Month in review: Apple security in October 2017
Posted on
by
Joshua Long
October has been another busy month! There’s a new variant of the Proton malware, a Wi-Fi “KRACK” attack affecting Apple devices, warnings about potential attacks against iOS device users, and plenty more.
Eltima Software Infected with OSX/Proton.C Malware
 One of the most significant bits of Mac-specific news in October was the discovery of another legitimate software developer whose download server was distributing compromised (infected) versions of the company’s apps.
One of the most significant bits of Mac-specific news in October was the discovery of another legitimate software developer whose download server was distributing compromised (infected) versions of the company’s apps.
You may recall that the same thing happened back in May with the popular Handbrake video-encoding software, and in 2016 the Transmission BitTorrent client was compromised on two separate occasions.
 This time, Eltima Software was the target—specifically its Mac apps Elmedia Player and Folx (a download manager and BitTorrent client).
This time, Eltima Software was the target—specifically its Mac apps Elmedia Player and Folx (a download manager and BitTorrent client).
If an unsuspecting Mac user downloaded and installed one of the infected apps, a new variant of the OSX/Proton malware would be installed as well. This malware gives an attacker virtually complete control over an infected Mac, and it attempts to steal a victim’s passwords, cryptocurrency wallets, browsing history and login data, and more.
For more information, including how to find out whether your Mac was infected, see Intego’s main article OSX/Proton Malware is Back! Here’s What Mac Users Need to Know.
Wi-Fi KRACK Attack
 A security researcher recently found a series of vulnerabilities in most implementations of the WPA2 Wi-Fi security protocol. Dubbed “KRACK attacks” (short for “key reinstallation attacks”), the vulnerabilities could enable a nearby attacker—within Wi-Fi range of a victim—to spy on all wirelessly transmitted data, and in some cases even inject and manipulate data.
A security researcher recently found a series of vulnerabilities in most implementations of the WPA2 Wi-Fi security protocol. Dubbed “KRACK attacks” (short for “key reinstallation attacks”), the vulnerabilities could enable a nearby attacker—within Wi-Fi range of a victim—to spy on all wirelessly transmitted data, and in some cases even inject and manipulate data.
As discussed in the third episode of the Intego Mac Podcast, it is important to note that WPA2 with AES is still the safest Wi-Fi encryption standard available for most users, but you’ll want to check to see whether any firmware updates are available for your wireless access point (and if there aren’t any available, ask the manufacturer when to expect an update).
 Apple has not stated whether its AirPort wireless base stations will be updated, according to AppleInsider.
Apple has not stated whether its AirPort wireless base stations will be updated, according to AppleInsider.
It’s not just wireless base stations that are affected, though.
According to the discoverer of the vulnerabilities, just about every device with Wi-Fi is likely vulnerable to KRACK attacks, including Mac and iOS devices.
Earlier in the month, Apple stated that its developer betas of upcoming “.1” versions of macOS, iOS, watchOS, and tvOS had already been updated to patch the KRACK vulnerabilities on the client side.
On October 31, Apple released macOS High Sierra 10.13.1 (and related security updates for macOS Sierra 10.12.6 and OS X El Capitan 10.11.6), iOS 11.1, tvOS 11.1, and watchOS 4.1, which addressed KRACK and other vulnerabilities. (See our article Apple Releases macOS 10.13.1 High Sierra, iOS 11.1 with Security Fixes for further details on the security content of these updates.)
Strangely, however, it appears that Apple may not have addressed KRACK for all supported hardware, including several older models of the iPhone and—most bizarre of all—even the current generation of Apple Watch.
As of today, the following devices that are capable of running the latest version of iOS, tvOS, or watchOS may nevertheless still be vulnerable to KRACK attacks:
- Apple TV (4th generation)
- Apple Watch (1st generation)
- Apple Watch Series 3
- iPhone 5s
- iPhone 6
- iPhone 6 Plus
- iPhone 6s
- iPhone 6s Plus
- iPhone SE
- iPad Air
- iPad Air 2
- iPad mini 2
- iPad mini 3
- iPad mini 4
- iPod touch 6th generation
We’ve reached out to Apple for clarification and comment, and will update this article if and when Apple responds.
In the mean time, if you haven’t yet upgraded to the latest OS, or if your device is on the list above (or if your device is an older model that cannot be upgraded to the latest OS), it’s best to avoid using public Wi-Fi networks if possible—but if you must use them, use a VPN and follow these best practices.
For more information on KRACK attacks, see Intego’s article Wi-Fi KRACK Vulnerabilities: FAQ for Mac, iPhone and iPad Users and the official KRACK Attacks site.
Apple Patches Disk Utility APFS Flaw and Keychain Stealing Vulnerability
On October 5, Apple released “macOS High Sierra 10.13 Supplemental Update,” a patch to address two serious vulnerabilities in the new Mac operating system.
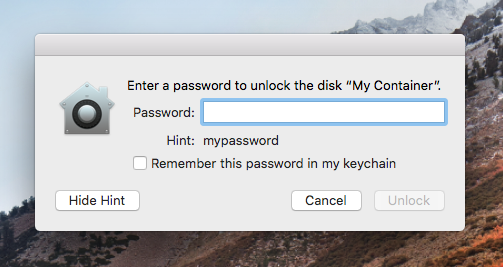 Disk Utility stored actual APFS volume passwords as hints. Image: Hacker Noon
Disk Utility stored actual APFS volume passwords as hints. Image: Hacker Noon
The first vulnerability was a serious flaw in Disk Utility that would cause an APFS volume password to be visible when a user would click on Show Hint. For more information, see Intego’s article Apple Issues Emergency Update to Fix Disk Utility Bug in macOS High Sierra.
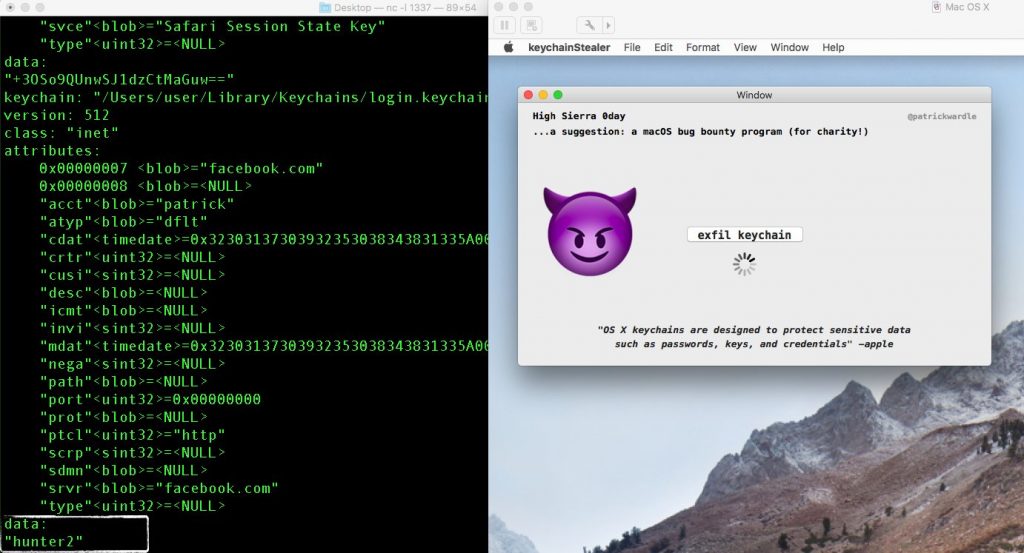 Malware can potentially steal all your Keychain passwords. Image: Patrick Wardle
Malware can potentially steal all your Keychain passwords. Image: Patrick Wardle
The second vulnerability fixed in this patch is one that I covered in our September month in review: a Keychain password-stealing vulnerability discovered by Patrick Wardle. Although this vulnerability affects older versions of macOS too, Apple has so far only patched it for High Sierra, so be sure to upgrade to High Sierra if your Mac is capable of running it (here’s how to find out).
iOS Attack #1: Apple ID Phishing Dialogs
An iOS developer named Felix Krause has warned about two potential attacks against iOS users.
Krause claims that it’s easy for any iOS app to spoof the “Sign In to iTunes Store” or “Sign-In Required” system dialog boxes and steal the user’s Apple ID password.
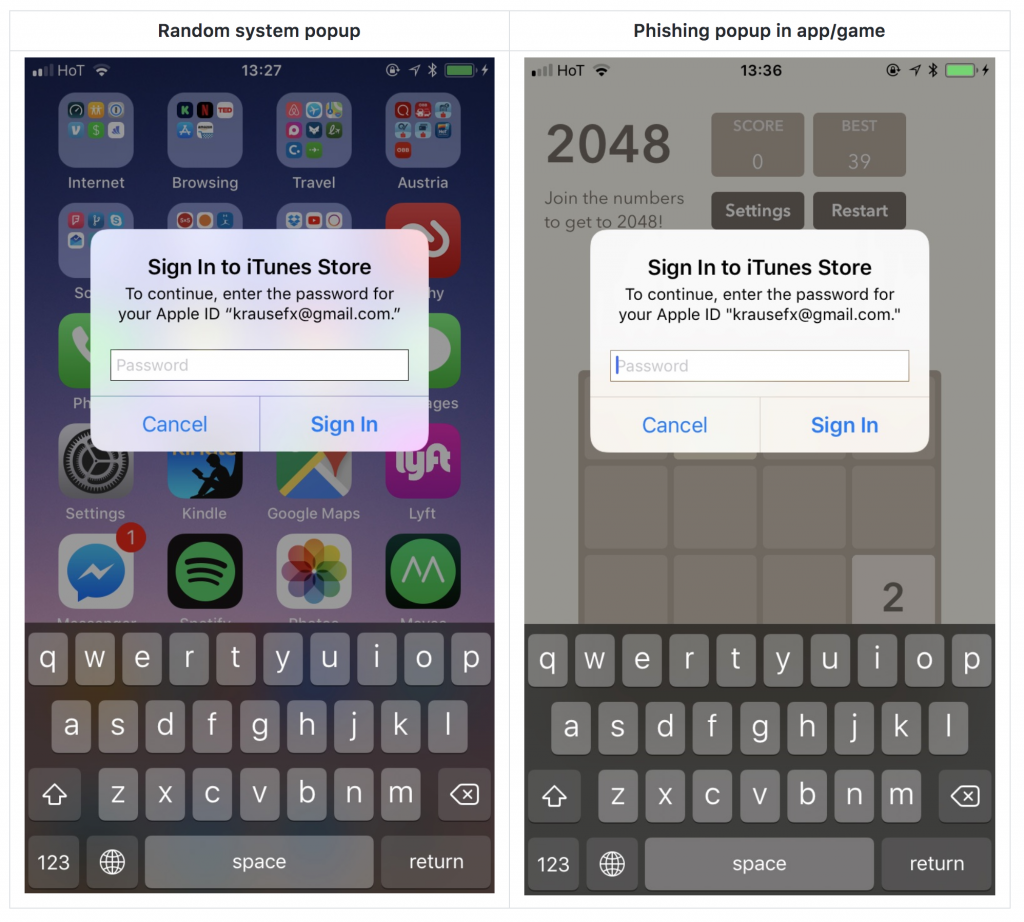 iOS apps can maliciously simulate Apple ID prompts. Image: Krause
iOS apps can maliciously simulate Apple ID prompts. Image: Krause
There are a number of things that a diligent user can do to mitigate this attack (until or unless Apple takes action to prevent developers from spoofing system dialog boxes):
- When one of these dialog boxes appears prompting you for your credentials, press the Home button; if you’re taken to the iOS home screen showing your list of installed apps, then the dialog box you saw was a phishing attempt originating from the app you were using when the dialog box appeared, according to Krause.
- Don’t even start typing your password into the dialog box until after you’ve followed step 1 to verify that it’s legitimate. If it’s a phishing attempt, then even if you click Cancel instead of Sign In, the app can still steal whatever portion of your password you’ve already typed.
- Enable two-factor authentication for your Apple ID, if you haven’t already done so. Although an attacker could potentially trick you into giving them a verification code to allow them to sign into your account, at least it gives you one more chance to realize you’ve made a mistake, back out, and change your Apple ID password before any harm can be done.
- Use a unique password for your Apple ID account. That way, if your Apple ID password does get stolen, an attacker won’t be able to successfully use that password to break into your other accounts (e-mail, etc.). And, of course, if you have any reason to suspect that some third party has obtained your password, be sure to reset your password to something completely different.
Krause has reported the vulnerability to Apple.
iOS Attack #2: Apps Can Do Creepy Things with Your Camera
Krause also warned that if you’ve ever authorized an iOS app to use your device’s camera, the app retains that permission until or unless you explicitly revoke it.
While that may not seem like a bad thing (and usually isn’t), it could be a problem for apps from less ethical developers. Once a user has granted an app permission to use the camera, any time the app is in the foreground it has complete access to your front and back cameras. According to Krause, an app’s developer could exploit this functionality to do some creepy things without the user’s knowledge, including such things as:
- secretly take pictures or stream video of the user whenever the user has the app open
- determine the exact location of the user (via a captured photo or video’s metadata)
- create a 3D model of the user’s face
- predict the user’s mood based on facial expressions (which a developer could use as a factor in deciding what to show the user on the screen)
 Apps with camera access can secretly analyze a user’s mood. Image: Krause
Apps with camera access can secretly analyze a user’s mood. Image: Krause
Unlike MacBooks and iMacs, the iPhone, iPad, and iPod touch do not have indicator lights that warn a user whenever a camera is active. Krause implies that it may behoove Apple to either include such lights on future revisions of iOS device hardware, or to update iOS to force the status bar to always be visible and show an indicator icon whenever the camera is active. Krause also suggests that Apple could change the behavior of iOS to include a way to grant apps only temporary access to the camera.
Until or unless Apple takes measures like these, there are a few ways that a user can mitigate such attacks or unwanted uses of their camera:
- Never grant a new app access to the camera unless it’s absolutely necessary. If you later decide that an app really does need to use the camera, you can always turn on the feature for that app temporarily via the Settings app.
- In the Settings app, scroll to the bottom and review the list of apps that are currently installed, and tap on each one to see which permissions you’ve granted. Revoke any permissions that you feel are unnecessary (permissions may include things like Camera, Photos, Location, or Cellular Data).
- If you’re still concerned, you can always physically block the camera lenses on your device whenever you’re not using them. You can find a variety of options for sale online by searching for phrases such as iPhone camera cover.
Krause has also reported this issue to Apple.
Other Security News, in Brief
There were other notable goings-on in the security world in October. Some highlights:
 Intego launched a new audio podcast featuring hosts Kirk McElhearn and me, Josh Long; you can read more about it here and subscribe via iTunes.
Intego launched a new audio podcast featuring hosts Kirk McElhearn and me, Josh Long; you can read more about it here and subscribe via iTunes. Intego has a new YouTube video series based on my month-in-review column. Check out September’s video, and be sure to subscribe and then click on the bell icon (?) to get notified when each new episode is available.
Intego has a new YouTube video series based on my month-in-review column. Check out September’s video, and be sure to subscribe and then click on the bell icon (?) to get notified when each new episode is available.- A Bloomberg report alleged that Apple had lowered its accuracy standard for Face ID security in the new iPhone X due to supply issues; however, Apple released a statement to The Verge and other news outlets the same day claiming that Bloomberg’s report was “completely false.”
 High-ranking U.S. Department of Justice official Rod Rosenstein called for “responsible encryption,” meaning weakened encryption that governments could bypass (along with any malicious party who gains access to a government’s method of entry). The EFF’s cybersecurity director Eva Galperin told CNET that “Calling it ‘responsible encryption’ is hypocritical. Building insecurity in your encryption is irresponsible.” You can read CNET and Ars Technica‘s coverage of the story.
High-ranking U.S. Department of Justice official Rod Rosenstein called for “responsible encryption,” meaning weakened encryption that governments could bypass (along with any malicious party who gains access to a government’s method of entry). The EFF’s cybersecurity director Eva Galperin told CNET that “Calling it ‘responsible encryption’ is hypocritical. Building insecurity in your encryption is irresponsible.” You can read CNET and Ars Technica‘s coverage of the story. Google released a three-part series of blog postings sharing technical details of several Broadcom chipset vulnerabilities that Apple mitigated in iOS 11, watchOS 4, and tvOS 11. You can find them here: Part 1, Part 2, Part 3.
Google released a three-part series of blog postings sharing technical details of several Broadcom chipset vulnerabilities that Apple mitigated in iOS 11, watchOS 4, and tvOS 11. You can find them here: Part 1, Part 2, Part 3.- Google rolled out a new “Advanced Protection” program detailing how users can improve their two-factor authentication when logging into Google though the use of two physical security keys. If you have a Google account, check out this New York Times article and Google’s site for further details.
 Facebook users should beware of a scam that may enable a friend (or an attacker who’s posing as your friend, or who has hijacked your friend’s account) to gain control of your Facebook account after alleging that that you’re one of their Trusted Contacts. For details on the attack, see The Hacker News‘ article.
Facebook users should beware of a scam that may enable a friend (or an attacker who’s posing as your friend, or who has hijacked your friend’s account) to gain control of your Facebook account after alleging that that you’re one of their Trusted Contacts. For details on the attack, see The Hacker News‘ article.- Flash had a zero-day vulnerability (again). If you use Flash Player in Safari or Firefox on your Mac, check to make sure it’s updated.
 Speaking of Flash, the Equifax site was caught distributing a malware-laden fake Flash update to visitors using Windows. It is unclear whether the site may have also attempted to foist malware on Mac-using visitors during the time the site was compromised. See Ars Technica‘s report for details. (As mentioned briefly in September’s update, Equifax has recently had several severe security problems come to light.)
Speaking of Flash, the Equifax site was caught distributing a malware-laden fake Flash update to visitors using Windows. It is unclear whether the site may have also attempted to foist malware on Mac-using visitors during the time the site was compromised. See Ars Technica‘s report for details. (As mentioned briefly in September’s update, Equifax has recently had several severe security problems come to light.) More than 50 vulnerabilities have been mitigated in Netgear devices including wireless access points, routers, switches, and network-attached storage, as reported by Threatpost. If you use Netgear products, be sure to check for a firmware update.
More than 50 vulnerabilities have been mitigated in Netgear devices including wireless access points, routers, switches, and network-attached storage, as reported by Threatpost. If you use Netgear products, be sure to check for a firmware update. Reuters reported about an alleged breach at Microsoft that happened in 2013, about which Microsoft has declined to comment. The breach of an internal bug-tracking database allegedly occurred after a Java vulnerability was exploited on Microsoft employees’ Macs.
Reuters reported about an alleged breach at Microsoft that happened in 2013, about which Microsoft has declined to comment. The breach of an internal bug-tracking database allegedly occurred after a Java vulnerability was exploited on Microsoft employees’ Macs.- Dell lost control of a customer support domain for a month, and there’s evidence that it may have been used for malicious intent during that time, as reported by Krebs on Security. (No, this story isn’t in any way Apple related, but part of me can’t help but be amused by Dell’s misfortunes ever since Michael Dell’s infamous slam of Apple in 1997. Also, there are very good lessons here for business owners when it comes to domain registration.)
Stay Tuned! Subscribe to The Mac Security Blog
Be sure to subscribe to The Mac Security Blog to stay informed about Apple security throughout each month.
If you missed Intego’s previous Apple security news roundups for 2017, you can check them out here.
Also, be sure to subscribe to our YouTube channel to get these monthly updates in video form, and click on YouTube’s bell icon (?) to get notified when each new episode is available!
Have something to say about this story? Share your comments below!
Eva Galperin photo credit: USENIX Enigma Conference