Month in review: Apple security in March 2018
Posted on
by
Joshua Long

March was a fairly humbling month for Apple security. An app that employed questionable cryptocurrency mining slipped past Apple’s review process and made its way into the Mac App Store, the Mac was “pwned” again at this year’s Pwn2Own contest, and another major security goof related to APFS passwords was discovered in macOS High Sierra. Meanwhile, a QR code vulnerability in iOS remains un-patched.
Read on for more details.
Unwanted Cryptomining in Mac App Store
![]() In mid-March, an App Store app was caught doing something controversial: mining cryptocurrency on behalf of the app’s developer.
In mid-March, an App Store app was caught doing something controversial: mining cryptocurrency on behalf of the app’s developer.
Evidently, several users of Qbix’s Calendar 2 app were surprised to learn that a recent app update had caused their Macs to start running more slowly and warmer than usual, and with loud fan noise. User reviews warned that the latest versions had embedded a cryptocurrency miner into the app—something which the program’s App Store description didn’t make clear.
There was some debate about whether an App Store app was allowed to mine for cryptocurrencies in this manner. Although Apple’s guidelines did not explicitly forbid mining, one could argue that the app’s mining behavior nevertheless may have implicitly violated some of Apple’s rules. As media and social media discussion of the controversy began to increase, Apple pulled the app from the App Store until the developer removed the mining functionality.
Be sure to check out our latest YouTube video, which demos Calendar 2’s undesirable behavior and shows how to identify whether an app is using a lot of processing power—a possible sign that cryptojacking might be happening in the background.
APFS Passwords Found in Plain Text Log Files
Sarah Edwards reported on her Mac forensics blog, Mac4n6, about two similar security issues related to the plain-text logging of APFS volume passwords.
APFS is Apple’s new file system available in macOS High Sierra, and it was supposed to have been designed with security in mind. However, in a series of three blog posts (first, second, third), Edwards revealed that certain persistent, macOS system log files may contain—in unencrypted plaintext—the passwords with which users encrypted their APFS volumes.
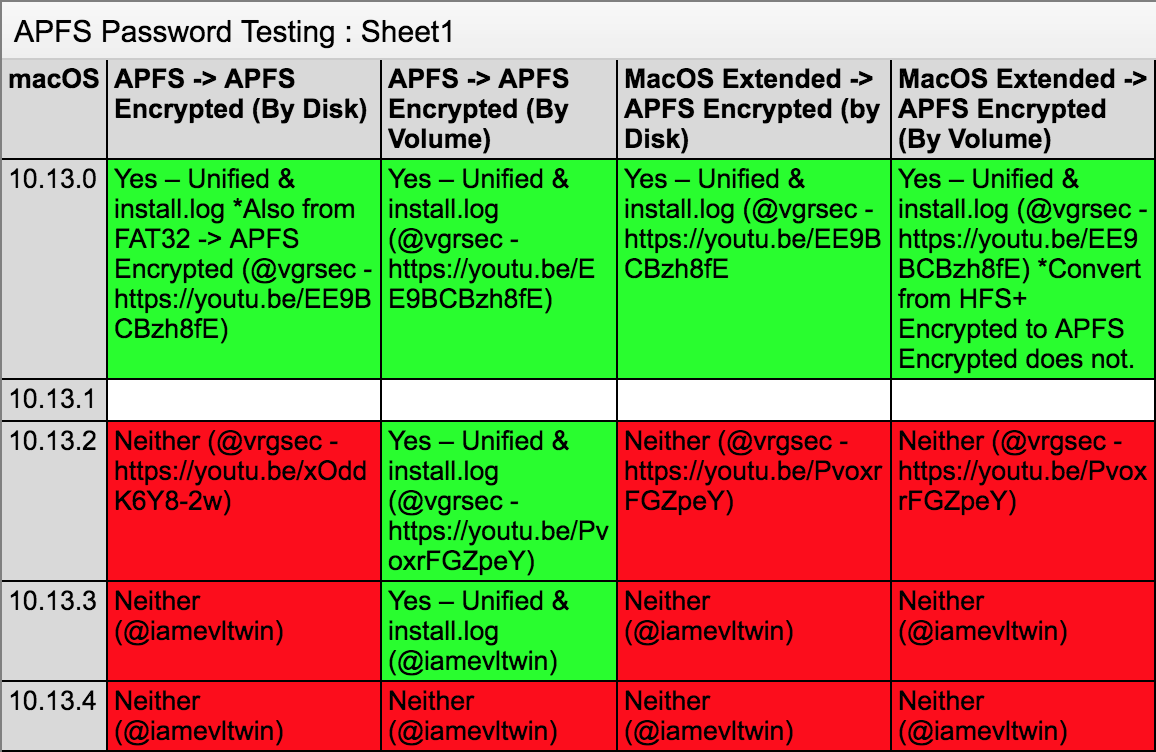
The bugs are fixed as of macOS 10.13.4. Credit: Sarah Edwards.
Thankfully, Apple seems to have resolved all of the known issues as of macOS High Sierra version 10.13.4, which was released at the end of March.
However, existing log files (or backups of those logs) could potentially still contain unencrypted APFS volume passwords. If you created any encrypted APFS volumes with a version of macOS High Sierra before 10.3.4, be sure to read Edwards’ articles to find out whether your Mac might be storing those passwords in plain text. Also check out Intego’s previous coverage:
macOS 10.13 High Sierra Stores APFS Encrypted Disk Passwords in Plaintext
You might recall that another security blunder related to APFS passwords was disclosed in September 2017, just two days after the first version of macOS High Sierra was released to the public.
iOS 11 Contains Unpatched QR Code Vulnerability

This QR code appears to go to facebook.com, but actually goes to Mueller’s site, infosec.rm-it.de
After waiting a reasonable 90 days for Apple to issue a patch, security researcher Roman Mueller publicly disclosed a vulnerability in the QR code reader functionality built into iOS 11’s Camera app.
Mueller found that by using a specially crafted URL, it’s possible to get iOS 11 to tell a user that it will go to an innocuous domain, for example apple.com, while actually redirecting the user to an entirely different domain—potentially a phishing page or other malicious site.
Below is an example video showing the vulnerability in action; the Camera app tells the user that the QR code leads to irs.gov, but it actually rickrolls the user instead.
Having way too much fun with @faker_‘s iOS 11 QR code vulnerability. ?#Apple #iOS #iOS11 #QRcode #vulnerability pic.twitter.com/sGDJq7bS0q
— the JoshMeister (@theJoshMeister) April 14, 2018
As of iOS 11.3, Apple still has not fixed the vulnerability. A commenter on Mueller’s blog says that the bug has been fixed in the first beta of iOS 11.4, however. Until Apple patches the flaw for the general public, it’s probably best to avoid scanning QR codes with iOS 11’s built-in Camera app.
For more details, see our article iOS 11’s Camera App Has a QR Code Vulnerability.
Mac Pwned Again at Pwn2Own Contest
Each year at the CanSecWest security conference, the Pwn2Own competition is an opportunity for hackers to “pwn” (“own,” or compromise) various devices, including Macs.
Confirmed! @5aelo used a JIT optimization bug in the browser, a macOS logic bug, & a kernel overwrite to execute code to successfully exploit Apple Safari. This chain earned him $65K & 6 points Master of Pwn points. pic.twitter.com/iLfNFnXzzs
— Zero Day Initiative (@thezdi) March 15, 2018
For the second year in a row, Samuel Groß (@5aelo) successfully compromised a Mac, once again following up the hack with his trademark Touch Bar alert message boasting of his pwnage.
Success! Samuel Groß (@5aelo) manages to pop calc and brings back his trademark touchbar finesse. Now off to the disclosure room for confirmation and vendor notification. pic.twitter.com/REQh1kHBjB
— Zero Day Initiative (@thezdi) March 14, 2018
As required by the contest, Groß responsibly disclosed the vulnerabilities that he used, and in late March, Apple mitigated the vulnerabilities for not only macOS but also for iOS, tvOS, and watchOS.
Apple Releases OS and Other Security Updates
 At the end of March, Apple released new versions of all of its major operating systems, each of which included security fixes: iOS 11.3 and tvOS 11.3, watchOS 4.3, and macOS 10.13.4.
At the end of March, Apple released new versions of all of its major operating systems, each of which included security fixes: iOS 11.3 and tvOS 11.3, watchOS 4.3, and macOS 10.13.4.
The Mac and iOS updates include a new Data & Privacy icon that will be found in places where Apple asks to use your personal information. We discussed this feature in episode 26 of the Intego Mac Podcast.
Apple’s new Data & Privacy icon, as seen in iOS 11.3. Image: Apple
In addition to operating system updates, Apple also patched security flaws in some of its other software. Vulnerabilities were mitigated in Safari 11.1 and Xcode 9.3 for Mac, and iTunes 12.7.4 for Windows and iCloud for Windows 7.4.
You can read the geeky details about the security updates at the official Apple security updates page, or read Intego’s more palatable summary:
Apple Issues New Security Updates, Patches APFS Volume Password Bug
Other Security News, in Brief
There were other notable goings-on in the security world in March. Some highlights:
 Four episodes of the Intego Mac Podcast were published in March. Be sure to subscribe to make sure you don’t miss any future episodes! The month’s topics included:
Four episodes of the Intego Mac Podcast were published in March. Be sure to subscribe to make sure you don’t miss any future episodes! The month’s topics included:
- GrayKey, a portable physical device, is a new method for law enforcement to unlock any iPhone, according to a Forbes report, and Mac security researcher Thomas Reed subsequently shared pictures of GrayKey in action; this news came on the heels of reports in February that Cellebrite could allegedly unlock any iPhone that was sent to them by law enforcement.
 Facebook created a special page in its Help Center to clarify for users whether their personal data was exposed after facing criticism for Cambridge Analytica obtaining data on millions of its users; see also Intego’s recent article about Facebook privacy settings, and listen to episode 26 of the Intego Mac Podcast in which we discuss this topic.
Facebook created a special page in its Help Center to clarify for users whether their personal data was exposed after facing criticism for Cambridge Analytica obtaining data on millions of its users; see also Intego’s recent article about Facebook privacy settings, and listen to episode 26 of the Intego Mac Podcast in which we discuss this topic.- A data breach at Orbitz (a popular travel site, now owned by Expedia) reportedly exposed 800,000 customers’ personally identifiable information and credit card numbers.
- A data breach at MyFitnessPal (a fitness iOS app by Under Armour) exposed 150 million users’ usernames, e-mail addresses, and hashed passwords; if you’ve used this app, be sure to change your password.
 The U.S. Department of Justice charged nine Iranian citizens—who were allegedly working on behalf of the government of Iran—with illegally hacking into and stealing scientific resources from “U.S. and foreign universities, private companies, and U.S. government entities.”
The U.S. Department of Justice charged nine Iranian citizens—who were allegedly working on behalf of the government of Iran—with illegally hacking into and stealing scientific resources from “U.S. and foreign universities, private companies, and U.S. government entities.”- Also, ITSPmagazine featured an article from Intego President Steve Kelly about the myth that Macs are more secure than PCs — check it out and share your thoughts!
Stay Tuned! Subscribe to The Mac Security Blog
 We’ll soon be covering RSA Conference, which runs from April 16–20 in San Francisco.
We’ll soon be covering RSA Conference, which runs from April 16–20 in San Francisco.
Subscribe to The Mac Security Blog for our coverage of the event, and to stay informed about Apple security throughout each month.
Also, each week we discuss Mac and iOS security news and other topics of interest on the Intego Mac Podcast. You’ll want to subscribe in iTunes/Podcasts to make sure you don’t miss any shows! Show notes are available at podcast.intego.com.
Last but not least, be sure to subscribe to the Intego YouTube channel to get informative video updates, and click on YouTube’s bell icon (?) so you’ll get notified when each new episode is available.