Month in Review: Apple Security in May 2017
Posted on
by
Joshua Long

May 2017 was yet another crazy month for Apple security. New Mac malware was distributed through phishing e-mails, a popular Mac app’s download server got compromised and distributed infected copies of software, notorious Windows malware was ported to Mac, Apple released numerous security patches, and more! Read on for more details.
New Mac Malware OSX/Dok Distributed Via Phishing Campaign
Phishing e-mails began circulating in late April and early May that contained an attachment with new Mac malware (detected by Intego VirusBarrier as OSX/Dok.A or OSX/Dok.B).
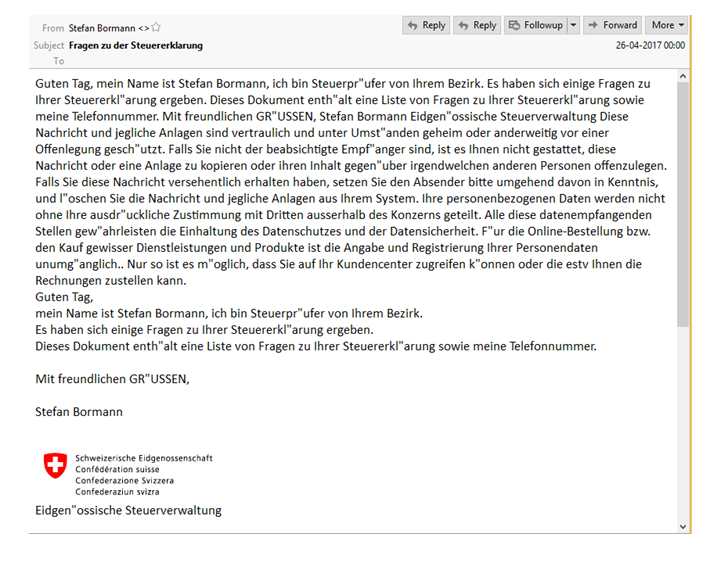
Image credit: Check Point. Sample of the phishing email spreading the malware.
The first variant (OSX/Dok.A) disguises itself as an old version of the macOS Preview app and the Mac App Store, tricking users into typing their password, which then allows the malware to install a malicious SSL/TLS certificate and a TOR proxy to intercept all Web traffic, including sites that would normally be (and may still appear to be) secure.
The second variant (OSX/Dok.B) is a full-fledged remote access Trojan (RAT) that attempts to steal keychains, iOS backups, iMessage chat history, and more from your Mac.
For more details, see OSX/Dok Can Read Encrypted Web Traffic, Open a Backdoor.
Although Apple updated its XProtect signatures and revoked the Apple Developer ID used to sign the first variant, CheckPoint noted that the attackers already began using a new Developer ID and began to further obfuscate their code to try to avoid detection.
New Mac Malware OSX/Proton.B Distributed Via HandBrake Download Server
The download server of popular video transcoding software HandBrake was compromised in early May, causing many who downloaded the software to inadvertently infect their Macs.
The compromised version of HandBrake put up an unusual dialog box, claiming, “HandBrake needs to install additional codecs,” and prompted the user for their administrator username and password.
Users who fell victim were encouraged by HandBrake’s developer to change all passwords in their macOS keychain and any saved browser passwords.
For details, see Handbrake’s Server Compromised, Download Installs Complex Trojan.
Panic Source Code Compromised After HandBrake Hack
![]()
The founder of Panic, a Mac software company known for its Coda and Transmit software (and unrelated to HandBrake), expressed concern that the source code of Panic software was allegedly stolen as a result of having installed the infected version of HandBrake on his Mac.
Panic warned that its code may be repackaged into fake or infected copies of its software. Be sure to only download Panic’s software from a trusted source.
New Mac Malware “Snake” Ported from Windows

Fox-IT reported that the Windows malware known variously as Snake, Turla, Uroburos, and Agent.BTZ has been ported to Mac (or in other words, the malware’s code was re-engineered to work with Macs). The Windows version of the malware has been around for many years and has been used in targeted attacks.
The Mac version of the Snake malware was discovered in a compromised Adobe Flash Player installer, signed with a then-valid Apple Developer ID (although not one issued to Adobe) to bypass Apple’s Gatekeeper protection. Apple has since revoked the certificate, but of course variants signed by another Developer ID could yet appear.
If you must run Adobe Flash Player content, it’s safest to use the version built into Google Chrome, or if you must install the plug-in for Safari and Firefox, be sure to only obtain it from this URL: https://get.adobe.com/flashplayer
Apple Security Updates

On May 15, Apple released security updates for its operating systems and other software, in part to mitigate vulnerabilities used to hack Apple products by several researchers competing in the annual Pwn2Own contest (which we mentioned briefly in our March news roundup).
Apple also appears to have patched the kernel vulnerability in macOS Sierra 10.12.4 that was reported by Patrick Wardle, which we mentioned in our April month in review.
Apple’s Mac operating system, macOS Sierra, has been updated to version 10.12.5, and its mobile operating system iOS has been updated to version 10.3.2 for eligible iPhone, iPad, and iPod touch devices. Security updates were also released for El Capitan, Yosemite, Safari, watchOS, and tvOS.
For details, see Apple Releases macOS Sierra 10.12.5 and More with Security Fixes.
Apple iCloud to Require App-Specific Passwords on June 15

Effective June 15, Apple will require those who use third-party applications with their iCloud account to enable two-step or two-factor authentication and use app-specific passwords for third-party apps (such as Microsoft Outlook, Mozilla Thunderbird, and BusyCal and BusyContacts).
This is a good step in the right direction; however, as noted by Macworld, there’s more that Apple could do to further protect users. For example, Apple could theoretically tighten app-specific passwords to only permit specific functionality, such as allowing access to only contacts or calendars, depending on the app’s actual needs.
Users should be aware that whenever they reset their primary Apple ID password, their old app-specific passwords will no longer work. More details can be found in Apple’s Using app-specific passwords support article.
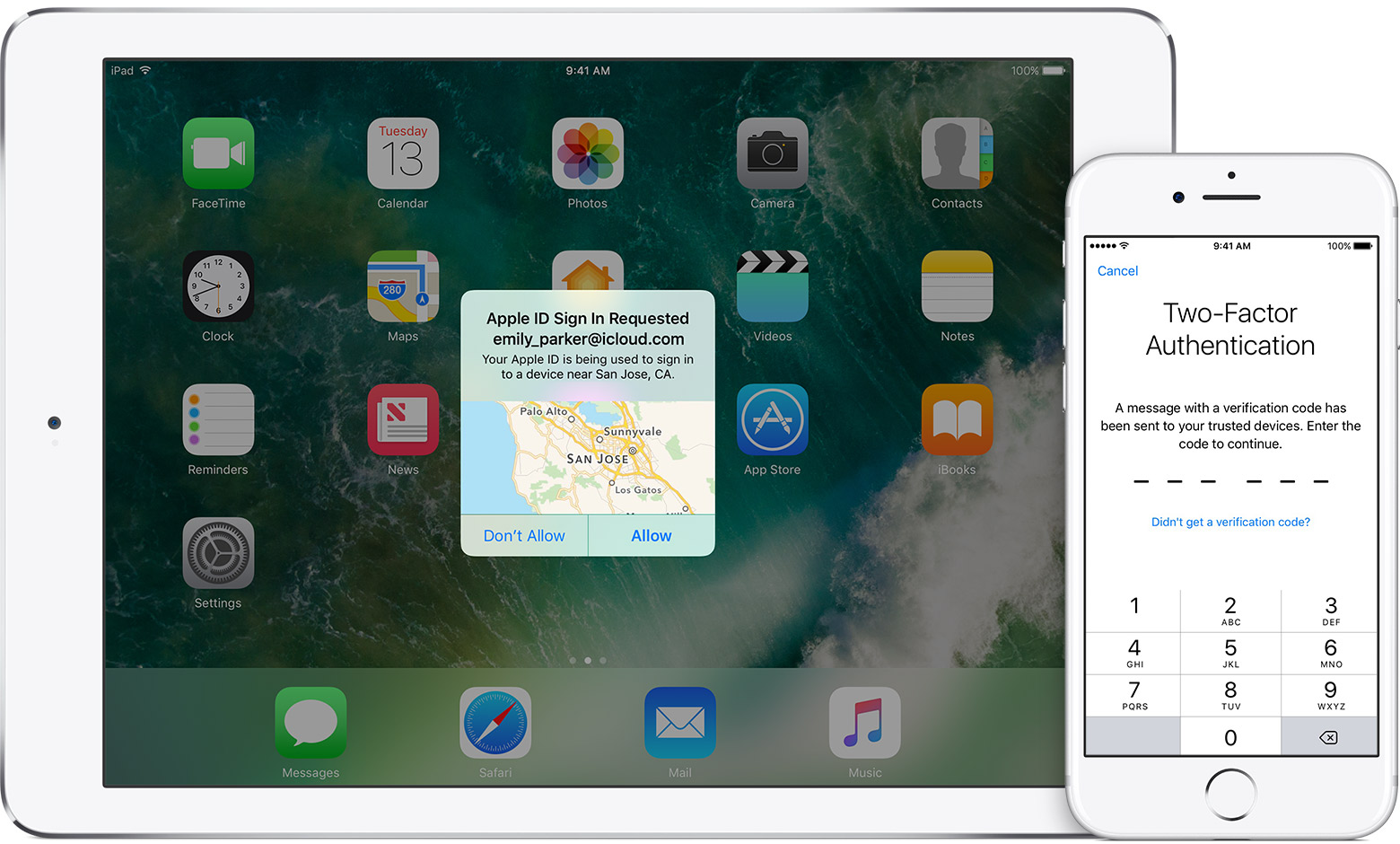
Even if you don’t use third-party apps with your iCloud account, it’s still wise to enable two-factor authentication to protect the security of your Apple ID. Apple recently changed the process of enabling two-factor authentication in iOS 10.3, so check Apple’s documentation for the latest steps to follow for iOS and macOS.
U.S. FTC Cracks Down on Tech Support Scams
The United States Federal Trade Commission (FTC) announced that it is partnering with federal, state, and international organizations to crack down on tech support scams.

Fake tech support alerts are becoming increasingly common. Image credit: Josh Long
The FTC reported that victims have spent millions of dollars on “tech support” to fix non-existent problems with their computers, having been duped by scary scam sites. The sites often claim to be run by Microsoft or Apple, as seen in the screenshot above, and encourage victims to call a phone number to be walked through a process to supposedly clean their computers (while, in reality, victims’ computers were never really infected in the first place).
Several fraudulent organizations based in the United States have recently been stifled, as the FTC’s efforts have led to indictments and arrests of scam operators. Nevertheless, scams like this will continue, so be vigilant; if you see fake warnings in your browser like the one above, don’t fall for them, and be sure to report them to the FTC.
Windows World: Macs Affected By WannaCry?
You’ve most likely seen major news media coverage of WannaCry, which is Windows ransomware capable of spreading itself across a network.
Although the vulnerabilities exploited by WannaCry do not affect macOS, those who use Windows on their Macs (either via Boot Camp or a virtual machine such as VMware Fusion, Parallels Desktop, or Oracle VirtualBox) should be aware of the vulnerability and install the necessary updates.
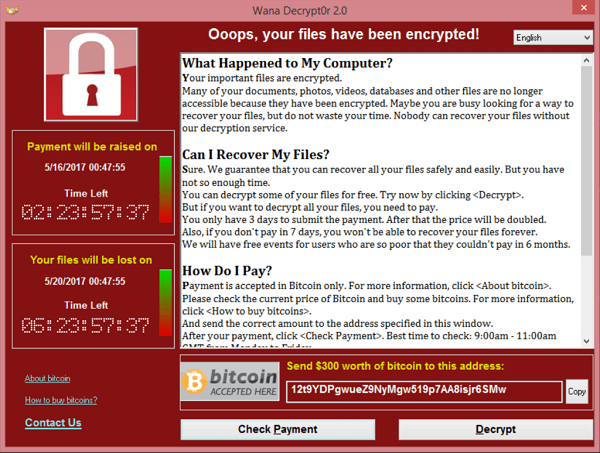
For more information, including how to protect your Mac from ransomware, see WannaCry and the State of Mac Ransomware.
Windows World: Macs Reportedly Unaffected By Intel AMT Vulnerability
A serious vulnerability in Intel’s Active Management Technology (AMT) was recently disclosed to the public that “can allow an unprivileged attacker to gain control of the manageability features” in PC hardware with AMT. Intel has released guidance on how to check for the vulnerability on your systems, how to mitigate the vulnerability if it’s present, and where to obtain firmware patches from various hardware manufacturers.
Mac users may wonder about whether their computers are vulnerable. The Register reported, “Apple Macs, although they use Intel chips, do not ship with the AMT software, and are thus in the clear.”
Stay Tuned! Subscribe to The Mac Security Blog
Be sure to subscribe to The Mac Security Blog to stay informed about Apple security throughout each month.
If you missed Intego’s previous Apple security news roundups for 2017, you can check them out here.
Have something to say about this story? Share your comments below!