New Mac ransomware-spyware EvilQuest in the wild
Posted on
by
Joshua Long

On Monday, June 29, Intego’s research team was alerted to new Mac malware spreading in the wild via BitTorrent. At first glance, it has telltale signs of ransomware—malware designed to encrypt a user’s files and demand a ransom to recover them—but it turns out to be much more nefarious.
The malware, dubbed OSX/EvilQuest (also known as OSX/ThiefQuest) and detected by Intego VirusBarrier as OSX/EvilQuest (previously OSX/Ransomware), has some pretty interesting characteristics. Here’s what you need to know about this latest threat.
In this article:
- Is this malware in the wild? How does it spread?
- What does the new malware do? How is it unique?
- How should Mac users avoid getting this malware?
- How can the malware be removed?
- How can I recover my files that got encrypted?
- Indicators of compromise
- How can I learn more?
Is this malware in the wild? How does it spread?
The EvilQuest malware comes disguised as an installer for any of various Mac applications, including Google Software Update, Ableton, Little Snitch, and Mixed In Key 8.
Thanks for the info! Been working on that this morning… seems it's getting dropped by some installers wrapping legit software like Little Snitch, Ableton, and Mixed In Key. There are probably others as well.
— Thomas Reed (@thomasareed) June 29, 2020
BitTorrent magnet links to download these Trojanized installers have been observed on RUTracker, a Russian forum site. The forum post seems to be dated June 9, so this malware may have gone undiscovered for approximately three weeks.
RUTracker forum post with BitTorrent link to Trojanized Little Snitch. Image: Reed
What does the new malware do? How is it unique?
Although the Trojanized installer may install the intended software, it also installs malware onto the victim’s system.
Among other things, the malware encrypts the user’s files, after which it displays a dialog box claiming that the user has three days to pay a U.S. $50 ransom to a particular Bitcoin address. Thankfully, nobody has yet paid the ransom—at least not to one Bitcoin address that has been found associated with this malware campaign—as of when this article was published.
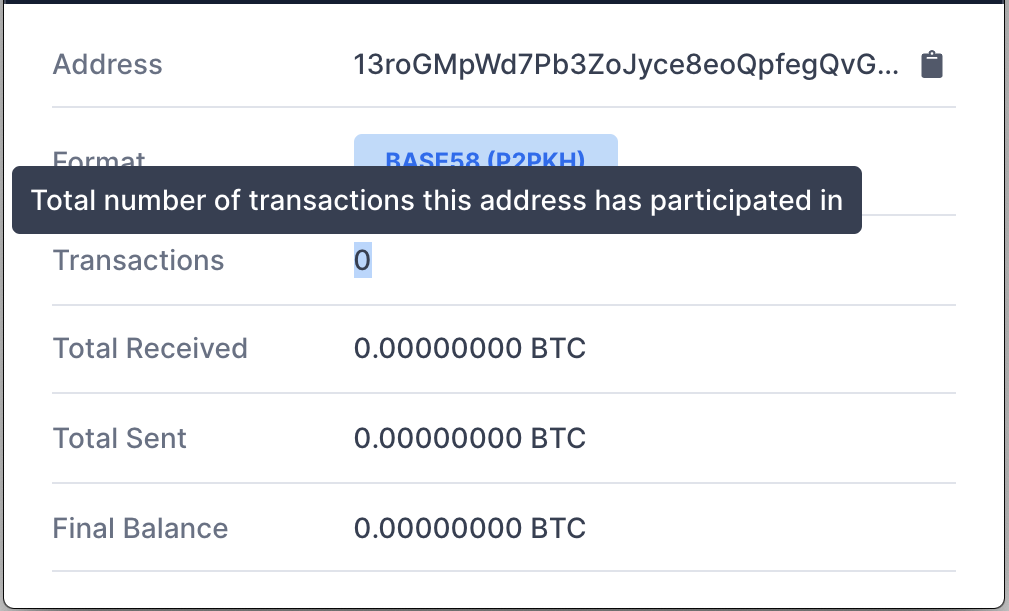
Evidently, nobody had paid the ransom as of when this article was published. Image: Intego
There’s actually a bit of a twist to the ransomware angle, though. Although so far this has sounded like standard ransomware behavior, the malware makers actually don’t provide an e-mail address or any other way to contact them, so it is unclear how the extortioners would know who paid them and therefore how to help that person decrypt their files.
In other words, this “ransomware” may be better described as a “wiper”—malicious software that encrypts files without providing any way to decrypt them, even if you give in to the extortioner’s demands. It remains to be seen whether the anti-malware community will be able to discover a way to decrypt documents encrypted by this malware.
There are also additional capabilities beyond encrypting the user’s documents. EvilQuest also phones home to command and control (C2) servers, can log a victim’s keystrokes, and it has data exfiltration capabilities—meaning it can steal potentially interesting files from a victim’s computer and send them to the malware maker.
EvilQuest also tries to avoid detection by behaving differently when running within a virtual machine or when a debugger is running—common tactics to make it more difficult for malware analysts and automated analysis tools to identify and assess malicious behaviors.
Update: After this article was first published, it came to light that EvilQuest also maliciously modifies Google Software Update background apps, which interestingly makes EvilQuest a true Mac virus.
Given all this functionality, the EvilQuest malware is not “merely” ransomware. It could also be described as a wiper, data stealer, spyware, keylogger, evader, virus, and a RAT.
How should Mac users avoid getting this malware?
This is not the first time that malware has been distributed via BitTorrent, or by disguising itself as illegitimately obtained full or “cracked” versions of Mac software. We wrote in 2017 about “Patcher” (OSX/Filecoder) ransomware that spread the same way.
In fact, later that year an Intego blogger did his own investigation of Mac software distributed through BitTorrent, and found that every app he downloaded was flagged by Intego VirusBarrier as containing malware:
In short, it simply is not a good idea to download Mac apps through BitTorrent. The safest way to obtain an app is through the Mac App Store where possible, or directly from the developer’s site.
How can the malware be removed?
Intego VirusBarrier X9, included with Intego’s Mac Premium Bundle X9, can detect and eliminate this malware.
Customers running VirusBarrier X8, X7, or X6 on older versions of Mac OS X are also protected. It is best to upgrade to the latest version of macOS if possible to ensure your Mac gets all the latest security updates from Apple.
How can I recover my files that got encrypted?
The malware maker doesn’t provide any contact information, so paying the ransom would be a one-way transaction; you’d be giving the bad guys your money, but you still wouldn’t be able to recover your encrypted files. (Whenever possible, it’s best to avoid paying ransoms anyway, of course, since giving money to criminals ultimately gives them motivation to keep victimizing others.)
Thankfully, the community has come together and reverse-engineered the encryption. There’s even a free utility that can be used to decrypt and restore files that have been encrypted by the EvilQuest malware.
Indicators of compromise
Some paths that have been observed so far from this malware campaign include the following:
/Library/LaunchDaemons/com.apple.questd.plist /Library/mixednkey/toolroomd /private/var/root/Library/.5tAxR3H3Y /private/var/root/Library/AppQuest/com.apple.questd /private/var/root/Library/LaunchAgents/com.apple.questd.plist ~/Library/.ak5t3o0X2 ~/Library/AppQuest/com.apple.questd ~/Library/LaunchAgents/com.apple.questd.plist Mixed In Key 8.dmg [if downloaded via BitTorrent]
The following domain and IP address have been observed as directly affiliated with this malware campaign:
andrewka6.pythonanywhere[.]com 167.71.237[.]219
Any recent network traffic to or from these addresses should be considered a possible sign of an infection.
How can I learn more?
For more technical analyses of this malware, you can refer to Patrick Wardle (part 1 and part 2), Thomas Reed (part 1 and part 2), Lawrence Abrams, and Phil Stokes‘ published research. WIRED writer Lily Hay Newman also has additional coverage of this story.
 We talked about this new malware on episode 142 and will follow up on episode 143 of the Intego Mac Podcast—be sure to subscribe to make sure you don’t miss any episodes. You’ll also want to subscribe to our e-mail newsletter and keep an eye here on The Mac Security Blog for the latest Apple security and privacy news.
We talked about this new malware on episode 142 and will follow up on episode 143 of the Intego Mac Podcast—be sure to subscribe to make sure you don’t miss any episodes. You’ll also want to subscribe to our e-mail newsletter and keep an eye here on The Mac Security Blog for the latest Apple security and privacy news.
You can also follow Intego on your favorite social and media channels: Facebook, Instagram, Twitter, and YouTube (click the 🔔 to get notified about new videos).