Apple + Recommended + Security & Privacy
The Evolution of iOS Security and Privacy Features
Posted on
by
Joshua Long

We recently published a story covering the evolution of macOS security and privacy features, where we discussed the major security improvements over the past decade in OS X, Apple’s operating system for Mac desktops and laptops.
As with desktop operating systems, the ever-changing threat landscape has also necessitated the evolution of mobile operating systems, including iOS.
 Google’s Android isn’t the only mobile platform with security problems. In spite of the iPhone, iPad, and iPod touch being known for their locked-down nature and “walled garden” app ecosystem, iOS devices are not as perfectly safe as we might like to believe. Exploits that can take advantage of iOS are out there in the wild, and even Apple’s ostensibly “safe” App Store has been penetrated with questionable and malicious software on several occasions (the XcodeGhost debacle is just one example).
Google’s Android isn’t the only mobile platform with security problems. In spite of the iPhone, iPad, and iPod touch being known for their locked-down nature and “walled garden” app ecosystem, iOS devices are not as perfectly safe as we might like to believe. Exploits that can take advantage of iOS are out there in the wild, and even Apple’s ostensibly “safe” App Store has been penetrated with questionable and malicious software on several occasions (the XcodeGhost debacle is just one example).
Users of Apple’s smartphone and tablet have also been targets of fraud, identity theft, and espionage campaigns — just like users of desktops and laptops.
To help protect its customers and combat some of these threats, Apple has added many security and privacy-enhancing features to iOS since its initial release nearly nine years ago. With each major revision, along with incremental security updates, Apple has continued to improve the baseline security of its mobile operating system.
Following is a timeline of some notable security improvements that Apple has made in every version of iOS to date.
June 2007: iPhone OS 1

The iPhone was the first of what we now know as “iOS devices.” However, when the iPhone was announced, Apple had yet to come up with a name for its new mobile operating system; in fact, you might be surprised to learn that Apple actually called iOS “OS X” at first.
Apple had little to say about the security of the first iPhone. For its time, the original iPhone was far more advanced than any other smartphone on the market, so few people bothered worrying about things like security. After all, it was amazing and revolutionary, so what else really mattered?
Little did anyone know then what security challenges lay in store for mobile operating systems.
Although there was no App Store yet, and thus there were no officially sanctioned third-party applications, the original iPhone included “a rich HTML email client and Safari — the most advanced web browser ever on a portable device,” which unbeknownst to most users made the phone vulnerable to a variety of potential attacks.
By the time the iPhone was just months old and the iPod touch had just been released, there was already a small community of hackers and tinkerers making and distributing unauthorized third-party apps.
Apple’s first attempt at squashing this phenomenon arrived in the form of the iPhone 1.1.1 Update, about which one developer noted, “It looks like Apple is locking down the iPhone with encryption and signing, the same way they locked down the iPod Touch.”
Prior to the iPhone 2.0 software release, there were a total of four security updates for the original iPhone OS, fixing a combined total of 22 security vulnerabilities (note: vulnerability counts in this article are based on CVE IDs).
July 2008: iPhone OS 2

Macworld reported that the iPhone 2.0 software (later renamed “iPhone OS” for its 2.2 release) included a single new built-in app: the App Store. For some, this lessened the desire to hack one’s own iPhone to install unapproved third-party software; nevertheless, the jailbreaking community continues to have its devotees even today.
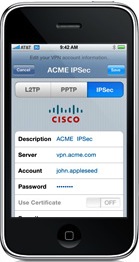 Apple added a number of security improvements to the iPhone 2.0 software, with a primary focus on making the iPhone a more viable option for enterprise businesses. Among the new features were support for Cisco IPSec VPNs, Wi-Fi support for WPA2 Enterprise and 802.1x authentication, configuration profiles for enforcing security policies, and the ability for a company to remotely wipe (erase) an employee’s lost or stolen iPhone. It was also possible to add multiple VPN configurations, and Apple added a “VPN” icon to the top of the screen to make it more obvious to the user when they were connected.
Apple added a number of security improvements to the iPhone 2.0 software, with a primary focus on making the iPhone a more viable option for enterprise businesses. Among the new features were support for Cisco IPSec VPNs, Wi-Fi support for WPA2 Enterprise and 802.1x authentication, configuration profiles for enforcing security policies, and the ability for a company to remotely wipe (erase) an employee’s lost or stolen iPhone. It was also possible to add multiple VPN configurations, and Apple added a “VPN” icon to the top of the screen to make it more obvious to the user when they were connected.
The VPN indicator icon (a newer iOS version is pictured). Image credit: Apple
Apple also opened up Location Services to third-party applications, which would prompt the user for permission first.
The iPhone 2.0 software itself fixed a total of 13 security vulnerabilities. It was followed by a total of two security updates (prior to the iPhone OS 3.0 Software Update) fixing a combined total of 20 vulnerabilities.
June 2009: iPhone OS 3

One of the biggest security improvements in iPhone OS 3 was that users who paid $100 per year for MobileMe (the predecessor of iCloud) could enable Find My iPhone. This feature provided the ability to locate a lost or stolen iPhone, with options to subsequently send the device an alert sound or an “Important Message” dialog box, or even remotely deactivate or wipe the phone similar to the corporate remote-wipe feature added in the iPhone 2.0 software.
 However, the iPhone OS 3.0 implementation of Find My iPhone could be fairly easy for a thief to bypass, given the right circumstances. If an iPhone owner had turned off Location Services, then the Find My iPhone feature would not work in the first place. If an iPhone owner had left Location Services on but neglected to enable a passcode to lock their phone, then a thief could simply swipe to unlock the phone and disable either the Find My iPhone feature or Location Services immediately after stealing it. MobileMe-subscribing iPhone owners who did not have a passcode on their phone, and then lost their phone, could remotely assign a passcode to prevent whoever found the phone from unlocking it (this feature was introduced in iPhone OS 3.1).
However, the iPhone OS 3.0 implementation of Find My iPhone could be fairly easy for a thief to bypass, given the right circumstances. If an iPhone owner had turned off Location Services, then the Find My iPhone feature would not work in the first place. If an iPhone owner had left Location Services on but neglected to enable a passcode to lock their phone, then a thief could simply swipe to unlock the phone and disable either the Find My iPhone feature or Location Services immediately after stealing it. MobileMe-subscribing iPhone owners who did not have a passcode on their phone, and then lost their phone, could remotely assign a passcode to prevent whoever found the phone from unlocking it (this feature was introduced in iPhone OS 3.1).
Apple added an AutoFill feature to Safari in iPhone OS 3. The feature only automatically filled in contact information from the user’s Address Book; Apple opted to not AutoFill credit card information at that time (although the feature was added several years later in iOS 7).
The iPhone OS 3.0 software itself fixed a total of 46 security vulnerabilities. It was followed by a total of three security updates (prior to the release of iOS 4) fixing a combined total of 16 vulnerabilities.
June 2010: iOS 4

In iOS 4, Apple introduced the option to use a long password rather than a four-digit PIN to log into an iOS device. Now instead of a limit of 10,000 possible passwords (which made it possible to guess the correct password within hours if trying every combination one at a time), the password options could now be virtually limitless, which could dramatically increase the security of unlocking an iOS device.
Apple added functionality to encrypt e-mail attachments when the device was locked with a passcode (for supported iOS devices). This encryption was extended to third-party applications, which could also now encrypt their data using the same technology.
Apple also improved privacy in iOS 4 by giving users per-app control over Location Services. Now it was possible to, for example, allow Maps access to your location while preventing your Twitter app from being able to identify where you were while composing a tweet. Whenever an app was currently tracking your location, an indicator icon would appear in the bar across the top of the screen to indicate this; a user could then find out which app was currently using their location by opening the Settings app and looking under Location Services.
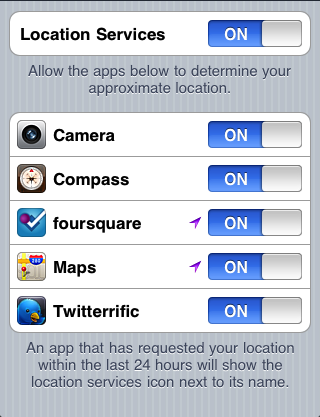
Image credit: Apple
The iOS 4.0 release itself fixed a total of 65 security vulnerabilities. It was followed by a total of seven main security updates (prior to the release of iOS 5) that fixed 179 vulnerabilities. (Now Apple was really getting into the security-patching groove.)
October 2011: iOS 5

Apple added an “Unsecured Call” warning dialog box to iOS 5, mysteriously without providing any documentation to explain this feature (a Google search of Apple’s site only reveals one discussion topic from a single concerned user, and searching Apple’s site via their own search bar produces no search results). The warning dialog box, titled “Unsecured Call,” states, “The cellular network you are using is not encrypted. This call can be intercepted by unauthorized listeners,” with buttons to either Ignore or End Call. A 9to5Mac article points to speculation that Apple’s warning could be notifying the user of active attacks of the sort shown in a DEF CON 18 talk given in 2010, in which a researcher demonstrated how GSM networks (like AT&T and T-Mobile) could easily have their calls intercepted and recorded; see the DEF CON talk description and YouTube video.
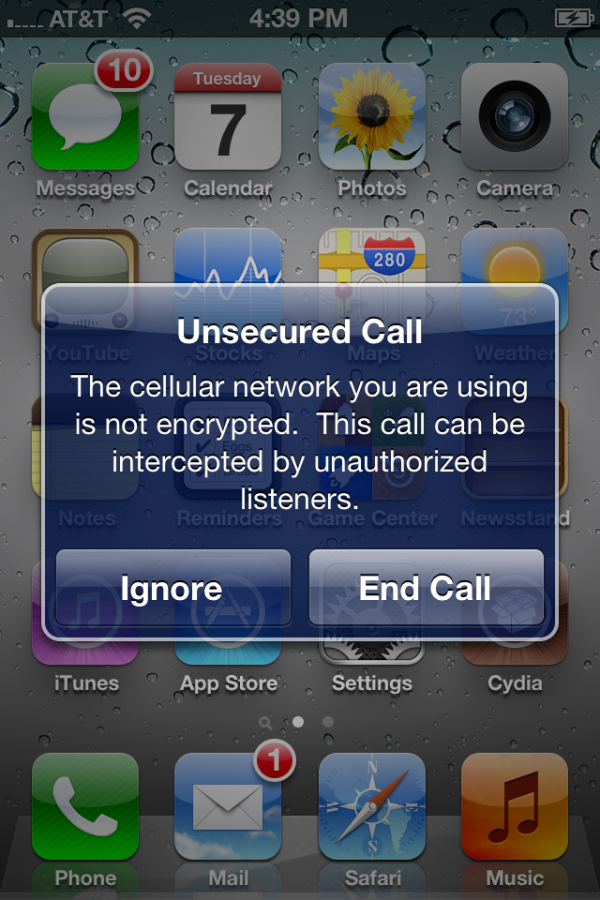
Image credit: @MuscleNerd
![]() Apple also designed a new app called Find My Friends that gave the option of sharing one’s location with other iOS users. Apple put a lot of thought into privacy when developing this app, and made it clear what data would be shared with whom. Ars Technica has a detailed rundown of how Find My Friends worked.
Apple also designed a new app called Find My Friends that gave the option of sharing one’s location with other iOS users. Apple put a lot of thought into privacy when developing this app, and made it clear what data would be shared with whom. Ars Technica has a detailed rundown of how Find My Friends worked.
The iOS 5.0 release itself fixed a total of 96 security vulnerabilities. It was followed by a total of three security updates (prior to the release of iOS 6) that fixed 90 vulnerabilities.
September 2012: iOS 6

Apple included some new privacy features in iOS 6. In the Settings app there was a Privacy section that now included the Location Services functionality mentioned above, and also included toggle switches to enable or disable apps’ access to your contacts, calendars, reminders, photos, and your Twitter and Facebook accounts. This section also included a Bluetooth Sharing screen that showed decides that had requested to share data via Bluetooth.
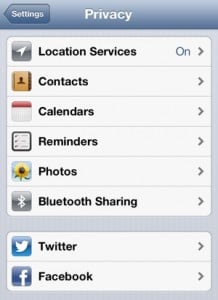 Also in the Settings app, but found under General > About > Advertising > Limit Ad Tracking, was a toggle switch allowing users to turn “Limit Ad Tracking” to ON (later, in iOS 7, this setting was moved to the Privacy section with the other features noted above). The Limit Ad Tracking feature was designed to prevent apps from displaying ads targeted toward a user’s interests.
Also in the Settings app, but found under General > About > Advertising > Limit Ad Tracking, was a toggle switch allowing users to turn “Limit Ad Tracking” to ON (later, in iOS 7, this setting was moved to the Privacy section with the other features noted above). The Limit Ad Tracking feature was designed to prevent apps from displaying ads targeted toward a user’s interests.
A guide to these privacy options with additional screenshots can be found at iPhoneHacks.
The iOS 6.0 release itself fixed a total of 197 security vulnerabilities. It was followed by a total of three security updates (prior to the release of iOS 7) that fixed 37 vulnerabilities.
September 2013: iOS 7

Apple did much to improve security in iOS 7, but this major iOS release was not without controversy.
Let’s get the most controversial items out of the way first.
The infamous “goto fail” SSL bug that came to light in February 2014 rattled the security community, prompting wild speculation that Apple may have intentionally bypassed the SSL digital signature check to give the U.S. government a backdoor. The bug had been present in all iOS 7 versions prior to 7.0.6, some versions of iOS 6 prior to 6.1.6, and versions of OS X Mavericks prior to 10.9.2. Part of the public outcry over the “goto fail” bug was due to OS X not being patched in tandem with iOS; users had to wait a while until Mavericks version 10.9.2 was released to fix the problem on the Mac side.
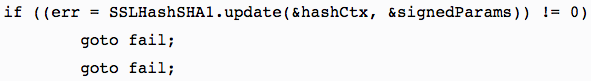
The second “goto fail;” in this code caused a major security weakness in Apple’s operating systems.
Just a couple months later, there was further controversy when a researcher discovered that e-mail attachments were not actually being encrypted when a passcode was enabled, in spite of Apple’s claims to the contrary. Apple acknowledged the bug and subsequently fixed it in iOS 7.1.2 — which was released in June 2014, nine months after the initial release of iOS 7.
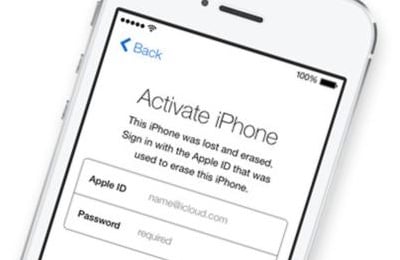 A new feature called Activation Lock, which is on by default when Find My iPhone is enabled in iOS 7, was designed to deter would-be thieves from stealing iPhones. With the feature enabled, the owner’s Apple ID and password must be entered before anyone can disable Find My iPhone, erase the device, or reactivate and use the device — effectively turning stolen iOS devices into shiny doorstops. Naturally the idea that one’s device could be “bricked” by forgetting one’s password (or that a user could lock a company-owned device with their personal Apple ID) prompted some concern, but overall the feature was a step in the right direction for mobile device security. Intego has previously published several articles about Activation Lock.
A new feature called Activation Lock, which is on by default when Find My iPhone is enabled in iOS 7, was designed to deter would-be thieves from stealing iPhones. With the feature enabled, the owner’s Apple ID and password must be entered before anyone can disable Find My iPhone, erase the device, or reactivate and use the device — effectively turning stolen iOS devices into shiny doorstops. Naturally the idea that one’s device could be “bricked” by forgetting one’s password (or that a user could lock a company-owned device with their personal Apple ID) prompted some concern, but overall the feature was a step in the right direction for mobile device security. Intego has previously published several articles about Activation Lock.
Touch ID was a new feature introduced in iOS 7 to complement the new Home button fingerprint sensor on the iPhone 5s (and later iPad and iPhone models). The Chaos Computer Club successfully fooled Touch ID with a fake fingerprint just one day after the iPhone 5s was released. The feature also prompted concerns about whether one can “take the fifth,” or in other words refuse to unlock a device when compelled to do so by law enforcement, when the unlocking method is “something you are” as opposed to “something you know.”
Heck, someone with a simple wrench could just knock you out and use your finger to unlock your iPhone before stealing it or rummaging through its contents. Touch ID certainly had its positive and negative points. To date, Apple still has not given users the option to require both unlocking methods, a fingerprint and a password, which would provide effective two-factor authentication.

Let’s just say that Touch ID has some drawbacks. Image credit: Imgur.
Apple’s default Personal Hotspot passwords from previous versions of iOS could easily be brute-forced in “less than 50 seconds” according to research published in June 2013, making it relatively easy to hijack someone else’s cellular data connection. Apple mitigated this flaw by improving the Personal Hotspot password generator in iOS 7.
Many mobile devices had been vulnerable to an attack known as “juicejacking,” where an untrusted public charging station could potentially steal data or inject malware into your device — without any interaction on the user’s part other than simply plugging in the charging cable. In a Black Hat conference talk in 2013, researchers demonstrated that they could infect an iOS device within one minute after it was plugged in. In iOS 7, Apple mitigated such attacks by prompting users to decide whether to “trust this computer” when connecting an iOS device to anything that’s capable of more than just charging.
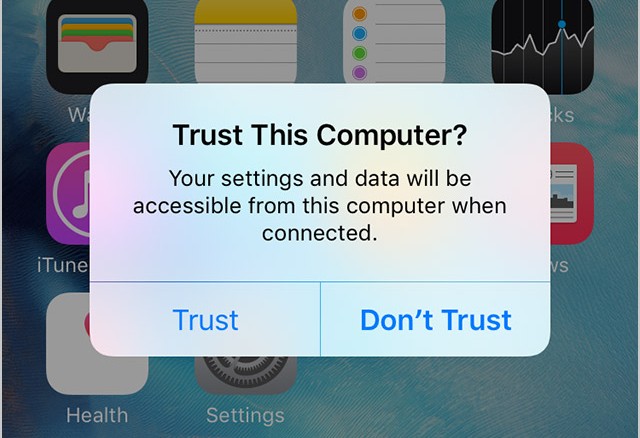
The “Trust This Computer?” prompt (iOS 9 pictured). Image credit: Apple
Several other iOS 7 security features and concerns are detailed in this iMore article.
Apple released a white paper (PDF) in February 2014 detailing many very technical aspects of iOS 7’s core security functionality. Security expert Steve Gibson spent three consecutive episodes of the Security Now! podcast delving into the details covered by this white paper.
The iOS 7.0 release itself fixed a total of 80 security vulnerabilities. It was followed by a total of seven security updates (prior to the release of iOS 8) that fixed 111 vulnerabilities.
September 2014: iOS 8

One of the most innovative new security and privacy features of iOS 8 is that when it uses Wi-Fi to scan for things nearby, for example to more accurately determine your phone’s location, iOS now uses a random spoofed MAC address rather than the true physical MAC address of your phone’s wireless hardware. This feature was added, in part, because some retail stores had begun using mobile device MAC addresses to track where customers walked, how much time they spent in each section, and how often they frequented the store — all without explicitly asking the customer for permission to track them, and without giving them any way to opt out other than putting their phone in airplane mode.
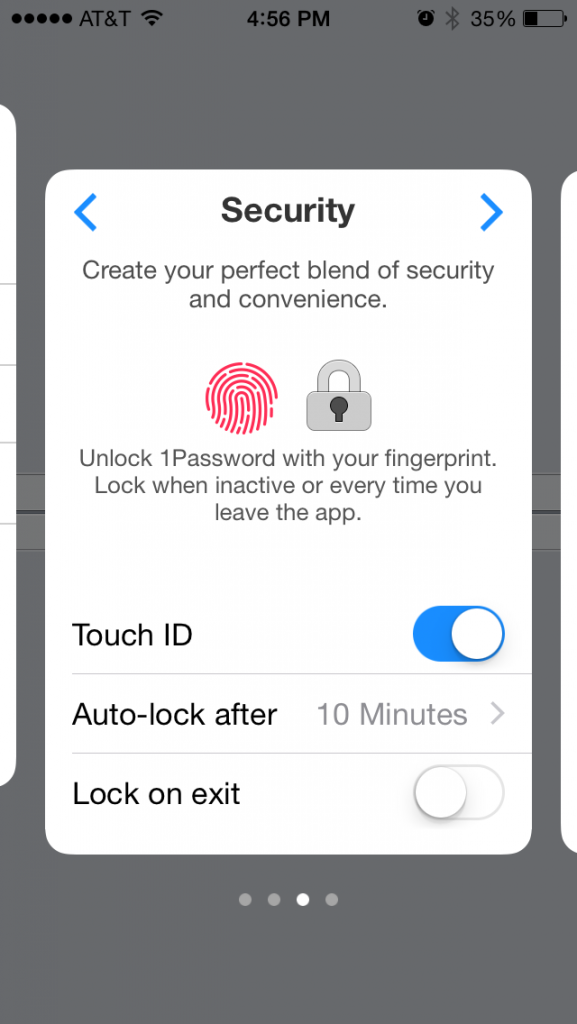
Beginning in iOS 8, third-party apps such as 1Password (pictured) can use Touch ID. Image credit: Andrew Cunningham of Ars Technica
Apple opened up Touch ID authentication to third-party developers in iOS 8. This means that any app that adds the feature can prompt you to place your finger on the Home button to unlock the app, or certain parts of the app.
![]() In iOS 8, Apple added DuckDuckGo as an optional search provider to Safari (although Google continued to be the Web browser’s default search engine). DuckDuckGo prides itself on being “the search engine that doesn’t track you,” making a point of not collecting any personal information from users. Check out Intego’s interview of DuckDuckGo founder and CEO Gabriel Weinberg.
In iOS 8, Apple added DuckDuckGo as an optional search provider to Safari (although Google continued to be the Web browser’s default search engine). DuckDuckGo prides itself on being “the search engine that doesn’t track you,” making a point of not collecting any personal information from users. Check out Intego’s interview of DuckDuckGo founder and CEO Gabriel Weinberg.
 Along with the introduction of HealthKit, Apple added new options in the Settings app’s Privacy section for Health and Motion & Fitness. Similarly, when HomeKit was added in iOS 8.1, a corresponding Privacy option was available for it as well.
Along with the introduction of HealthKit, Apple added new options in the Settings app’s Privacy section for Health and Motion & Fitness. Similarly, when HomeKit was added in iOS 8.1, a corresponding Privacy option was available for it as well.
Several other new security and privacy enhancements in iOS 8 can be found in a blog post by Louie Abreu (hat tip to Ars Technica).
The iOS 8.0 release itself fixed a total of 56 security vulnerabilities. It was followed by a total of eight security updates (prior to the release of iOS 9) that fixed 219 vulnerabilities.
September 2015: iOS 9

The most controversial feature of iOS 9 was the introduction of Content Blockers, a new category of software downloadable from the App Store. Content Blockers can be used to either hide Web page components from view, or block them outright so they won’t be loaded in the first place. Apple states that the types of content that can be blocked include “cookies, images, resources, pop-ups, and other content.”  Of course, ad blocking is one of the most common uses for content blockers, which brings ethical considerations into play about businesses’ need to monetize their content via advertisements versus users’ right to privacy and security; third-party advertisement systems have unintentionally hosted dangerous content several times in recent years. See also Intego’s write-up about Content Blockers as well as Ars Technica’s overview which delves further into the ethical and technical debate.
Of course, ad blocking is one of the most common uses for content blockers, which brings ethical considerations into play about businesses’ need to monetize their content via advertisements versus users’ right to privacy and security; third-party advertisement systems have unintentionally hosted dangerous content several times in recent years. See also Intego’s write-up about Content Blockers as well as Ars Technica’s overview which delves further into the ethical and technical debate.
Apple made six-digit passcodes the default instead of the traditional four-digit passcodes. This effectively increased the number of possible PIN combinations from 10,000 to one million. Of course, a longer and more complex custom password (via Apple’s “Custom Alphanumeric Code” option) is still a much better option than numerals only. See Intego’s walkthrough on how to switch to a stronger iOS passcode.
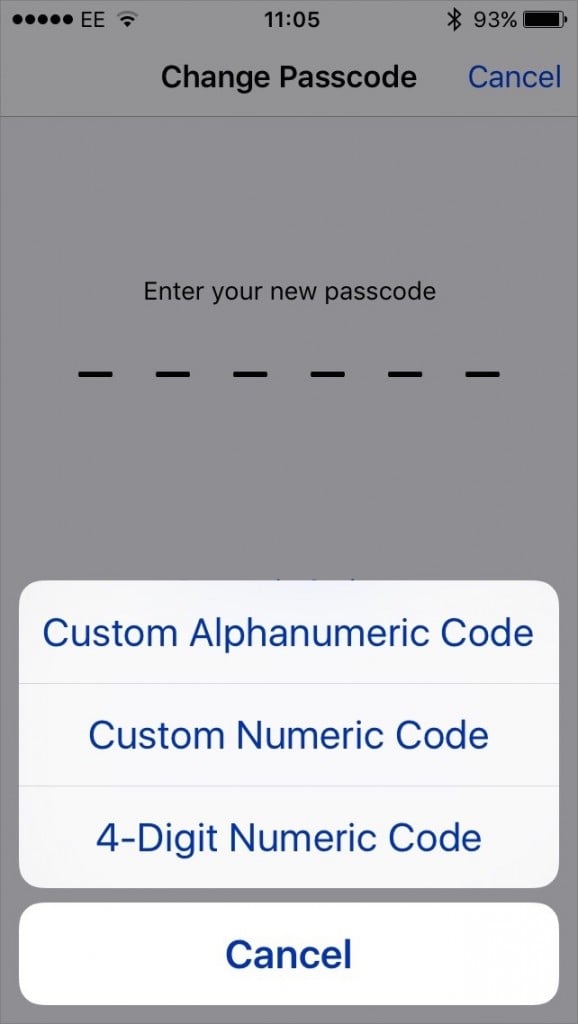
Passcode options in iOS 9
As noted in our companion article about macOS security and privacy features, Apple introduced App Transport Security (ATS), which encourages developers to use HTTPS and more specifically TLS 1.2 with forward secrecy (the latest successor to SSL), when their apps initiate Web requests to back-end servers (for example, to send or receive user data from the “cloud”). Apps created for iOS 9 and OS X 10.11 El Capitan have this feature enabled by default, but for now Apple allows developers to easily opt out and continue making connections using weaker encryption (e.g. SSL) or without encryption (HTTP).
If you have both iOS 9 and OS X El Capitan, Apple encourages you to enable two-factor authentication for your Apple ID. You may be asking yourself, “Hasn’t that feature been around for a while?” The answer is no, not exactly. Apple has another feature that it calls two-step verification, but Apple’s two-factor authentication takes advantage of functionality built into the latest versions of iOS and OS X. You can read all the details about the new functionality in Apple’s support article: Two-factor authentication for Apple ID.
You can read more about iOS 9 privacy and security features in this Apple support article about iOS 9 privacy as well as the latest version of Apple’s iOS Security white paper (PDF).
The iOS 9.0 release itself fixed a total of 105 security vulnerabilities.
What’s Next?
Apple has already publicly announced a security feature that will be included in iOS 9.3. The upcoming iOS 9 update will give users the ability to lock individual notes in the Notes app using Touch ID or a password.
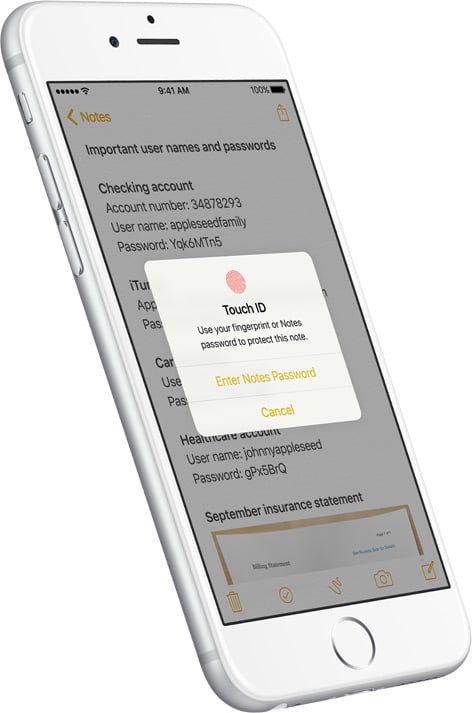
iOS 9.3 will allow Touch ID locking for Notes. Image credit: Apple
Each new version of iOS has included additional features, enhancements, and modifications that have improved the baseline security and privacy of the mobile operating system. It is commendable that Apple continues to include new and innovative improvements with each release. Of course, as is expected of major software companies, Apple also releases security updates to remediate vulnerabilities discovered in the current version of the OS.
Even with all that Apple has done and continues to do to keep iOS users safe, it’s critical for users to stay aware of the various types of attacks they may face on a daily basis, and to continually keep up on how to avoid falling victim to them. We encourage you to subscribe to The Mac Security Blog via the e-mail sign-up form in the sidebar, and to follow us on Facebook and Twitter, to stay abreast of iOS and Mac security threats.
What security and privacy features has Apple added to macOS over the past decade? Check out our companion article, The Evolution of macOS Security and Privacy Features.