Apple + Recommended + Security News
“I Am Root”: a retrospective on a severe Mac vulnerability
Posted on
by
Joshua Long
 Image credit: Johnathon Burns modified by Gaël
Image credit: Johnathon Burns modified by Gaël
On November 28, the world became aware of a major security vulnerability in macOS High Sierra that could allow an attacker to enable the “root” administrator account on a victim’s Mac.
The bug is being called “#IAmRoot” and “#rootgate” in various online discussions.
We first wrote about the vulnerability here:
Major Authentication Security Flaw Reported in macOS High Sierra [Update]
Apple has since patched the bug, but the severity and nature of the vulnerability are so noteworthy as to warrant a much deeper dive into what happened.
? Grab some popcorn and read on for a story that may entertain and amaze you.
What Is the “I Am Root” Vulnerability?
In unpatched versions of macOS High Sierra 10.13 or 10.13.1, an attacker could invoke a system authentication dialog box, type “root” (the name of a powerful UNIX administrator account that’s disabled by default in macOS), and either enter no password or a password of their choosing, and macOS would enable the root account with the attacker’s chosen password.
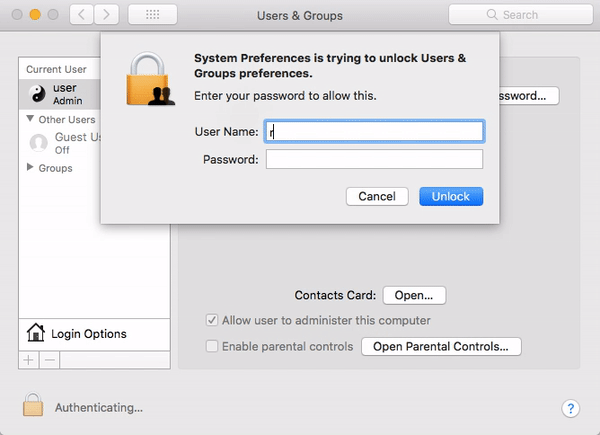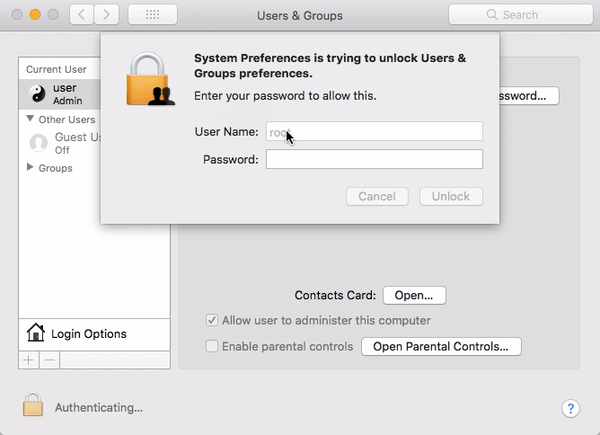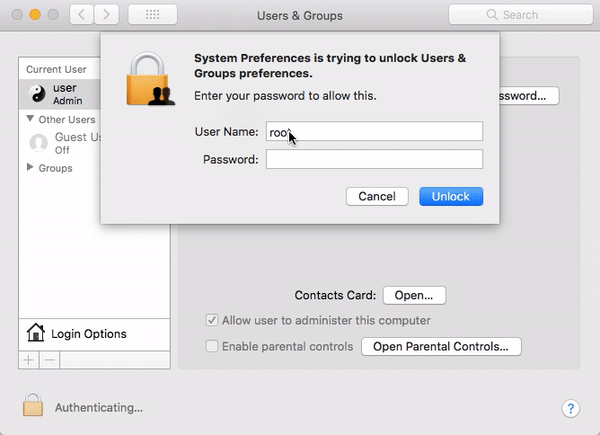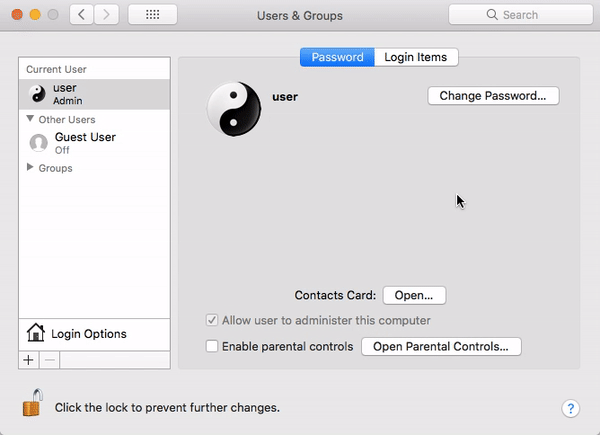 The “I am root” attack in action. Image credit: Patrick Wardle
The “I am root” attack in action. Image credit: Patrick Wardle
Thus, if you were to leave your Mac unattended for less than a minute, someone could simply walk up to your Mac and make their own personal superuser account without your permission or knowledge.
(As an aside, all it would take is a couple more clicks and the attacker could also enable Remote Login, File Sharing, Screen Sharing, and other features so they can continue to control and exploit your Mac after they walk away. Be sure to read How to Lock Your Mac Screen and Protect It from Prying Eyes for a few basic tips on physical security.)
Under normal circumstances, it would be nearly impossible to create your own administrator account on someone else’s Mac without having to first authenticate using an existing administrator account or password. This bug changes that in a big way.
Remote Exploitation
So, you might be thinking, the answer is to never leave your Mac unattended, right? Although it’s probably a good idea to keep your Mac in sight for other reasons, unfortunately, depending on your system’s settings, basic physical security may not be enough to stop an attacker.
If you had the Screen Sharing feature enabled, then an attacker could even enable the root account without physical access to your Mac, as demonstrated in this video by Patrick Wardle:
If certain sharing services enabled on target – this attack appears to work ? remote ??☠️ (the login attempt enables/creates the root account with blank pw) Oh Apple ???? pic.twitter.com/lbhzWZLk4v
— patrick wardle (@patrickwardle) November 28, 2017
Yes, if your Mac had Screen Sharing enabled, then the vulnerability could be exploited by anyone else on your local network. So, for example, your roommate, coworker, or even some miscreant at a public place where you happened to be using Wi-Fi, could have sat in front of their own Mac laptop and enabled the root account on your computer without your knowledge or permission.
The attacker could then log into your computer as root via Screen Sharing, which would then enable them to turn on Remote Login and File Sharing, as noted above.
How Did This Vulnerability Become Known?
The earliest known disclosure of the vulnerability was a post to the Apple developer forums on November 13, in which a developer shared this as a possible way to enable the root account that had worked for him.
The developer said that he had read about this method of enabling root elsewhere on the forums, but when asked to find the original post he wasn’t able to locate it. He was also apologetic, stating that he hadn’t realized that what he described was a major security flaw.
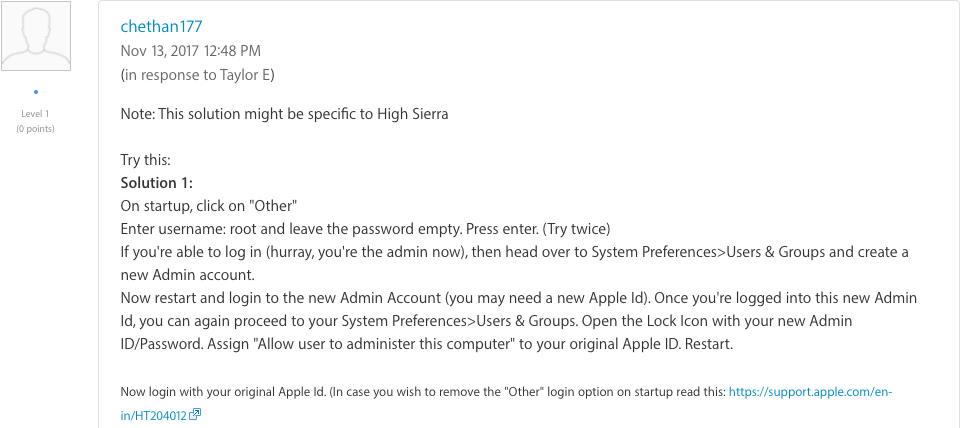
The first known disclosure of the “I am root” bug. Image: Apple via Internet Archive
A week later, on November 20, a Twitter user shared a video demonstrating the bug on Twitter and tagged Apple in the tweet, but Apple did not respond or take action.
#Meta #ThisIsNotOkay #SecurityThruObscurity #RightToRepair #FollowTheMoney @Apple https://t.co/MEUSxGoCX2 @GIPHY @* pic.twitter.com/QZkcJKNty5
— @jeremydmiller78 (@jeremydmiller78) November 20, 2017
Eight days after that, on November 28, a developer from Turkey posted about it publicly with a much more clear description, and tagged both Apple and Apple Support. This tweet went viral.
Dear @AppleSupport, we noticed a *HUGE* security issue at MacOS High Sierra. Anyone can login as “root” with empty password after clicking on login button several times. Are you aware of it @Apple?
— Lemi Orhan Ergin (@lemiorhan) November 28, 2017
It is generally considered to be a poor practice to publicly disclose the full details of a vulnerability, including the exact steps required to exploit it, without first privately disclosing the bug to the developer and giving the developer a reasonable amount of time to investigate and fix the issue. This type of full public disclosure leaves all users of a platform vulnerable to a widely known zero-day attack until the developer can release a patch.
Did Apple Create the Vulnerability?
The “I am root” vulnerability itself seems to have been the result of a programming logic error introduced in macOS High Sierra by Apple’s development team. For those who may be interested in the full technical details, you can read this write-up by Mac security researcher Patrick Wardle.
But how could Apple have released macOS High Sierra without being aware of such a tremendously serious vulnerability? Has anything like this ever slipped past Apple’s quality control engineers before?
Previous Major Flaws in macOS
The nature of the “I am root” bug is reminiscent of the “goto fail” vulnerability.
In 2013, early versions of OS X Mavericks 10.9 as well as iOS 6.1 and 7.0 were found to have a very simple programming glitch, specifically the inclusion of a single duplicated line of code, that created a gaping security hole in the operating systems. That one erroneous line of code made it easy for a “man in the middle” attacker to maliciously intercept or alter Mac or iOS users’ HTTPS encrypted traffic. (Search for “goto fail” in this article to learn more.)
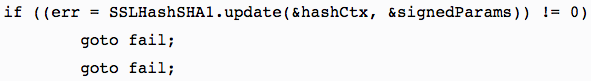
“goto fail;”: One duplicated line of code caused a severe security glitch in 2013.
The timing of “goto fail” couldn’t have been worse for Apple, as the bug was revealed shortly after Edward Snowden had turned the spotlight on the National Security Agency’s alleged mass surveillance of U.S. citizens. Given that Snowden was fresh in people’s minds, some conspiracy theorists hypothesized that perhaps Apple’s “goto fail” bug might have been evidence of collusion with the U.S. government (notably, there was never any evidence to support this conspiracy theory).
Like “goto fail,” the “I am root” bug seems to have been caused by a fairly simple programming error made by Apple engineers that wasn’t noticed until after the operating system was released.
Apple’s Apology
After releasing the patch, Apple gave the following statement to news outlets on Wednesday, November 29, apologizing for the vulnerability:
Security is a top priority for every Apple product, and regrettably we stumbled with this release of macOS.
When our security engineers became aware of the issue Tuesday afternoon, we immediately began working on an update that closes the security hole. This morning, as of 8 a.m., the update is available for download, and starting later today it will be automatically installed on all systems running the latest version (10.13.1) of macOS High Sierra.
We greatly regret this error and we apologize to all Mac users, both for releasing with this vulnerability and for the concern it has caused. Our customers deserve better. We are auditing our development processes to help prevent this from happening again.
Conclusion (Let’s Hope)
Apple deserves credit for being so quick to release a patch for the vulnerability after knowledge of the bug went viral.
It’s also great that Apple chose to apply the patch automatically to affected systems. (If you’re not sure whether your systems have been patched, scroll to the bottom of our initial article about the vulnerability to find out how to check.)
Apple began installing the security update automatically on November 29.
Although it’s pleasing to hear that Apple is “auditing [its] development processes,” one has to wonder why this higher level of scrutiny wasn’t already in place four years ago after “goto fail” became known to the public.
Between this and the Keychain password exfiltration-enabling bug discovered in September, Apple has been having a bit of a rocky start with High Sierra.
Let’s hope that Apple keeps its promise and dedicates more resources to keeping major, preventable security flaws from making their way into its operating systems.