Month in review: Apple security in November 2017
Posted on
by
Joshua Long

What a month! November brought to light a huge security vulnerability affecting macOS High Sierra, plus Mac malware that masquerades as anti-virus software, and specially crafted masks can fool Face ID (despite Apple’s claims). Read on for the details!
I Am Root: Major Root-Access Flaw in High Sierra
 The biggest news of the month is still fresh in our memory. On November 28, the world became aware of a major security vulnerability in macOS High Sierra that could allow an attacker to enable the “root” administrator account on a victim’s Mac.
The biggest news of the month is still fresh in our memory. On November 28, the world became aware of a major security vulnerability in macOS High Sierra that could allow an attacker to enable the “root” administrator account on a victim’s Mac.
A bug was introduced in macOS High Sierra 10.13, and remained in 10.13.1, that allowed an attacker to invoke a system authentication dialog box, type “root” (the name of a powerful UNIX administrator account that’s disabled by default in macOS), and either enter no password or a password of their choosing, and macOS would enable the root account with the attacker’s chosen password.
If a system running High Sierra had Screen Sharing enabled, it was even possible to exploit the vulnerability remotely, without having physical access to the Mac.
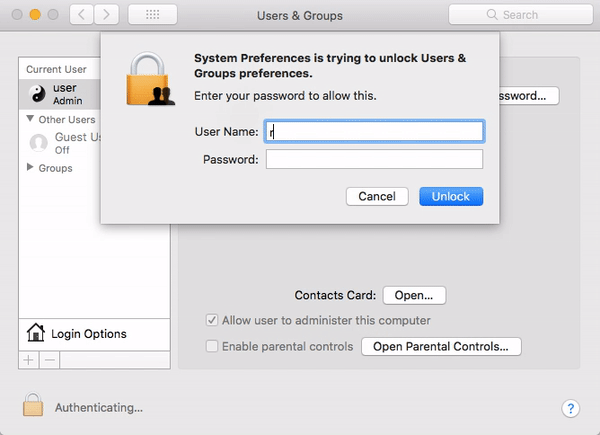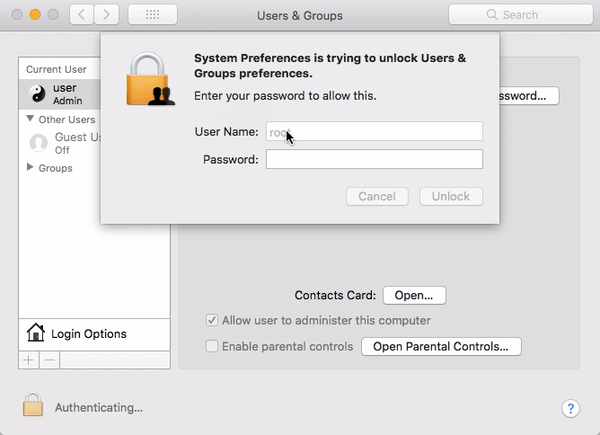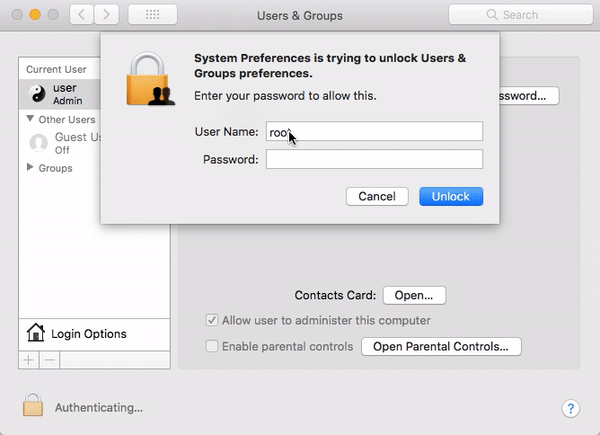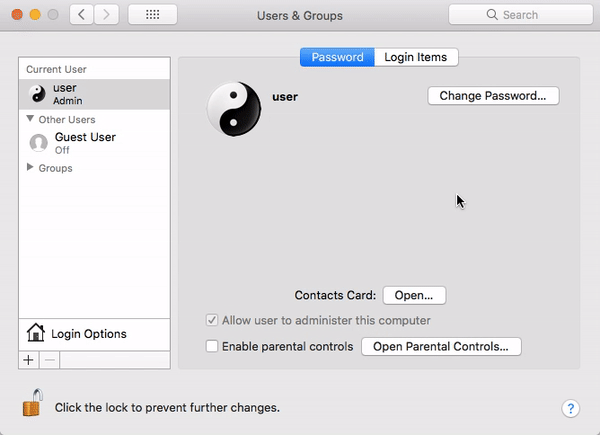 The “I am root” attack in action. Image credit: Patrick Wardle
The “I am root” attack in action. Image credit: Patrick Wardle
Thankfully, Apple responded quickly after the bug became widely known. By the next morning, Apple released a patch and pushed it out to all High Sierra users.
There’s a lot more to this story! For all the juicy details, don’t miss our extensive coverage: “I Am Root”: A Retrospective on a Severe Mac Vulnerability!
Proton Malware Masquerades as Anti-Virus
Earlier this year, we reported that variants of the Proton malware were discovered on the legitimate download sites of Handbrake and later Elmedia Software. In both cases, the developers’ legitimate apps were infected with malware and made available directly from the developers’ sites for a period of time without their knowledge.
 In November, the makers of the Proton malware decided to try a different tactic to infect users.
In November, the makers of the Proton malware decided to try a different tactic to infect users.
A blog was discovered that purported to be operated by Symantec, an anti-virus company. On this fake anti-virus blog was a link to download a supposed “Symantec Malware Detector,” which in reality is just a Trojan horse designed to install the Proton malware onto victims’ Macs.
If a victim were to download an ran the fake virus scanner, they would be prompted to enter their administrator username and password, at which point the malware would secretly infect the system and then display a fake virus scan (much like other fake antivirus software has done in the past).
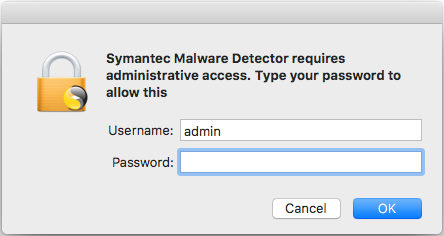 The fake antivirus attempts to gain admin privileges.
The fake antivirus attempts to gain admin privileges.
Intego VirusBarrier (which is legitimate anti-virus software!) identifies the new malware variant as OSX/Proton.D.
For lots more details, check out our article Watch Out! A Fake Antivirus Blog is Distributing Proton Malware, and listen to our new Intego Mac Podcast episode discussing it (have you subscribed yet? ?).
Face ID Fooled By Hackers… and a 10-Year-Old Boy?
Two stories surfaced in November claiming that the iPhone X’s new Face ID technology had been successfully tricked into unlocking Apple’s latest smartphone.
One story from CNET reports that Vietnamese hackers created a specially crafted face mask that allegedly was able to successfully spoof a real person’s face to log into an iPhone X. You can watch the mask makers’ proof-of-concept video, which has been viewed 1.2 million times.
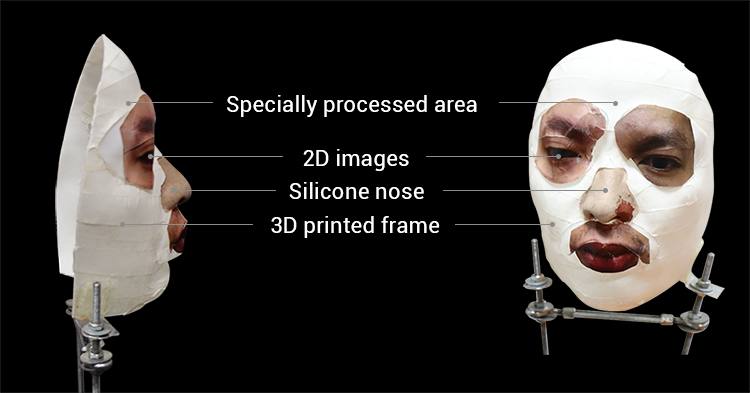 This mask can allegedly bypass Face ID. Image credit: BKAV via CNET
This mask can allegedly bypass Face ID. Image credit: BKAV via CNET
This is particularly interesting given that when Apple introduced the iPhone X, Apple executive Phil Schiller took the stage and bragged that Apple had tasked Hollywood mask-making experts with trying to fool Face ID, and their efforts were unsuccessful.
 In late November, AppleInsider reported that the same Vietnamese group repeated the test, developing a second mask that allegedly fools Touch ID. They claim that the new mask cost about U.S. $200 to make. Their second proof-of-concept video much more convincingly demonstrates the authenticity of their work; the researcher turns off Face ID and then re-enrolls his face, then shows his face unlocking the iPhone, and then finally shows the mask unlocking the iPhone, all without any camera cuts.
In late November, AppleInsider reported that the same Vietnamese group repeated the test, developing a second mask that allegedly fools Touch ID. They claim that the new mask cost about U.S. $200 to make. Their second proof-of-concept video much more convincingly demonstrates the authenticity of their work; the researcher turns off Face ID and then re-enrolls his face, then shows his face unlocking the iPhone, and then finally shows the mask unlocking the iPhone, all without any camera cuts.
Hot on the heels of the original mask story came a report from Wired that a 10-year-old boy was able to successfully and repeatedly unlock his mother’s iPhone X.
 Boy’s face unlocks mom’s iPhone X. Image: Malik/Sherwani via TechWorm
Boy’s face unlocks mom’s iPhone X. Image: Malik/Sherwani via TechWorm
The idea that a child could gain access to his parent’s phone, which may contain private information, seemed to really catch people’s interest; the family’s 41-second YouTube video has been viewed more than 2.3 million times.
Apple’s Schiller admitted during the iPhone X unveiling keynote that there’s a higher probability of false matches for people who have “a close genetic relationship” with the user.
Dangerous Gadget “Deals” Hit Holiday Shopping Season
 Following the U.S. Thanksgiving holiday are “Black Friday” and “Cyber Monday,” two of the biggest shopping days of the year, when retailers have big sales to draw in customers at the theoretical start of the holiday shopping season. Sometimes these promotional sales seem a little too good to be true.
Following the U.S. Thanksgiving holiday are “Black Friday” and “Cyber Monday,” two of the biggest shopping days of the year, when retailers have big sales to draw in customers at the theoretical start of the holiday shopping season. Sometimes these promotional sales seem a little too good to be true.
This year at least one popular online retailer has been selling and openly promoting ancient iPhones and iPads for which Apple is no longer releasing security updates. Using a device online when its security is years out of date is very unsafe and should be avoided.
Beware of “bargains” that may come with unexpected security risks.
If you have holiday shopping left to do, be sure to check out these articles for tips on how to ensure that the products you’re buying are secure and how to shop safely:
Caution! These Black Friday “deals” may be bad for your security
7 essential tips to stay safe shopping online on Black Friday and Cyber Monday
Other Security News, in Brief
There were other notable goings-on in the security world in November. Some highlights:
- Apple offered to help the FBI break into a Texas shooter’s iPhone but the FBI allegedly ignored Apple’s offer, according to Forbes. Apple did not offer a backdoor or a way to break or bypass Touch ID, but rather Apple suggested ways that the FBI could obtain information from the phone such as applying the deceased killer’s fingerprints to the Touch ID sensor within 48 hours after the man had last used his iPhone.
 Two Safari vulnerabilities in iOS 11.1 through 11.1.2 have yet to be patched. ZDNet reports that security researchers successfully compromised Safari in the Tokyo Mobile Pwn2Own contest just a day after the release of iOS 11.1. Since then, Apple has released both iOS 11.1.1 and 11.1.2, but neither one seems to fix any additional vulnerabilities according to Apple.
Two Safari vulnerabilities in iOS 11.1 through 11.1.2 have yet to be patched. ZDNet reports that security researchers successfully compromised Safari in the Tokyo Mobile Pwn2Own contest just a day after the release of iOS 11.1. Since then, Apple has released both iOS 11.1.1 and 11.1.2, but neither one seems to fix any additional vulnerabilities according to Apple. Cryptojacking is becoming more common according to Ars Technica. The term “cryptojacking” refers to the surreptitious mining of cryptocurrency (usually Monero, similar to Bitcoin) in a user’s browser. Kirk McElhearn and I discussed this topic at length, including how to protect yourself, on the November 15 episode of the Intego Mac Podcast—be sure to subscribe to make sure you don’t miss any episodes:
Cryptojacking is becoming more common according to Ars Technica. The term “cryptojacking” refers to the surreptitious mining of cryptocurrency (usually Monero, similar to Bitcoin) in a user’s browser. Kirk McElhearn and I discussed this topic at length, including how to protect yourself, on the November 15 episode of the Intego Mac Podcast—be sure to subscribe to make sure you don’t miss any episodes:

 Intego launched a free app, VirusBarrier Scanner, in the Mac App Store. You can learn more about the difference between a malware scanning utility and full-featured security software, or download the scanner now:
Intego launched a free app, VirusBarrier Scanner, in the Mac App Store. You can learn more about the difference between a malware scanning utility and full-featured security software, or download the scanner now:

- Apple released two XProtect updates in November. (XProtect is Apple’s bad-download blocker that’s built into macOS.) The first XProtect update was released on November 6 and blocks two malicious ad-loaders and a Mughthesec variant, and the second update was released on November 30 and blocks OSX.ParticleSmasher.A (Apple’s name for the OSX/Proton.D fake antivirus malware described above) and OSX.HiddenLotus.A (which Intego VirusBarrier detects as OSX/HiddenCloud).
Stay Tuned! Subscribe to The Mac Security Blog
Be sure to subscribe to The Mac Security Blog to stay informed about Apple security throughout each month.
If you missed Intego’s previous Apple security news roundups for 2017, you can check them out here.
Also, be sure to subscribe to our YouTube channel to get monthly updates in video form, and click on YouTube’s bell icon (?) so you’ll get notified when each new episode is available!
“I am root”/Groot cartoon image credit: Johnathon Burns modified by Gaël