Denial of Service Attack Targets Mac and iOS Users
Posted on
by
Jay Vrijenhoek
This week, 9to5Mac reported on a tech support scam that caused a Denial of Service (DoS) attack on a Mac. While this DoS was described as an attack caused by malware, it appears to be a malicious script loaded by a web browser instead, in this case Safari.
This DoS attack is not malware in the traditional sense, because nothing is actually installed on the affected system. What is happening is that links to malicious site(s) that run this script are sent via email from email addresses [email protected] and [email protected]. These email addresses are also recorded as registration info for the malicious domains. It is currently unknown if the emails contain a simple text link or an application that may change the browser’s home page to the malicious site.
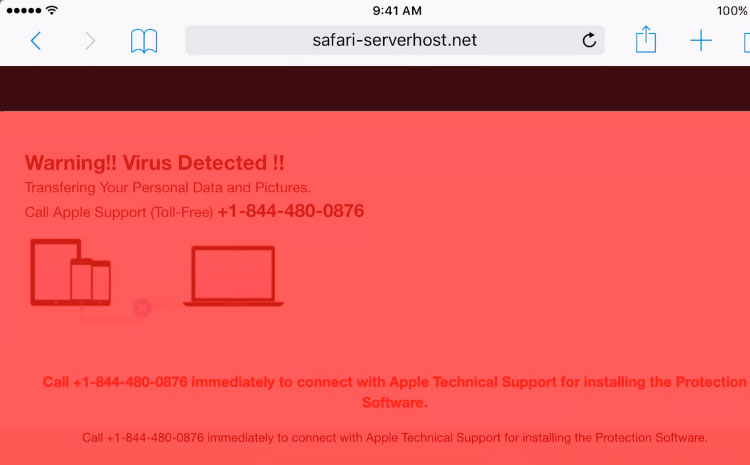
Some of the websites that trigger the DoS are safari-get[.]com, safari-get[.]net, safari-serverhost[.]com and safari-serverhost[.]net. At the time of writing, all but the last domain are inactive. There could, of course, be many other websites yet discovered that trigger the same behavior.
With one of the known sites still active, Intego was able to test the reported behavior, which we will detail below.
Observed Behavior
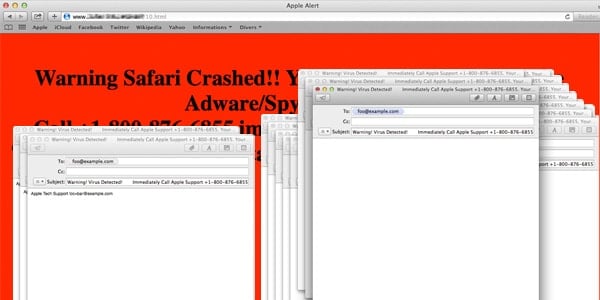
The malicious site loads a script that opens the Mail application and drafts a new email with the subject “Warning! Virus Detected! Immediately Call Apple Support,” and a phone number that is most definitely not Apple’s (it is known to be associated with similar scams). It doesn’t just draft one of those emails, it drafts hundreds until your Mac runs out of memory and locks up.
Attempts to quick or force quick Mail will not work, instead, doing so causes the browser script to open Mail again and begin drafting fresh emails. The browser must be closed first to stop the script, and then Mail can be closed. However, since Safari remembers the last page that was open when it was quit, the next time Safari is launched the fun starts all over again. Even if the Mail application is not configured, it keeps opening and asks to add an account.
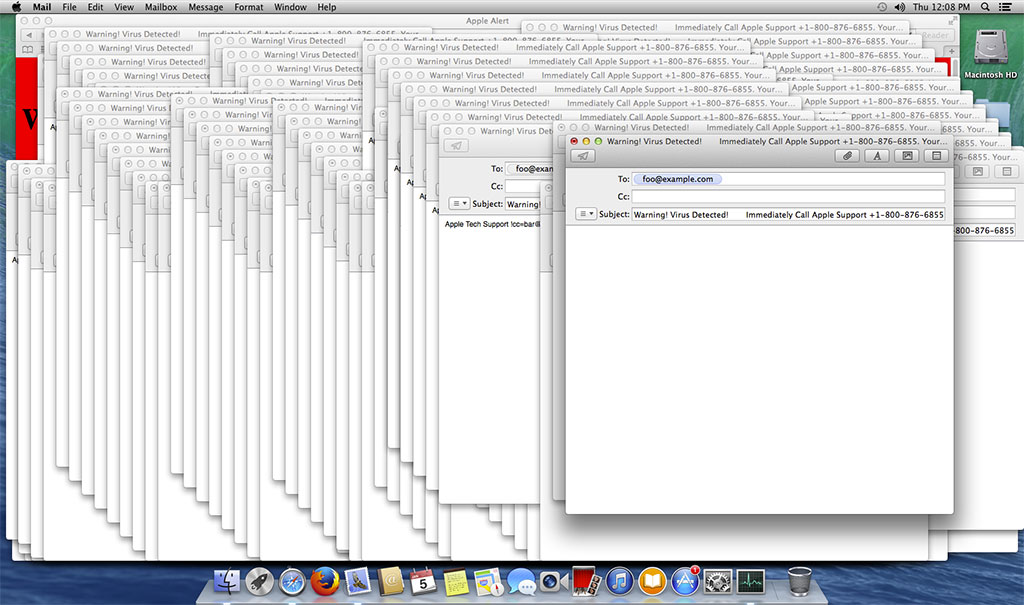
The behavior mentioned above was tested on OS X 10.9, 10.10, 10.11 and 10.12, and was observed on all of them. Only macOS 10.12.1 and up (safari 10.0.1 and newer) appear to protect against this attack with Safari recognizing the attempts and warning the user.
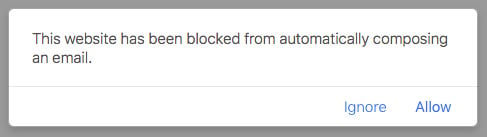
On the affected systems, Safari is the most vulnerable to this attack. Google Chrome loads the script and launches Mail, but once Mail is quit, Chrome does not re-open it. Chrome itself does freeze, though. Firefox briefly stalls when loading the website, and then offers to stop the malicious script.
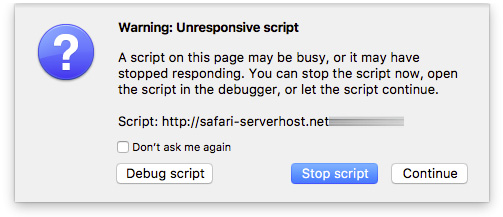
For Mac users who are not running macOS 10.12.1 or newer, the use of Firefox is highly recommended as it is constantly updated even for older OS X versions, and it appears to protect from at least this particular attack. Upgrading to the latest macOS version is of course preferred.
The page checks for a specific version of the operating system and loads a script accordingly. In our testing, on several versions of OS X, only the script that opened Mail was loaded—but when Malwarebytes investigated, they found another script that opened iTunes instead of Mail. We triggered this script by manually tweaking the web address. A different style webpage loads and iTunes is opened, which, in our testing on different OS X versions, crashed immediately.
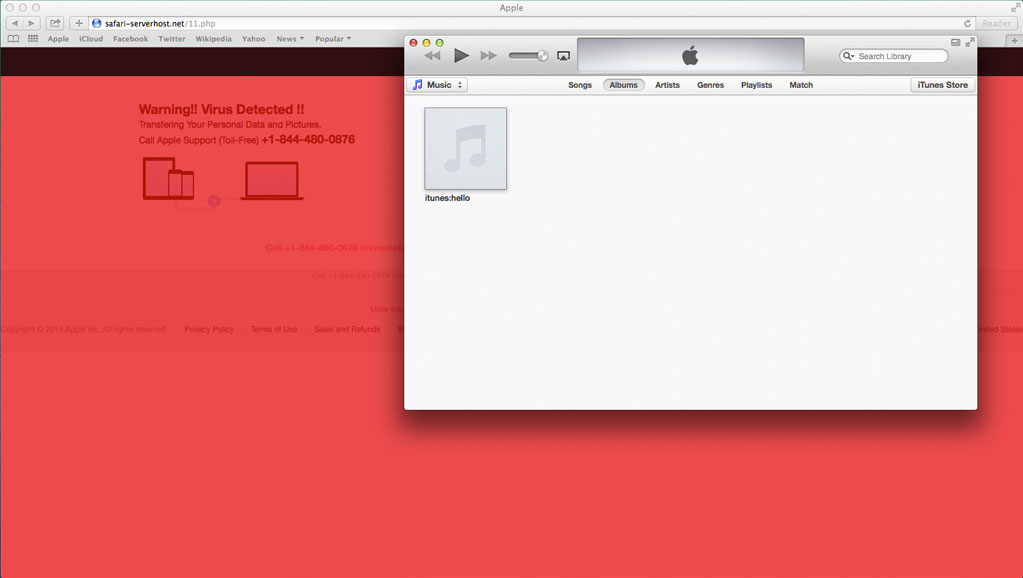
Mitigation on a Mac
If this DoS attack has already hit you and you are currently looking at a locked up Mac, or are unable to open Safari without it hijacking your Mail again, there are some steps you can take to clear this up.
- Force quit Safari first, then force quit Mail
If possible, force quit the applications in that order. Quitting Mail first will simply cause Safari to open it again. - Restart your Mac
Your Mac is either very slow, as Mail used up most of its memory, or it’s frozen completely. A restart will free the memory and give you a smooth running Mac to work with. If the Mac is frozen, holding down the power button until it shuts off is your only option. If your Mac automatically starts Safari or you have it set to remember which applications were open before the restart, you may immediately be thrown back into the same behavior.
At this point your Mac still has enough free memory to function, so immediately pull up the Force Quit window by pressing the following keys:
'Option-Command-Escape'
Then select Safari and force quit it, followed by Mail. - Reset Safari
The malicious site has to be cleared from Safari, but this can’t be done from inside Safari. Luckily, this can be easily done without losing your bookmarks or saved passwords. You’ll need to locate the folder that saves the last state Safari was in when it quit. This can be found in your user home folder > Library > Saved Application State. In that folder, delete the folder named “com.apple.Safari.savedState.” You can now start Safari and it should open with your default home page. The malicious link will be saved in Safari’s history, so make sure to erase it there as well. - Clear Mail
There’s a good chance that Mail was kind enough to save all those drafts for you, and they will pop up again when you start the app. To clear all those drafts out you’ll have to manually delete them from your hard drive. (This is also a good time to make sure your backup is current!) Go to your user home folder > Library > Mail > V2 (V3 or V4 depending on your version of OS X). In that folder you will see several folders that are named after your email accounts, starting with “IMAP” or “POP.” Check each of those folders to see if they contain a “Drafts.mbox” folder. Open the drafts folder and inside will be another folder with a long name, such as “A1344DBE-5B24-4398-8320-E78F80208689,” or something similar. Inside that folder is Data > Messages.
The messages are numbered, so using QuickLook (don’t double-click them as this will open the Mail app) you’ll have to check them all to see if it’s one of the virus warning drafts or a draft you had saved yourself. If you’re lucky, there are a few dozen or less. If you’re not so lucky, there may be hundreds. Of course, if you know there were no drafts you saved, you can just clear out the entire “Messages” folder and empty the Trash. Ironically, the drafts are still there, they just no longer have a sender, subject or content. To prevent the actual draft windows from opening, there is one more file that needs to be deleted. This can be found in the same V2 (V3 or V4) folder > MailData. Delete the file named “Envelope Index.”
Now when you start Mail, you’ll be greeted with a “Mail Message Import” window. Scary as it sounds, all your email is still there, Mail just has no idea because you’ve just deleted the index file. Mail will import all the mail, rebuild the index file and you are back in business.
Mitigation on iOS
On iOS 8, 9 and the current 10, loading the malicious website also results in a new Mail message being drafted—but only one draft is created.
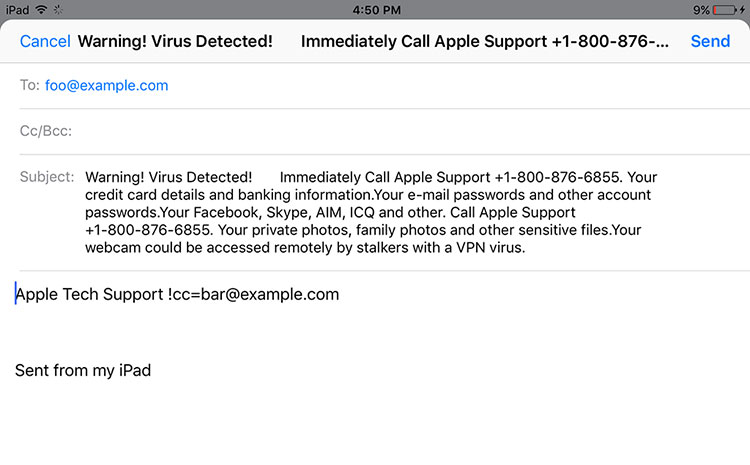
This single draft can be cancelled and deleted, but a new one will pop up straight away. Therefore, you will need to clear Safari history and website data. To clear Safari on the iOS device, it has to be reset, which can be done by going to Settings > Safari > Clear History and Website Data.
Loading the script that calls iTunes on the Mac has no effect on iOS, instead it just shows the webpage without opening any other app.
While not malware in the traditional sense, this DoS shows there are multiple ways to attack a Mac or iOS user. In this case, not a lot of effort was put into the scripting that triggered Mail or iTunes. The authors could have made the emails actually send to various different addresses, acting as a spammer on their behalf, for example. Still there are many, many users who may actually contact the phone number presented on their screen and pay the scammers for “support.” This makes these scams so successful they are likely not going anywhere anytime soon.
Be vigilant when you receive email from someone you don’t know, especially when an email contains links or buttons. On the Mac, hover your cursor over the link to see what site it will really send you to. On iOS devices, just press and hold on a link to see a pop-up with the real URL in it. And remember: If you don’t trust it, delete it.