Apple releases macOS Monterey 12.6, iOS 15.7, and more; fixes zero-day vulns
Posted on
by
Jay Vrijenhoek and Joshua Long
![]()
On Monday, September 12, Apple released updates to all of its main operating systems. A few were major upgrades, namely iOS 16 and watchOS 9, as well as tvOS 16. Two “actively exploited” (i.e. zero-day, in-the-wild) vulnerabilities were fixed.
Let’s take a look at some of the security issues that these updates mitigate. We’ll also read between the lines, and hypothesize about which OS versions Apple may (and may not) update going forward.
In this article:
- macOS Monterey 12.6
- macOS Big Sur 11.7
- macOS Catalina: No security updates
- Safari 16
- iOS 16
- iOS 15.7 and iPadOS 15.7
- iOS 12: No security updates
- watchOS 9
- watchOS 8: No security updates (yet)
- tvOS 16
- HomePodOS 16
- Key takeaways
- How can I learn more?
macOS Monterey 12.6
Apple’s latest Mac operating system update is available for all supported Macs currently running macOS Monterey. According to Apple, “This update provides important security updates and is recommended for all users.”
Apple has identified eight CVEs (named security vulnerabilities) that impact this OS, as well as acknowledging that Identity Services’ security may be improved. Three of the eight are kernel vulnerabilities, one of which Apple says “may have been actively exploited,” meaning it’s an in-the-wild, zero-day vulnerability.
ATS
Impact: An app may be able to bypass Privacy preferences
Description: A logic issue was addressed with improved state management.
CVE-2022-32902: Mickey Jin (@patch1t)
iMovie
Impact: A user may be able to view sensitive user information
Description: This issue was addressed by enabling hardened runtime.
CVE-2022-32896: Wojciech Reguła (@_r3ggi)
Kernel
Impact: An app may be able to execute arbitrary code with kernel privileges
Description: The issue was addressed with improved memory handling.
CVE-2022-32911: Zweig of Kunlun Lab
Kernel
Impact: An app may be able to disclose kernel memory
Description: The issue was addressed with improved memory handling.
CVE-2022-32864: Linus Henze of Pinauten GmbH (pinauten.de)
Kernel
Impact: An application may be able to execute arbitrary code with kernel privileges. Apple is aware of a report that this issue may have been actively exploited.*
Description: The issue was addressed with improved bounds checks.
CVE-2022-32917: an anonymous researcher
Maps
Impact: An app may be able to read sensitive location information
Description: A logic issue was addressed with improved restrictions.
CVE-2022-32883: Ron Masas, breakpointhq.com
MediaLibrary
Impact: A user may be able to elevate privileges
Description: A memory corruption issue was addressed with improved input validation.
CVE-2022-32908: an anonymous researcher
PackageKit
Impact: An app may be able to gain elevated privileges
Description: A logic issue was addressed with improved state management.
CVE-2022-32900: Mickey Jin (@patch1t)
Identity Services
We would like to acknowledge Joshua Jones for their assistance.
*emphasis added
For the full list of security patches included in macOS Monterey 12.6 (at least those that Apple has disclosed so far), have a look here.
You can get this update by going to System Preferences > Software Update, where compatible Macs running macOS Mojave or newer will see the Monterey update appear. If your Mac is running macOS High Sierra or older, look for macOS Monterey in the App Store and download it from there.
macOS Big Sur 11.7
Simply listed as an update that “provides important security updates and is recommended for all users.” The same vulnerabilities fixed in Monterey 12.6 were also fixed for Big Sur. However, Big Sur 11.7 also includes two additional updates, one of which Apple says “may have been actively exploited.” This means that two in-the-wild, zero-day vulnerabilities were patched for Big Sur.
Contacts
Impact: An app may be able to bypass Privacy preferences
Description: This issue was addressed with improved checks.
CVE-2022-32854: Holger Fuhrmannek of Deutsche Telekom Security
Kernel
Impact: An application may be able to execute arbitrary code with kernel privileges. Apple is aware of a report that this issue may have been actively exploited.*
Description: An out-of-bounds write issue was addressed with improved bounds checking.
CVE-2022-32894: an anonymous researcher
*emphasis added
The kernel vulnerability was previously addressed for macOS Monterey in 12.5.1 on August 17. Apple left macOS Big Sur users vulnerable to this actively exploited, in-the-wild vulnerability for nearly a month after making the update available for macOS Monterey. Unfortunately, this kind of behavior isn’t uncommon of Apple. For this reason, it’s important to stay on the latest version of Apple operating systems whenever possible.
As for the contacts vulnerability, it has only been patched in macOS Big Sur 11.7, iOS 16, and iOS and iPadOS 15.7. It is unclear whether this vulnerability affects macOS Monterey. However, if it did, Apple would have presumably included it in the list of vulnerabilities addressed in macOS Monterey 12.6.
For the full list of security patches included in macOS Big Sur 11.7 (at least those that Apple has disclosed so far), have a look here.
If you have a Mac that maxes out at macOS Big Sur and cannot run macOS Monterey or later, you can get this update by going to System Preferences > Software Update. If your Mac is running macOS High Sierra or older, look for macOS Big Sur in the App Store and download it from there.
macOS Catalina: No security updates
Notably, macOS Catalina did not receive a single security update today—not even for Safari. Apple has likely terminated support for macOS Catalina in anticipation of the upcoming macOS Ventura release.
Although disappointing for some people whose Macs are stuck with Catalina, this is not entirely unexpected or unprecedented. Apple did much the same thing last year, ceasing security updates for macOS Mojave early, before macOS Monterey was yet available.
If you have an older Mac that can’t run macOS Monterey and you cannot afford a newer Mac, learn how to upgrade an unsupported Mac to the latest macOS.
How to Install macOS Monterey on Unsupported Macs, for Security Improvements
Safari 16
Available for macOS Monterey and macOS Big Sur, this update addresses at least four named security vulnerabilities. Three of them are WebKit vulnerabilities that could lead to either arbitrary code execution or UI spoofing. The fourth vulnerability is in Safari Extensions that could allow websites to track users using the technology. The short list of fixes can be seen here.
Safari 16 is available in System Preferences > Software Update for Macs running Monterey or Big Sur. It will appear once macOS 12.6 or 11.7 has been installed.
Interestingly, macOS Monterey 12.6 does not include the Safari update as it has in the past. Instead, Safari is available as a separate update. Presumably this is because Apple is beginning to transition Monterey to the “n minus 1” phase. Apple typically releases all applicable security updates for the current (n) major macOS release, and limited security updates for the two previous (n-1 and n-2) macOS versions.
iOS 16
This iOS update is packed with new features and enhancements. When it comes to security-related patches, details have only been released about eleven of them so far. The published details show the same fixes as those in iOS 15.7, although the page states, “Additional CVE entries to be added soon.”
Why Apple is holding back these details is unknown, but it may have something to do with the fact that iPadOS 16 won’t be released until October. Chances are, many of the same bugs and security issues addressed in iOS 16 will also be addressed in iPadOS 16 when it is released. Perhaps some of those mitigations may not be made available for iPadOS 15, which is currently the only non-beta OS supported on recent iPads.
The same “actively exploited” kernel vulnerability (CVE-2022-32917) that was mitigated in both macOS updates has also been addressed in iOS 16. Interestingly, Apple doesn’t specify that it’s aware of reports of the vulnerability being exploited for iOS 16. This may simply be because iOS 16 has been in beta until now.
If you’re curious, you can keep an eye on this page for future additions to the list of iOS 16.0 security fixes. We may update this article or discuss details about future additions, either here on The Mac Security Blog or on the Intego Mac Podcast.
Unfortunately, it may take up to 1–4 weeks for any new iOS or iPadOS version to roll out to customers (as discussed on the Intego Mac Podcast in episode 233), unless users pay attention to third-party Apple or security news sources like Intego’s blog or podcast, and manually check for new updates when they’re released.
iOS 15.7 and iPadOS 15.7
Apple says that this update is available for iPhone 6s and later, iPad Pro (all models), iPad Air 2 and later, iPad 5th generation and later, iPad mini 4 and later, and iPod touch (7th generation).
Interestingly, Apple is currently making iOS 15.7 the default upgrade path for iOS 16-compatible iPhones. The new iOS 16 is instead being offered as an optional alternative upgrade for now. This is similar to the initial rollout of iOS 15. We expect this to change in the near future, with iOS 16 becoming the only upgrade path for fully up-to-date versions of iOS 15, on iOS 16-compatible devices.
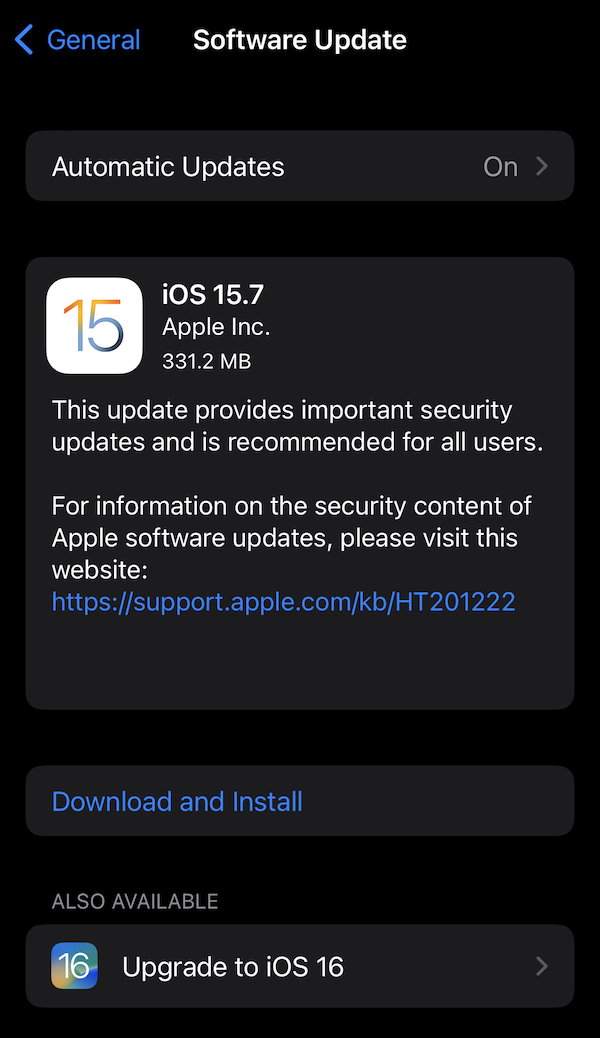
An iPhone screenshot showing iOS 15.7 as the default, with iOS 16 as an optional alternative upgrade. Expect iOS 16 to be the only option soon.
No non-security release notes are available yet for iOS 15.7 or iPadOS 15.7, suggesting the update may be strictly limited to security updates, with minimal, if any, non-security bug fixes or new features.
Apple addressed at least eleven named security-related issues, and two “additional recognitions,” in iOS and iPadOS 15.7. The same “actively exploited” kernel vulnerability (CVE-2022-32917) that was mitigated in both macOS updates and iOS 16 has also been addressed in iOS 15.7. The list of security issues Apple acknowledged as having been addressed can be found here.
To get your hands on this latest update, connect your device to your Mac and follow the update prompts. You can also download these updates over the air by going to Settings > General > Software Update on your device.
Given that Apple’s Studio Display runs a full version of iOS 15, it is not known whether iOS 15.7 will be released for the display as well, if it even needs it. It also remains to be seen whether the display’s firmware will soon be based on iOS 16 instead. For now, the current Apple Studio Display firmware version is 15.5, which was released in mid-May.
iOS 12: No security updates
Not surprisingly, iOS 12 did not receive a security update today.
We recently mentioned that it wasn’t clear whether old devices stuck on iOS 12 would continue to get security updates after the release of iOS 16. Apple never answered us, but the lack of iOS 12 updates today might be our answer.
Time will tell whether we’ll see any more security updates for iOS 12. Even if so, they would only be minimal updates to address in-the-wild vulnerabilities that are known to affect the ancient iOS version.
For the time being, at least, iOS 12 is presumed dead.
watchOS 9
Available for: Apple Watch Series 4 and later
Apple has not yet published any details about the security-related content of this major new watchOS version. Instead, Apple only says, “details available soon.” It likely fixes many of the same vulnerabilities addressed in today’s other updates.
As for why Apple is withholding the details, one can only speculate. Perhaps Apple doesn’t want to reveal details of any vulnerabilities that will be patched in the upcoming iPadOS 16 and macOS Ventura that also apply to watchOS 9. Or perhaps there may be a forthcoming watchOS 8 update that fixes some vulnerabilities addressed in watchOS 9.
watchOS 8: No security updates (yet)
The Apple Watch Series 3, which Apple was still selling in its online store until the Series 8 and Ultra models were announced on September 7, is incompatible with watchOS 9.
We presume that a watchOS 8 security update specifically for the Series 3 may be forthcoming. This could explain why Apple is withholding the list of watchOS 9’s security vulnerabilities for now.
Apple has not yet confirmed whether, or for how long, security updates will be made available for Apple Watch Series 3. Such a move would not be unprecedented, however. As recently as late 2020, Apple released simultaneous updates for two or three watchOS versions at a time, mainly to support older Apple Watch models.
tvOS 16
Available for: Apple TV 4K and Apple TV HD
As with watchOS 9, Apple remains tight-lipped about the security contents of this update, only stating that they will be “available soon.” It likely fixes many of the same vulnerabilities addressed in today’s other updates.
The new tvOS 16 supports the same hardware as tvOS 15, so it’s unclear why Apple would withhold the update’s details for now.
HomePodOS 16
Apple’s rarely-mentioned HomePodOS (also known as audioOS) for HomePod also received an update. Apple has never mentioned this operating system on its security updates page, so it is unclear whether any security issues were addressed in this week’s update.
HomePod updates are generally not urgent, and they are supposed to install automatically. However, if you would like to update your HomePod or HomePod mini’s operating system manually, you can go into the Home app on your iPhone or iPad, then tap the House icon > Home Settings > Software Update > temporarily disable (toggle off) Install Updates Automatically > then tap Install. After updating, remember to re-enable the Install Updates Automatically setting.
Key takeaways
Whenever an Apple update addresses an “actively exploited” security issue, it is important to install the update as soon as you can. Thus, you should definitely prioritize installing this week’s macOS Monterey, iOS, and iPadOS updates.
If you have a Mac running Big Sur that’s compatible with Monterey, you may wish to update to the new Big Sur version, and then as soon as practical, upgrade to macOS Monterey. Here’s why. Generally speaking, it is best to update to the latest Apple OS versions quickly for security reasons. For maximum security, one cannot rely on any minimal security patches Apple may release for previous OS versions.
Apple’s Poor Patching Policies Potentially Make Users’ Security and Privacy Precarious
Whenever you’re preparing to update iOS, iPadOS, or macOS, always back up your data before installing any updates. This gives you a restore point if something does not go as planned. We published a companion article today about how to prepare before upgrading your operating system.
See also our related article on checking your macOS backups:
How can I learn more?
 Each week on the Intego Mac Podcast, Intego’s Mac security experts discuss the latest Apple news, security and privacy stories, and offer practical advice on getting the most out of your Apple devices. Be sure to follow the podcast to make sure you don’t miss any episodes.
Each week on the Intego Mac Podcast, Intego’s Mac security experts discuss the latest Apple news, security and privacy stories, and offer practical advice on getting the most out of your Apple devices. Be sure to follow the podcast to make sure you don’t miss any episodes.
You can also subscribe to our e-mail newsletter and keep an eye here on The Mac Security Blog for the latest Apple security and privacy news. And don’t forget to follow Intego on your favorite social media channels: ![]()
![]()
![]()
![]()
![]()
![]()
![]()