Month in Review: Apple Security in June 2017
Posted on
by
Joshua Long

June 2017 was another interesting month for Mac malware! Read on for more details.
New Mac Ransomware and Spyware — as a Service
In late May, a security researcher discovered new sites on the “Dark Web” (that is, sites only accessible via the Tor network) that offered Mac spyware and Mac ransomware “as a service.”
What exactly is malware as a service? Essentially, the idea is that a developer of malware takes the time to create, market, and sell some malware, so that anyone who’s willing to pay for it can theoretically use it to spy on someone’s computer or share in ransomware profits. Engaging in such behavior is, of course, illegal in many jurisdictions.
MacSpy (Spyware as a Service)
The first Mac “as-a-service” malware to be discovered was MacSpy, which is advertised as a remote access Trojan (RAT) that gives an attacker the ability to take screenshots, record audio, retrieve clipboard contents, steal photos synchronized from an iPhone via iCloud, and log keystrokes on a victim’s Mac (although the latter functionality requires the attacker to know the victim’s sudo password).

MacSpy’s homepage mimics Apple’s. Image credit: Alien Vault
For a detailed analysis of the MacSpy malware, see Alien Vault’s blog post.
Intego VirusBarrier anti-virus detects “MacSpy” as OSX/MacSpy.A.
MacRansom (Ransomware as a Service)
Shortly after MacSpy was discovered, the same researcher found “MacRansom” advertised through a nearly identical Dark Web site. As you might guess from the name, the idea is that the ransomware encrypts files on the victim’s Mac, and then demands payment from the victim if they want to recover their files.
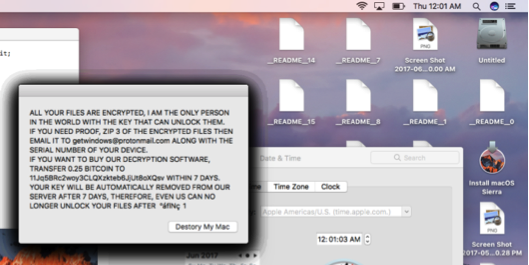
OSX/MacRansom encrypts files and demands payment. Image credit: Fortinet
For detailed analyses of the MacRansom malware, see Patrick Wardle’s Objective-See blog post and Fortinet’s blog post.
Intego VirusBarrier anti-virus detects “MacRansom” as OSX/MacRansom.A.
New Mac Malware: Variant of OSX/OceanLotus
 The “OceanLotus” malware first came on the scene in May 2015, and in February 2016 Intego reported on a version that was distributed via a fake Adobe Flash Player installer.
The “OceanLotus” malware first came on the scene in May 2015, and in February 2016 Intego reported on a version that was distributed via a fake Adobe Flash Player installer.
The OceanLotus malware was the first Mac version of its Windows counterpart that had been found in 2015. Used for corporate and industrial espionage, it found its way to the target via social engineering and the use of watering hole attacks. Once installed, the Trojan was able to take screenshots, get information on which windows were open, processes running, download files, modify files, and more. The Command & Control (C&C) server was ultimately shut down and after some time its very existence was mostly forgotten; that is, until now.
As reported by researchers at Palo Alto Networks (PAN), OceanLotus is back, this time with the installer package disguised as a password-protected Microsoft Word document.
When a victim double-clicks on what appears to be a .docx file (which is actually an application), the victim’s computer becomes compromised, and the malware replaces the fake Word file with an actual Word file and opens it. Although the malware is now embedded in the victim’s Mac, no obvious trace of it is left behind for the victim to discover later.
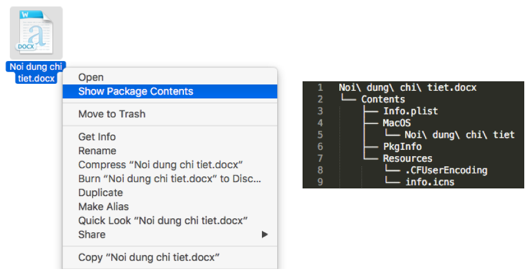
Look out! That’s a malicious app, not a Word file. Image credit: Palo Alto Networks
The level of sophistication of these and other aspects of the new OceanLotus variant suggest that this isn’t your run-of-the-mill Mac malware. According to PAN, “we have now observed multiple espionage motivated threat actors targeting macOS. It is imperative that the same types of strong security practices and policies organizations use to defend Windows devices are applied universally to include macOS devices as well.” We agree with that assessment.
For a detailed analysis of the new OceanLotus malware variant, see PAN’s blog post.
Intego VirusBarrier detects the new sample as OSX/OceanLotus.
Scam Software Reportedly Earned Huge Revenue in iOS App Store
A recent article on Medium claimed that nefarious iOS developers had been somehow getting fishy apps past App Store reviewers, gaming Apple’s advertising system, and then scamming App Store customers into incredibly expensive, auto-renewing, questionable services.

Scam software made it to #10 in Apple’s Top Grossing list. Image credit: Johnny Lin, Medium
One notable example was a supposed VPN service that charged a recurring $99.99 every 7 days if the user laid their finger on the Touch ID sensor (whether or not they had time to read the fine print). That particular app made it to the #10 position in the Top Grossing section of the App Store, with an estimated revenue of U.S. $80,000 per month. This apparently went largely unnoticed for a couple months.
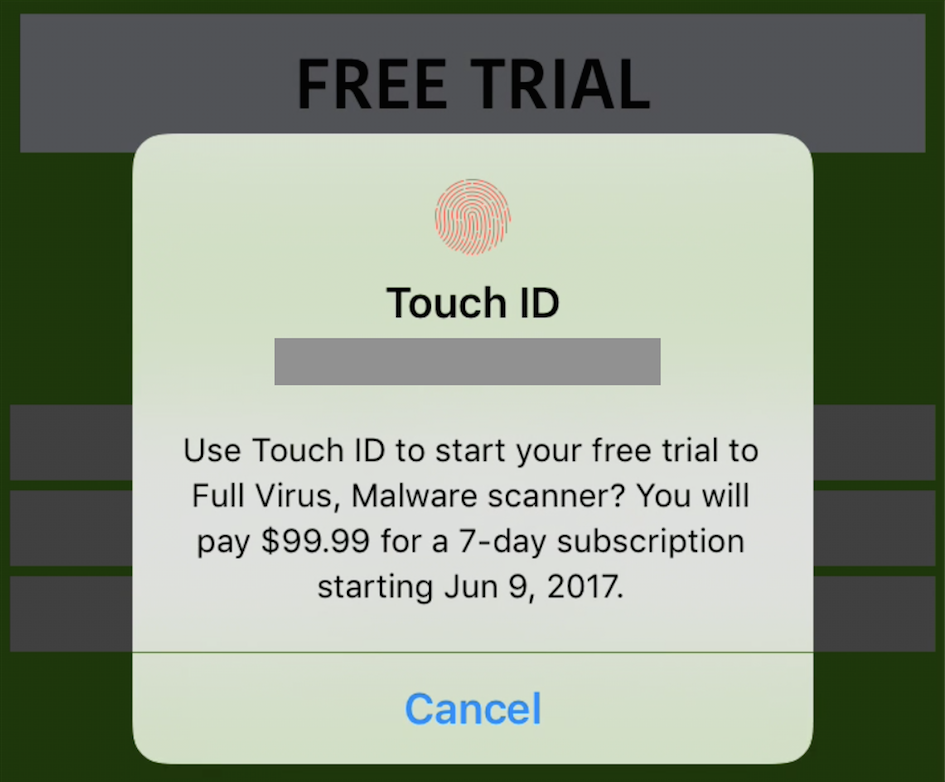
Be sure to read Touch ID prompts carefully. Image credit: Johnny Lin, Medium
The article is still an interesting read, even though Apple seems to have taken action to clean up the App Store, at least for now; no obvious scam apps are currently among the top-grossing 200 apps in the U.S. iOS App Store as of today. Nevertheless, it’s a good reminder to be vigilant when installing any third-party software, even if it comes from Apple’s Mac or mobile App Stores. If an app looks fishy, don’t download it, and if you have reason to believe it’s malicious, report it to Apple.
Other Security News
In brief, June has also brought some other interesting (although not necessarily Apple-related) security news:
* The WannaCry ransomware is still alive as news surfaced of yet another nasty piece of ransomware, called Petya. With the help of the same Windows vulnerability that WannaCry abused, “[Petya] spreads in internal networks with WMIC and PSEXEC,” Mikko Hypponen confirmed.
We are aware of a major Windows #ransomware, #Petya. Intego VirusBarrier detects this as W32/Petya. Related details: https://t.co/dPU3j5bZUE
— Intego Mac Security (@IntegoSecurity) June 27, 2017
* According to Ars Technica, a new Vault 7 leak claims that the U.S. Central Intelligence Agency (CIA) has had the ability to infect home routers from manufacturers such as Belkin, D-Link, and Linksys for the past decade.
* The U.S. National Security Agency (NSA) has officially launched its own public Github source code repository.
Stay Tuned! Be sure to subscribe to The Mac Security Blog to stay informed about Apple security throughout each month. If you missed Intego’s previous Apple security news roundups for 2017, you can check them out here.
Have something to say about this story? Share your comments below!