OSX/Coldroot and the RAT invasion
Posted on
by
Joshua Long
 The past several weeks have brought to light three distinct families of RAT malware for Macs. We’ve previously covered CrossRAT and EvilOSX, and in this article we’ll explore OSX/Coldroot.
The past several weeks have brought to light three distinct families of RAT malware for Macs. We’ve previously covered CrossRAT and EvilOSX, and in this article we’ll explore OSX/Coldroot.
First, let’s briefly take a look at what exactly is a “RAT.” Later, we’ll also explore why so many RATs have been discovered already in 2018, and we’ll explain how you can protect yourself from these threats.
What is a RAT?
 RAT is an acronym that stands for “remote administration tool” or “remote access Trojan.” While there are plenty of perfectly legitimate software utilities for accessing another computer (for example, Apple Remote Desktop), the term RAT is generally reserved for software that’s designed to be installed and used without the computer user’s knowledge, often with the intention of spying or stealing resources.
RAT is an acronym that stands for “remote administration tool” or “remote access Trojan.” While there are plenty of perfectly legitimate software utilities for accessing another computer (for example, Apple Remote Desktop), the term RAT is generally reserved for software that’s designed to be installed and used without the computer user’s knowledge, often with the intention of spying or stealing resources.
RATs commonly include features that allow a remote attacker to control or spy on your computer. They may allow an attacker to do such things as observe your screen, take screenshots, activate your camera or microphone, log everything you type including your passwords, copy files to or from your computer, or execute other commands, all in the background and without your knowledge.
What’s the story behind OSX/Coldroot?
 Over the same weekend that Intego researchers discovered OSX/Shlayer, another researcher, Patrick Wardle, independently discovered OSX/Coldroot, an entirely different type of Mac malware: a RAT.
Over the same weekend that Intego researchers discovered OSX/Shlayer, another researcher, Patrick Wardle, independently discovered OSX/Coldroot, an entirely different type of Mac malware: a RAT.
In preparation for a talk at an upcoming security conference, Wardle searched VirusTotal—a site that uses dozens of anti-virus engines to analyze individual files that users upload—for a sample of malware that attempts to directly modify a macOS database file (TCC.db) to grant itself special permissions.
One sample that came up in the search results was undetected by all 60 of VirusTotal’s anti-virus engines. However, Wardle felt that a variety of indicators pointed to the strong probability that the software was malicious. The following were indicators that were relatively easy to discover by a casual observer:
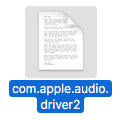 The software’s name, com.apple.audio.driver2.app, is suspicious because it seems to be trying to disguise itself as Apple software.
The software’s name, com.apple.audio.driver2.app, is suspicious because it seems to be trying to disguise itself as Apple software.- Although the sample is actually a Mac app, its icon is that of a text document, which seems to imply that the app’s creator may have been trying to trick users into double-clicking on it. (Incidentally, this has been a problem for decades, and Apple still hides the .app extension by default in the Finder, making it more difficult for users to detect a misleading icon.)
- If the app is opened, it prompts for your password without any observable behavior afterward, which is unusual. (This is how OSX/Coldroot gains the ability to run again whenever the Mac is restarted.)
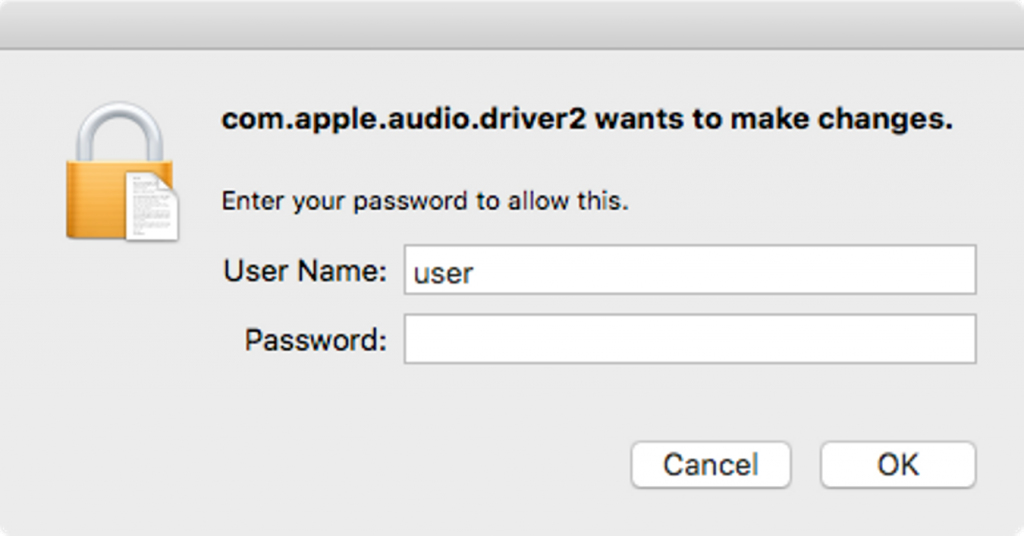
OSX/Coldroot prompts for your password. Image: Wardle
There were also a number of other indicators that the software was probably malicious, but that would only be noticeable to a skilled researcher:
- The software attempts to directly modify TCC.db, an Accessibility database that tracks special permissions that the user has granted to apps. No third-party software should ever attempt to directly alter that database. (OSX/Coldroot attempts this hack for the purpose of keylogging.)
- The software is not digitally signed, as legitimate software from Apple and most reputable third-party developers usually is. (See our recent article about OSX/Shlayer malware for a brief explanation of code signing.)
- The sample is packed (compressed) with UPX, a common technique for attempting to hide malicious code from anti-virus scanners. It’s very rare for legitimate Mac software to employ a code-packing algorithm like UPX.
Once the malware is installed, it logs the user’s keystrokes to a file (misleadingly named “adobe_logs.log”). It also phones home to a command-and-control server which seems to be located in Australia, and it copies itself into a hidden folder and installs a LaunchDaemon to allow itself to run again every time the Mac is restarted.
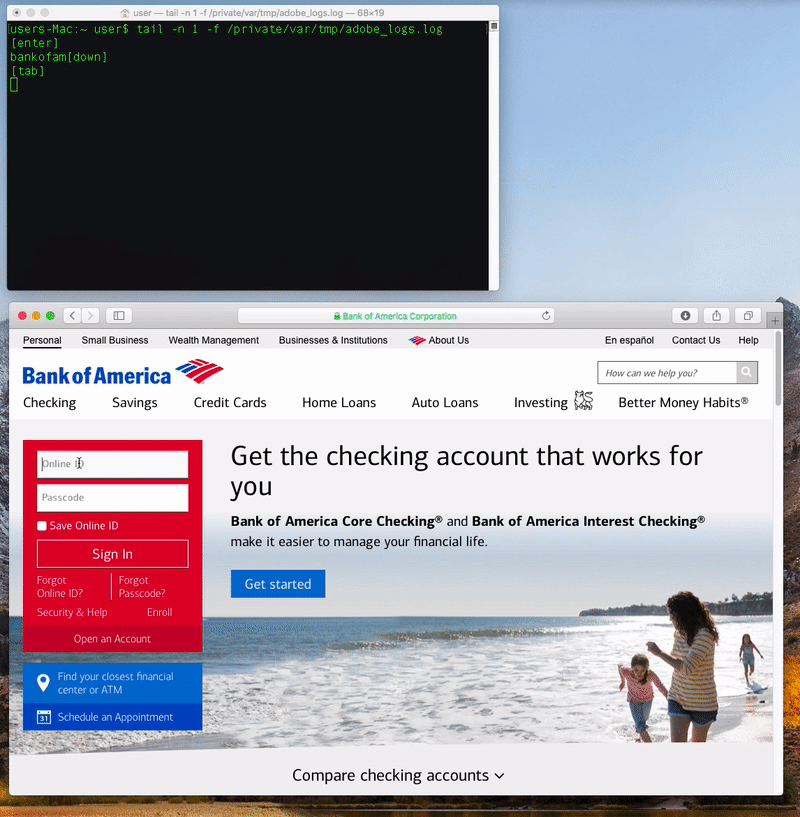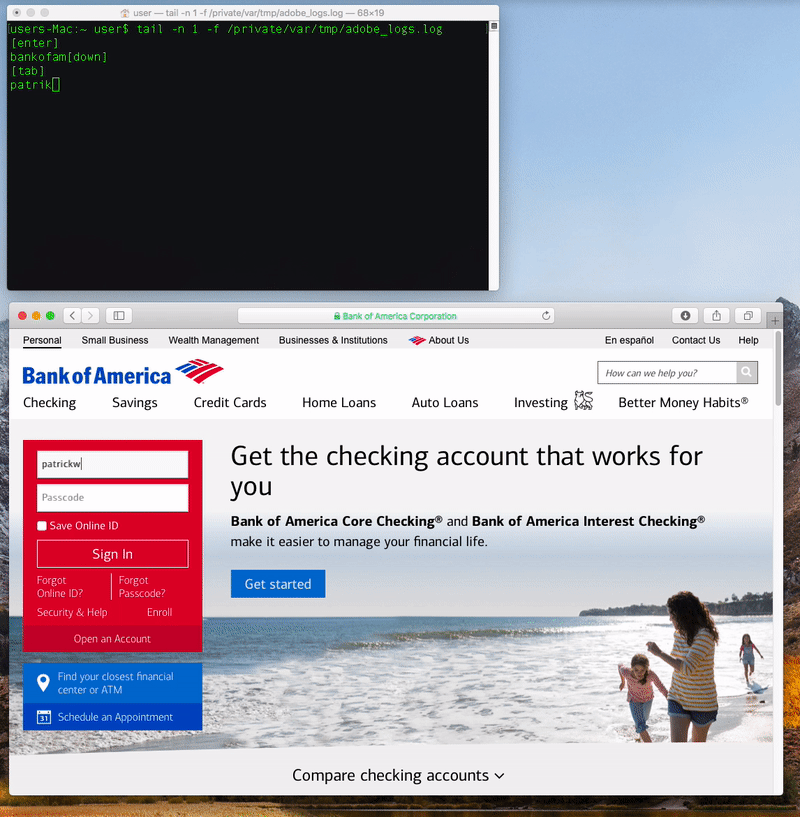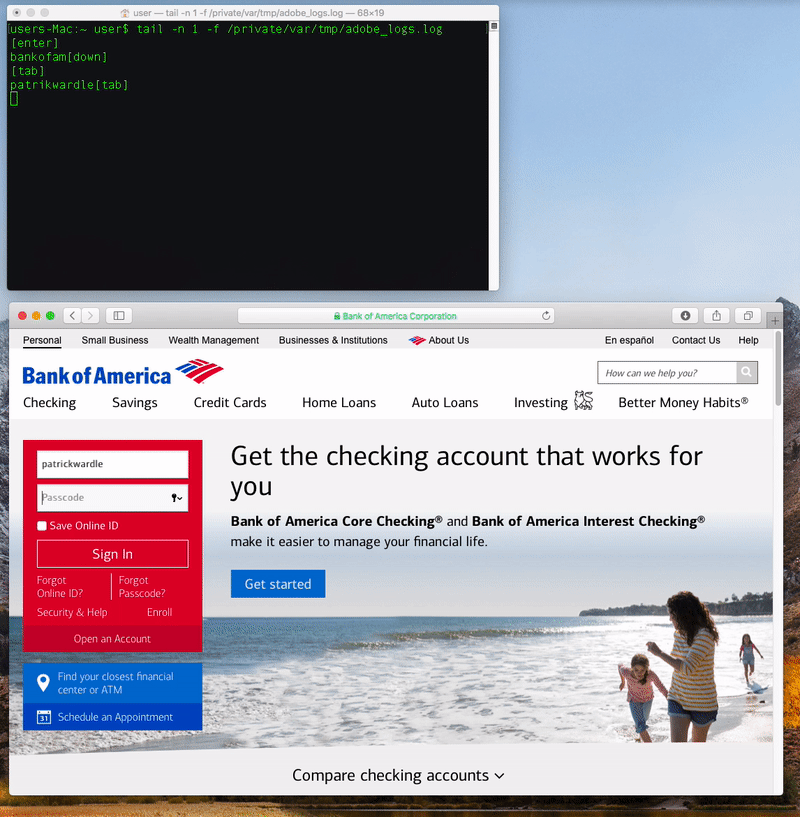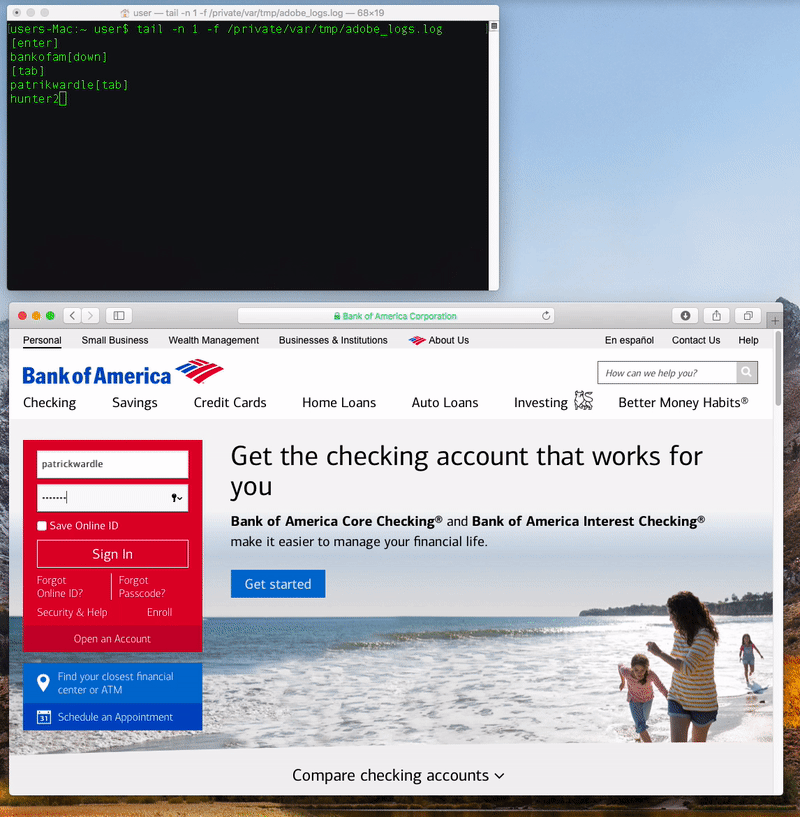
Coldroot’s keylogging in action, as revealed by Wardle.
The RAT also has the capability of performing functions for the attacker such as:
- listing, renaming, or deleting files and folders
- listing the apps that are currently running
- launching or quitting apps
- downloading or uploading files
- determining which window is currently in the foreground
- streaming continuous screenshots to the attacker
- shutting down the computer
Wardle discovered that the developer of Coldroot had uploaded a 27-minute demonstration video in 2016. (The video was removed from YouTube after Wardle found it, but Wardle has posted a mirror of it in his write-up.) The video shows that Coldroot was evidently developed with cross-platform compatibility, capable of controlling infected Windows and Linux systems in addition to Macs.
Is my Mac infected with OSX/Coldroot?
Following are the main indicators of compromise (IoCs). An infected Mac may have components located at the following paths:
- /Library/LaunchDaemons/com.apple.audio.driver.plist
- /private/var/tmp/adobe_logs.log
- /private/var/tmp/com.apple.audio.driver.app
- /private/var/tmp/runme.sh
Network administrators can search Web traffic logs for attempts to access the IP address 45.77.49.118 on port 80.
Why so many RATs in a short period of time?
One might wonder: why were three different Mac RATs—CrossRAT, EvilOSX, and Coldroot—all discovered within a couple months of each other? The answer seems to be simply coincidence. In fact, variants of all three of these RATs were developed in 2017 or earlier, entirely independent of one another.
 Coldroot, according to comments in the YouTube video, was evidently originally released in 2017, and Wardle found a source code repository for an early version that was under development in March 2016. WHOIS records indicate that Mohamed Osama (who goes by the name Coldzer0) evidently registered the domain for Coldroot’s homepage in July 2015. Thus, Coldroot is probably the oldest of the three RATs.
Coldroot, according to comments in the YouTube video, was evidently originally released in 2017, and Wardle found a source code repository for an early version that was under development in March 2016. WHOIS records indicate that Mohamed Osama (who goes by the name Coldzer0) evidently registered the domain for Coldroot’s homepage in July 2015. Thus, Coldroot is probably the oldest of the three RATs.
 CrossRAT is cross-platform Java software, designed to infect Windows and Linux systems in addition to Macs. It is associated with Dark Caracal, a global cyber-espionage campaign that is believed to have nation-state backing. A joint report by Lookout and the Electronic Frontier Foundation indicates that the “version 0.1” sample they found was last modified in March 2017.
CrossRAT is cross-platform Java software, designed to infect Windows and Linux systems in addition to Macs. It is associated with Dark Caracal, a global cyber-espionage campaign that is believed to have nation-state backing. A joint report by Lookout and the Electronic Frontier Foundation indicates that the “version 0.1” sample they found was last modified in March 2017.
 EvilOSX was first discovered almost a year ago, in May 2017. The February 2018 variant may have been noticed in part because of Wardle’s publication of his findings about OSX/Coldroot, which might have prompted others to look further into Mac RATs. Interestingly, in spite of including features that are overtly malicious in nature, EvilOSX is developed as open-source software that’s freely available on GitHub, a popular software development repository. The developer goes by the name Marten4n6.
EvilOSX was first discovered almost a year ago, in May 2017. The February 2018 variant may have been noticed in part because of Wardle’s publication of his findings about OSX/Coldroot, which might have prompted others to look further into Mac RATs. Interestingly, in spite of including features that are overtly malicious in nature, EvilOSX is developed as open-source software that’s freely available on GitHub, a popular software development repository. The developer goes by the name Marten4n6.
How can Mac users protect themselves from RATs?
![]() Keeping your Mac updated with the latest version of macOS, and installing Apple security updates as soon as they’re available in the App Store, are important steps in keeping your Mac protected from a variety of infections.
Keeping your Mac updated with the latest version of macOS, and installing Apple security updates as soon as they’re available in the App Store, are important steps in keeping your Mac protected from a variety of infections.
Wardle notes that the sample of OSX/Coldroot he found will not run on the latest version of macOS High Sierra (which he speculates may be due to a bug related to UPX packing). He also points out that the malware’s attempt to directly modify the system file TCC.db is thwarted by the operating system’s System Integrity Protection (SIP) feature if the user is running macOS Sierra or later.
 Since RATs are designed to run secretively without alerting a user to their presence, and may be installed through any number of methods including as a secondary infection, one of the best ways to protect your Mac from RATs is to use anti-virus software with real-time scanning together with an outbound firewall. (The firewall that’s built into macOS only protects against certain inbound threats, but will not prevent malware on your system from phoning home to an attacker.)
Since RATs are designed to run secretively without alerting a user to their presence, and may be installed through any number of methods including as a secondary infection, one of the best ways to protect your Mac from RATs is to use anti-virus software with real-time scanning together with an outbound firewall. (The firewall that’s built into macOS only protects against certain inbound threats, but will not prevent malware on your system from phoning home to an attacker.)
Intego’s Mac Premium Bundle X9 includes both VirusBarrier X9 and NetBarrier X9, the best commercial anti-virus and firewall software available for Mac. VirusBarrier detects and eradicates OSX/Coldroot, CrossRAT (Java/LaunchAgent), and OSX/EvilOSX.
Editor’s note: This story was updated March 9, 2018 for accuracy and comprehensiveness.Have something to say about this story? Share your comments below!
“Cold root” image composed by Joshua Long using public-domain images of roots and icicles. Caracal and firewall images: Pixabay.