Apple’s Quick Look reveals your darkest secrets
Posted on
by
Joshua Long
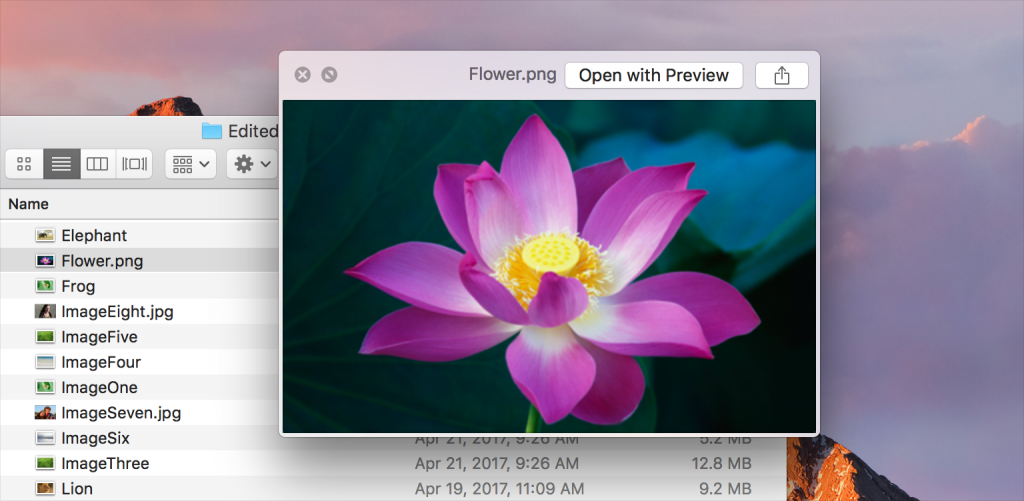
Quick Look in the macOS Finder. Image: Apple
For more than a decade, macOS has included a feature called Quick Look that makes it easy to preview files right within the Finder, without having to launch an app.
While Quick Look can certainly be a useful feature, its implementation in macOS has some surprising and potentially disturbing privacy implications.
Let’s take a look at why the feature may be problematic and what you can do to safeguard your private data.
What Exactly Is Quick Look?
Introduced in Mac OS X 10.5 Leopard, Quick Look displays file previews right within the Finder for a variety of common file types, including but not limited to photographs and other images, plain text and rich text files, PDFs, Microsoft Office documents, Web pages, and documents in Apple’s Pages, Keynote, and Numbers formats.

Clicking on a file in the Finder and pressing space bar invokes Quick Look. Image: Pixabay
When a user clicks on a file and presses the space bar on the keyboard, a preview image is generated and displayed in the Finder. To avoid having to generate the same preview again every time Quick Look is invoked for that file, macOS caches the preview image to the Mac’s internal hard drive.
Even without manually invoking the feature via the space bar, Quick Look may nevertheless generate and cache small previews automatically. Simply opening a folder in the Finder will generate previews of sufficient quality as to reveal the files’ contents.
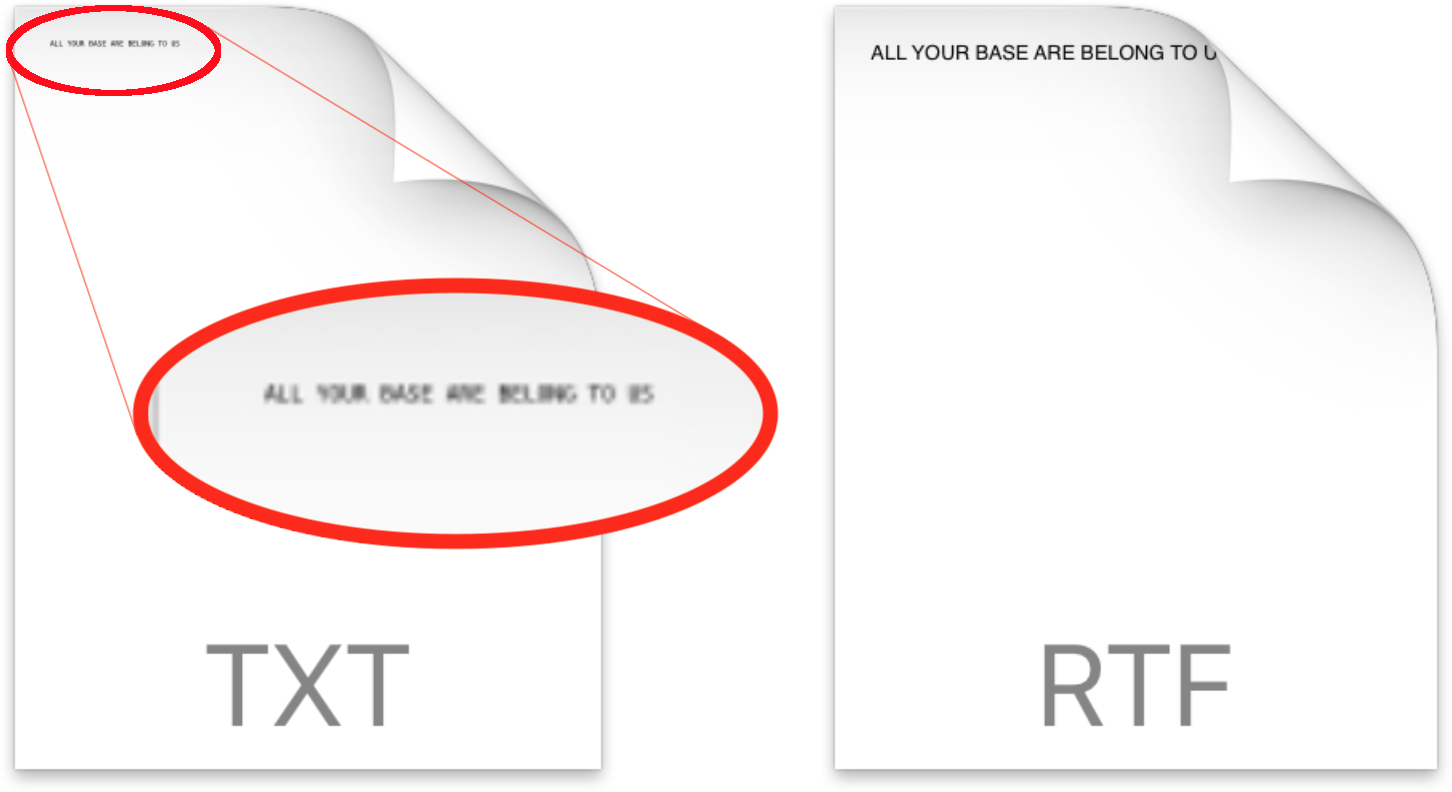
Viewing a folder can generate preview images clear enough to reveal file contents. Image: Wardle
What’s the Privacy Concern?
 While the Quick Look feature is very convenient and not necessarily a concern for most Mac users, highly privacy conscious users may be dismayed to learn that Quick Look doesn’t properly respect users’ implicit desires for privacy, as detailed in a technical article by Wojciech Reguła and Patrick Wardle.
While the Quick Look feature is very convenient and not necessarily a concern for most Mac users, highly privacy conscious users may be dismayed to learn that Quick Look doesn’t properly respect users’ implicit desires for privacy, as detailed in a technical article by Wojciech Reguła and Patrick Wardle.
The main issue is that external drives and drives that are no longer mounted—including fully encrypted disks—are cached to the Mac’s internal hard drive.
If you’ve taken the time to fully encrypt an external hard drive, or if you’ve gone to the trouble of creating an encrypted disk image to keep sensitive files private, you’ve made a clear and unmistakable choice to safeguard the files contained within that volume and keep them away from prying eyes.
Unfortunately, so far Apple has not chosen to respect your implicit desire for privacy when it comes to Quick Look caching.
Whenever you have a drive or disk image mounted on your Mac, even if that disk is encrypted or password-protected, macOS will treat it like any other disk and may cache Quick Look previews of your sensitive files.
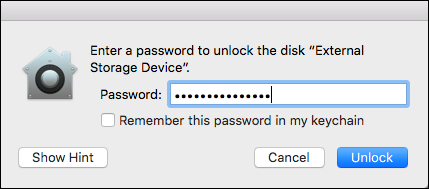
Even password-protected disks’ files may be cached by Quick Look. Image: USC
This means that anyone who later gains access to the contents of your Mac’s internal drive—even when that external drive is no longer connected—may be able to see previews of all your private files.
So What? Doesn’t FileVault Protect Me?
 You may wonder why this matters given that every version of macOS since Yosemite has offered to encrypt the Mac’s internal hard drive by default when you do a clean install. Shouldn’t that mean that Quick Look previews should be secure?
You may wonder why this matters given that every version of macOS since Yosemite has offered to encrypt the Mac’s internal hard drive by default when you do a clean install. Shouldn’t that mean that Quick Look previews should be secure?
It’s important to be aware that your internal hard drive may not necessarily be encrypted; there are a number of scenarios in which your Mac’s drive might never have had whole-disk encryption enabled.
The easiest way to tell if your Mac’s internal drive is encrypted is to open Disk Utility (you can find it by looking in the Utilities folder inside the Applications folder, or by doing a Spotlight search for it by name). When you open Disk Utility, your Mac’s internal boot volume will already be selected. If the disk is encrypted, you’ll see either “APFS (Encrypted)” or “Mac OS Extended (Journaled, Encrypted)” displayed beneath your drive’s name.
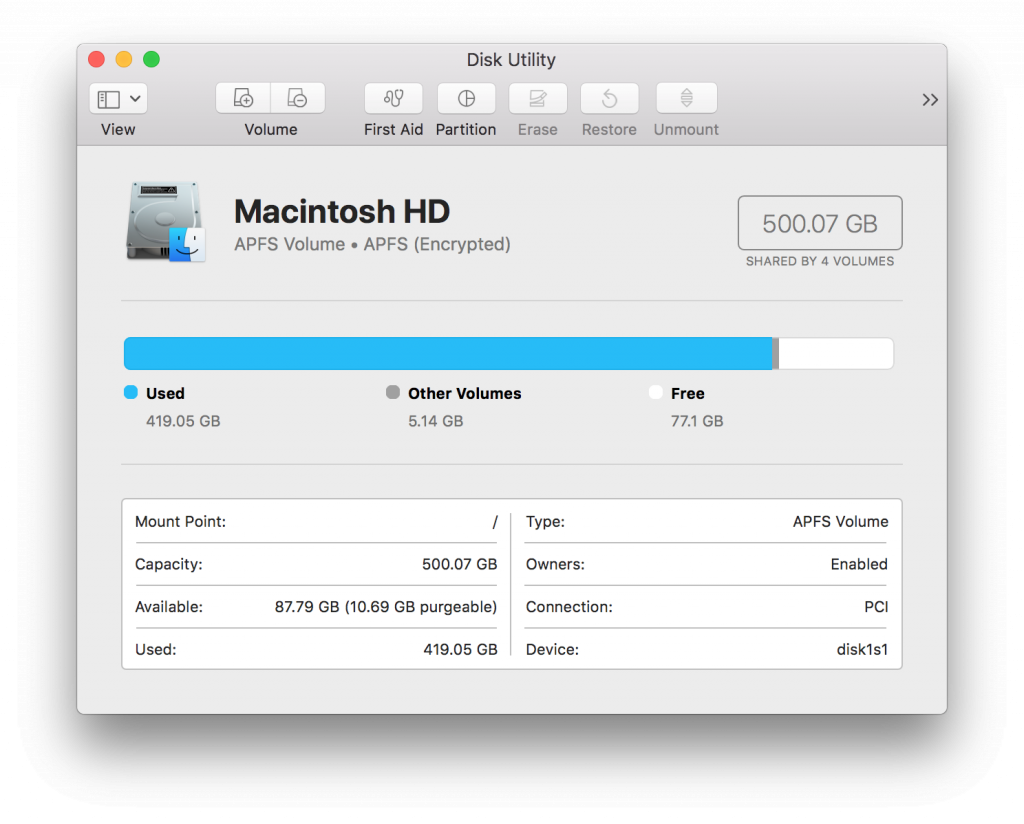
But even if your internal drive is encrypted, you shouldn’t assume that your Quick Look cache or any other files will always remain private.
If you ever leave your Mac unlocked and unattended for a while, someone could walk up to your computer and get full access to your documents.
 Or if your Mac becomes infected with a RAT, an attacker may be able to access your files remotely, regardless of whether your drive is encrypted.
Or if your Mac becomes infected with a RAT, an attacker may be able to access your files remotely, regardless of whether your drive is encrypted.
Full-disk encryption only prevents access to a drive’s contents when it isn’t mounted. When the drive is mounted, it’s just as accessible to spies as an unencrypted drive.
How To Disable Quick Look Caching
If you’re wondering whether there’s a way to prevent Quick Look from caching previews of all your files, the answer is yes—you’re in luck!
You can copy and paste the following commands into the Terminal app (which you can find in the Utilities folder or via Spotlight) to disable Quick Look caching and delete the database:
qlmanage -r disablecache
qlmanage -r cache
rm -rf $TMPDIR/../C/com.apple.QuickLook.thumbnailcache
You may wish to restart your Mac after running these commands.
Where Can I Learn More?
For more technical details about Quick Look’s caching issue, you can check out Reguła and Wardle’s article.
We also discussed the Quick Look problem on episode 40 of the Intego Mac Podcast. Be sure to subscribe to the Intego Mac Podcast, the Intego YouTube channel, and The Mac Security Blog to stay informed about the latest Apple security news.