Apple + Recommended + Security & Privacy
Take that FBI! OS X Yosemite Encrypts Disks by Default, Better Protecting Privacy
Posted on
by
Graham Cluley

With the release of OS X Yosemite, Apple has blown a loud raspberry in the direction of law enforcement agencies and data thieves round the world.
The reason? The latest version of Apple’s operating system for desktops and laptops positively encourages users to turn on full disk encryption, in the shape of FileVault 2.
FileVault is nothing new. It has been around in its “FileVault 2” incarnation since OS X Lion. (Prior to that, FileVault was available in a form that didn’t encrypt the whole drive—and as such offered considerably weaker security.)
But what’s new in OS X Yosemite, is that more users are likely to enable FileVault than ever before—as at installation you have to consciously opt-out of having your hard drive encrypted, rather than opt-in.
As The Guardian reports, the fact that more people than ever before will be taking advantage of OS X’s powerful cryptographical technology is unlikely to go down well with those who may have an interest in deciphering our data. Last week, the FBI’s director, James Comey, decried the company’s decision to offer similar tools on mobile devices running iOS 8:
“With Apple’s new operating system, the information stored on many iPhones and other Apple devices will be encrypted by default,” Comey told the Brookings Institute in Washington DC. “Shortly after Apple’s announcement, Google announced plans to follow suit with its Android operating system. This means the companies themselves won’t be able to unlock phones, laptops, and tablets to reveal photos, documents, email, and recordings stored within.”
Of course, computers with encrypted hard drives make it not only harder for law enforcement agencies to unlock their secrets, it also makes life much tougher for data thieves, too.
FileVault encrypts your entire hard drive using XTS-AES 128, a secure encryption algorithm. The reason why you should strongly consider enabling the feature on your Macs and MacBooks is if your hard drive isn’t fully encrypted, anyone who manages to steal your computer can access any data upon it.
With FileVault, however, as soon as your Mac is shut down, its entire drive is encrypted and locked up. Only when an authorised user turns on and logs into the Mac are the drive’s contents unlocked. (Yet another reason why it’s a good idea not to have an obvious password.)
Although FileVault takes a while to initially encrypt your hard drive’s contents, you can continue working (and even turn off your computer if you want) during the process. It will just pick up where it left off at the next opportunity.
And when your system’s hard drive has been entirely encrypted, you shouldn’t even notice any difference in behaviour or performance (on a newer Mac at least). As far as you’re concerned, the computer acts as normal, your files are accessible as usual without any jiggerypokery, because FileVault 2 is doing all the crafty work invisibly and silently in the background.
Encryption that is so seamless it “just works?” That’s how it should be.
In my opinion, it’s a good thing that Apple is better protecting its customers by leaving FileVault enabled by default.
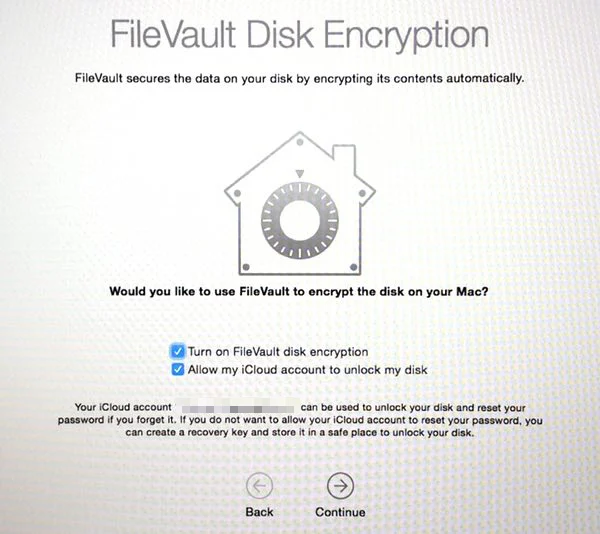
If you haven’t yet given FileVault a go, it’s easy to enable.
Make sure you have logged into OS X with an account that has admin privileges, and go to System Preferences > Security & Privacy > FileVault. Once there, press Turn on FileVault.
Further Reading:
- OS X Yosemite: Security and Privacy Features Overview
- Spotlight Search in OS X Yosemite Falls Foul of Another Privacy Glitch
- Spotlight Suggestions in OS X Yosemite and iOS: Are You Staying Private?