OSX/Dok Can Read Encrypted Web Traffic, Open a Backdoor
Posted on
by
Jay Vrijenhoek

Security researchers last Friday discovered a new piece of Mac malware, named OSX/Dok, that affects all versions of OS X, including the latest macOS Sierra. Once installed, OSX/Dok is able to intercept all of your web traffic, even that which is transmitted over HTTPS.
Hidden alongside Dok, Intego’s malware research team found another variant of the malware, called “Bella,” which is very similar on the surface but installs a Remote Access Trojan (RAT) on infected Macs. Intego VirusBarrier with up-to-date malware definitions will detect and eradicate each component as OSX/Dok.A and OSX/Dok.B respectively.
What is the infection vector?
OSX/Dok is spread through phishing campaigns and was seen posing as an email with questions about tax returns, written in German. According to Check Point researchers, OSX/Dok mostly targets European Mac users, which we will note appears accurate as these phishing emails have not been reported in other languages.
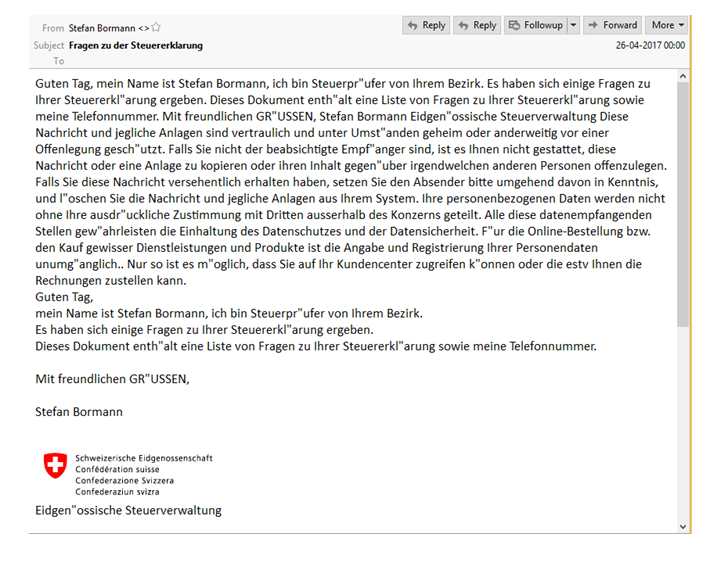
Image credit: Check Point. Sample of the phishing email spreading the malware.
The phishing email contains a Dokument.zip file that, when opened, shows a file named “Dokument,” which uses an old Preview application icon that has not been used since OS X 10.9 Mavericks (and a poor quality one at that).
![]()
Compared to the actual Preview app icon used up until OS X 10.9 Mavericks, you can see in the above image that the quality is very poor. To savvy Mac users, this is an instant giveaway that something is amiss. On Macs running OS X 10.10 Yosemite or newer, the icon for Preview has actually changed, so it becomes even easier to spot the fake.
Where does OSX/Dok.A install?
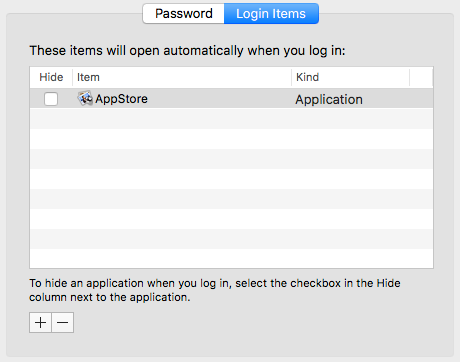
When the Dokument file is opened, a fake warning is displayed while the malware application AppStore.app is placed in the /Users/Shared/ folder.
Now in its new location, OSX/Dok will execute itself and give all users on the system permission to run the malware, delete the original application copy, and then place itself in the Login Items to ensure it gets a chance to install its payload.
OSX/Dok then displays a full screen message, stating that a security issue has been identified and updates are required. This window can not be moved or closed.
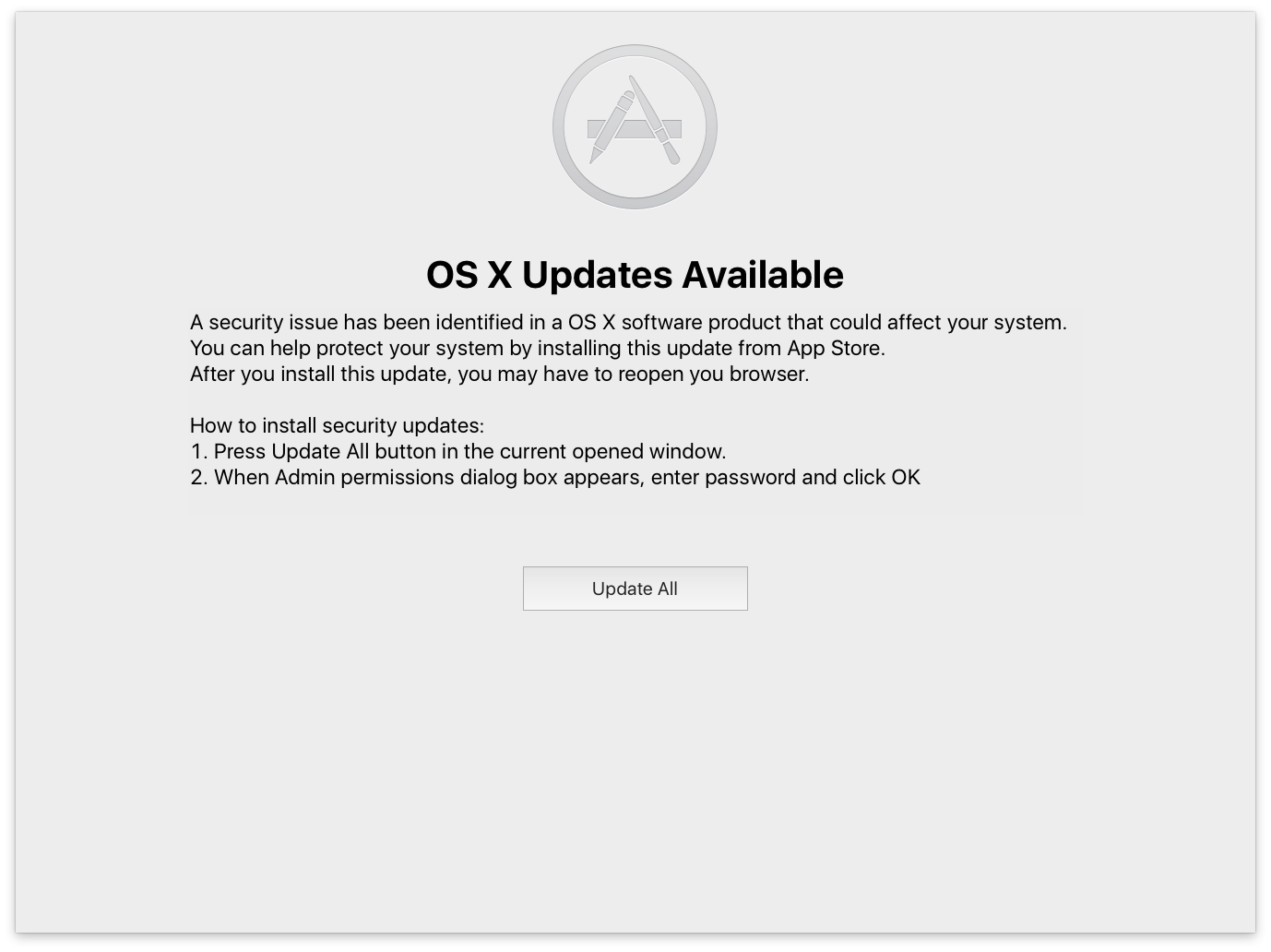
This fake security alert is a ploy to get your administrator password. It asks for your password when the “Update All” button is clicked. The window will stay up for about 5 minutes while in the background several changes to the system are made. These changes include the installation of brew, which in turn facilitates the installation of TOR and SOCAT. If OSX/Dok obtains administrator privileges, thanks to the provided password, it grants admin privileges wherever needed without the user ever seeing a password prompt again. This is done by modifying the sudoers file.
When Dok is done, the full screen window will close and the Login Item is removed. The login item is replaced, however, with several LaunchAgents in /Users/*User*/Library/LaunchAgents.
com.apple.Safari.pac.plist
com.apple.Safari.proxy.plist
homebrew.mxcl.tor.plist
The first two files are obviously meant to look like they belong to Apple’s Safari browser; they don’t, however. The third file might be trying to masquerade as something related to Homebrew, a popular macOS package manager.
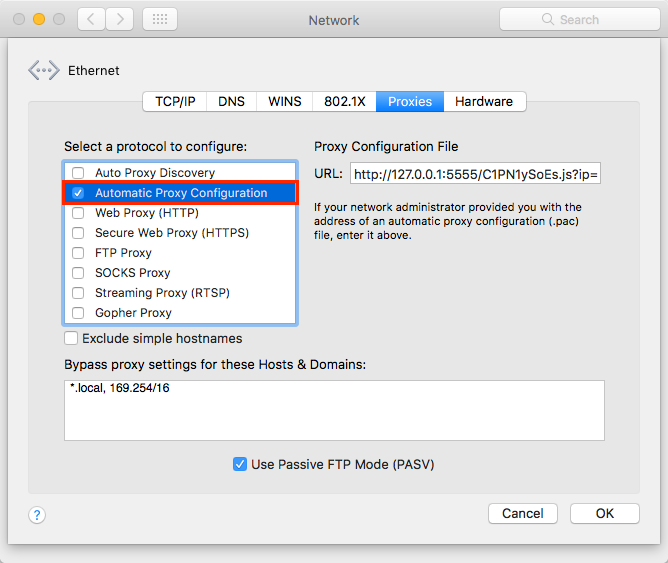
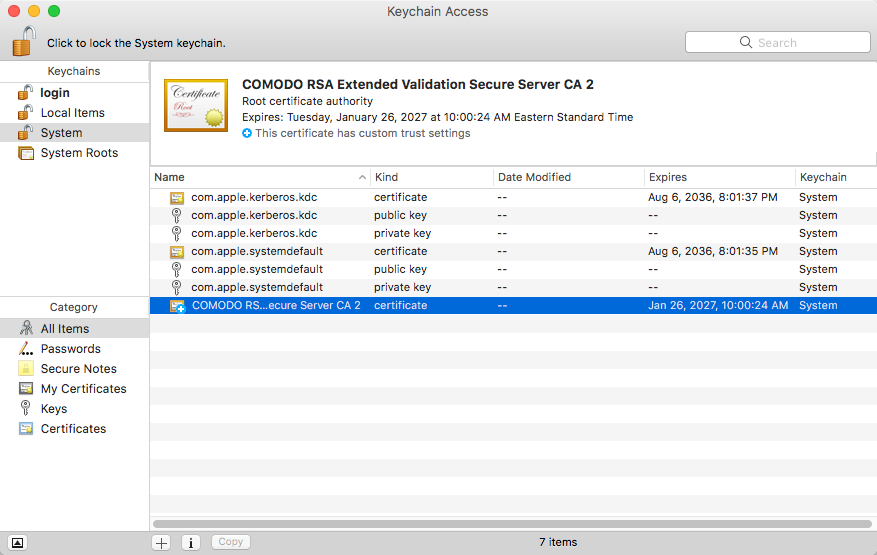
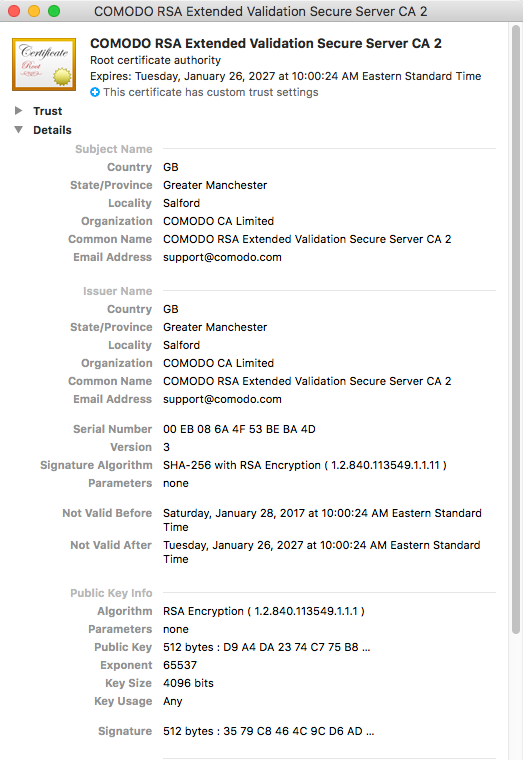
Other system changes that are made include a change to the Network settings to set up a proxy, and the installation of a root certificate in the System.keychain, which allows the attacker to intercept all web traffic sent through that proxy. Victims will not know that their information is being intercepted, noted Check Point:
By abusing the victim’s new-found trust in this bogus certificate, the attacker can impersonate any website, and the victim will be none the wiser.
The proxy setup can be viewed by opening System Preferences > Network > Select your active network connection > Advanced > Proxies.
Open up Applications > Utilities > Keychain Access, and select the System keychain. There you can see the root certificate Dok installed.
As a result of all of the above actions, when attempting to surf the web, the user’s web browser will first ask the attacker web page on TOR for proxy settings. The user traffic is then redirected through a proxy controlled by the attacker, who carries out a Man-In-the-Middle attack and impersonates the various sites the user attempts to surf. The attacker is free to read the victim’s traffic and tamper with it in any way they please.
An additional surprise: OSX/Dok.B
Alongside the discovery of Dok, Intego’s malware research team found another piece of malware, called “Bella,” identified by Intego VirusBarrier as OSX/Dok.B. While related to OSX/Dok.A, its behavior appears to be very different from the other version.
The malware comes as a .zip file, named Dokument.zip, and contains an application named Dokument. Just like the above mentioned malware, it installs an AppStore application in /Users/Shared/. The application is signed with the same certificate as well. That is where the similarities end.
OSX/Dok.B does not display a full screen window that claims software updates need to be installed. Instead, it installs a backdoor named Bella, which is open-source and available on GitHub. Bella uses a Command & Control (C&C) server located in Russia and is capable of exfiltrating iOS backups, keychains, iMessage chat history and screenshots it makes. It’s also able to phish for passwords, capture data from your camera and microphone, and more. In short, Bella is a full fledged Remote Access Trojan (RAT) that doesn’t leave any visible traces on the infected system.
Whereas OSX/Dok.A modified the system’s network settings and left visible files in the user /Library/LaunchAgents folder, OSX/Dok.B makes no visible changes to any system settings and the files that are placed in the library are invisible.
The following files are placed in the User library:
~/Library/Containers/.bella/Bella
~/Library/Containers/.bella/bella.db
~/Library/LaunchAgents/com.apple.iTunes.plist
If Bella was able to gain root access, these items will be found in the root library instead.
Should Mac users be concerned about OSX/Dok?
At the time of writing, Apple has already revoked the developer certificate that was used to sign the malicious applications, which should avoid further infections. This kind of malware can be very dangerous as it can intercept traffic that is supposed to be secure and compromise a host of user data. Just think of what can happen if your online banking login credentials are intercepted.
How to tell if your Mac is infected (and removal instructions)
- Open System Preferences > Network > Select your active network connection > Advanced > Proxies. If an automatic proxy configuration is set as shown in the image earlier in this article, your Mac was Dok’d. Uncheck the proxy, click OK and apply the changes.
- Have a look in the Users/Shared folder. If the AppStore application is present, delete it.
- In your User folder /Library/LaunchAgents, look for the following files:
- com.apple.Safari.pac.plist
- com.apple.Safari.proxy.plist
- homebrew.mxcl.tor.plist
If these files are present, delete them.
To manually check for the invisible files OSX/Dok.B placed, you first need to make invisible files visible in the Finder. In macOS Sierra this can quickly be done with the following key combination:
Command-Shift-. (period)
For older OS X versions this can be done by typing the following commands in the Terminal app:
$ defaults write com.apple.Finder AppleShowAllFiles true
$ killall Finder
When done, enter the same commands but change “true” to “false”.
With the hidden files now visible, check both the root library and the user library for these files:
- /Containers/.bella/Bella
- /Containers/.bella/bella.db
- /LaunchAgents/com.apple.iTunes.plist
For Intego VirusBarrier customers, protection comes in the form of updated virus definitions, which will detect and remove all of the OSX/Dok files. However, in order for VirusBarrier to grab these updated definitions, the proxy that was set by OSX/Dok must be disabled first if you found yourself infected before these definitions were made available. As long as the proxy is on, VirusBarrier will not be able to contact the update servers. Intego VirusBarrier detects all OSX/Dok components as OSX/Dok.A and OSX/Dok.B.
How to protect yourself from OSX/Dok
Phishing scams are still very popular; even with most people aware of it, the success rates are so high that attackers continue using the strategy. Never open email attachments unless you were expecting that attachment and know the person it came from. If there is any doubt, call the person who supposedly sent you the email to verify it’s real.
OSX/Dok shows once again how easy it is for a developer certificate to be abused, and how effective it is in bypassing macOS’s built-in Gatekeeper protection. Stay vigilant and avoid downloading every email attachment you receive, and you will minimize the risk of installing malicious software, particularly OSX/Dok.