macOS 10.13 High Sierra Stores APFS Encrypted Disk Passwords in Plaintext
Posted on
by
Jay Vrijenhoek
Uh oh! macOS and iOS forensic analyst, Sarah Edwards, recently reported on a bug in macOS X 10.13 High Sierra that stores passwords to encrypted external APFS volumes in plaintext. These passwords are stored in system log files and can easily be retrieved with a simple terminal command.
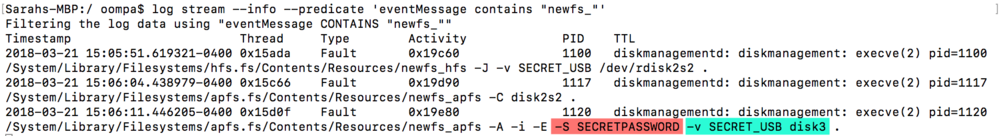
Image credit: Sarah Edwards at mac4n6.com
Apple always publishes security notes after system updates are released, which we inform our readers of on The Mac Security Blog, but Apple’s notes typically do not list every issue. In the case of this bug, Apple addressed it in High Sierra version 10.13.1, but made no mention of it in their security release notes. This bug was likely a result of other APFS encryption related bugs (or at least somehow related to it), so perhaps Apple felt it didn’t need to provide the additional details.
If this specific bug fix was not mentioned by Apple, it surfaces an important question: What other bugs and vulnerabilities may have been addressed by Apple in the past that we’re not aware of? This goes to show it’s always a good idea to install the latest updates as soon as possible, because they may very well include fixes to bugs and vulnerabilities that Apple does not tell you about.
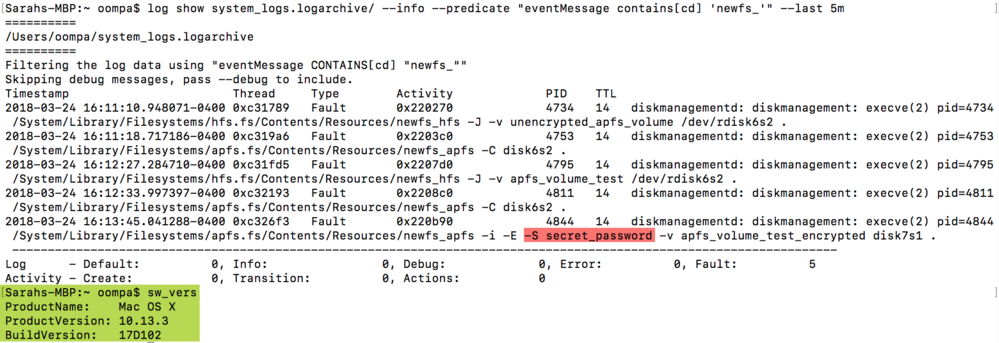
Now, of course, I would not be writing about this if there wasn’t a catch. With the help of other Twitter users, Sarah Edwards found that the bug is still present in the current version of High Sierra 10.13.3! While partially patched in earlier versions of High Sierra, if an existing APFS volume is encrypted in 10.13.3, the password will be stored in plaintext in the logs. Existing APFS volumes may be vulnerable, because of the earlier mentioned bug that showed a password in the password hint window.
Apple’s fix was to erase the encrypted volume and recreate it. If an APFS volume was created back then, and a 10.13.3 user decides to encrypt it now, the new bug will rear its head and store the password in plaintext. Newly created APFS volumes can be encrypted without the password showing in the logs.
Why is this a big deal? Well, passwords stored in plaintext can be discovered by anyone with unauthorized access to your machine, and malware can collect log files as well and send them off to someone with malicious intent. If you’ve ever had a support call with Apple, you may have been walked through installing an information collection app; this app is used to scrape all sorts of data from your Mac, and it sends it to Apple for analysis so they can help you resolve your issue. Log files are included, so now your plaintext password was sent to Apple.
Now that the news is out, Apple will probably address this soon, but until then here is what you can do to protect your encrypted volumes:
- If you are still using macOS 10.13(.0), update to 10.13.3 right away. There have been a LOT of security related issues that were addressed in the .1, .2 and .3 updates, as well as several supplemental updates. Back up your data and use the Updates tab in the App Store app to get your system up to date.
- If you have APFS encrypted volumes that were created in 10.13 prior to the release of the supplemental update in October 2017, they must be erased and recreated. Sarah Edwards reported on external volumes only, so it is currently not known if this bug affects internal volumes as well. This is, of course, a tedious task, especially if you have a 4 TB encrypted external drive that is nearly full. However, to prevent this bug from manifesting on your system, that volume must be backed up, erased, recreated and restored.
Computers have been dealing with bugs and vulnerabilities for a very long time, and this won’t change any time soon. When using computers that run systems and applications designed by humans, coding issues are simply an inescapable fact of life. To err is human, as they say.
Security researchers and analysts will continue to find these bugs and bring them to light, and then it’s Apple’s job to fix them. Our ‘job’ as end users is to install these security updates as soon as they are released, so that our systems and data are as safe as can be — a dance that will go on for many years to come and a routine everyone is essentially forced to do (or your IT staff) if you want a secure system.
Ahhh, computers, aren’t they fun?! 🙂