New OceanLotus Backdoor Discovered Targeting macOS
Posted on
by
Jay Vrijenhoek
Last week, security researchers published a report on a new backdoor that is part of the OceanLotus toolkit. This latest iteration of OceanLotus malware targets macOS and uses a malicious Microsoft Word document to infect a host system.
The malicious document name seen in the wild was “2018-PHIẾU GHI DANH THAM DỰ TĨNH HỘI HMDC 2018.doc,” but can of course have any name in any language. The document claims to be a registration form for an event with HDMC, an organization in Vietnam that advertises national independence and democracy.
OceanLotus (a.k.a. APT 32, APT-C-00, SeaLotus, and Cobalt Kitty) was also responsible for launching targeted attacks against human rights organizations, media organizations, research institutes, and maritime construction firms. Intego VirusBarrier identifies and eradicates this new malware variant as OceanLotus.D.
How does OceanLotus.D infect Macs?
The assumption is that this new backdoor is distributed via email, possibly by phishing or spear phishing attacks. The malicious payload is part of a Microsoft Word document that, once opened, will display a warning stating the document is unable to be opened.
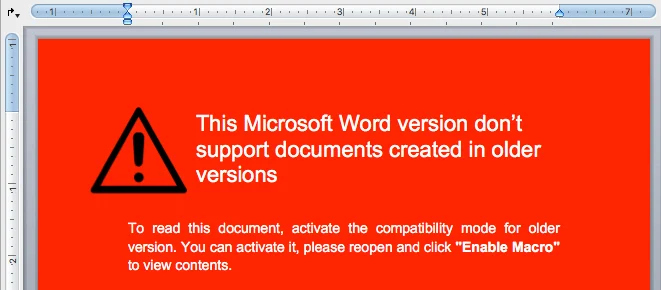
This warning is fake and simply part of the document itself. The user is instructed to reopen the document and click “Enable Macros,” if prompted.
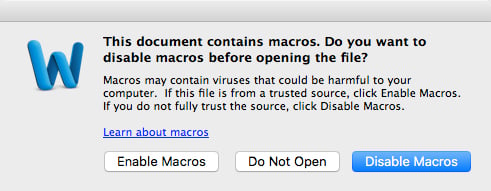
Enabling macros, however, would be a mistake as this allows the document to install its payload—the OceanLotus.D backdoor. No user name or password is required for this to happen.
What can OceanLotus.D do?
Once the backdoor is in place, the malware is able to communicate with a Command & Control (C&C) server and do any of the following:
- Get file sizes
- Download & execute file
- Run terminal command
- Remove file
- Upload file
- Download file
- Get configuration info
The C&C servers were identified as:
- Ssl[.]arkouthrie[.]com
- s3[.]hiahornber[.]com
- widget[.]shoreoa[.]com
All domains are hosted on the same server with the IP address of 185.174.101.13.
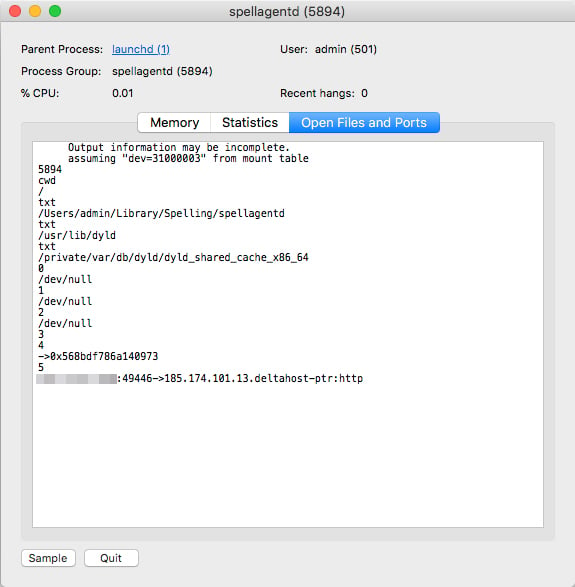
Persistence is maintained by placing a plist in either /Library/LaunchDaemons/ or ~/Library/LaunchAgents/. This launch agent invokes a process stored in ~/Library/Spelling/ named “spellagentd” or stored in /Library/CoreMediaIO/Plug-Ins/FCP-DAL/iOSScreenCapture.plugin/Contents/Resources/ and named “screenassistantd.” The below image shows what the spellagentd process is running and communicating with the C&C server:
Should Mac users be concerned about OceanLotus.D?
It is important to note that for the malicious Word document to drop its payload, the Mac user must use Office 2011. In Word versions ranging 14.4.4 – 14.7.7 the document was able to drop its payload every time. However, using Office 2016 with Word versions ranging 15.39 – 16.11 the document was unable to drop its payload, and it even started throwing errors as more updates were applied.
So far, OceanLotus.D has not been seen in widespread use, but it could be used part of other malware attacks. Because OceanLotus takes virtually no CPU power or memory and requires no user name and password to install, a Mac user can be infected without ever knowing. Wherever OceanLotus.D may come from, Intego VirusBarrier customers are protected from this new malware variant, and have been since March 20, 2018.
How to tell if your Mac is infected (and removal instructions)
To check if your Mac is infected and to clear the infection if present, you first need to make invisible files visible in the Finder. In macOS Sierra and High Sierra, this can quickly be done with the following key combination:
Command-Shift-. (period)
For older OS X versions this can be done by typing the following commands in the Terminal app:
$ defaults write com.apple.Finder AppleShowAllFiles true
$ killall Finder
When done, enter the same commands but change “true” to “false.”
With the hidden files now visible, check both the root library and the user library for these files:
- Library > LaunchDaemons – Look for a file named com.apple.screen.assistantd.plist and delete it if found.
- ~ Library > LaunchAgents > com.apple.spell.agent.plist – Delete this file if present.
- Library > CoreMediaIO > Plug-Ins > FCP-DAL > iOSScreenCapture.plugin > Contents > Resources – Look for a file named screenassistantd and delete it if found.
- ~ Library > Spelling > screenassistantd – Delete this file.
If an infection is found and the above files have been deleted, empty your trash and restart your Mac.
How to protect yourself from OceanLotus.D
Intego VirusBarrier users are protected as it detects OceanLotus.D, and will remove it from an infected system or block it from installing if it makes its way to your Mac in the future. Of course, using antivirus with real-time scanning along with a two-way firewall solution, such as Intego NetBarrier, will also alert you of any connection attempts to/from applications, which allows you to spot suspect behavior.
This is not the first time Macros have been abused to install Mac malware, and it certainly won’t be the last time. Therefore, only enable macros if you absolutely need them and trust the document that requests them completely.