Month in Review: Apple Security in February 2017
Posted on
by
Joshua Long

Another month, another round of Apple security news. Like last month, February has certainly kept the news coming—this time including a tidal wave of new malware designed to infect Macs.
New Mac Malware: Filecoder/Findzip Ransomware
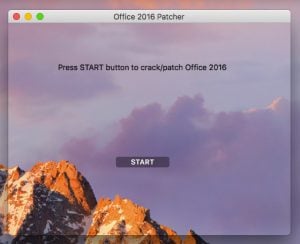
Yesterday the story broke that a new ransomware Trojan horse affecting Macs is out there in the wild. Called OSX/Filecoder by Intego and OSX.Findzip.A by Apple, the malware masquerades as a “patcher” or cracking tool for illegally unlocking unlicensed copies of Adobe Premiere Pro CC or Microsoft Office 2016.
Whilst the Trojan horse app pretends to do some mysterious cracking magic, instead it surreptitiously encrypts all of the user’s documents, after which read-me files are dropped onto the desktop requesting payment of a multi-hundred dollar ransom to recover the user’s files.
Check out Intego’s write-up for more details: Patcher Ransomware Attacks macOS, Encrypts Files Permanently.
New Mac Malware: Sofacy XAgent
The biggest buzz in Mac malware this month involved a backdoor associated with a group known variously as Sofacy, APT28, and Fancy Bear. The malware itself is dubbed OSX/Sofacy.gen by Intego, and OSX.XAgent.A by Apple. If a Mac has previously been infected by Sofacy’s malware known as Komplex, that malware may download and install XAgent as a secondary infection.
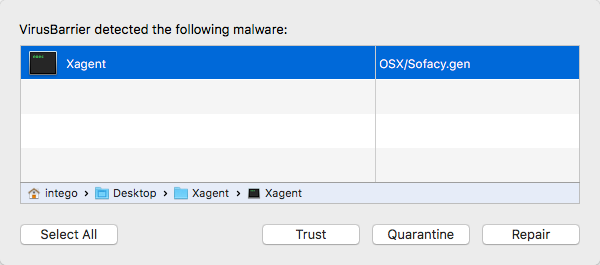
Intego VirusBarrier detects Sofacy XAgent
XAgent includes functions to allow an attacker to do just about anything with your Mac, including but not limited to logging everything you type (including your passwords), automatically taking a screenshot every ten seconds, stealing iPhone and iPad backups, and accessing the command shell (effectively equivalent to typing commands into your Mac’s Terminal app).
For further details on this malware, see Intego’s article: Komplex Malware: The Return of Sofacy’s XAgent.
New Mac Malware: iKittens
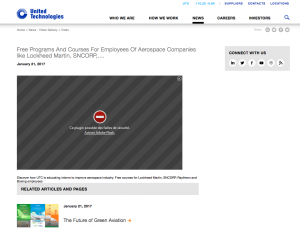 Earlier this month, a report was published describing Mac malware called MacDownloader or OSX.iKitten.A. The malware was targeted at the United States defense industry, and was distributed through a site that impersonated an aerospace firm (as depicted in the screenshot; image credit: Iran Threats).
Earlier this month, a report was published describing Mac malware called MacDownloader or OSX.iKitten.A. The malware was targeted at the United States defense industry, and was distributed through a site that impersonated an aerospace firm (as depicted in the screenshot; image credit: Iran Threats).
The deceptive page pushes a fake Flash Player installer that infects the victim’s Mac with iKitten malware, after which iKitten attempts to upload a copy of the user’s Keychain (which contains a user’s saved passwords) to a site maintained by the malware developer.
The malware itself is poorly written and doesn’t seem to persist in memory after a reboot, but by the time a user reboots their system, their passwords may have already been stolen.
New Mac Malware: EmPyre Word Macro
If you’ve been around long enough, you may remember hearing about Microsoft Office macro viruses nearly two decades ago. Around that time, Word and Excel macro viruses (that is, Microsoft Office documents containing malicious scripts that automatically execute predefined actions) had started to become a cross-platform threat, but in recent years we haven’t heard much about macro viruses.
Well, don’t count out macro viruses just yet, because at least one malware developer has gone retro!
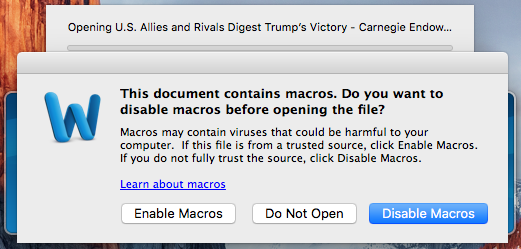
Image credit: Patrick Wardle
A file named “U.S. Allies and Rivals Digest Trump’s Victory – Carnegie Endowment for International Peace.docm” recently circulated that contained a Microsoft Word macro (as indicated by the .docm filename extension) which contained EmPyre malicious code.
If a user attempts to open the file, Word will present a dialog box stating that the document contains macros (and in fine print it states that “Macros may contain viruses that could be harmful to your computer”).
If the user ignores the warning and carelessly clicks on the (non-default) button “Enable Macros” (as seen in the screenshot above), their Mac could become infected with additional malware. For more details, see Patrick Wardle’s write-up.
New Mac Malware: PROTON RAT
Reports circulated in early February about a new remote access Trojan (RAT), called PROTON (OSX.Proton.A), found on a Russian cybercrime message board. The RAT was reportedly available for other would-be criminals to purchase for their own targeted campaigns, and even offered to add an Apple-approved developer signature to the attacker’s custom RAT software in order to bypass Apple’s Gatekeeper protection on the victim’s Mac.
After deploying the RAT onto a victim’s Mac, an attacker could allegedly gain complete remote access, including viewing the user’s screen in real time, recording keystrokes, uploading the victim’s files, downloading additional malware, accessing the webcam, issuing shell commands, and other nefarious things. More information can be found in this PDF report published by Sixgill (their accompanying blog post was offline at the time of this article’s publication).
iCloud Was Storing “Deleted” Safari History
Forbes broke the story that a company in Russia had developed a tool, called Phone Breaker, that could recover (ostensibly) deleted Safari browser history as far back as November 2015. The tool’s functionality was independently confirmed by a Forbes source.
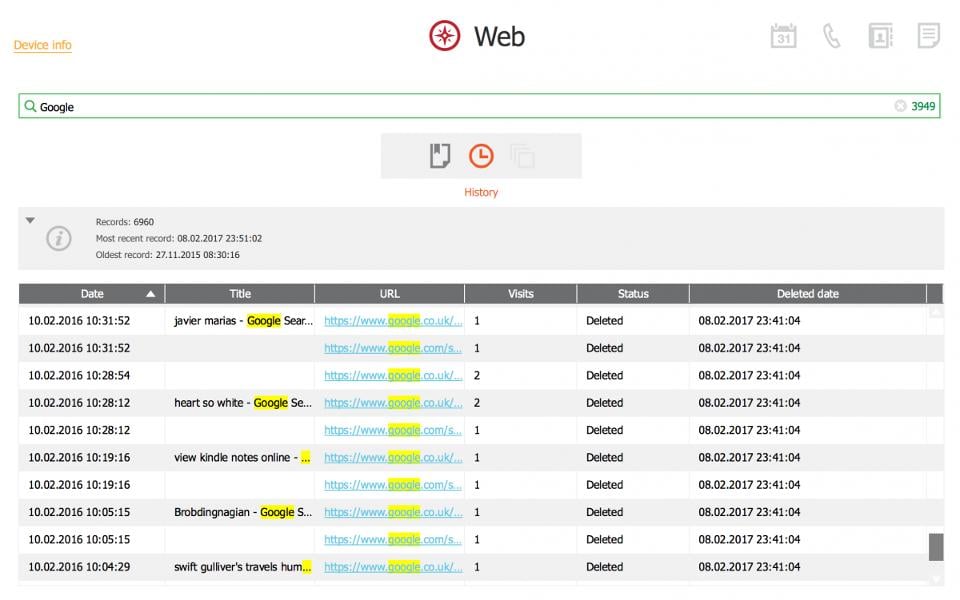
Phone Breaker screen shot. Image credit: Forbes
Apple did not respond to Forbes’ media inquiry, but shortly after the article was published, old browsing history records began disappearing from iCloud accounts that were known to have been affected.
Since Apple was tight-lipped about the ordeal, one can only speculate, but it’s possible that in late 2015 Apple either made a programming error that caused Safari history to no longer get deleted and has now corrected the issue on the back end, or perhaps Apple has yet to fix the underlying issue and has started proactively deleting old history backups while working on a more permanent fix.
Apple Security Updates
Apple has released security updates for the following software this month:
- GarageBand 10.1.6 (available for Macs running macOS Sierra, OS X El Capitan, or OS X Yosemite) fixes a vulnerability described in a single CVE (Common Vulnerabilities and Exposures) ID, preventing maliciously crafted files from causing arbitrary code execution (i.e. doing bad stuff to your Mac) — If that sounds familiar, it’s because a similar bug discovered by the same security researcher was just patched last month
- Logic Pro X 10.3.1 (available for Macs running Sierra or El Capitan) fixes the same vulnerability that was patched in this month’s GarageBand update
![]() Apple also released updates for the Apple Remote Desktop Client and Apple Remote Desktop Admin software (both of which are available for Macs running Sierra, El Capitan, or Yosemite), vaguely mentioning that the new Admin app offers “Improved security, with an optional compatibility option to support older clients in the Security tab of the Preferences panel.”
Apple also released updates for the Apple Remote Desktop Client and Apple Remote Desktop Admin software (both of which are available for Macs running Sierra, El Capitan, or Yosemite), vaguely mentioning that the new Admin app offers “Improved security, with an optional compatibility option to support older clients in the Security tab of the Preferences panel.”
When asked to comment on the security improvements, an Apple representative responded with the following details:
- ARD clients in Sierra and the ARD console now use the Secure Remote Password (SRP) protocol for authentication where possible.
- The Diffie-Hellman key size for encryption has been increased to 2048 bits.
Apple also uses the SRP protocol for communications between mobile devices running iOS 9.3 or later and HomeKit accessories, according to this Apple white paper (PDF).
Alleged Nude Celebrity Photo Leak Blamed on “iCloud Hack”

Image credit: IMDb
Various celebrity gossip sites reported earlier this week that model/actress Emily Ratajkowski had allegedly fallen victim to a cyberattack, and that naked pictures of her were stolen from her iCloud account.
A salacious someone who allegedly was in possession of those photos reportedly attempted to convince a gossip columnist to publish the photos online.
The gossip columnist—who, by the way, seems to be the sole source for the story—declined to publish the pictures.
No details about the alleged hack have been published, but the story brings to mind a similar alleged “iCloud hack” celebrity photo leak that we reported on in 2014.
In this case, it’s quite probable that the attacker simply guessed or phished Ratajkowski’s password—assuming that the story is even authentic. There is no evidence to suggest that Apple’s iCloud servers were compromised.
RSA Conference
 Last week I attended RSA Conference, an annual cybersecurity conference held in San Francisco at (and around) the Moscone Center. We’ll publish a separate article very soon covering some highlights—there’s some great stuff that you won’t want to miss.
Last week I attended RSA Conference, an annual cybersecurity conference held in San Francisco at (and around) the Moscone Center. We’ll publish a separate article very soon covering some highlights—there’s some great stuff that you won’t want to miss.
Stay Tuned! Subscribe to The Mac Security Blog
There’s more to come. Be sure to subscribe to The Mac Security Blog to catch our RSA Conference coverage, and of course to stay informed about Apple security throughout each month.
If you missed Intego’s other recent Apple security news roundups or our security predictions for 2017, you can check them out here: