Fake App Store pages are the new fake Flash Player alerts
Posted on
by
Joshua Long

For more than a decade, I’ve been writing about malicious results in search engines. Poisoned search results may appear anywhere, even in Google, Bing, or other popular search engines.
Search results contain links to pages that appear to have valuable information. But not every link in the list is necessarily helpful.
In fact, search results can be worse than unhelpful—they can also be unsafe. They may lead to malware, phishing sites, or other scams.
In this article:
- The latest scam: mimicking App Store pages
- The consequences of clicking
- How can I check whether my Mac is infected?
- What can I do to prevent infection?
- Additional technical details
- How can I learn more?
The latest scam: mimicking App Store pages
Historically, Web-based malware campaigns targeting Mac users have often led to fake Flash Player pop-up warnings, which led to Trojan horse downloads claiming to be Flash updaters or installers.
This week, Kirk McElhearn (veteran Mac journalist, Intego writer, and fellow Intego Mac Podcast host) texted me an interesting screenshot:
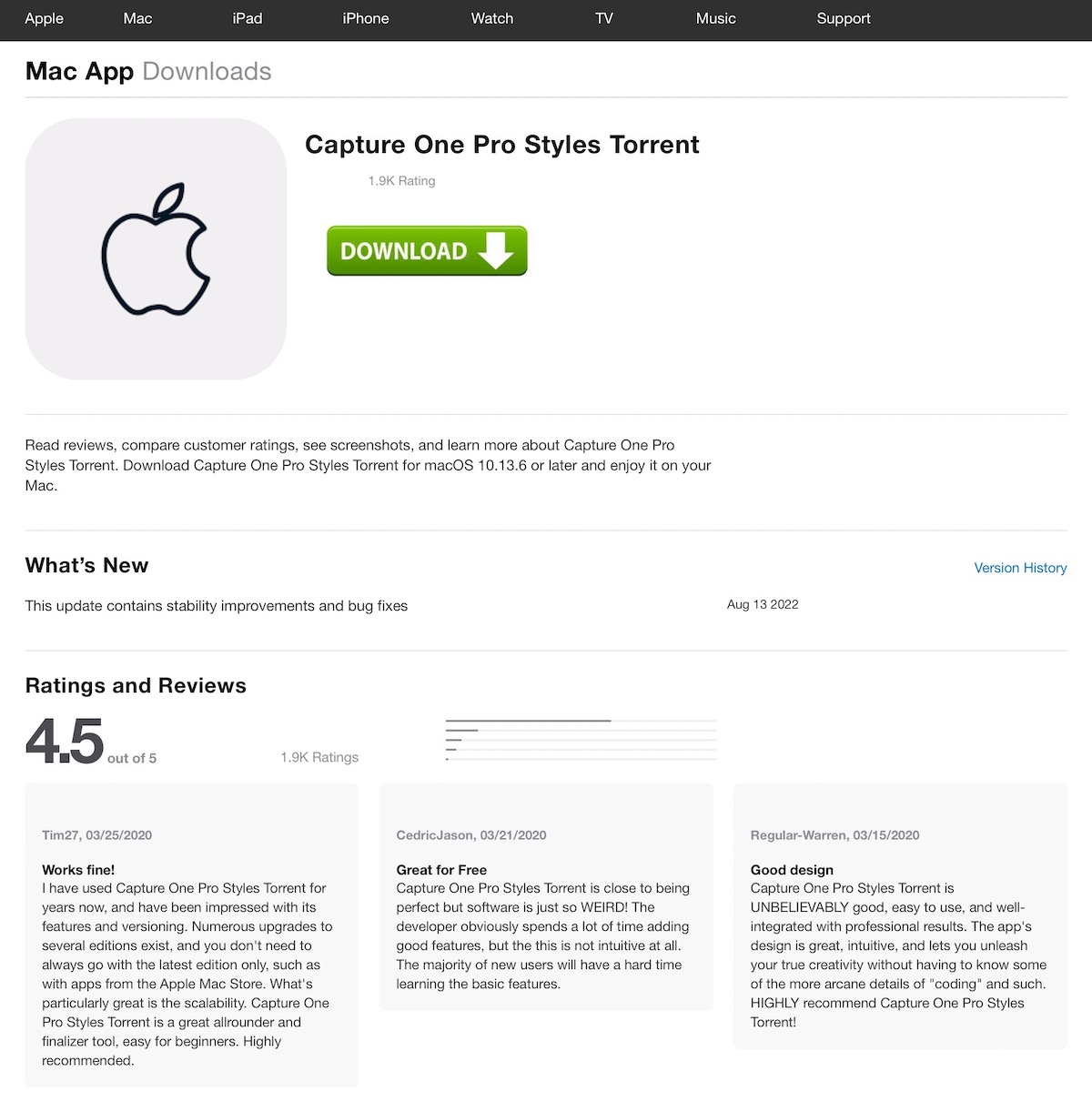
At first glance, one might be tempted to think that this is a legitimate page for an app available in the App Store. But upon closer inspection, some things don’t seem quite right—at least to a savvy user.
The big, green “download” button with a down-facing arrow doesn’t look like something Apple would ever use. Where you’d expect to see an app icon, in this case there’s an outline of the Apple logo on a gray background. And the title of this “app” contains the word Torrent; you’d never find torrents or BitTorrent client software in the App Store.
But it’s quite likely that the average Mac user would not immediately recognize those warning signs. And that’s exactly what the page is banking on.
The consequences of clicking
If you click on the download button on a page like this, you may be redirected to Mac malware (for example, a Bundlore variant disguising itself as an Adobe Flash Player installer, if you can believe that; Flash was discontinued in 2020).
You might instead be redirected to a page designed to trick you into creating an account, thereby capturing your real e-mail address and a password. Given that many people reuse the same password on multiple sites, the site operators could potentially use this to hack into your e-mail, Facebook, or other accounts.
How can I check whether my Mac is infected?
If you think you may have unintentionally downloaded malware onto your computer, download a free trial of Intego’s Mac or Windows software and start a scan.
To avoid future infections, follow the tips below.
What can I do to prevent infection?
If you encounter a malicious site like the one described above, simply close the browser tab or page by pressing Command-W (⌘W).
Whenever possible, download software directly through Apple’s App Store app, which comes preinstalled on your Mac, iPhone, or iPad. If a Mac app that you need isn’t available in the App Store, go directly to the software developer’s site to learn how to purchase or download it.
Be sure to use anti-malware protection software from a trusted developer, like Intego’s Mac Premium Bundle X9 or Intego Antivirus for Windows.
Additional technical details
Intego VirusBarrier X9 detects this malware as OSX/Bundlore.BEa. This malware family is also sometimes called Bnodlero.
Intego’s research team has encountered numerous examples of these malicious pages hosted on subdomains of weebly.com, a free Web page hosting site. Similar fake App Store pages may be found elsewhere on the Web as well.
We also observed multiple variations on this theme. Sometimes the fake App Store page claimed to offer Google Chrome (which, in reality, cannot be found in the Mac App Store). Aside from fake App Store pages, we also observed fake MediaFire download pages.
These fake download screens appeared after the weebly-hosted pages had begun to load. Upon closer inspection, we found that the weebly sites’ HTML code contained embedded JavaScript code that loaded an iframe (or inline frame). This has the effect of invisibly loading a page hosted on a malicious domain, embedded within the weebly site.
Advanced users may be interested to know that blocking JavaScript in your browser (using NoScript, for example) may therefore in some cases prevent the fake App Store screen from loading. However, blocking JavaScript breaks most legitimate Web sites, too, so this technique is not recommended for most users.
Some of the malicious or compromised domains we observed included the following (WARNING: visiting these sites may lead to malware):
aleleim[.]info asasasasasa[.]vet asetar[.]info basati[.]info bltlly[.]com crophysi[.]ru ehgum[.]xyz euletep[.]top gobitta[.]info iminna[.]info nulnerk[.]top operaterefinedcompletelytheproduct[.]vip orafukz[.]xvz otucxiixa[.]xyz qaadxet[.]cfd siiwafami[.]xyz vovantrafline[.]com xiolade[.]info
How can I learn more?
To read some of our past research into search engine poisoning campaigns, you can check out:
- New Mac malware reveals Google searches can be unsafe (2020)
- OSX/CrescentCore: Mac malware designed to evade antivirus (2019)
- How SEO Poisoning Works and Why You Should Care (2011)
- So You Think You Can Trust Google Results (2009)
- ‘New Moon’ Movie Attracts Malware Makers (2009)
- What ‘Dr. Seuss Coloring Pages’ and ‘Red Spots on Face’ Have in Common (2009)
 Each week on the Intego Mac Podcast, Intego’s Mac security experts discuss the latest Apple news, security and privacy stories, and offer practical advice on getting the most out of your Apple devices. Be sure to follow the podcast to make sure you don’t miss any episodes.
Each week on the Intego Mac Podcast, Intego’s Mac security experts discuss the latest Apple news, security and privacy stories, and offer practical advice on getting the most out of your Apple devices. Be sure to follow the podcast to make sure you don’t miss any episodes.
You can also subscribe to our e-mail newsletter and keep an eye here on The Mac Security Blog for the latest Apple security and privacy news. And don’t forget to follow Intego on your favorite social media channels: ![]()
![]()
![]()
![]()
![]()
![]()
![]()