Two-Factor Authentication: How It Works and Why You Should Use It
Posted on
by
Kirk McElhearn

It’s getting increasingly risky to use online services. You store a lot of your personal data in the cloud, and your credit cards are linked to accounts on retail websites. Hackers would love to get at your data, to empty your bank account, or to access your email account, using it for spam and phishing. And if someone can pretend they are you — steal your identity — they can cause innumerable problems to you and your finances.
We also hear of an increasing number of data breaches, where major websites, stores, or services have entire databases of user names and passwords hacked. These databases are then traded on the hacker underground, allowing anyone willing to pay a few cents per name to access your accounts. And in some cases, they’re passed around for free.
More and more websites and services are using two-step verification or two-factor authentication (often abbreviated 2SV or 2FA, respectively) to provide an additional layer of security. This security technique verifies your identity when you log into a website by requiring you to both know something and have something in your possession. The thing you need to know is a user name and a password or a PIN; the thing you need to have is often a mobile phone, but it could also be a USB dongle or other device that can generate one-time codes.
RELATED: What is Multi-Factor (Two-Factor) Authentication?
Most of the services you use likely offer two-factor authentication. These include:
- Apple (iCloud and other services)
- Amazon (and Amazon-owned services)
- Google (Gmail and other services)
- Instagram and Threads
- Roku
- X (formerly known as Twitter)
- Dropbox
- Microsoft (Office 365 and other services)
- PayPal (but only in certain countries)
- Snapchat
- Tumblr
- Yahoo!
- Most major banks
- And many others…
In fact, the majority of big companies and new startups typically offer some form of 2FA these days.
How Two-Factor Authentication Works
When you activate two-factor authentication for a website or a service, you generally first have to provide your mobile phone number. You can also use a two-factor authentication app—which is actually more secure than receiving two-factor codes via SMS—but the phone remains the most common method of using two-factor authentication.
Related:
Two-factor authentication (2FA) apps for iOS: Which are the best?
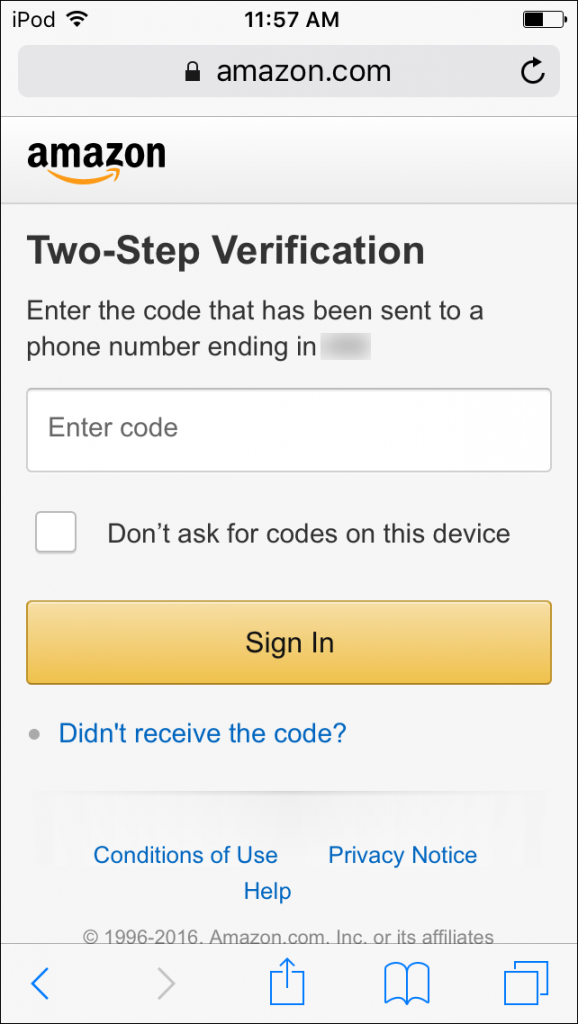
Most forms of two-factor authentication ask you to sign in with your user name and password, and then enter a code that is sent to you via SMS. This method not only proves that you know something (the user name and password), but also that you have something (the mobile phone), which you have “registered” as a device to receive these codes.
In most cases, once you’ve used two-factor authentication on a device, you won’t be asked to do so again on that device. Some services may only trust your device for 30 days or one year, and others may give you the option of trusting a device permanently. For example, if you have two-factor authentication active for Amazon, and want to buy something from Amazon on a friend’s iPad or a public computer, you’ll need to enter a code that Amazon sends to your mobile phone. But there’s a checkbox in the authorization dialog that lets you decide whether this device should be trusted in the future.
If it’s your computer or phone, you’ll likely want to trust it; but, if not, that device won’t be able to log into your account again without getting a new code.
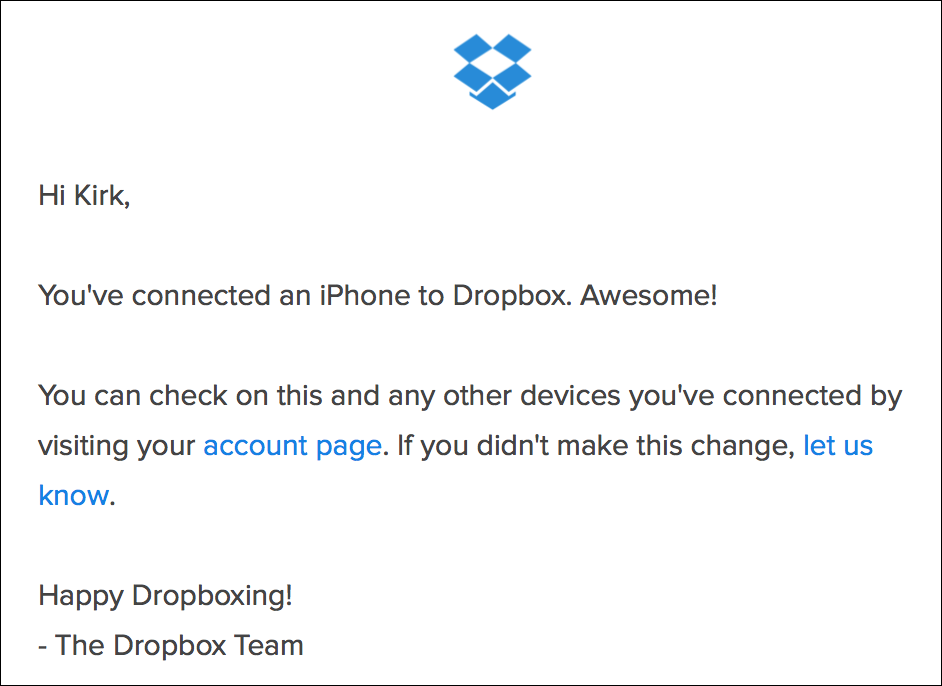
Some services don’t offer such an option, but will send you an email each time you connect a new device to their service. This is to ensure that you haven’t been hacked; that someone hasn’t gotten your user name, password, and your mobile phone. Here’s what Dropbox sends when you sign in for the first time on a device:
Apple sends you emails when a new device logs into your iCloud account, even if you don’t have two-factor authentication turned on.
Why You Should Use Two-Factor Authentication
As I explained at the beginning of this article, two-factor authentication helps protect your sensitive, personal data. Take Dropbox, Google, or iCloud, for example. On any of these services, you may store personal files and photos, and on iCloud or Google, you may sync your contacts, calendars, and email. Just think how much information a hacker would have about you if they were able to access your account. (Remember when Jennifer Lawrence’s nude photos leaked?)
Sure, two-factor authentication is a bit of an annoyance, at least the first time you log in on a device. Set up a new iPhone, for example, and it’ll take you a while to get all your accounts up and running. (You have to do this for each new device, since each device sends its unique identifier to a login server, and authentication is required when you log in on a new device.)
Your mobile phone is generally secure, especially if you use an iPhone with Touch ID. If you do, think about setting a long passcode (i.e., six characters, instead of just four), to ensure that, if your phone is lost or stolen, thieves cannot get access to your device. If they do, they can potentially access all your accounts, because they can receive the codes sent for two-factor authentication (this assumes that you have stored passwords and set your web browser to auto-fill them).
One problem occurs if you lose your mobile phone; you can be locked out of certain accounts for a while. Some services let you set a backup phone number, which could be a friend’s or spouse’s phone, or even a landline, if you can receive text-to-speech SMSs. If you can’t do this, buy a cheap phone, and get a pay-as-you-go SIM, so you can receive SMSs when you need them. Naturally, your carrier will be able to port your phone number to a new SIM card, when you replace your lost phone, but this may take several days.
The inconvenience of this is far outweighed by the added security you get when using two-factor authentication.
Setting Up Two-Factor Authentication
For more detailed information about certain services, see these articles that we’ve published on The Mac Security Blog:
- How to Activate Apple’s Two-Step Verification for iCloud
- Protect Your Amazon Account with Two-Step Verification
- How to Manage Gmail and Google Security and Privacy Settings
For other services, check your account settings, and look for a section related to account passwords and security.
It may take some time to go through every one of the services you use to activate two-factor authentication, but you’ll be much better protected if you do. You may prevent some of your accounts from getting hijacked in the future.
How can I learn more?
 Each week on the Intego Mac Podcast, Intego’s Mac security experts discuss the latest Apple news, including security and privacy stories, and offer practical advice on getting the most out of your Apple devices. Be sure to follow the podcast to make sure you don’t miss any episodes.
Each week on the Intego Mac Podcast, Intego’s Mac security experts discuss the latest Apple news, including security and privacy stories, and offer practical advice on getting the most out of your Apple devices. Be sure to follow the podcast to make sure you don’t miss any episodes.
You can also subscribe to our e-mail newsletter and keep an eye here on The Mac Security Blog for the latest Apple security and privacy news. And don’t forget to follow Intego on your favorite social media channels: ![]()
![]()
![]()
![]()
![]()
![]()
![]()