Month in Review: Apple Security in April 2017
Posted on
by
Joshua Long

The end of April is upon us, can you believe it’s almost May already? A lot has happened since this time last month, so let’s jump right in with April’s security news roundup.
Some of the highlights in April include Apple security updates, a phishing scam targeting iPhone users, and an update on the Apple ID extortion attempt, among a slue of other important security news. Read on for the details!
Apple Security (and, Oops… Insecurity) Updates
 Apple released several security updates in late March and early April.
Apple released several security updates in late March and early April.
We covered the following updates in this article late last month:
- macOS Sierra 10.12.4
- Security Update 2017-001 for El Capitan and Yosemite
- iOS 10.3
- tvOS 10.2
- watchOS 3.2
- Safari 10.1
- Keynote 7.1, Numbers 4.1, and Pages 6.1 for Mac
- Keynote, Numbers, and Pages 3.1 for iOS
- macOS Server 5.3
Apple subsequently released the following security updates:
- iCloud for Windows 6.2 resolved six CVEs by improving certificate and memory handling and input validation, as disclosed by Apple here
- iOS 10.3.1 mitigated a serious issue with Broadcom’s Wi-Fi system on a chip (SoC) found in many iOS and Android devices that could have allowed a nearby attacker to execute arbitrary code on the Wi-Fi chip, as disclosed by Apple here, with further coverage from Tech Times
- Apple Music 2.0 for Android resolved a certificate validation issue that could have allowed an attacker in a privileged network position to obtain sensitive user information, as disclosed by Apple here
Along with these security updates, however, Apple inadvertently introduced a new insecurity as well.
According to Mac security researcher Patrick Wardle, Apple unintentionally introduced a new zero-day vulnerability in macOS Sierra 10.12.4 in an attempt to fix another security bug that Wardle had reported.
Apple ‘fixed’ one of my reported kernel bugs in macOS 10.12.4 by 1) not fixing it at all 2) introducing an 0day kernel info leak ?♂️ #0day https://t.co/YtMDjrj9uP
— patrick wardle (@patrickwardle) April 6, 2017
Exploitation of the vulnerability requires network-level auditing to be enabled, which Wardle notes must be turned on with root privileges. For this reason, it’s unlikely that many end users will be affected by this vulnerability before Apple releases a fix.
More than two weeks after Wardle published the complete details of his findings, Apple still has not released an update for macOS Sierra to address this vulnerability.
SMS Phishing Scam Targets iPhone Users
BGR reported that phishing scam text messages targeting iPhone users have been making the rounds this past week.
Some iPhone users have been receiving SMS text messages claiming that their Apple ID will be disabled, unless they confirm their “informations” by tapping on a shortened URL.
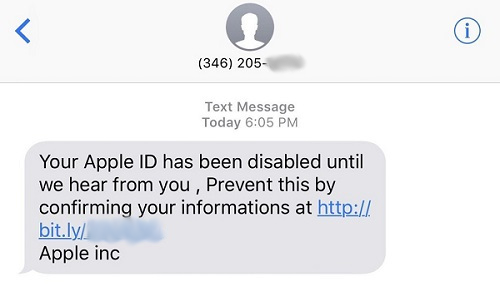
Apple has not disabled your Apple ID; don’t fall for this scam. Image credit: BGR
Apple will never disable your Apple ID until you tap on a link in a text message.
Anyone who may have fallen victim to this scam should change their password immediately at https://appleid.apple.com. We also advise Apple users to enable two-factor authentication for their Apple ID to help avoid their account becoming compromised by similar scams.
Apple ID “Breach” Extortion Update
Last month , we reported that a group of extortionists calling itself Turkish Crime Family was threatening to remotely wipe Apple devices and reset iCloud accounts if Apple had not paid a hefty US $75,000 ransom by April 7.
, we reported that a group of extortionists calling itself Turkish Crime Family was threatening to remotely wipe Apple devices and reset iCloud accounts if Apple had not paid a hefty US $75,000 ransom by April 7.
Apple claimed last month that iCloud itself had not been breached, and this claim was corroborated by a report in early April from “Have I Been Pwned?” creator Troy Hunt, who confirmed that the primary source of the Apple e-mail addresses and passwords that Turkish Crime Family had shared with reporters seemed to have been a previous breach of gaming company Evony.
So what happened on April 7? There were no major media reports indicating that a large number of devices had been remotely erased or iCloud accounts reset. As for Turkish Crime Family, a Twitter account apparently belonging to the group claimed that more than $476,000 worth of Bitcoin had been paid to the group on April 7. The implication that the ransom had been paid seems rather suspicious considering that the group had only asked Apple for $75,000.
The crime group’s Twitter account has not been updated since April 7.
Find My Mac Easily Disabled with Physical Access
The Mac Observer reported that it’s possible to disable Apple’s Find My Mac feature by simply resetting a Mac’s NVRAM (a classic Mac repair feature that was once known as “zapping the PRAM”).
Thus, if a thief steals your Mac, in theory they could simply reboot your Mac (holding down the Command-Option-P-R keystroke) and prevent you from being able to locate your computer.

This keystroke can be used to disable Find My Mac unless you have a firmware password set. Image credit: JohnHWiki
To mitigate the weakness, TMO recommended setting a firmware password on your Mac. On a Mac with a firmware password, the NVRAM cannot be reset without first entering the password at boot time.
Unofficial App Store Hidden in an App Store App
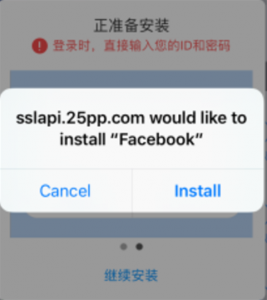
Image credit: iTnews
An unofficial app store was temporarily available within an app in Apple’s official App Store, according to a report from iTnews.
According to the report, a Japanese-language app that claimed to have been a household financial helper program was, in fact, a subversive way of getting an unofficial Mandarin Chinese-language app store past Apple’s vetting process to get it into the official App Store.
It’s unclear what exactly the developer’s intention was; perhaps it was intended as a way to install third-party apps, or modified versions of apps, without having to jailbreak a device. However, one app that was available on the unofficial store was a jailbreaking app.
The important take-away for users of iPhone, iPad, and iPod touch devices is that Apple’s app vetting process is not perfect, and occasionally some dubious apps make their way into the App Store. Users should exercise caution with any App Store apps that are either new or have very few reviews.
Unicode Implementation Issue Facilitates Phishing
 An implementation issue in the way that Mozilla Firefox, Opera, and Google Chrome browsers have displayed URLs could make it easier for an attacker to make a very convincing phishing site, as explained by Wordfence.
An implementation issue in the way that Mozilla Firefox, Opera, and Google Chrome browsers have displayed URLs could make it easier for an attacker to make a very convincing phishing site, as explained by Wordfence.
Essentially, an attacker can register a domain with a URL that in Firefox and Opera (and old versions of Chrome) will look identical, or nearly identical, to the address of a legitimate site.
Wordfence used the example of epic.com, a healthcare site, and registered the domain “xn--e1awd7f.com” which uses look-alike, internationalized domain name (IDN) characters that in some browsers appears as “epic.com” in the address bar.
Less than a week after Wordfence published its findings, another researcher registered a look-alike apple.com domain, xn--80ak6aa92e.com, as reported by Ars Technica.
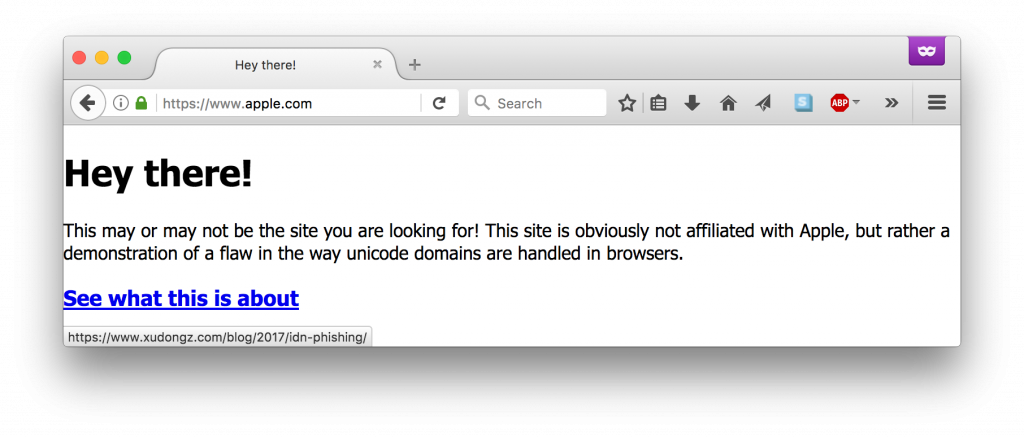
Firefox displays this site’s address as https://www.apple.com rather than https://www.xn--80ak6aa92e.com
Both example sites have a free TLS (“SSL”) certificate from LetsEncrypt, adding legitimacy to the way the sites appear in affected browsers’ address bars.
The idea of IDN homograph attacks is not new; there’s actually a Wikipedia article for it. However, after the recent media attention, two of the three affected browsers are taking action to address the issue.
Google has already mitigated this issue by releasing Chrome version 58.
Opera users can use the beta version, 45, or the developer version, 46, which mitigate the issue. The current stable release, version 44 (44.0.2510.1218), does not address the issue.
Meanwhile, according to Ars Technica, Mozilla’s lead developers have indicated that they do not plan to address the issue by changing Firefox’s default behavior. Firefox users who wish to mitigate this issue themselves may do the following:
- Type “about:config” into the address bar
- Agree to accept the risk
- Search for “network.IDN_show_punycode”
- Double-click the item to change from the default “false” setting to “true”
Apple’s Safari browser does not display these sites’ addresses in a misleading manner.
EFF Releases “Troubling” Report on Ed-Tech App Privacy
The Electronic Frontier Foundation has released a report (summary; full report) detailing privacy concerns with regard to devices issued by schools to students. Those who work in education, or concerned parents, may be interested in reviewing the report, which mentions iPads and some popular edtech apps.
Ed tech apps show troubling trends in data retention and encryption. Read more in our new student privacy report. https://t.co/bxckLiNz4h
— EFF (@EFF) April 15, 2017
Stay Tuned! Subscribe to The Mac Security Blog
Be sure to subscribe to The Mac Security Blog to stay informed about Apple security throughout each month.
If you missed Intego’s previous Apple security news roundups for 2017, you can check them out here: