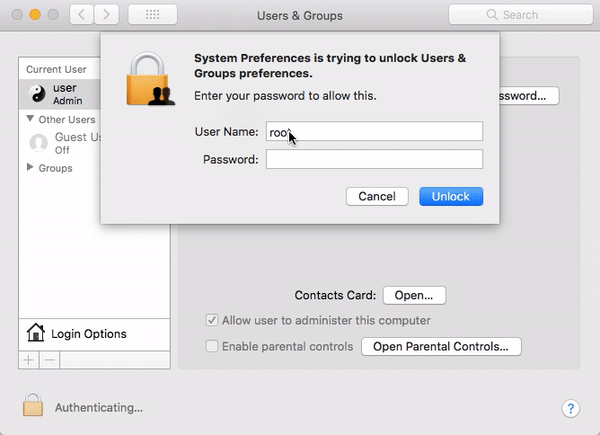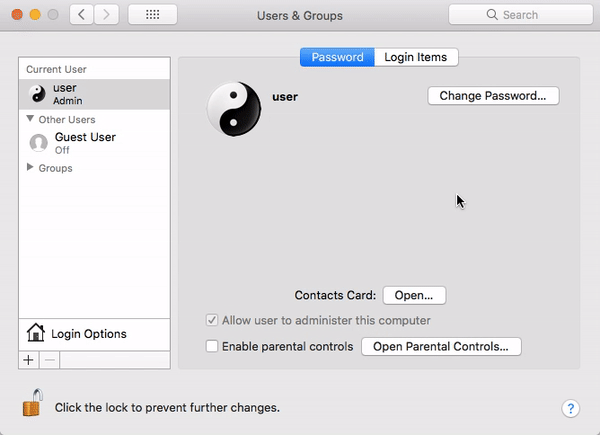 The “I am root” attack in action. Image credit: Patrick Wardle
The “I am root” attack in action. Image credit: Patrick Wardle
Apple rushed to mitigate the flaw, pushing a patch to all Internet-connected macOS High Sierra users, but in its haste Apple made some errors that had to be rectified in future patches.
Face ID Fooled By Hackers… and a 10-Year-Old Boy
Two stories surfaced in November claiming that the iPhone X’s new Face ID technology had been successfully tricked into unlocking Apple’s latest smartphone.
Vietnamese hackers released two proof-of-concept videos showing masks they made that were able to successfully fool an iPhone X into unlocking. This is particularly interesting given that when Apple introduced the iPhone X, Apple executive Phil Schiller took the stage and bragged that Apple had tasked Hollywood mask-making experts with trying to fool Face ID, and their efforts had been unsuccessful; apparently they just hadn’t been trying the right methods.
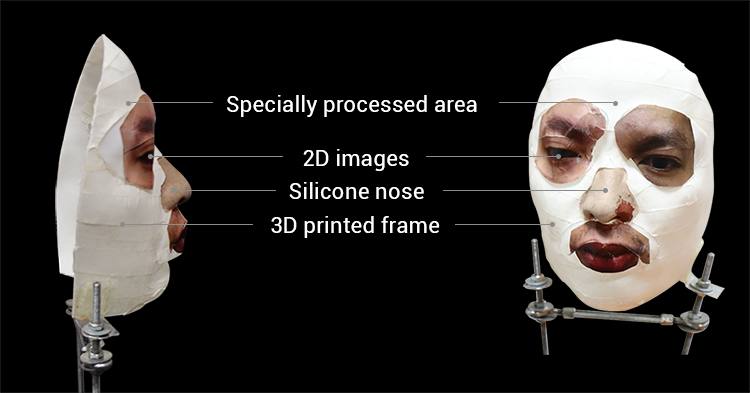 This mask can allegedly bypass Face ID. Image credit: BKAV via CNET
This mask can allegedly bypass Face ID. Image credit: BKAV via CNET
As seen in a viral video, a ten-year-old boy successfully unlocked his mother’s iPhone X because Face ID evidently thought they were the same person. Apple’s Schiller admitted during the iPhone X unveiling keynote that there’s a higher probability of false matches for people who have “a close genetic relationship” with the user.
(Runner Up) Proton Malware Masquerades as Anti-Virus
Honorable mention goes to the story of a fake antivirus blog that distributed a new variant of the OSX/Proton malware.
 This time, rather than Proton being injected into another developer’s legitimate app and download server, the Proton malware spread via a fake anti-virus app, called “Symantec Malware Detector,” distributed via a fake security blog.
This time, rather than Proton being injected into another developer’s legitimate app and download server, the Proton malware spread via a fake anti-virus app, called “Symantec Malware Detector,” distributed via a fake security blog.
December
Main article: Month in Review: Apple Security in December 2017
“IOHIDeous” Mac Zero-Day Dropped New Year’s Eve
On the last day of 2017, a security researcher dropped a macOS zero-day vulnerability that’s believed to have been around for more than fifteen years, existing in numerous Mac OS X, OS X, and macOS releases.

IOHIDeous logo. Image credit: Siguza
In order for an attacker to take advantage of the bug (dubbed “IOHIDeous”), they would reportedly either need local access to a victim’s Mac, or to have previously compromised a victim’s Mac.
Apple would later patch the vulnerability in January, but only for the current and two previous versions of macOS (High Sierra, Sierra, and El Capitan). Previous versions of the Mac operating system remain vulnerable.
Apple Updates Everything (Even AirPort)
 Apple finally released firmware updates for its AirPort wireless networking products to mitigate the Broadpwn and KRACK Attack vulnerabilities that had been known to the public for months.
Apple finally released firmware updates for its AirPort wireless networking products to mitigate the Broadpwn and KRACK Attack vulnerabilities that had been known to the public for months.
Apple also issued KRACK mitigations for certain specific models of iOS, tvOS, and watchOS products that for some reason had been excluded from October’s KRACK updates.
Although Meltdown and Spectre would not become public knowledge until January 2018, Apple also released mitigations for the Meltdown speculative execution vulnerability in its December updates for macOS High Sierra, iOS 11, and tvOS 11 (Apple said that “watchOS did not require mitigation” for Meltdown).
Additional Coverage
Of course, all of the above only scratches the surface; there’s plenty more that happened in 2017 that we can’t cover in this article. In addition to the links above to each month’s full list of stories, here are some additional year-in-review articles from other sources, covering either Mac security, cybersecurity in general, or Apple news from 2017:
- Objective-See: “Mac Malware of the Year”
- ZDNet: “10 things in cybersecurity that you might have missed this year”
- CSO Online: “2017 Threat Trends – The Year in Review”
- AppleInsider: “Apple 2017 Year in Review” article series
Stay Tuned! Subscribe to The Mac Security Blog
Be sure to subscribe to The Mac Security Blog to stay informed about Apple security throughout each month.
Also, each week we discuss Mac and iOS security news and other topics of interest on the Intego Mac Podcast. You’ll want to subscribe in iTunes/Podcasts to make sure you don’t miss any shows! Show notes are available at podcast.intego.com.
Last but not least, be sure to subscribe to the Intego YouTube channel to get monthly updates in video form, and click on YouTube’s bell icon (🔔) so you’ll get notified when each new episode is available.
Fruit fly photo: Arian Suresh (CC BY 2.0). “I am root”/Groot cartoon image credit: Johnathon Burns modified by Gaël. For additional image credits, please see the captions above and/or the linked Intego articles.