OSX/ZuRu Mac malware spread through Trojan apps
Posted on
by
Joshua Long

A new variety of Mac Trojan horse malware has been caught in the wild. And, surprisingly, the latest Trojan horses don’t claim to be Adobe Flash Player installers this time.
Seekers of several macOS applications—notably including iTerm2, a third-party Terminal app for Mac—may have unintentionally downloaded an OSX/ZuRu Trojan horse.
Let’s examine this recent malware, how it spread, and how to eliminate an infection.
How was OSX/ZuRu discovered?
Pan Xiaopan discovered the first in-the-wild sample of OSX/ZuRu while searching for the Mac app iTerm2 on the Chinese search engine Baidu.
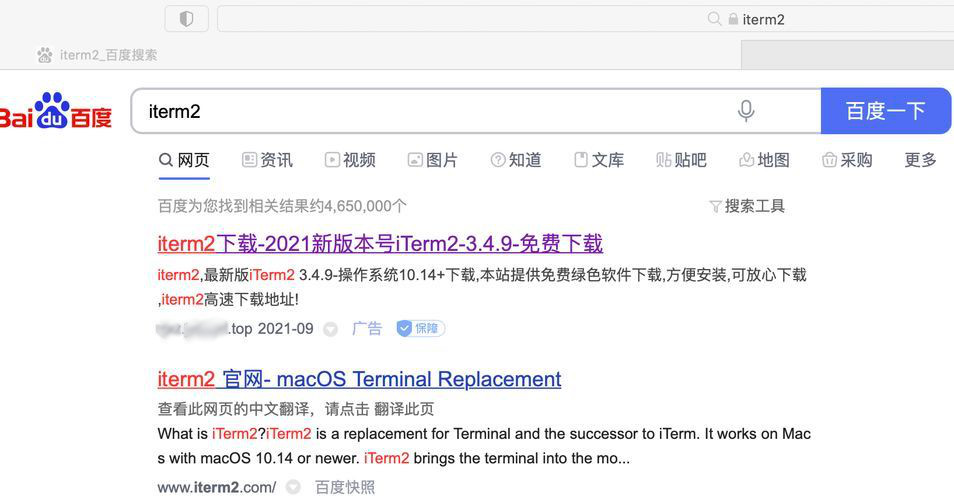
Baidu poisoned search results for iTerm2 led to OSX/ZuRu malware. (Screenshot: Pan Xiaopan)
Rather than the top result being the legitimate iTerm2, the first link actually led to a malware site designed to look virtually indistinguishable from the legitimate software’s homepage. This technique of introducing malicious results into search queries is known as search engine poisoning.
Attempting to download iTerm2 from the lookalike site would instead download a disk image infected with an OSX/ZuRu Trojan horse.
The real iTerm2 site is hosted at iterm2.com, which appeared as the second result in the Baidu search. The malicious site that linked to the Trojan disk image used a very similar domain: iterm2[.]net.
Baidu has reportedly removed the fraudulent link from its search results.
Researchers later found several other disk images infected with OSX/ZuRu, disguised as other Mac software including Microsoft Remote Desktop, Navicat, SecureCRT, and also reportedly SnailSVN.
What does OSX/ZuRu do to an infected Mac?
If a user is tricked into running the Trojan horse, OSX/ZuRu downloads and runs a Python script that collects various information from an infected Mac, including but not limited to:
- the user’s macOS Keychain database
- the user’s bash and zsh Terminal command history
- the user’s iTerm2 saved state
- the user’s ssh keys and known hosts
- the system’s /etc/hosts file
Many of these files could contain highly sensitive information such as passwords and private keys.
The malware then attempts to exfiltrate a zip archive of this data to the server from which the Python script was downloaded.
An outbound firewall, such as Intego NetBarrier X9, can block malware from exfiltrating data from your Mac.
How can one remove or prevent OSX/ZuRu and other threats?
Given that Apple’s threat mitigation features such as notarization, Gatekeeper, XProtect, and MRT do not block many types of threats, it is evident that Apple’s own macOS protection methods are insufficient by themselves.
Related: Do Macs need antivirus software?
 Intego VirusBarrier X9, included with Intego’s Mac Premium Bundle X9, can protect against, detect, and eliminate OSX/ZuRu malware.
Intego VirusBarrier X9, included with Intego’s Mac Premium Bundle X9, can protect against, detect, and eliminate OSX/ZuRu malware.
VirusBarrier is designed by Mac security experts, and it protects against a much wider variety of malware than Apple’s mitigation methods.
If you believe your Mac may have been infected, or to prevent future infections, it’s best to use antivirus software from a trusted Mac developer that includes real-time scanning, such as Intego VirusBarrier X9—which also protects Macs from M1-native malware, cross-platform malware, and more. Intego recently earned a 100% detection rating for Mac malware in two independent tests conducted by AV-Comparatives and AV-TEST.
Note: Intego customers running VirusBarrier X8, X7, or X6 on older versions of Mac OS X are also protected from these threats. It is best to upgrade to the latest versions of VirusBarrier and macOS, if possible, to ensure your Mac gets all the latest security updates from Apple.
Indicators of compromise (IoCs)
Following are some specific ways to identify whether a Mac may have been infected by OSX/ZuRu.
Apple has since revoked the Developer ID that was used for signing this malware. The developer name and Team ID of the revoked dev account is:
Jun Bi (AQPZ6F3ASY)
The following SHA-256 file hashes belong to known OSX/ZuRu files associated with this malware campaign.
04e1d0e1b6aa0852677f6bbf64a60ea33bc0b07b197280b22a155f8e94aead5c 0560072ef7055802e977865324d95171126fe68cb797d4ebc0bda328435014fa 1e462f8716275dbae6acb3ff4f7a95624c1afb23c5069fa42a14ed49c2588921 2c269ff4216dc6a14fd81ffe541994531b23a1d8e0fbd75b9316a9fa0e0d5fef 4e8287b61b0269e0d704c6d064cb584c1378e9b950539fea366ee304f695743f 548c7e456d11d9acf06589be1a13a8c4229a3e41139570ee8e078e421ff0890c 5ca2fb207762e886dd3336cf1cb92c28f096a5fbb1798ea6721b7c94c1395259 6df91af12c87874780cc9d49e700161e1ead71ae045954adbe7633ec9e5e45ff 7874df70f3e732af5676dd6f25eeb89de0cfaa84d5b39aca2cfc6f5bff6a23a7 ae0510032cd4699ef17de7ed1587918ffcd7ff7c9a77fc45f9d68effe2934132 b556ff7d0095ddf87535b3b9c3e40aacdd65f4dbe5ceedb31613826857161bfb e5126f74d430ff075d6f7edcae0c95b81a5e389bf47e4c742618a042f378a3fa f1277ace85516f9decce8d86f5faceb9bb2ac9dd4faed5563c98b00df0545c3f ffb0a802fdf054d4988d68762d9922820bdc3728f0378fcd6c4ed28c06da5cf0
The following domains and IP address have been observed to have ties with this malware:
kaidingle[.]com 47.75.123[.]111 iterm2[.]net rjxz.jxhwst[.]top
Any recent network traffic to or from any of these domains should be considered a possible sign of an infection.
Is OSX/ZuRu known by any other names?
Other vendors’ names for threat components from this malware campaign may include variations of: DMG/ZuRu.A, Mac.BackDoor.CobaltStrike.2, Mac.Trojan.ZuRu, MacOS:CobalStrike-C, MacOS:ZuRu-A, OSX/CobaltStrike.A, OSX/CobaltStrike.Beacon.B, OSX/iTerm, OSX/Spy.ZuRu.A, OSX/ZuRu-A, Python:Agent-CC, Trojan-Spy.OSX.Zuru, Trojan:MacOS/Multiverze, Trojan:Script/Wacatac.B, Trojan:Win32/Casdet!rfn, Trojan.MAC.ZuRu.A, Trojan.MacOS.ZURU, Trojan.OSX.Zuru, and Win32.Trojan-spy.Zuru.
How can I learn more?
For more technical details of the recent OSX/ZuRu campaign, you can read Patrick Wardle’s write-up (and Pan Xiaopan’s original write-up, in Chinese).
We discussed OSX/ZuRu on episode 206 of the Intego Mac Podcast. Be sure to follow the podcast to make sure you don’t miss any episodes! You’ll also want to subscribe to our e-mail newsletter and keep an eye here on The Mac Security Blog for the latest Apple security and privacy news.
Be sure to follow Intego on your favorite social media channels: Facebook, Instagram, Twitter, and YouTube (click the 🔔 to get notified about new videos).