Intego discovers fake Arc browser with unique AppleScript malware component
Posted on
by
Joshua Long

In recent months, we’ve written numerous articles about stealer malware that infects Macs—most recently Cuckoo, an Atomic Stealer (AMOS) variant that mimicked the popular Homebrew software.
A couple weeks ago, reports surfaced of a Trojanized version of the Windows version of Arc, a hot new Chromium-based browser from The Browser Company of New York. As with many similar campaigns, that Trojan horse spread through malvertising—malicious Google Ads in the top “Sponsored” slot in Google search results, that looked like genuine ads for Arc.
Intego immediately began hunting for a Mac version of this malware. And sure enough, we found one.
Here’s everything you need to know about the Trojanized Arc variant of the AMOS malware, and how to stay protected from similar threats.
In this article:
- Intego discovers Arc browser Trojan horse
- Don’t “just Google it”
- How can I keep my Mac safe from similar malware?
- Indicators of compromise (IOCs)
- Do security vendors detect this by any other names?
- How can I learn more?
Intego discovers Arc browser Trojan horse
Our research team discovered that threat actors were indeed distributing a Mac version of a Trojan horse masquerading as the Arc browser.
We came across Arc-1-26-45415.dmg, which contained a Mach-O binary compiled to run on both Intel- and Apple silicon-based Macs.
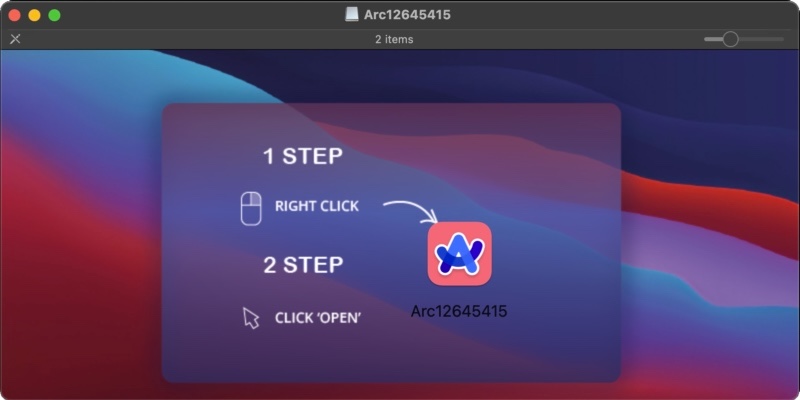
In this case, the threat actor got lazy and reused a common Trojan disk image background, a generic disk image name, and “right click” instructions. But, ironically, they took the time to make a customized, color-swapped version of the Arc browser logo, rather than simply copy-pasting the actual logo from a real copy of the Arc app.
As expected, this is yet another Atomic macOS Stealer (aka AtomicStealer or AMOS) sample. That means it has the usual infostealer functionality: gathering wallets, passwords, and other sensitive data, and exfiltrating them to the malware maker.
But interestingly, this sample uses an AppleScript payload to execute those functions. Very similar AppleScript code was used in another campaign recently, in which threat actors mimicked a Mac cleaner app.
By comparing the AppleScript code from both samples, we determined that the Arc Trojan’s AppleScript was actually an earlier version of the script seen in the cleaner app Trojan campaign.
Don’t “just Google it”
It’s very likely that the team behind this campaign distributed this Trojan via the same, or a similar, Google Ads poisoning campaign site as the one that distributed the Windows version of the Arc-lookalike Trojan. Threat actors often pay Google for top placement, with sponsored ads disguised as real ads for legitimate software. These ads appear immediately above the actual search results; if you aren’t careful, you could inadvertently visit a malware distribution site instead of landing on the real software developer’s site.
We recommend that everyone get out of the habit of “just Google it” to find legitimate sites. Such habits often include clicking on the first link without giving it much thought, under the assumption that Google won’t lead them astray, and will give them the correct result right at the top. Malware makers know this, of course, and that’s why they’re paying Google for the number-one position.
Until or unless Google does a much better job of vetting its ads, a better practice than “Google it” would be to bookmark trusted sites whenever possible, and to go back to those bookmarks in the future.
How can I keep my Mac safe from similar malware?
If you use Intego VirusBarrier, you’re already protected from this malware. Intego detects these samples as OSX/Amos.ext, OSX/Amos.scpt, and similar names.
 Intego VirusBarrier X9, included with Intego’s Mac Premium Bundle X9, is a powerful solution designed to protect against, detect, and eliminate Mac malware.
Intego VirusBarrier X9, included with Intego’s Mac Premium Bundle X9, is a powerful solution designed to protect against, detect, and eliminate Mac malware.
If you believe your Mac may be infected, or to prevent future infections, it’s best to use antivirus software from a trusted Mac developer. VirusBarrier is award-winning antivirus software, designed by Mac security experts, that includes real-time protection. It runs natively on both Intel- and Apple silicon-based Macs, and it’s compatible with Apple’s current Mac operating system, macOS Sonoma.
One of VirusBarrier’s unique features is that it can scan for malicious files on an iPhone, iPad, or iPod touch in user-accessible areas of the device. To get started, just attach your iOS or iPadOS device to your Mac via a USB cable and open VirusBarrier.
If you use a Windows PC, Intego Antivirus for Windows can keep your computer protected from malware.
Indicators of compromise (IOCs)
Following are SHA-256 hashes of malware samples from the Arc-wannabe AMOS malware campaign (the DMG, Mach-O, and AppleScript), as well as the aforementioned later variant of the AppleScript:
b949aa5270a5fb8278bf8134eccad0df8a2f510e7f84c7e9912169b22acd6fcb 0a76cf7149595c847c6d0c5cb5a662e5f82b97103ce010c4a19e73e55e257ce0 b18e247cccee3bdee2f707c647910b06eeacfef5e75e16fbb0b32d1ff37ce385 22f4150660e7e012059a9d6a6a5fcf755a8006fbd4c4702df32518ca56fde94d
The following IP address was used as the data exfiltration target for this campaign (and has been used in previous AMOS campaigns):
79.137.192[.]4
The following domains and IP address were previously identified as having been used in conjunction with the Windows version of the fake-Arc Trojan campaign:
ailrc[.]net aircl[.]net 185.156.72[.]56
Network administrators can check logs to try to identify whether any computers may have attempted to contact one of these domains or IPs in recent weeks, which could indicate a possible infection.
Do security vendors detect this by any other names?
Other antivirus vendors’ names for this malware may include variations of the following:
A Variant Of OSX/PSW.Agent.AV, ABRisk.CWKB-0, Generic.MAC.Stealer.I.1FC5F911 (B), Generic.MAC.Stealer.I.33ECED2C (B), HEUR:Trojan-PSW.OSX.Amos.p, HEUR:Trojan-PSW.OSX.Amos.v, Mac.Stealer.38, MAC/Agent.AV!tr.pws, MacOS:Agent-AKV [Trj], MacOS:AMOS-E [Trj], MacOS/Agent.BG.gen!Camelot, MacOS/Agent5.CT, Malware.OSX/AVA.Agent.dggdh, Malware.OSX/GM.Agent.LY, Malware.VBS/avi.AMOS.22f415, Osx.Trojan-QQPass.QQRob.Zchl, OSX.Trojan.Gen, OSX/GM.Agent.LY, OSX/PSW.Agent.BH, OSX/PWS-CNS, RiskWare:MacOS/Agent.BJ, Trojan ( 0040f4861 ), Trojan:MacOS/Multiverze, Trojan.Generic.35674866 (B), Trojan.Generic.D2205AF2, Trojan.MacOS.AVI.VSNW02F24, Trojan.OSX.Amos.i!c, Trojan.OSX.Psw, Trojan.Script.Stealer.i!c, UDS:Trojan-PSW.OSX.Amos.p, Unix.Malware.Macos-10027865-0, VBS/avi.AMOS.22f415
How can I learn more?
Be sure to check out our previous Mac malware articles from 2024 and earlier. And, if you’d like, you can read Jérôme Segura’s write-up about the Windows variant of the Arc Trojan for more details about that particular campaign.
 Each week on the Intego Mac Podcast, Intego’s Mac security experts discuss the latest Apple news, including security and privacy stories, and offer practical advice on getting the most out of your Apple devices. Be sure to follow the podcast to make sure you don’t miss any episodes.
Each week on the Intego Mac Podcast, Intego’s Mac security experts discuss the latest Apple news, including security and privacy stories, and offer practical advice on getting the most out of your Apple devices. Be sure to follow the podcast to make sure you don’t miss any episodes.
You can also subscribe to our e-mail newsletter and keep an eye here on The Mac Security Blog for the latest Apple security and privacy news. And don’t forget to follow Intego on your favorite social media channels: ![]()
![]()
![]()
![]()
![]()
![]()
![]()