New EvilOSX Malware Spotlights Risk of Poor Password Hygiene
Posted on
by
Jay Vrijenhoek

Around the same time OSX/Dok was discovered last year, a remote access tool (RAT) for macOS and OS X was also found, called EvilOSX. While OSX/Dok made headlines, the sample of EvilOSX malware didn’t receive much attention at that time, because while capable and dangerous it was a low risk threat that had not been used on a large scale. Use of the open source EvilOSX was mostly by those experimenting with it, and perhaps by some who genuinely attempted to infect a target.
With little fanfare, EvilOSX was quickly forgotten by most; that is, until a few days ago when John Lambert posted the following tweet:
If you are interested in OSX malware, have a look at this new sample of EvilOSX that just appeared on VT.
1⃣Repo: https://t.co/vI8jv0ILWO
2⃣Source and decodes: https://t.co/o9t78vTZTt
3⃣Hash: 89e5b8208daf85f549d9b7df8e2a062e47f15a5b08462a4224f73c0a6223972a pic.twitter.com/8DWJYXY2E5— John Lambert (@JohnLaTwC) February 21, 2018
What we’re looking at here is indeed a new sample of EvilOSX malware and looks to be from the same malware author, Marten4n6, who created the original variant. The new variant of EvilOSX is still a RAT, and while still not currently used as part of a malware campaign in large scale attacks, the author still appears hard at work.
Here’s a comparison of features, comparing the old EvilOSX malware vs. the new variant:
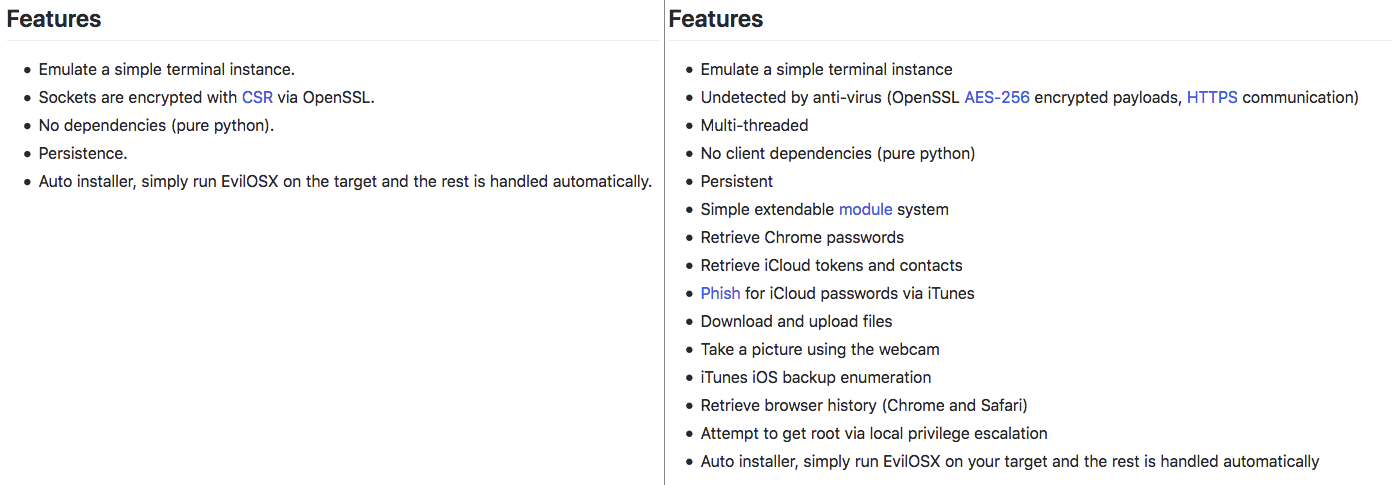
The new EvilOSX also includes an update module, so the malware can update itself if a new version comes out. Needless to say, this is not a RAT you want on your system. However, with the risk of infection currently low, there is no need for alarm, especially if you are an Intego VirusBarrier customer with up-to-date malware definitions. If EvilOSX ever makes its way onto your system, despite what the EvilOSX author claims, Intego VirusBarrier will detect it as OSX/EvilOSX and eliminate it accordingly.
What is the infection vector?
EvilOSX is a remote access tool (RAT) that, for now, would most likely find its way onto your Mac through an angry ex or a “look at me I’m a cool h4ck3r!” coworker. With EvilOSX being open source and easily accessible, at any time it may find its way to a piece of malware that is far more widespread. Currently, as far as we know and as mentioned earlier, we are not aware of EvilOSX being bundled with malware that attempts to infect Macs on a large scale.
Where does OSX/EvilOSX install?
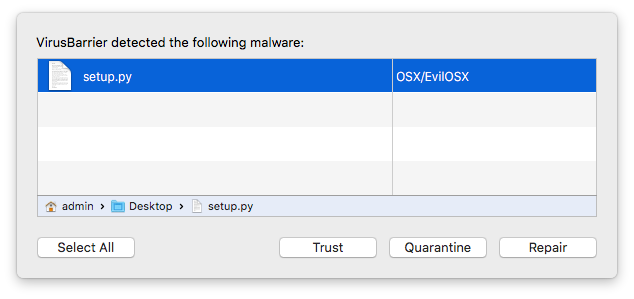
A launch agent is placed in ~/Library/LaunchAgents, named “com.apple.EvilOSX.plist.” The RAT itself is placed inside a hidden directory, in ~/Library/Containers, named “.EvilOSX.” There are just two components to EvilOSX, as the setup script is automatically removed once installation is complete. As soon as EvilOSX touches down on your system, VirusBarrier will let you know.
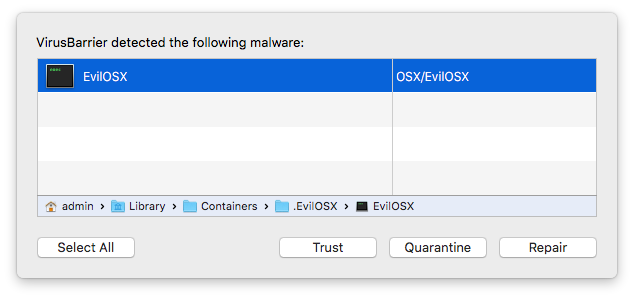
If for some reason you trust the file and run it, VirusBarrier will alert you again when EvilOSX installs itself in a hidden directory.
Meanwhile, NetBarrier will alert you to a connection attempt that is being made to icanhazip.com.
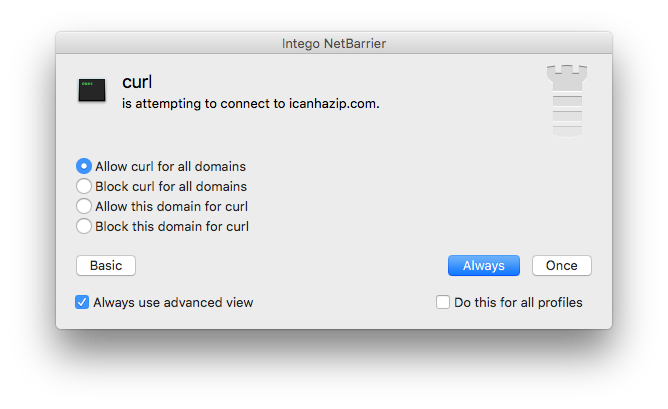
As you can see, there is a very slim chance EvilOSX can infect a system if the user is paying attention to the various popups generated by it. Even though the creator of EvilOSX states that his malware is “undetected by anti-virus,” this is simply not the case.
Should Mac users be concerned about OSX/EvilOSX?
Currently no malware exists that uses EvilOSX as a payload, but targeted Mac users are at risk. For now, in order to infect Macs with EvilOSX, someone would need physical access to your machine, or a victim would need to be tricked via social engineering to download and install it.
If your Mac is not properly locked down, EvilOSX should concern you. Installation of the malware does not require an administrator password and, according to the malware author, a Mac can be infected in about 10 seconds or less. This means anyone with access to your computer can install EvilOSX if you walk away for even just a minute. For this and other security reasons, always make sure your Mac is locked down as soon as you leave your desk. For tips on how to encrypt and password protect your system, have a look here. A simple screensaver password is a big step to keeping unwanted snoops out of your system when you go to grab a coffee or take a bathroom break.
Unfortunately, if someone has the kind of access to your Mac that allows them to install EvilOSX, they can also easily instruct your anti-virus product to trust the installed RAT. By the time you get back to your desk, you wouldn’t know that your Mac was infected and your anti-virus solution wouldn’t inform you.
If your Mac is properly locked down, I’d say there is currently no cause for concern.
How to tell if your Mac is infected (and removal instructions)
In your User folder /Library/LaunchAgents, look for a file named “com.apple.EvilOSX.plist.” If it’s there, delete it. This is the file EvilOSX uses for persistence.
Also in your User folder /Library/Containers, a hidden directory will be present if the system is infected with EvilOSX. To make the invisible directory visible, use the following key combination: Command-Shift-. (period)
Now look for a folder named “.EvilOSX.” If it’s there, delete it. This is the actual RAT contacting the Command and Control (C&C) server and looking for instructions. If infections are found and the components subsequently deleted, restart your Mac, empty the trash and restart again. Your Mac should now be free of EvilOSX.
For Intego VirusBarrier customers, protection comes in the form of updated virus definitions, which will detect and remove all of the OSX/EvilOSX files.
How to protect yourself from OSX/EvilOSX
We are not aware of EvilOSX being bundled with other malware that attempts to infect Macs on a large scale. As long as you follow the usual precautions and make sure your files come from a trusted source, your Mac is locked down properly, and you have a few up-to-date layers of security in place, the risk of getting infected by EvilOSX or any other malware is very low.
EvilOSX made a brief appearance on the radar last year not to be heard from again until a few days ago. This shows that development on these kinds of tools is ongoing. This goes for all kinds of malware and shows the importance of the security industry to constantly be on the lookout for new potential threats. For you, the user, this shows the importance of always keeping your system and security solutions up to date to ensure you are protected from vulnerabilities and malware as soon as they are discovered.