Recommended + Security & Privacy
Did Jennifer Lawrence’s Naked Photos Leak Out Because She Told the Truth? Lying Can Protect your iCloud Account
Posted on
by
Graham Cluley

The private nude photos of 100 female celebrities, including Oscar-winning actress Jennifer Lawrence, have been distributed across the Internet – and now we’re beginning to find out more about how it might have happened.
Apple has issued a statement to the press, confirming it has “discovered that certain celebrity accounts were compromised by a very targeted attack on user names, passwords and security questions.”
The attacks were against the celebrities’ iCloud accounts, but Apple has denied that the criminal hackers were able to gain access to private photographs and movies (many of which exhibited full frontal nudity) because of a security hole in its iCloud or Find my iPhone systems.
As we described earlier today, there had been growing suspicion that the hackers could have exploited a security hole in the Find My iPhone API to access iCloud accounts.
Security researchers Andrey Belenko and Alexey Troshichev created a tool called iBrute, which made it child’s play to bombard any iCloud account with hundreds (or potentially many thousands) of the most commonly-used passwords, in order to break in.
Shockingly, Apple’s systems seemed to have no “rate-limiting” in place (the flaw is now said to have been fixed), which could have detected the suspicious behaviour and stopped it dead in its tracks.
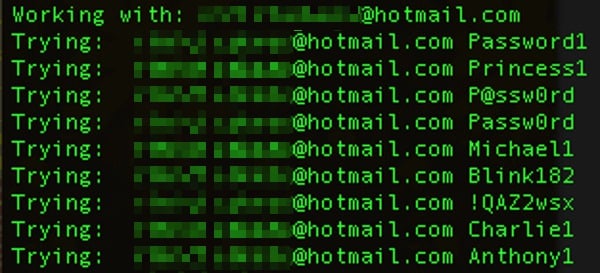
In Apple’s statement however, the company appears to be denying that this method was used by the celebrity hackers:
“We wanted to provide an update to our investigation into the theft of photos of certain celebrities. When we learned of the theft, we were outraged and immediately mobilized Apple’s engineers to discover the source. Our customers’ privacy and security are of utmost importance to us. After more than 40 hours of investigation, we have discovered that certain celebrity accounts were compromised by a very targeted attack on user names, passwords and security questions, a practice that has become all too common on the Internet. None of the cases we have investigated has resulted from any breach in any of Apple’s systems including iCloud® or Find my iPhone. We are continuing to work with law enforcement to help identify the criminals involved.”
Instead, Apple appears to believe that this was a more old school hack, where hackers were able to guess so-called “security questions” that users must answer if they want to reset their password.
In a nutshell, if you forget your iCloud password you can ask Apple’s permission to reset it. However, Apple will only allow you to reset the password if you jump through enough hoops to confirm you are who you say you are.
The way in which Apple does that is through asking you for your date of birth and for “security questions” that, in theory, only you should know. The idea is that you may not remember your password, but you’re unlikely to have forgotten the model of your first car, or the first name of your best friend at high school.
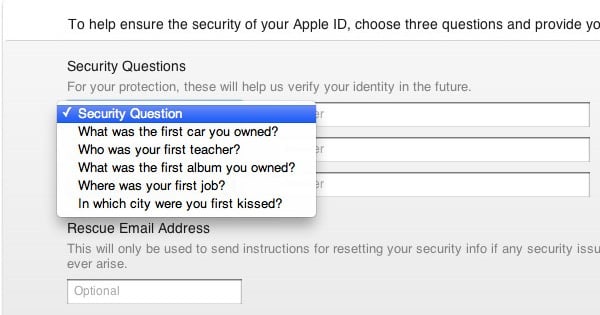
If you answer the questions correctly, then Apple will allow you to reset your iCloud password, sending a confirmation email to your account.
Can you see the problem?
The victims are celebrities, the minutiae of whose lives are pored over by gossip magazines, feverish fans and Wikipedia entries. Chances are that a quick Google search might reveal the answers to the “secret” security questions, and allow a hacker to gain access.
The problem is that people – yes, even celebrities are people – feel compelled to answer questions honestly.
 It’s not as if Apple employees are going to check what your first car was, so why not answer Golden Wombat? They have no way of telling if your best friend at school was Boutros Boutros-Ghali, the sixth Secretary-General of the United Nations, so why not tell Apple that it was?
It’s not as if Apple employees are going to check what your first car was, so why not answer Golden Wombat? They have no way of telling if your best friend at school was Boutros Boutros-Ghali, the sixth Secretary-General of the United Nations, so why not tell Apple that it was?
So long as you REMEMBER the secret security answers (or get a password vault to remember them for you) then there’s no harm in having some fun and giving an answer that no-one else on the internet will be able to guess.
Because remember, it’s not just celebrity hackers who might find it all too easy to guess your secret answers. It could be your colleagues at work, or your rival in the cheerleading team, or your ex-boyfriend who left you on bad terms.
It’s unknown, so far, precisely how the hackers were able to determine the celebrities’ email addresses, but there has to be a suspicion that address books were hacked and that some individuals might have been phished or infected with malware to speed the process along.
It is also worth pointing out that it seems unlikely that this story is over. The scale of the hack, the humiliating nature of some of the images that have been stolen and distributed on the internet, and the high profile of those concerned, will mean that this issue will capture the media’s attention for a while now.
And no doubt, we may find more about who was responsible for the hack – and more details of how they perpetrated it.
For one thing, it’s clear that some of the images contained in the celebrity photo stash date back some years, whereas others are just a couple of weeks old. Whoever has been collecting nude pictures of celebrities like Jennifer Lawrence and Kate Upton has been pursuing their hobby for quite some time.
Top tips for securing your iCloud account

Use a strong, hard-to-crack, impossible to guess password.
And make sure it’s unique. That means not using the same password anywhere else on the Internet. If you don’t think you’ll be able to remember it, use a password management program to do the hard work for you.
Your data is too valuable to end up in the hands of hackers just because you chose a password like “Twinkletoes” or “Password1.”
Enable two-factor authentication wherever possible.
Many online accounts today provide you with 2FA (also known sometimes as two-step verification). This can mean that you are sent an SMS message with a one-time password to enter alongside your regular passwords, or that you check an app on your smartphone to generate a one-time password when you need it.
The beauty of this approach is that the hackers don’t just need your regular username and password, they also need to have access to your smartphone. That makes things much harder for them.
Although Apple may be claiming that the celebrity hack was not their fault, I do think they could do more to encourage users to enable two-factor authentication.
Have a complex iCloud security code.
By default, Apple encourages users to have a four digit security code to protect their iCloud accounts. However, that means there are only 10,000 options – something that a brute force attack could potentially break in no time at all.
Instead, make sure that you have chosen the option for a complex security code instead.
Start lying.
Stop feeling compelled to tell the truth. Ask yourself, does this website *really* need to know my real date of birth or can I give it a fake one? (Don’t lie about being an adult if you’re not, or vice versa by the way. That’s a whole different bag of snakes).
But next time a site asks you to tell it a piece of personal information as a security test, dream up something that no-one else will be able to find out about you, but which you’ll remember.
That’s why my mum Xena Warrior Princess called her pet dog “RHFu8tb2,” and why you (and Jennifer Lawrence) should consider doing something similar.