Apple’s OS X Mavericks 10.9.2 Update Fixes SSL Bug
Posted on
by
Derek Erwin
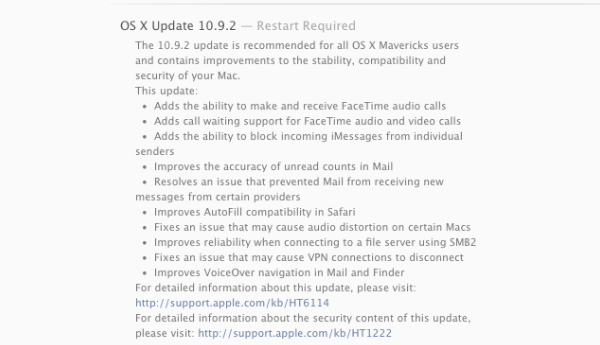
Apple has just released OS X Mavericks 10.9.2 with fixes for an SSL bug that was patched on iOS and Apple TV last week. Weighing in at 859.7 MB, the Mac OS X 10.9.2 update is fairly substantial – offering fixes and improvements across the board. Apple also released Security Update 2014-001, which addresses multiple OS X vulnerabilities, as is normal for major operating system updates.
These updates are available for: OS X Lion Server 10.7.5, Mac OS X 10.7.5, 10.8.5, 10.9 and 10.9.1.
Perhaps most importantly, Security Update 2014-001 fixes a serious SSL bug (CVE-2014-1266) that concerns data security. The SSL flaw allows an attacker to intercept and decrypt SSL/TLS communications, which is, as Larry Seltzer noted at ZDNet, “probably the most important security protocol there is today.”
Altogether, the OS X security update fixes multiple vulnerabilities in Apache, the most serious of which may lead to cross-site scripting, it patches issues that allow the App Sandbox to be bypassed, resolves a number of bugs related to arbitrary code execution, and addresses a problem that may lead to the disclosure of memory contents when viewing maliciously crafted JPEG files, among a slew of other bug fixes. Root certificates have been updated as well; the complete list of recognized system roots may be viewed via the Keychain Access application.
Apple provided the following descriptions of all vulnerabilities resolved in this update:
- CVE-2013-1862, CVE-2013-1896 : Multiple vulnerabilities existed in Apache, the most serious of which may lead to cross-site scripting. These issues were addressed by updating Apache to version 2.2.26.
- CVE-2013-5179 : The LaunchServices interface for launching an application allowed sandboxed apps to specify the list of arguments passed to the new process. A compromised sandboxed application could abuse this to bypass the sandbox. This issue was addressed by preventing sandboxed applications from specifying arguments. This issue does not affect systems running OS X Mavericks 10.9 or later.
- CVE-2014-1254 : A memory corruption issue existed in the handling of handling of Type 1 fonts. This issue was addressed through improved bounds checking.
- CVE-2014-1262 : A memory corruption issue existed in the handling of Mach messages passed to ATS. This issue was addressed through improved bounds checking.
- CVE-2014-1255 : An arbitrary free issue existed in the handling of Mach messages passed to ATS. This issue was addressed through additional validation of Mach messages.
- CVE-2014-1256 : A buffer overflow issue existed in the handling of Mach messages passed to ATS. This issue was addressed by additional bounds checking.
- CVE-2014-1257 : Resetting Safari did not always delete session cookies until Safari was closed. This issue was addressed through improved handling of session cookies. This issue does not affect systems running OS X Mavericks 10.9 or later.
- CVE-2014-1258 : A heap buffer overflow existed in CoreAnimation’s handling of images. This issue was addressed through improved bounds checking.
- CVE-2014-1261 : A signedness issue existed in CoreText in the handling of Unicode fonts. This issue is addressed through improved bounds checking.
- CVE-2014-1263 : When using curl to connect to an HTTPS URL containing an IP address, the IP address was not validated against the certificate. This issue does not affect systems prior to OS X Mavericks v10.9.
- CVE-2014-1266 : Secure Transport failed to validate the authenticity of the connection. This issue was addressed by restoring missing validation steps.
- CVE-2014-1265 : An unprivileged user may change the system clock. This update changes the behavior of the system setup command to require administrator privileges to change the system clock.
- CVE-2014-1259 : A buffer overflow existed in the handling of file names. This issue was addressed through improved bounds checking.
- CVE-2014-1264 : Accessing a file’s ACL via Finder may corrupt the ACLs on the file. This issue was addressed through improved handling of ACLs.
- CVE-2013-6629 : An uninitialized memory access issue existed in libjpeg’s handling of JPEG markers, resulting in the disclosure of memory contents. This issue was addressed by better JPEG handling.
- CVE-2013-5139 : An out of bounds array access existed in the IOSerialFamily driver. This issue was addressed through additional bounds checking. This issue does not affect systems running OS X Mavericks v10.9 or later.
- CVE-2013-5178 : An issue existed in the handling of certain unicode characters that could allow filenames to show incorrect extensions. The issue was addressed by filtering unsafe unicode characters from display in filenames. This issue does not affect systems running OS X Mavericks v10.9 or later.
- CVE-2013-5986, CVE-2013-5987 : An issue existed that allowed writes to some trusted memory on the graphics card. This issue was addressed by removing the ability of the host to write to that memory.
- CVE-2013-4073, CVE-2013-4113, CVE-2013-4248, CVE-2013-6420 : Multiple vulnerabilities existed in PHP, the most serious of which may have led to arbitrary code execution. These issues were addressed by updating PHP to version 5.4.22 on OS X Mavericks v10.9, and 5.3.28 on OS X Lion and Mountain Lion.
- CVE-2014-1260 : A memory corruption issue existed in QuickLook’s handling of Microsoft Office files. Downloading a maliciously crafted Microsoft Office file may have led to an unexpected application termination or arbitrary code execution. This issue does not affect systems running OS X Mavericks 10.9 or later.
- CVE-2014-1252 : A double free issue existed in QuickLook’s handling of Microsoft Word documents. This issue was addressed through improved memory management.
- CVE-2014-1246 : A buffer overflow existed in the handling of ‘ftab’ atoms. This issue was addressed through improved bounds checking.
- CVE-2014-1247 : A memory corruption issue existed in the handling of ‘dref’ atoms. This issue was addressed through improved bounds checking.
- CVE-2014-1248 : A buffer overflow existed in the handling of ‘ldat’ atoms. This issue was addressed through improved bounds checking.
- CVE-2014-1249 : A buffer overflow existed in the handling of PSD images. This issue was addressed through improved bounds checking.
- CVE-2014-1250 : An out of bounds byte swapping issue existed in the handling of ‘ttfo’ elements. This issue was addressed through improved bounds checking.
- CVE-2014-1245 : A signedness issue existed in the handling of ‘stsz’ atoms. This issue was addressed through improved bounds checking.
- CVE-2011-3389 : There were known attacks on the confidentiality of SSL 3.0 and TLS 1.0 when a cipher suite used a block cipher in CBC mode. To address these issues for applications using Secure Transport, the 1-byte fragment mitigation was enabled by default for this configuration.
- OS X Mavericks 10.9.2 Update (859.7 MB)
- OS X Mavericks 10.9.2 Update (Combo) (859.7 MB)
- Security Update 2014-001 (Lion) (123.4 MB)
- Security Update 2014-001 (Mountain Lion) (115.8 MB)
- Security Update 2014-001 Server (Lion) (173.6 MB)