Multi-Platform Proof of Concept Virus Clapzok.A Examined
Posted on
by
Arnaud Abbati
A multi-platform virus, named Multi/Clapzok.A, have been released by researcher JPanic. It is written in Assembly, and targets Windows, Linux and OS X 32-bit executables.
This proof of concept is an update of JPanic’s Capzloq Tekniq (2006), that targets Windows and Linux operating systems. The OS X infection process is similar to the concept Roy G Biv exposed with MachoMan (2006) on VX Heavens.
Peter Ferrie, Principal Anti-virus Researcher at Microsoft Corporation, has published an analysis in the Virus Bulletin issue of June 2013. While this content is only available to subscribers, well known reverser Fractal Guru also published a technical analysis of the OS X infection on his blog.
In short, when the virus is executed, it looks for other 32-bit executables (either Windows, Linux or OS X native and FAT binaries) to replicate itself.
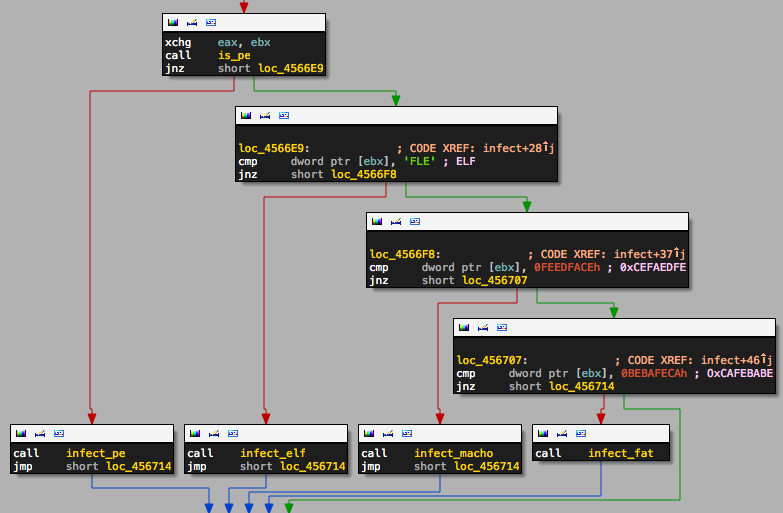
On OS X, it modifies the __PAGEZERO load command to store its code, then changes the entry point in LC_UNIXTHREAD to trigger its execution. It then restores the original entry point in memory, so the infected program can run normally.
It does not infect 64-bit executables (shellcode is 32-bit) or programs built with the latest Developer Tools, where GCC’s LC_UNIXTHREAD has been replaced by LC_MAIN in Clang. Also, fat binaries that contain both i386 and x86_64 architectures, running on a 64-bit machine, won’t execute the virus payload. Finally, a code-signed binary would detect the modification.
Despite the significant limitations, this academics research is interesting as it exposes simple caveats Apple hasn’t patch since 2006.
JPanic has not published his source code yet, and our malware researchers have not spotted any malicious use of his work.
Intego VirusBarrier with latest Virus Definitions detect Multi/Clapzok.A and similar __PAGEZERO load command abuses.