SysJoker: Cross-Platform Backdoor Malware for Mac, Windows, and Linux
Posted on
by
Joshua Long

SysJoker is one of the most recently discovered Mac malware families. But SysJoker is not just Mac malware—it’s cross-platform malware that can also infect PCs running Windows or Linux.
Intego detects this malware’s various components as OSX/SysJoker.gen, OSX/SysJoker.lct, Linux/SysJoker.A, and Win32/SysJoker.A.
Let’s examine this new threat and what makes it unique.
How was SysJoker discovered?
According to Intezer, SysJoker “was first discovered during an active attack on a Linux-based web server of a leading educational institution.” Mac and Windows variants were found layer. Although the malware was discovered in December 2021, it may have been deployed sometime earlier in the second half of the year.
What does SysJoker do to an infected computer?
SysJoker pretends to be an operating system update mechanism. In reality, though, it has been observed to collect specific information about the infected computer, such as the MAC address, user name, and IP address. Thus its primary goal appears to be espionage, or in other words, spying on the victim.
The initial macOS SysJoker component is named types-config.ts, masquerading as either a TypeScript or MPEG transport stream video file. However, the file is actually a universal Mach-O binary, meaning that it’s designed to infect Macs with either an Intel or Apple Silicon (e.g. M1) processor.
The malware has methods of persistence, meaning it can continue to actively infect a computer after a reboot. Because it communicates with a command and control (C&C) server, it’s possible for the malware to receive additional instructions—and download additional components and upgrade its capabilities—at any time.
How can one remove or prevent SysJoker and other threats?
Unfortunately, the threat mitigation features that Apple has built into macOS—such as notarization, Gatekeeper, XProtect, and MRT—do not block many types of threats. Thus, Apple’s own macOS protection methods are insufficient by themselves.
Related: Do Macs need antivirus software?
 Intego VirusBarrier X9, included with Intego’s Mac Premium Bundle X9, can protect against, detect, and eliminate SysJoker malware. VirusBarrier is designed by Mac security experts, and it protects against a much wider variety of malware than Apple’s mitigation methods.
Intego VirusBarrier X9, included with Intego’s Mac Premium Bundle X9, can protect against, detect, and eliminate SysJoker malware. VirusBarrier is designed by Mac security experts, and it protects against a much wider variety of malware than Apple’s mitigation methods.
If you believe your Mac may have been infected, or to prevent future infections, it’s best to use antivirus software from a trusted Mac developer that includes real-time scanning, such as Intego VirusBarrier X9—which also protects Macs from M1-native malware, cross-platform malware, and more. Intego recently earned a 100% detection rating for Mac malware in two independent tests conducted by AV-Comparatives and AV-TEST.
And if you’re a Windows user, Intego Antivirus for Windows can protect your PC from SysJoker, too.
Note: Intego customers running VirusBarrier X8, X7, or X6 on older versions of Mac OS X are also protected from these threats. It is best to upgrade to the latest versions of VirusBarrier and macOS, if possible, to ensure your Mac gets all the latest security updates from Apple.
What can we learn from the domains used by SysJoker?
As noted by Patrick Wardle, the domain graphic-updater[.]com — which the malware appears to use as a C&C server — resolves to the IP address 23.254.131[.]176. As of Tuesday, accessing this IP address via a browser would display a list of files hosted on a Web server:
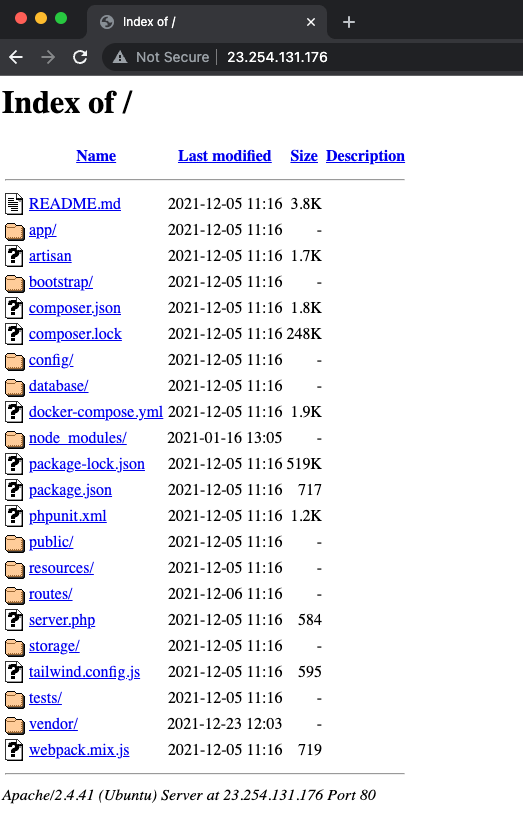
Was this SysJoker’s C&C server? Image: Wardle
Interestingly, it appears that the version of Apache running on this server was 2.4.41. This Apache version was originally released in August 2019 and contains numerous known vulnerabilities. It’s therefore plausible that the malware maker or distributor may have hacked into someone else’s server and hijacked it to use as their C&C server.
As of Thursday, the HTTP server hosted at this IP address appears to be offline. Additionally, the server github[.]url-mini[.]com that had been hosting Windows malware appears to be offline now, and Google appears to have removed the two C&C-related text files from Google Drive.
Indicators of compromise (IoCs)
Unlike most Mac malware, this malware is not signed using an Apple-issued Developer ID. Rather, the types-config.ts file uses an ad-hoc signature with the identifier test-555549448174817ef4cf398d975b7860466eaec7.
The following SHA-256 file hashes belong to known SysJoker files associated with this malware campaign:
1a9a5c797777f37463b44de2b49a7f95abca786db3977dcdac0f79da739c08ac macOS a26c69d3221eaca93eb29f3c7b67bcccbaca18595211efd8a73324f0519e51e3* macOS bd0141e88a0d56b508bc52db4dab68a49b6027a486e4d9514ec0db006fe71eed Linux d028e64bf4ec97dfd655ccd1157a5b96515d461a710231ac8a529d7bdb936ff3 Linux 1ffd6559d21470c40dcf9236da51e5823d7ad58c93502279871c3fe7718c901c Windows 61df74731fbe1eafb2eb987f20e5226962eeceef010164e41ea6c4494a4010fc Windows *hash first reported by Intego
The following files and folders may potentially be found on an infected Mac:
/Library/LaunchAgents/com.apple.update.plist /Library/MacOsServices /Library/MacOsServices/updateMacOs /Library/SystemNetwork ~/Library/LaunchAgents/com.apple.update.plist ~/Library/MacOsServices ~/Library/MacOsServices/updateMacOs ~/Library/SystemNetwork
Note that ~ denotes the user’s home folder, e.g. /Users/username.
The following domains, IP address, and files hosted on Google Drive have been observed to have ties with this malware. Network administrators can check logs to try to identify whether any computers on their network may have attempted to contact one of these sites between December 2021 and today.
23.254.131[.]176 bookitlab[.]tech github[.]url-mini[.]com graphic-updater[.]com office360-update[.]com winaudio-tools[.]com drive[.]google[.]com/uc?export=download&id=1-NVty4YX0dPHdxkgMrbdCldQCpCaE-Hn drive[.]google[.]com/uc?export=download&id=1W64PQQxrwY3XjBnv_QAeBQu-ePr537eu
Is SysJoker known by any other names?
Other vendors’ names for threat components from this malware campaign may include variations of: Backdoor:MacOS/SysJoker.A, Backdoor.Linux.SYSJOKER.YXCALZ, Backdoor.OSX.SysJoker.gen, Backdoor.SysJoker!1.DB62, Backdoor/OSX.Agent.360176, Backdoor/W32.SysJocker, BehavesLike.Win32.Vundo.ch, BScope.Trojan.Occamy, E64/SysJoker.A, ELF:Joker-A [Trj], Linux.BackDoor.SysJoker, LINUX/Agent.roatu, LINUX/Agent.xbpol, Linux/SysJoker.A!tr, Linux/SysJokr-A, Mac.BackDoor.SysJoker.1, MacOS:Joker-A [Trj], MacOS/SysJoker.A, Mal/Generic-S + Troj/DwnLd-VP, Mal/Generic-S + Troj/Steal-CFG, Osx.Backdoor.Sysjoker.Ahog, OSX.S.Agent.360176, OSX/SysJoker.A!tr, RDN/Sysjoker, TR/Dldr.Agent.rukwx, TR/Redcap.rjsiq, Trj/GdSda.A, TROJ_FRS.VSNTAC22, Trojan-Downloader.SysJoker, Trojan:Linux/Vigorf.A, Trojan:Win32/Casdet!rfn, Trojan.Agent.SysJocker, Trojan.Linux.OUTBREAK.USELVAC22, Trojan.Linux.SysJoker.B, Trojan.MAC.SysJoker.A, Trojan.OSX.Agent, Trojan.OSX.SysJoker.m!c, Trojan.Win32.Sysjoker, W32.Trojan.Sysjoker, and Win32/SysJoker.A.
How can I learn more?
For additional technical details about the SysJoker malware, you can read Intezer’s and Patrick Wardle’s write-ups.
We discussed SysJoker on episode 222 of the Intego Mac Podcast. Be sure to follow the podcast to make sure you don’t miss any episodes! You’ll also want to subscribe to our e-mail newsletter and keep an eye here on The Mac Security Blog for the latest Apple security and privacy news.
You can also subscribe to our e-mail newsletter and keep an eye here on The Mac Security Blog for the latest Apple security and privacy news. And don’t forget to follow Intego on your favorite social media channels: ![]()
![]()
![]()
![]()
![]()
![]()
![]()
SysJoker logo images based on: “Jester- Joker Card” by GoShows (CC BY 2.0) and “Matrix – iPhone Background” by Patrick Hoesly (CC BY 2.0); both images modified.