Pegasus spyware hacks iPhones of prominent individuals
Posted on
by
Kirk McElhearn and Joshua Long
Information has come to light this week about Pegasus spyware and how it has targeted many prominent individuals, from journalists and activists to heads of state—such as French president Emmanuel Macron—tens of thousands of high-profile people were targeted by this spyware which is able to monitor and extract data from infected devices.
The Pegasus spyware is developed by the Israel-based firm NSO Group, and is sold to government intelligence, military, and law enforcement agencies to provide “authorized governments with technology that helps them combat terror and crime.”
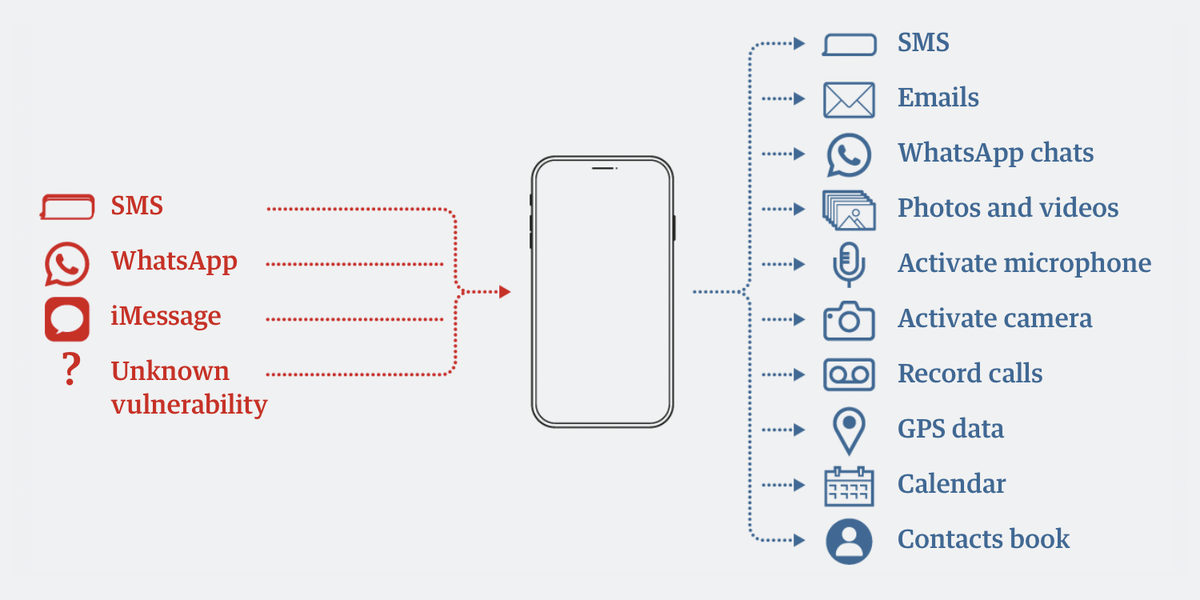
Pegasus can infect iPhones and Android phones, usually leverages zero-day vulnerabilities, and, in some cases, is even delivered via a zero-click exploit. These attacks could be successful either if a malicious user is within range of a phone they want to hack, or sometimes simply calling a phone or sending it an e-mail could exploit vulnerabilities and allow the spyware to gain control of the device. Other possible vectors include messages sent by SMS (as we discussed in 2016), iMessage, or WhatsApp (as we discussed in 2019), and in some cases users may not even need to click links or take any actions to enable the spyware to activate.
When Pegasus is installed on a phone, it can collect data from a device and send it back to an attacker. It can copy data from text messages, emails, WhatsApp chats, calendars, and contacts. It can also siphon off photos, activate the microphone and camera, record calls, and more. Anything done on a phone infected by Pegasus can be monitored remotely.
NSO Group only sells this spyware to governments, law enforcement organizations and the military, suggesting that any abuses of the software are state-sanctioned attacks. The data discovered by the “Pegasus Project”—a collaborative journalistic investigation into the NSO Group and its clients—includes some 50,000 phone numbers of infected devices. The majority of these numbers were located in Mexico, the Middle East, and North Africa, but there were also many numbers in European countries, Afghanistan, and others. Member’s of the Dalai Lama’s inner circle were targeted, and it is suspected that the Indian government carried out these attacks. It is also suspected that the hack of Jeff Bezos’ phone, which occurred in 2018, was carried out using Pegasus under orders of the Saudi government.
It isn’t easy to find out if a device has been infected by Pegasus; Amnesty International outlines the forensics used to determine if phones are compromised, by searching for traces left behind, and has released a Mobile Verification Toolkit (MVT) that advanced users can install to find if their phone has been affected. This is not just an app that runs with a tap or a click, but requires some installation via Terminal, which then checks data in an iPhone backup on a computer.
While this sort of targeted attack is mainly used against high-profile individuals, it’s not impossible that others may have been targeted.
Apple said in a statement to The Guardian (emphasis ours):
Apple unequivocally condemns cyberattacks against journalists, human rights activists, and others seeking to make the world a better place. For over a decade, Apple has led the industry in security innovation and, as a result, security researchers agree iPhone is the safest, most secure consumer mobile device on the market. Attacks like the ones described are highly sophisticated, cost millions of dollars to develop, often have a short shelf life, and are used to target specific individuals. While that means they are not a threat to the overwhelming majority of our users, we continue to work tirelessly to defend all our customers, and we are constantly adding new protections for their devices and data.
Apple is admitting that they cannot prevent spyware like Pegasus from infecting iPhones, but brushes off the threat, saying that it is only “used to target specific individuals.” However, the statement goes on to say that “we continue to work tirelessly to defend all our customers,” which seems to conflict the first part of the statement, because clearly they are saying that they can’t protect everyone.
While the vulnerabilities used for this sort of exploit “often have a short shelf life,” new ones are discovered all the time. While some “white-hat hackers” who discover vulnerabilities report them to Apple—in part to benefit from the company’s bug-bounty program, which pays security researchers who find serious issues—”black-hat hackers” meanwhile sell exploits for up to millions of dollars to companies like NSO Group or to gray-market vulnerability brokers.
The fact that Apple doesn’t allow antivirus software to run on iOS devices means that users have no easy way of knowing if they are infected by malware like Pegasus. The only known way to identify the existence of Pegasus spyware on an iPhone is via MVT—which isn’t easy to use. (Other malware on iPhones can be identified by VirusBarrier X9—the only Mac antivirus that can scan the contents of iPhones.)
Apple releases security updates regularly, to fix vulnerabilities that it has discovered or that have been disclosed to the company, but this is a perpetual cat-and-mouse game, as each new operating system update presents new possibilities for malicious users to find ways to break into devices.
To date, tens of thousands of phones are known to have been infected by Pegasus spyware to take control of the phone and its data.
How can I learn more?
You can read our 2016 and 2019 reports on the Pegasus spyware via our Pegasus archives.
 Each week on the Intego Mac Podcast, Intego’s Mac security experts discuss the latest Apple news, security and privacy stories, and offer practical advice on getting the most out of your Apple devices. Be sure to follow the podcast to make sure you don’t miss any episodes.
Each week on the Intego Mac Podcast, Intego’s Mac security experts discuss the latest Apple news, security and privacy stories, and offer practical advice on getting the most out of your Apple devices. Be sure to follow the podcast to make sure you don’t miss any episodes.
We discuss Pegasus spyware and more on episode 197 of the Intego Mac Podcast.
You can also subscribe to our e-mail newsletter and keep an eye here on Mac Security Blog for the latest Apple security and privacy news. And don’t forget to follow Intego on your favorite social media channels: Facebook, Instagram, Twitter, and YouTube.
Image credits: Pegasus attack vectors and capabilities graphic by the Guardian.