New Mac malware reveals Google searches can be unsafe
Posted on
by
Joshua Long

Intego has discovered new Mac malware in the wild, actively spreading through malicious results in Google searches.
The new malware tricks victims into bypassing Apple’s built-in macOS security protections, and it uses sneaky tactics in an effort to evade antivirus detection.
As of Friday, the new malware installer and its payload had a 0/60 detection rate among all antivirus engines on VirusTotal. Intego VirusBarrier is the first anti-malware solution that is known to detect and remove this malware.
Intego identifies the new malware as unique new variants of OSX/Shlayer (the original variant of which was first discovered by Intego in 2018) and OSX/Bundlore (with similarities to past versions of OSX/MacOffers and Mughthesec/BundleMeUp/Adload).
In this article:
- What does the new malware do? How is it unique?
- Is this malware in the wild? How does it spread?
- Can’t Google stop this?
- How does the malware bypass protections built into macOS?
- How can the malware be removed?
- Are there a lot of victims of this specific malware?
- What is known about the creators of this malware?
- Indicators of compromise
- How can I learn more?
What does the new malware do? How is it unique?
As is commonly seen in Mac malware, this newly updated Shlayer malware is delivered as a Trojan horse application on a .dmg disk image, masquerading as an Adobe Flash Player installer.
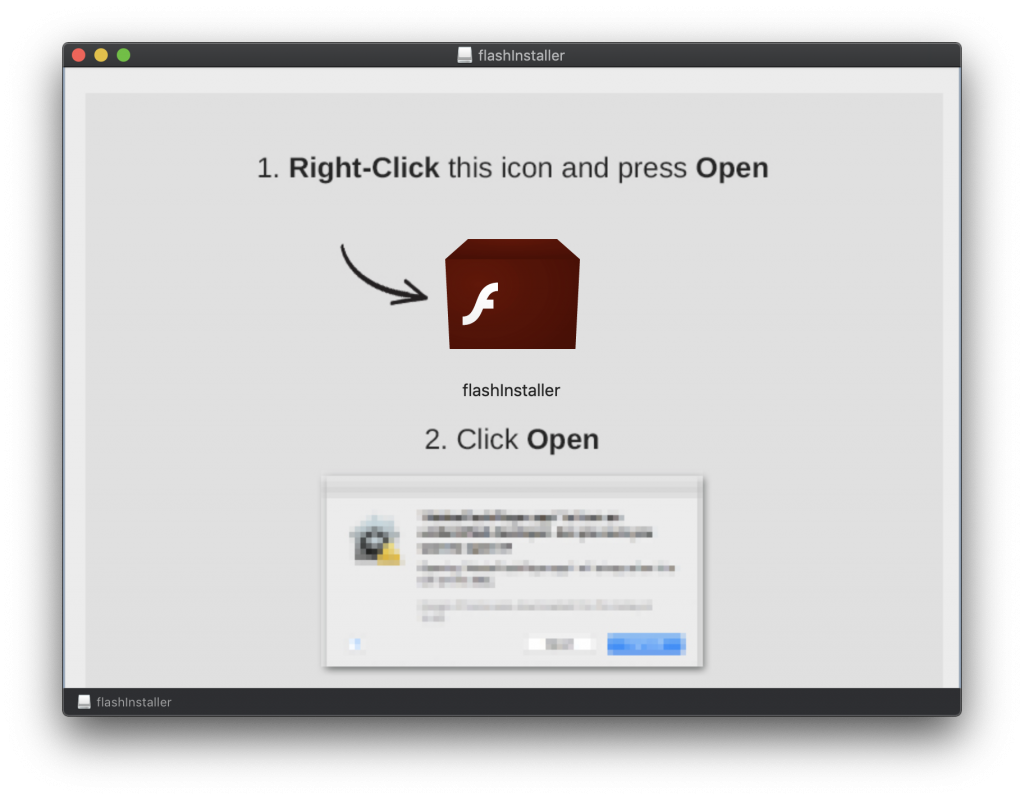
Note: The “censored” appearance is how it actually appears on victims’ Macs.
After the deceptive Flash Player installer is downloaded and opened on a victim’s Mac, the disk image will mount and display instructions on how to install it. The instructions tell users to first “right-click” on flashInstaller and select Open, and then to click Open in the resulting dialog box.
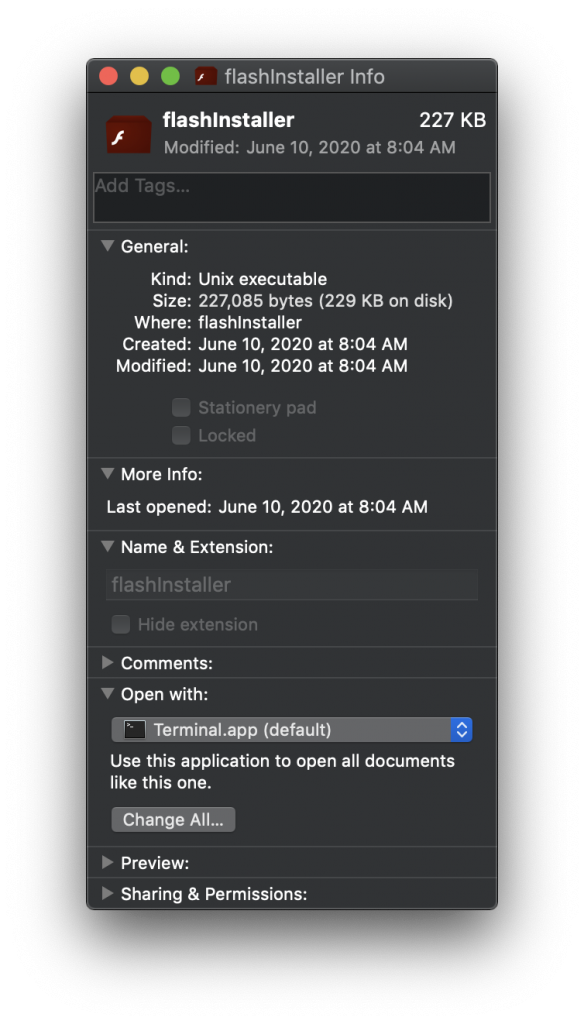
“Get Info” window for the flashInstaller file
If a user follows the instructions, the “installer app” launches. While the installer has a Flash Player icon and looks like a normal Mac app, it’s actually a bash shell script that will briefly open and run itself in the Terminal app.
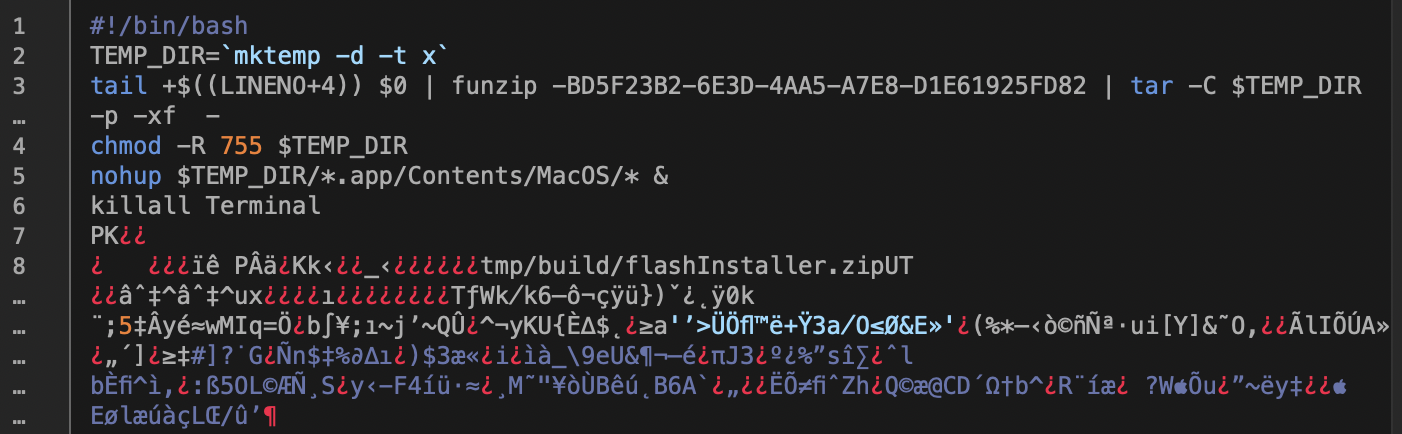
A portion of the script’s code, showing the beginning of the embedded .zip file
As the script runs, it extracts a self-embedded, password-protected .zip archive file, which contains a traditional (though malicious) Mac .app bundle. After installing the Mac app into a hidden temporary folder, it launches the Mac app and quits the Terminal. All this takes place within a split second.
Once the Mac app launches, it downloads a legitimate, Adobe-signed Flash Player installer, so that it can appear to be genuine—but the hidden Mac app is designed to also have the capability to download any other Mac malware or adware package, at the discretion of those controlling the servers to which the hidden Mac app phones home.
The developers’ decision to hide the Mac .app within a password-protected .zip file, and to hide that within a bash shell script, is a novel idea—and it is also extremely clear evidence that the developers are trying to evade detection by antivirus software.
Is this malware in the wild? How does it spread?
While searching Google for the exact titles of YouTube videos, Intego’s research team encountered Google search results that, when clicked, pass through multiple redirection sites and end up on a page that claims the visitor’s Flash Player is out of date, and displays deceptive warnings and fake dialog boxes to entice the victim to download a supposed Flash Player updater—which is, in fact, a Trojan horse.
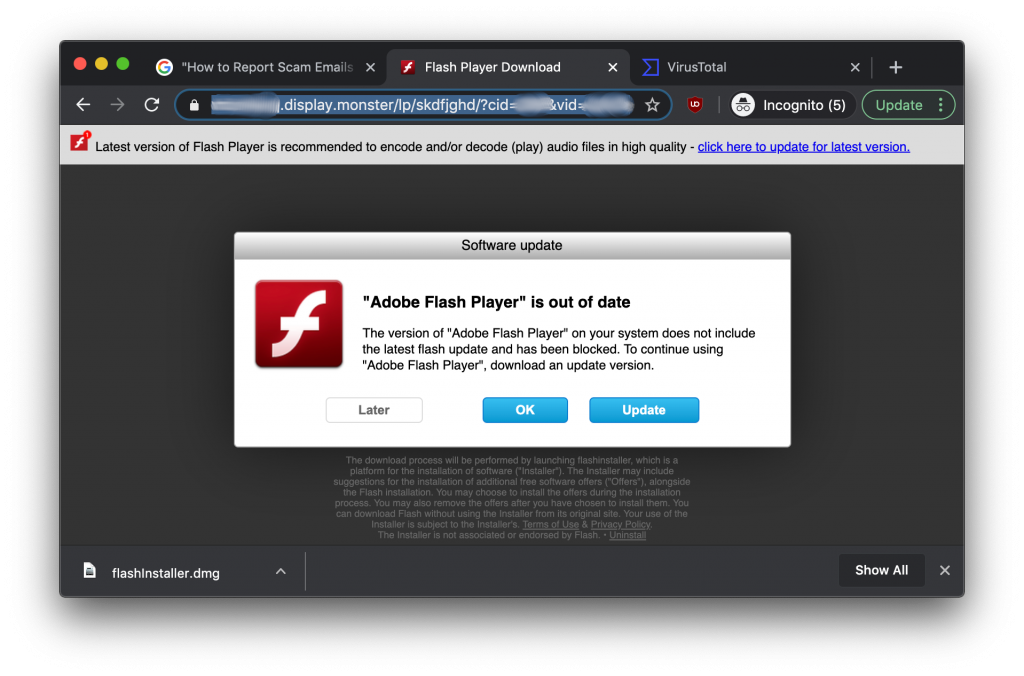
This newly re-engineered malware purports to be a legitimate Flash Player installer, but it has the capability to surreptitiously download and install additional unwanted packages containing adware or spyware.
 This is far from the first time that search engine results have led to in-browser fake dialog boxes and malicious downloads; this has been happening for more than a decade.
This is far from the first time that search engine results have led to in-browser fake dialog boxes and malicious downloads; this has been happening for more than a decade.
Last year, Intego was also the first to discover OSX/CrescentCore, another example of search results leading to Mac malware. Like the new Shlayer variant, CrescentCore was a Trojan horse disguising itself as a Flash Player installer.
Can’t Google stop this?
Although in this particular case the malware was found via Google search results, the same thing could happen with any search engine: Bing, Yahoo!, DuckDuckGo, Startpage, Ecosia, or any others.
Search engines face numerous challenges in trying to prevent poisoned search results that lead to malware.
For one thing, malware is constantly changing in order to evade detection, as evidenced by this new malware campaign. Even if Google had scanned the site for known malware before indexing it, Google wouldn’t have found any, because the malware was brand new and as-yet undiscovered.
For another thing, pages are often designed to dynamically present different content depending on the context. If a Web server determines that Google is crawling the site, it may present an entirely different page from the one you might see if you go directly to the URL in your browser—and that page may be different from the page you’d see if you click on a link in Google search results (meaning google.com is the “referrer”), as was the case with this campaign.
It may not be an impossible task, but it’s certainly a significant challenge to try to keep all potentially harmful content from appearing in search results.
Intego has reported the known-malicious search results to Google.
How does the malware bypass protections built into macOS?
A lot of Mac malware in the past couple years has been “signed” by an Apple Developer Account, meaning that the malware maker has paid for an Apple account (or at least hijacked a legitimate developer’s account) in order to get special access to developer resources (and, in some cases, less scrutiny from built-in protections in macOS).
Interestingly, the makers of this malware didn’t even bother getting an Apple Developer Account. Instead, they used a sneaky tactic to trick victims into bypassing Apple’s built-in protections.
Normally, as of macOS Catalina, users will see a dialog box like this if they double-click on a Mac app that isn’t signed with a valid (and non-revoked) Apple Developer Account:
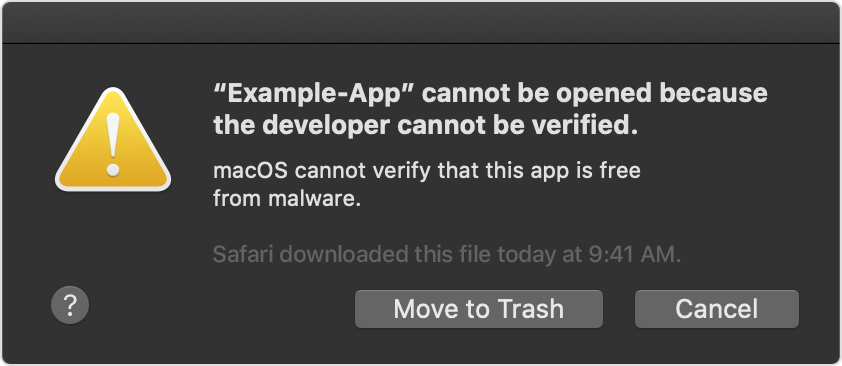
Catalina alert message: “macOS cannot verify that this app is free from malware.” Image: Apple.
By tricking a user into “right-clicking” (Apple calls this Control-clicking) on a malware app and clicking Open, victims will instead see a dialog box more like this:
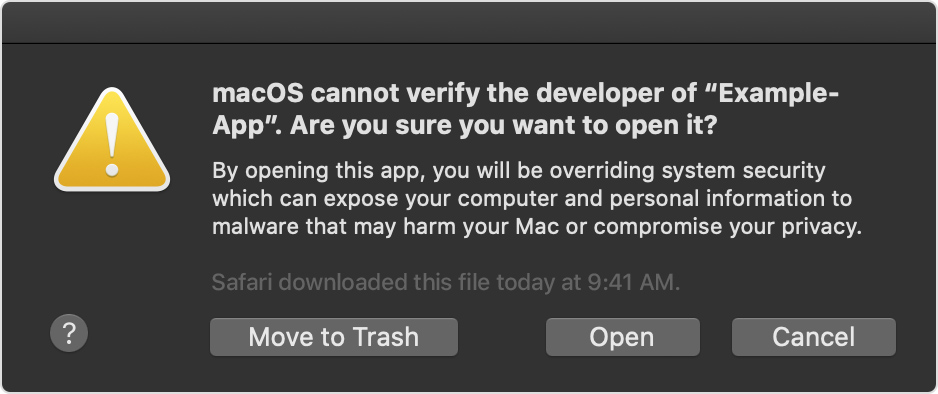
Catalina alert message: “By opening this app, you will be overriding system security which can expose your computer and personal information to malware that may harm your Mac or compromise your privacy.” Image: Apple.
Note that in this slightly different dialog box, there’s an “Open” button. In this case, the malware makers are hoping you’ll ignore Apple’s fine print and instead blindly follow the instructions from the malicious disk image’s background image.
How can the malware be removed?
Intego VirusBarrier X9, included with Intego’s Mac Premium Bundle X9, can detect and eliminate this malware. (Customers running VirusBarrier X8, X7, or X6 on older versions of Mac OS X are also protected.)
Very few other third-party antivirus solutions are known to detect it, as of when this article was last updated.
Are there a lot of victims of this specific malware?
In general, fake Flash Player installers seem to be very successful, since Mac malware makers have continued to use Flash installers as a Trojan horse for nearly a decade.
Related: Adobe Flash Player is dead, yet 10% of Macs are infected with fake Flash malware
Adobe Flash Player is dead, yet 10% of Macs are infected with fake Flash malware
For this specific malware campaign, it remains unclear how many sites are offering the malware and how many varieties of search results are poisoned. Because the malware is brand new, it remains to be seen how widespread infections are.
However, there is a design flaw in the initial stage of the malware that may help prevent infections from escalating beyond opening the disk image. After the disk image mounts, it instructs the victim to “right-click” on the installer, which may be a bit puzzling to many casual Mac users. Unlike typical Windows PCs, there is no obvious right-side button on Apple mice and trackpads. Therefore, novice Mac users may not know how to do the Mac equivalent of a right-click, and therefore may not understand how to run the malware installer script.
What is known about the creators of this malware?
The company behind this malware has chosen a rather generic name for itself, FlashDownloader, and they claim in their license.txt file that you can contact them at [email protected]. The domain flashdownloader[.]pro was registered on June 8, 2020, just days before the malware was first observed in the wild.
Interestingly, it appears that the company behind this new Shlayer variant also has ties to a supposedly “safe, secure and fast” Web browser with a built-in “free VPN” for Windows, and they claim that a Mac version is coming soon.
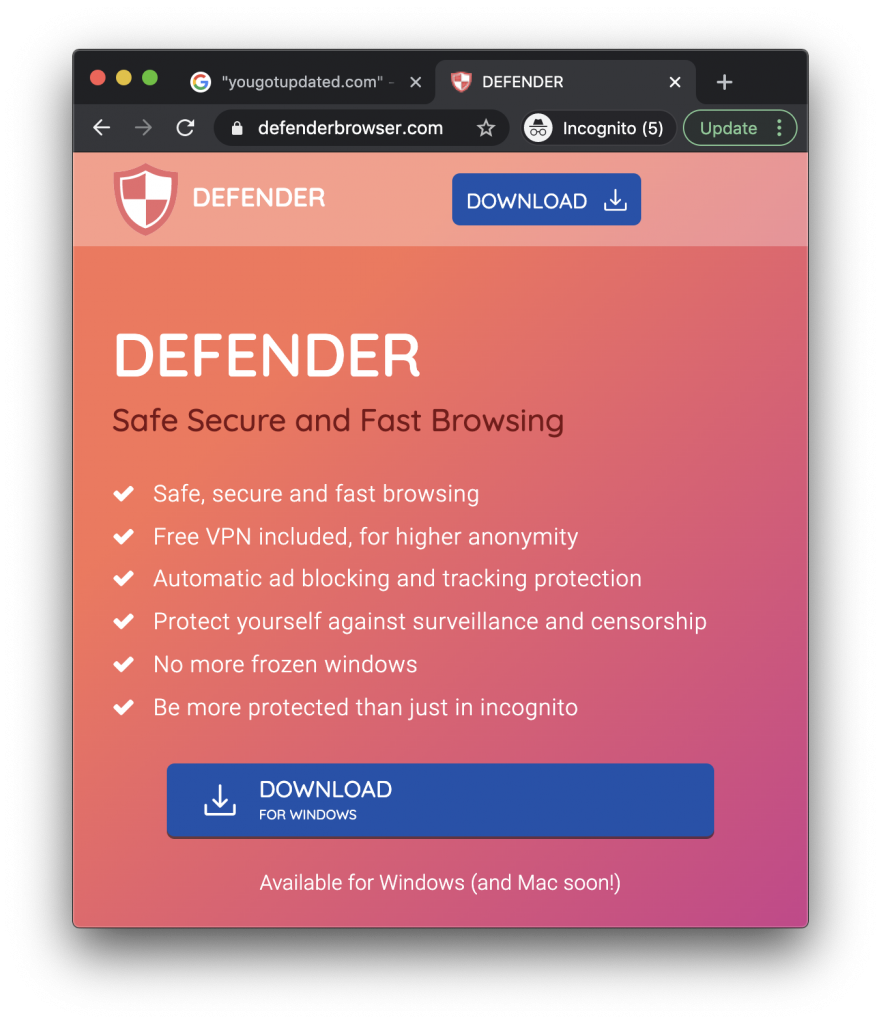
The Windows version of this browser is not currently detected as a potentially unwanted program (PUP/PUA) by any anti-malware software, according to VirusTotal. However, as we’ve previously warned our blog readers and podcast listeners, it’s good to be a bit skeptical about things that normally cost money but that someone claims to offer completely free (for example, a free VPN service). If a service that’s expensive to operate is being offered free of charge, this often means that your data is the product that generates revenue for the company.
Indicators of compromise
The following SHA256 hashes have been observed so far from this malware campaign:
flashInstaller.dmg disk image; initial download, usually in ~/Downloads d49ee2850277170d6dc7ef5f218b0697683ffd7cc66bd1a55867c4d4de2ab2fb 97ef25ad5ffaf69a74f8678665179b917007c51b5b69d968ffd9edbfdf986ba0 flashInstaller bash script; installer on disk image; unsigned 86561207a7ebeb29771666bdc6469d81f9fc9f57eedda4f813ca3047b8162cfb 2c2c611965f7b9c8e3524a77da9b2ebedf1b7705e6276140cffe2c848bff9113 flashInstaller.zip temp file created by the script 3cd3f207a0f2ba512a768ce5ea939c1aed812f6c8f185c1838bfc98ffd9b006e bdbfefab84527b868eb073ece6eff6f5b83dc8d9ed33fe0a824ffee3b9f47b6e Installer found within a .app in a subfolder of /private/var/folders Mach-O macOS binary; self-signed 05b9383b6af36e6bf232248bf9ff44e9120afcf76e50ac8aa28f09b3307f4186 907c31b2da15aa14d06c6e828eef6ca627bd1af88655314548f747e5ed2f5697
The following domains have been observed as directly affiliated with this malware campaign, i.e. fake Flash warnings, file hosting, or communication servers:
youdontcare[.]com display[.]monster yougotupdated[.]com installerapi[.]com uzasignals[.]com
Any network traffic to or from the domains above should be considered a possible sign of an infection.
There is also some evidence to suggest that the following additional domains may be related to this campaign in various ways:
flashdownloader[.]pro defenderbrowser[.]com installvibes[.]com
Update: A couple weeks after Intego published this article, a separate analysis of this malware was written up by Phil Stokes at SentinelOne’s blog, which contains additional IOCs for related samples.
How can I learn more?
 We talked about this new malware on episode 140 of the Intego Mac Podcast—be sure to subscribe to make sure you don’t miss any episodes. You’ll also want to subscribe to our e-mail newsletter and keep an eye here on The Mac Security Blog for the latest Apple security and privacy news.
We talked about this new malware on episode 140 of the Intego Mac Podcast—be sure to subscribe to make sure you don’t miss any episodes. You’ll also want to subscribe to our e-mail newsletter and keep an eye here on The Mac Security Blog for the latest Apple security and privacy news.
You can also follow Intego on your favorite social and media channels: Facebook, Instagram, Twitter, and YouTube (click the 🔔 to get notified about new videos).