Watch Out! A Fake Antivirus Blog is Distributing Proton Malware
Posted on
by
Jay Vrijenhoek

A new variant of OSX/Proton has been uncovered this week by malware researcher “noar” (@noarfromspace). The previous iteration of Proton malware, discovered in October, had targeted Eltima, the makers of the Elmedia Player software. This time, OSX/Proton is being distributed as part of a fake antivirus scanner, named “Symantec Malware Detector,” found on a Symantec security blog that is equally fake.
The blog symantecblog(.)com is a professional looking clone of the real Symantec blog, and even has a post on it about a “new version” of CoinThief, a trojan from a few years ago. The trick post concludes with the following recommendation:
“To scan the system for all traces of the malware and completely remove CoinThief from the preinstalled software you can use our free tool – Symantec Malware Detector.”
The truth is there is no new version of “CoinThief” malware, and the recommended Symantec Malware Detector is nothing but a way to con Mac users into installing a new variant of OSX/Proton. Intego VirusBarrier identifies and eradicates this new variant of Proton malware as OSX/Proton.D.
How does Proton malware install?
Those who download and run the fake antivirus are greeted with a window that sports the Symantec brand along with a small agreement notice.

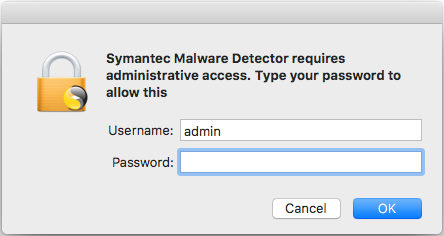
Clicking the “Check” button will prompt for administrative login credentials. This prompt also looks genuine.
Once the password is entered, OSX/Proton.D has everything it needs to install. Users will be presented with a scan in progress, which is, of course, also fake — Proton malware will install in the background.

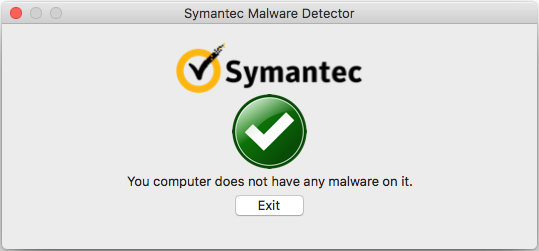
When the fake scan completes, the all-clear is given and the application can be quit.
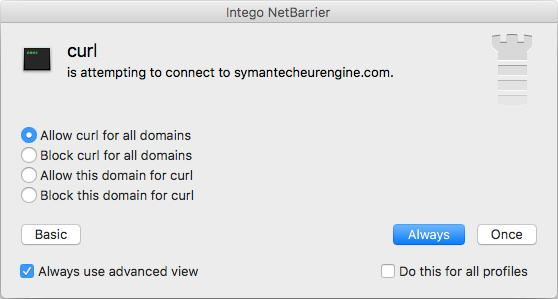
If a good firewall is used, you can see the malware even attempts to connect to symantecheurengine(.)com, which at first glance does not appear suspicious as the application specifically mentioned a heuristic engine during setup. However, a closer look at that domain shows this is also a fake. Typing it in to a browser window will simply redirect to the fake Symantec website as it only accepts traffic on a specific port, but a lookup of the domain quickly reveals this is not a Symantec domain.
The registration details mention an @protonmail.com address and the hosting is not one Symantec uses. The registration date is also just a few days old.
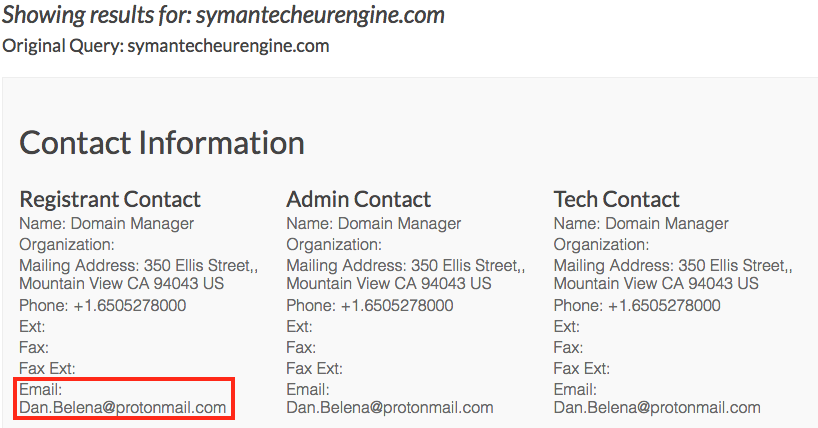
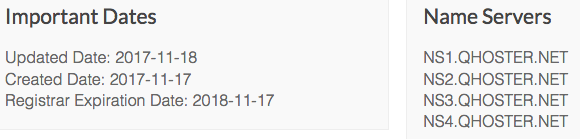
This domain is most likely the Command & Control (C&C) server as it is pinged by the malware often.
The use of a protonmail email address is also observed when checking the registration of the symantecblog(.)com domain.


What can OSX/Proton.D do on infected Macs?
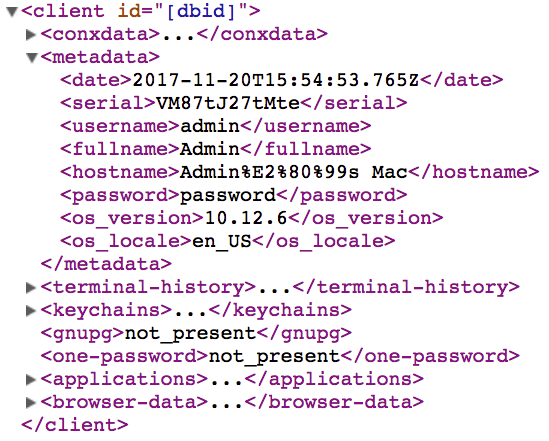
If a Mac user followed all of the above steps installing the malware, OSX/Proton.D will have already collected several pieces of information and stored them in a hidden directory, waiting to be uploaded. Information gathered by OSX/Proton includes:
- A screenshot of the desktop
- Your user name and password
- IP address
- Version of macOS
- Hardware serial number
- List of the last run terminal commands
- Contents of your system and local Keychains
- List of installed applications
- Browser history and stored cookies
- 1Password vaults
- GPG passwords
And this is just what’s collected upon installation. With the administrator name and password available, the contents of the Mac Keychain can be accessed right away, which gives those behind this latest OSX/Proton access to social media accounts, online banking and much more sites and services that have their info stored in the keychain.
Should Mac users be concerned about Proton?
It’s clear by now that OSX/Proton is a successful backdoor, so we expect it will be used more in the future. What makes it successful is the way it’s distributed, not the malware itself (which is still pretty rudimentary in how it keeps itself active). By going after supply chains, like it did with Transmission and Eltima, and now through faking a legitimate security blog, malicious actors have found ways to get the malware onto more systems. Even those who never download software from bad sources, never click suspicious pop-ups, and never click links in emails that look suspect can become infected.
How to tell if your Mac is infected (and removal instructions)
Open Activity Monitor and search for a process named “xpcd.” If this process is running, your Mac is infected.
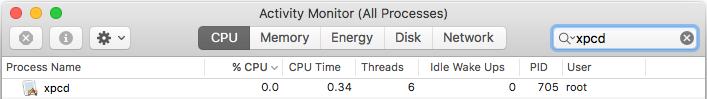
Click the process, and then close it with the X button in the menu bar.
To clear the infection off your Mac, browse to the following folders and trash the following files:
- Applications* – Delete the Symantec Malware Detector application.
*It may also be in your Downloads folder or on your Desktop. - Library > LaunchAgents > com.apple.xpcd.plist – Delete this file.
To manually check for the invisible files OSX/Proton placed, first you need to make invisible files visible in the Finder. In macOS Sierra and High Sierra, this can quickly be done with the following key combination:
Command-Shift-. (period)
For older OS X versions, this can be done by typing the following commands in the Terminal app:
$ defaults write com.apple.Finder AppleShowAllFiles true $ killall Finder
When done, enter the same commands but change “true” to “false.”
With the hidden files now visible, check both the root library and the user library for these files:
- Library > .cachedir – Delete this directory (this holds the collected data)
- Library > .random – Delete this directory (this holds the OSX/Proton backdoor)
With those files deleted, empty the trash and restart your Mac. Double-check the same locations again after the restart to ensure the infection is indeed cleared. If a warning shows that some items cannot be deleted, because they are in use, you’ll be able to empty the trash after the restart.
For Intego’s Mac anti-virus customers, protection comes in the form of updated malware definitions, which will detect and remove all of the Proton files. Proton components are detected by Intego VirusBarrier as OSX/Proton.D.
How to protect yourself from Proton
Running Mac antivirus with up to date malware definitions is always recommended. In this way, malware can be caught before it even has a chance to install. The use of a good firewall is also highly recommended, because newly discovered malware must be added to the product definitions before it’s able to find and eliminate the malware. While this is typically done within hours of a new malware discovery, there is always a small gap. A firewall does not require definition updates; after all, network traffic is network traffic.
Even if no antivirus product is used, a firewall will show you when an application or process attempts to phone home. This gives you time to research the information displayed and make an informed decision to allow or deny the connection. For example, here is what Intego NetBarrier users will see upon catching OSX/Proton’s attempt to contact the fake domain: