How to set up Two-Factor Authentication on Twitter
Posted on
by
Kirk McElhearn

Twitter recently announced that they will stop allowing the use of SMS-based two-factor authentication for their service, except for Twitter Blue subscribers. This $8 a month service offers a blue checkmark (though not actual verification), the ability to edit tweets, and more. This change will take place on March 20, 2023, and, if you are using SMS-based two-factor authentication (2FA) at that time, Twitter will turn it off, rendering your account less secure.
SMS-based 2FA is not very secure – SMSes can be intercepted, and SIM cloning can allow people to pretend they have your phone – and the other methods available are much more robust. But Twitter’s decision to turn off SMS-based 2FA is dangerous, and their choice to allow it to be used for a price is misguided.
If you have SMS-based 2FA on Twitter, you should change this to use an authenticator app, and there’s one built into macOS, iOS, and iPadOS. Here’s how to do this on Mac, iPhone, or iPad.
About Twitter’s 2FA
Two-factor authentication, or 2FA, protects your account by requiring that, to log into a website or service, you must enter something you know, your user name and password, and something you have, such as a one-time code. These codes can can be sent by email or SMS, or can be generated by authenticator apps. It’s also possible to use a security key, a sort of dongle that works as a physical key generator.
The uptake of two-factor authentication on Twitter is quite low; as of December 2021, only 2.6% of active accounts used 2FA, and, of these, 74.4% used SMS-based 2FA, 28.9% used an authenticator app, and, only 0.5% used a security key. (Twitter notes that accounts can have multiple 2FA methods set up.) Twitter has offered these three methods of 2FA for many years, and most people choose SMS because it is simpler and does’t require additional software.
If you don’t currently use 2FA on Twitter, you should. If the password you use for Twitter is weak, or if you reuse a password that may have shown up in a data breach, 2FA prevents hackers from taking control of your account. For many people, this includes not just tweets but also direct messages, which may contain personal information.
In addition, 2FA can help protect you from phishing. If you do get tricked into entering your user name and password on a phishing site, hackers won’t be able to get into your account without the code that you generate.
While SMS is insecure, Ricky Mondello, a software engineer at Apple who works on security and passwords, points out that “SMS 2FA provides value, despite its flaws.” They explain that not everyone is targeted by hackers, and that weak passwords can be protected by any form of 2FA, even SMS. And they point out that SMS-based two-factor authentication is “relatively usable and accessible: lots of people understand what it means to give a service like Twitter their phone number and can figure out how to enter a code that’s texted to them.”
Why Twitter is making this change to two-factor authentication
Since Elon Musk bought Twitter for the inflated price of $44 billion, he has attempted to cut costs as much as possible. He recently said on Twitter that “Twitter is getting scammed by phone companies for $60M/year of fake 2FA SMS messages.”
SMS messages are not free, and it’s not clear whether Twitter is really “getting scammed,” but deciding to throw away security in this way seems shortsighted. While only a small percentage of Twitter users have 2FA turned on, and getting people to use an authenticator app instead of SMS is a good thing, the fact that Twitter is leaving SMS authentication available for a fee makes little sense. Essentially, paying users get lower security, if they wish, while users who don’t pay and want to use 2FA will be more secure.
Twitter could have switched their SMS two-factor authentication to email-based codes, which they use when they verify email addresses. This would be more or less free – there’s only minimal bandwidth costs for email, whereas there are carrier costs for SMS – and this is more secure than SMS.
In addition, Twitter users may go for months, or even years without needing to enter a new code. You only need to enter a code when logging in on a new device or a new browser. I can’t remember the last time I had to enter a 2FA code for my Twitter account.
It is possible that these “fake 2FA SMS messages” are sent when scammers try to log into accounts that are protected with 2FA. Perhaps a hacker has a username and password, and attempts to access an account, or tries to reset a password; at that point, an SMS is sent to the user.
How to set up Twitter’s two-factor authentication with an authenticator app
Setting up 2FA on Twitter is simple. On the Twitter website, tap or click the … icon, choose Settings and Support, then Settings and Privacy. Tap or click Security and Account Access, then Security.
In the Twitter app, tap or click your avatar, then Settings and Support, then Settings and Privacy.
The Two-Factor Authentication section allows you to manage this feature.
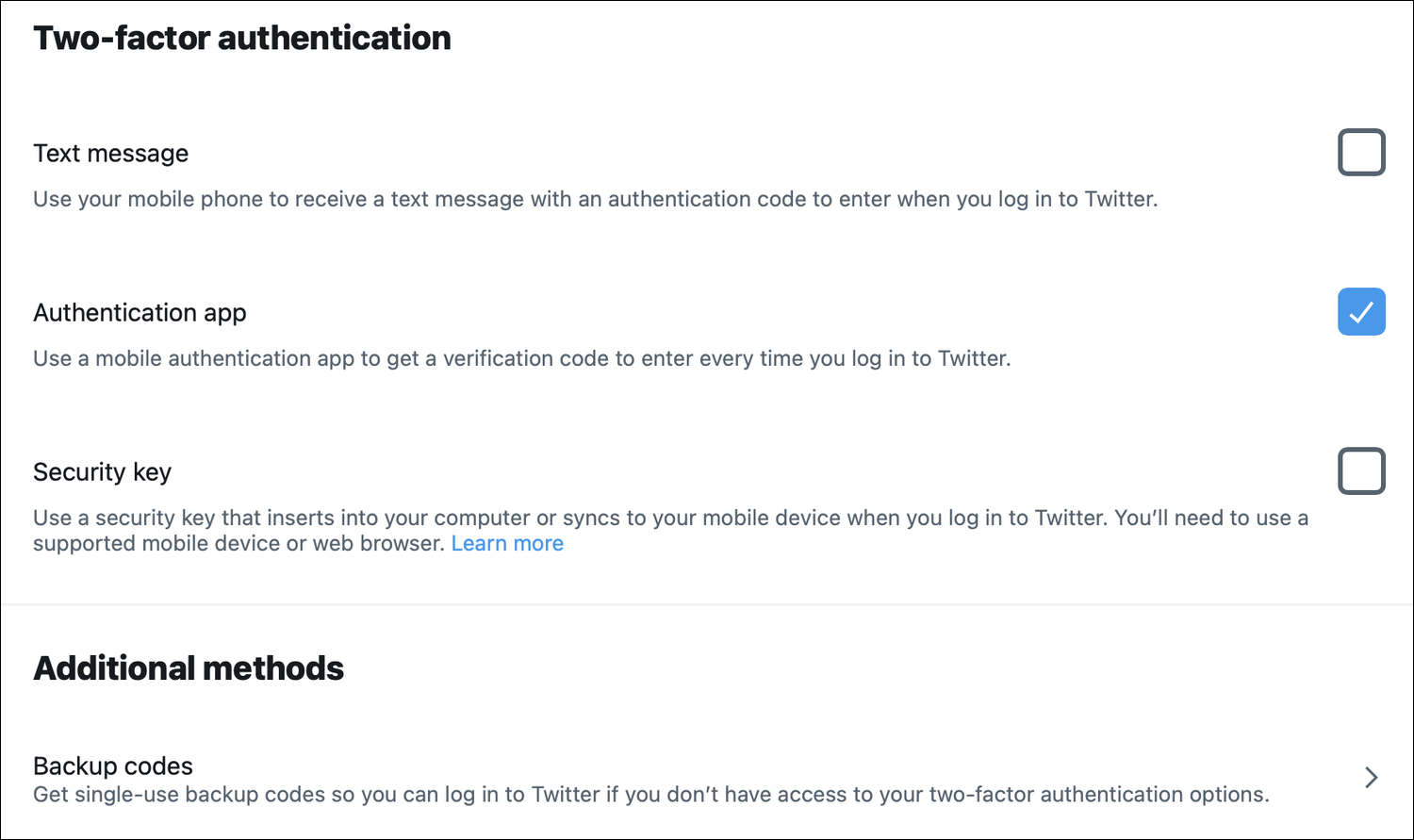
You can see the three options currently available: Text message, Authentication app, and Security key. You can also see, under Additional methods, a Backup codes section, which I discuss at the end of this article.
Tap or click the Authentication app checkbox. Follow the instructions, and, if you haven’t already confirmed your email address, Twitter will send you a confirmation email. Enter the code in this email. Twitter explains the steps for setting up two-factor authentication.
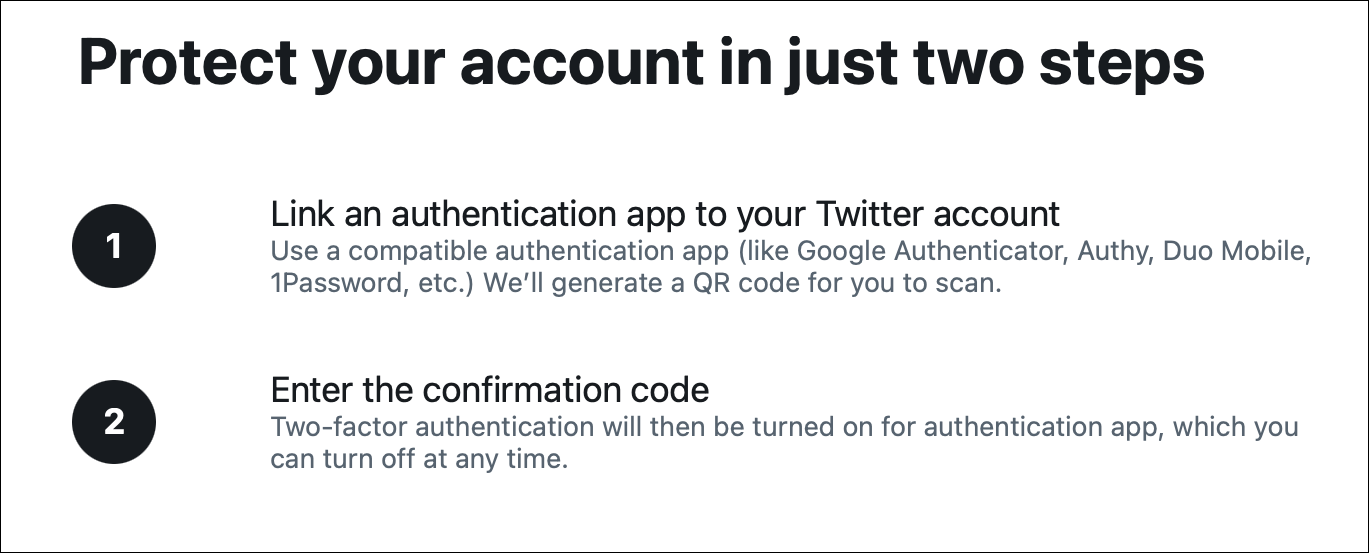
Twitter then displays a QR code; use the authenticator app on your phone to scan this code, then generate a code and enter it on the Twitter website. (I discuss authenticator apps below.)
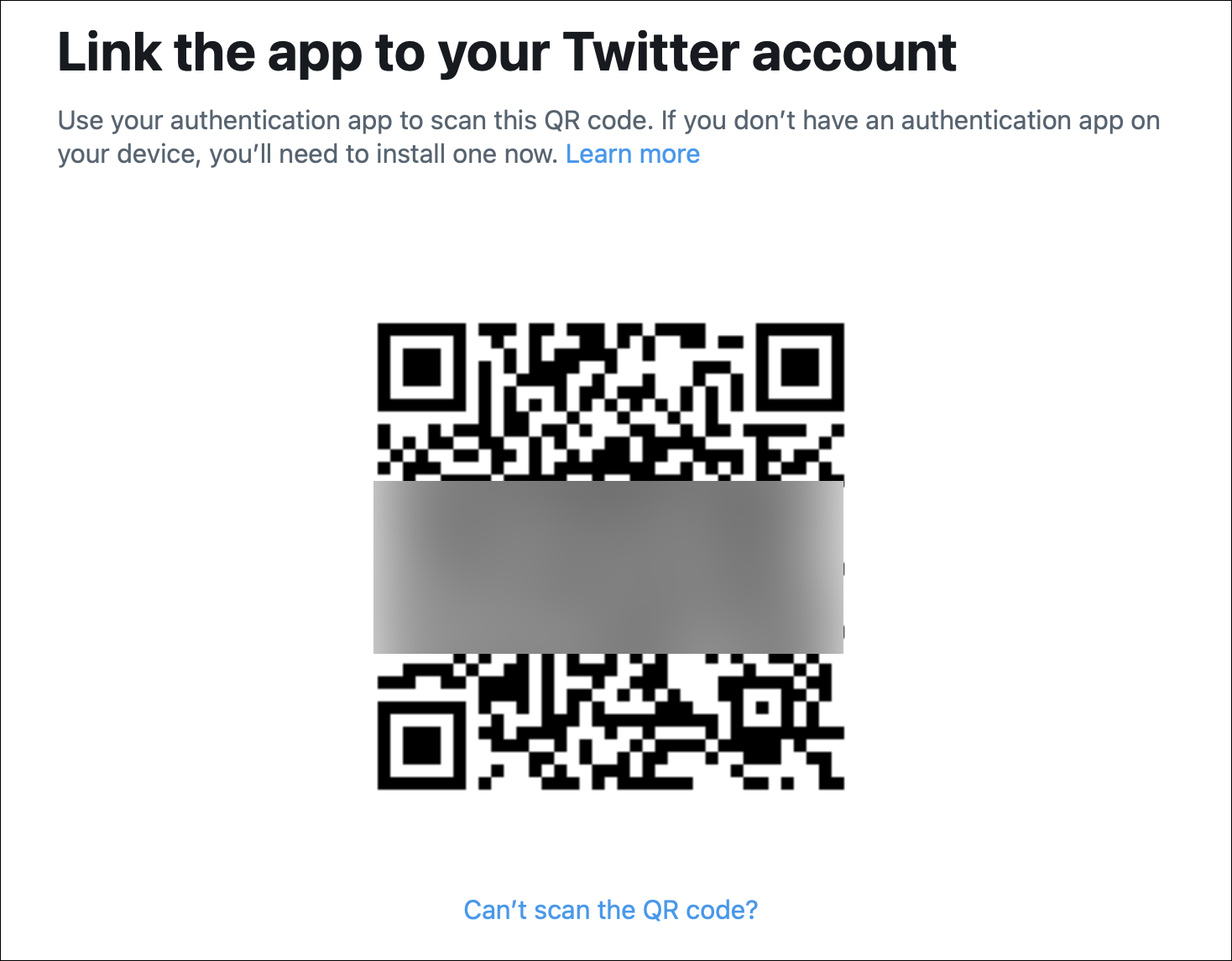
If you can’t scan the QR code, click the link below it to get a long alphanumeric code that you enter in your authenticator app.
Each time you log into Twitter on a new device or in a new browser, you’ll need to enter your user name, password, and a unique code that you generate.
Using the Apple Keychain as an authenticator app
To perform the above, you need an authenticator app, but you can also use the Keychain, which is built in to macOS, iOS, and iPadOS. Since macOS Monterey and iOS 15, the Keychain has supported two-factor authentication codes, and the information syncs across your devices via iCloud. As long as you don’t need to log in on an Android or Windows device without having an Apple device handy, you will never need anything else.
To do this on a Mac, go to Safari > Settings, click Passwords, enter your Mac’s password or use Touch ID, then find the Twitter account in the passwords list. Click Edit, then click Enter Setup Key:
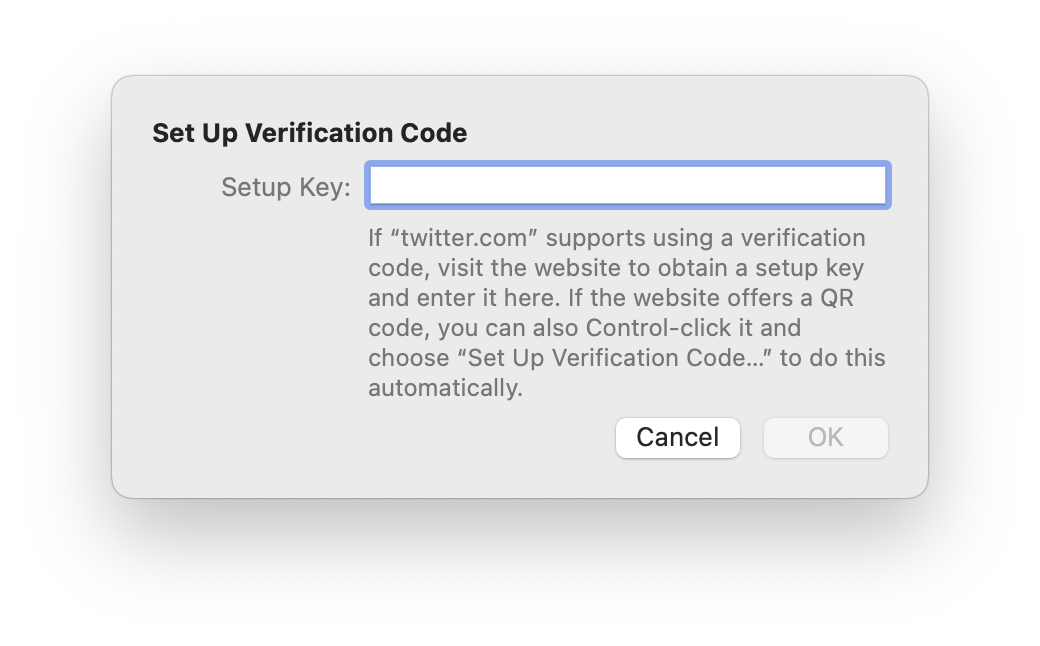
On an iPhone or iPad, go to Settings, scroll down a bit and tap Passwords, then search for the Twitter account you want to protect. Tap that entry, then, under Account Options, tap Set Up Verification Code. You have two options:
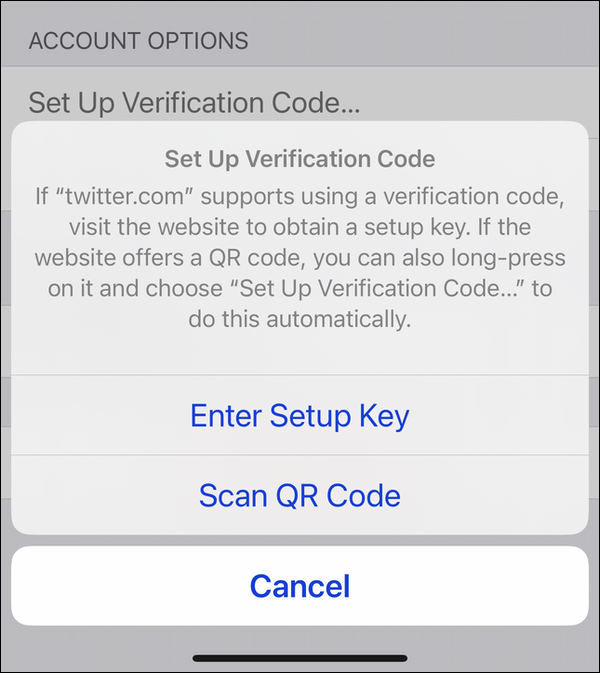
Choose Enter Setup Key, and enter the alphanumeric key that Twitter provides.
Whether you’ve done this on a Mac, iPhone, or iPad, you’ll now be prompted by Twitter to generate a code, to confirm that the process has worked. Enter that code to confirm, then click Verify.
Using other authenticator apps
You can use third-part authenticator apps, which we discuss in this article, such as Google Authenticator, Microsoft Authenticator, or Authy, and others. These apps all do nothing other than generate codes; they don’t store your passwords. You set up all your accounts that use 2FA in one of these apps, and, when you need a code, you generate it, then enter it on the website.
You can also use password managers, such as 1Password, Dashlane, or BitWarden to generate 2FA codes. With these apps, you can have your passwords and your two-factor code generators together.
Some authenticator apps and password managers have companion Apple Watch apps which allow you to generate codes on your wrist; this can be useful for sites where you need 2FA codes each time you log in. This isn’t the case with Twitter; you only need to enter a code the first time you log in with a new device or browser.
Creating backup codes
After you’ve set up 2FA, you should go back to the main Two-factor authentication page. Under Additional methods, you’ll find a link to backup codes. Click this, and Twitter generates a code made up of 12 alphanumeric characters. Copy this code and store it in a safe place, such as a password manager or secure notes app. You can generate multiple codes by clicking Generate a new code several times; it’s a good idea to save several of these, in case you have problems generating one-time codes. You can only use each of these codes once.
Bottom line
While Twitter’s sudden decision risks making many user accounts less secure, the publicity around this change could prompt more users to adopt 2FA on Twitter; the low percentage of accounts protected this way shows how weak the service’s security is. You should protect all accounts that offer this feature with two-factor authentication, and there are tools built into Apple’s operating systems that make this simple.
How can I learn more?
 Each week on the Intego Mac Podcast, Intego’s Mac security experts discuss the latest Apple news, including security and privacy stories, and offer practical advice on getting the most out of your Apple devices. Be sure to follow the podcast to make sure you don’t miss any episodes.
Each week on the Intego Mac Podcast, Intego’s Mac security experts discuss the latest Apple news, including security and privacy stories, and offer practical advice on getting the most out of your Apple devices. Be sure to follow the podcast to make sure you don’t miss any episodes.
You can also subscribe to our e-mail newsletter and keep an eye here on The Mac Security Blog for the latest Apple security and privacy news. And don’t forget to follow Intego on your favorite social media channels: ![]()
![]()
![]()
![]()
![]()
![]()
![]()