Atomic Stealer (AMOS) Mac malware spreads via malicious Google Ads
Posted on
by
Joshua Long

In May and September 2023, we wrote about earlier variants of Atomic Stealer. This malware—also known as Atomic macOS Stealer or AMOS for short—is designed to exfiltrate sensitive data from infected Macs. It is distributed in the form of Trojan horses, such as pirated or “cracked” versions of apps.
This week, reports have emerged of two different new variants of Atomic Stealer. Here’s everything you need to know about them and how to stay protected.
Atomic Stealer distributed through malicious Google Ads
One of the new Atomic Stealer variants, described by Jérôme Segura, has been confirmed to be distributed in the wild via Google Ads poisoning. A threat actor paid Google for top placement, with sponsored ads that mimicked the real ads of the Notion productivity software. These ads appeared immediately above the actual search results; if you weren’t careful, you could have inadvertently visited a malware distribution site instead of landing on the real software developer’s site.
If a victim clicked on a link in the malicious ad, they would be redirected to a fake Notion homepage which would offer Mac or Windows malware disguised as Notion software. The Windows malware was a stealer called Rhadamanthys, and the Mac malware was a new Atomic Stealer variant.

An OSX/AtomicStealer Trojan horse, masquerading as Notion productivity software.
Notably, this Atomic Stealer variant has very low detection on the multi-engine single file scanning site VirusTotal; only 6 out of 60 engines detect it, while other variants (like the ones described below) typically have at least 20 detections.
A second variant disguised as a “Crack Installer”
Another variant, described by Andrei Lapusneanu, disguises itself as an unspecified “Crack Installer.” If a victim follows the directions from the disk image, and does a “right click” and clicks Open, a Mach-O app runs. Like with the first variant, this app is a dropper, meaning it will attempt to download and execute a further stage of the malware.
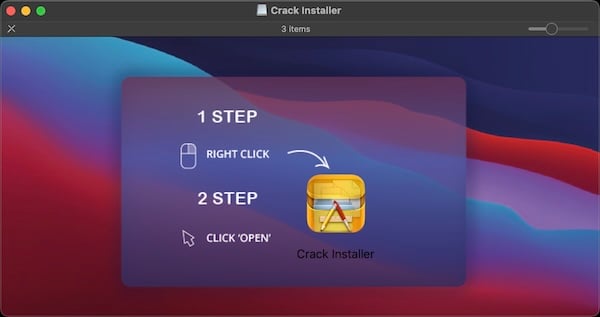
Another OSX/AtomicStealer Trojan, disguised as a “Crack Installer”
The next stage is a Python script that does all the usual things one expects stealer malware to do; it attempts to gather and exfiltrate browser data such as saved passwords, cookies, autofill text, and cryptocurrency wallets. It uses AppleScript code similar to that used in RustDoor malware seen earlier in February. This Atomic Stealer variant attempts to send the stolen data to an IP address that has previously been linked to Windows malware called Amadey.
How can I keep my Mac safe from malware?
If you use Intego VirusBarrier, you’re protected from this malware. Intego detects these samples as OSX/Stealer.ext, virus/OSX/Agent.mysf, virus/OSX/AVA.Agent.amos, virus/OSX/AVF.Agent.tfcg, virus/OSX/AVI.Agent.dkaa, and similar names.
 Intego VirusBarrier X9, included with Intego’s Mac Premium Bundle X9, is a powerful solution designed to protect against, detect, and eliminate Mac malware.
Intego VirusBarrier X9, included with Intego’s Mac Premium Bundle X9, is a powerful solution designed to protect against, detect, and eliminate Mac malware.
If you believe your Mac may be infected, or to prevent future infections, it’s best to use antivirus software from a trusted Mac developer. VirusBarrier is award-winning antivirus software, designed by Mac security experts, that includes real-time protection. It runs natively on both Intel- and Apple silicon-based Macs, and it’s compatible with Apple’s current Mac operating system, macOS Sonoma.
If you use a Windows PC, Intego Antivirus for Windows can keep your computer protected from malware.
How can I learn more?
For additional technical details and indicators of compromise (IOCs) for these Atomic Stealer variants, you can read Jérôme Segura’s write-up and social media post, and Andrei Lapusneanu’s write-up.
We discussed the resurgence of Atomic Stealer—as well as Google’s concerning ineptitude at preventing overt copycat ads that link to malware sites—on episode 333 of the Intego Mac Podcast.
Be sure to also check out our 2024 Apple malware forecast and our previous Mac malware articles from 2024 and earlier.
 Each week on the Intego Mac Podcast, Intego’s Mac security experts discuss the latest Apple news, including security and privacy stories, and offer practical advice on getting the most out of your Apple devices. Be sure to follow the podcast to make sure you don’t miss any episodes.
Each week on the Intego Mac Podcast, Intego’s Mac security experts discuss the latest Apple news, including security and privacy stories, and offer practical advice on getting the most out of your Apple devices. Be sure to follow the podcast to make sure you don’t miss any episodes.
You can also subscribe to our e-mail newsletter and keep an eye here on The Mac Security Blog for the latest Apple security and privacy news. And don’t forget to follow Intego on your favorite social media channels: ![]()
![]()
![]()
![]()
![]()
![]()
![]()