Apple notarizes new Mac malware… again
Posted on
by
Joshua Long

For the second time in six weeks, Apple has been caught notarizing Mac malware.
Intego previously reported that Apple inadvertently notarized more than 40 malware samples in August.
This time, rather than the notarized malware belonging to the OSX/Shlayer and OSX/Bundlore families, the latest malware is from the OSX/MacOffers (aka MaxOfferDeal) family.
All of the half-dozen samples of Trojan disk image (.dmg) files, as well as the malware’s first-stage Trojan application, had a 0% detection rate on VirusTotal when they were first uploaded between October 6 and 13. Meanwhile, a sample of the second-stage malicious payload was only detected by 4 out of 60 antivirus engines on VirusTotal as of October 12.
The new malware uses a technique called steganography to hide its malicious payload within a separate JPEG image file, which is likely why the malware was able to slip past Apple’s notarization process.
Why is notarized malware noteworthy?
Mac software developers submit apps to the Apple notary service, and Apple runs automated scans to check for malicious content. If the software appears to be malware-free, then Apple automatically notarizes it.
When Apple notarizes an app, it’s much easier for users to run the app on macOS Mojave, macOS Catalina, and the upcoming macOS Big Sur. (One can double-click on a notarized app to open it. However, one must control-click or right-click to open non-notarized apps.)
Therefore, there’s a significantly higher chance that victims will install Trojan horse malware that has sneaked through Apple’s notarization process undetected.
The discovery of this malware marks the second time that Apple is known to have notarized Mac malware samples; the first known incident was discovered several weeks earlier, in late August.
How does this malware use steganography?
Steganography is the ancient technique of stealthily hiding secret information inside something in plain sight. In this case, the application bundle found on the disk image contains a JPEG graphic file that seems innocuous to the naked eye. However, the JPEG contains a Base64-encoded .zip archive file that contains another malicious app.
A JPEG image file within the app bundle steganographically hides a malicious payload.
We’ve observed steganography used before in Mac malware. Notable examples include the VeryMal Shlayer campaign in 2019 and the MacDefender fake antivirus family in 2011.
How was the malware distributed?
This latest malware threat has been observed in the wild.
Mac malware researcher Matt Muir discovered the first sample while hunting for malware amongst cracked software.
“Cracked software” refers to software that has been modified to remove registration requirements or other restrictions that limit software functionality. Malware makers sometimes try to exploit the naïveté of people who seek to obtain commercial software without paying for it.
See also:
As is typical of most Mac malware these days, the latest OSX/MacOffers variant disguises itself as an Adobe Flash Player installer.
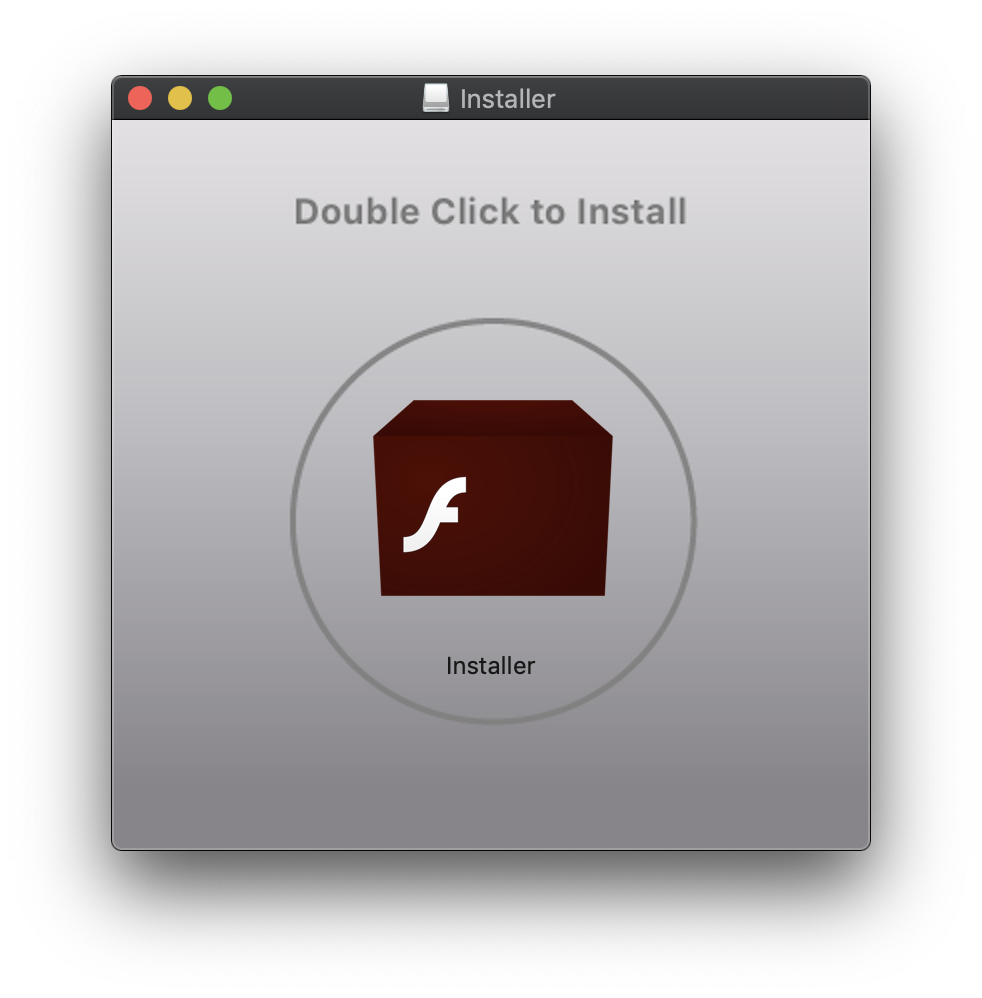
OSX/MacOffers arrives as a Flash Player-mimicking Trojan horse.
In 2020, nobody should believe any site that prompts them to download or update Flash. Adobe plans to discontinue security updates for the real Flash Player at the end of this year. Most browsers have already dropped support for Flash Player or disable it by default. Unfortunately, most end users are probably unaware of these facts, given that malware makers seem to still find success with fake Flash installers.
Until sometime within the next couple months, Google Chrome will continue to have its own built-in version of Flash that updates automatically along with the browser itself, so if you need to access sites with Flash content, you can still use Chrome for now. Never install Flash Player if you’re prompted to; it’s a telltale sign of malware.
See also:
Adobe Flash Player is dead, yet 10% of Macs are infected with fake Flash malware
How can one stay safe from notarized malware?
Notarized Mac malware will very likely continue to be a problem, as malware makers try old and new techniques to attempt to circumvent Apple’s automated malware checks.
In this case, Apple revoked the malware developer’s known certificate on or around October 12. This should help prevent new infections of the samples that have been found so far.
However, this certificate revocation doesn’t necessarily help Macs that have already become infected. It also doesn’t prevent the malware maker from registering new Apple Developer IDs and attempting to get new malware samples notarized. Furthermore, most Mac users aren’t using a trusted antivirus with real-time scanning, which often blocks new malware threats that Apple hasn’t mitigated.
 Thankfully, we’ve got you covered. Intego VirusBarrier X9, included with Intego’s Mac Premium Bundle X9, can protect against, detect, and eliminate this malware.
Thankfully, we’ve got you covered. Intego VirusBarrier X9, included with Intego’s Mac Premium Bundle X9, can protect against, detect, and eliminate this malware.
Note: Customers running VirusBarrier X8, X7, or X6 on older versions of Mac OS X are also protected. It is best to upgrade to the latest version of VirusBarrier and macOS if possible to ensure your Mac gets all the latest security updates from Apple.
Indicators of compromise (IoCs)
Following are some specific ways to identify whether a Mac may have been infected by this OSX/MacOffers campaign.
This malware has been observed using the generic-sounding filename “Player.dmg” for the initial infection phase. The existence of a file with that exact name in the ~/Downloads folder may be a possible sign of infection.
The malicious installer app uses a Bundle ID that does not follow expected patterns. Normally an app’s bundle identifier uses reverse domain name notation, for example com.apple.Safari or org.mozilla.firefox. However, this malware’s Bundle ID is:
someorgident.notarized
The copyright info for the first-stage Trojan horse identifies the company as “someorg.”
Apple has since revoked the Developer ID that was used for signing and requesting notarization of this malware. The developer name and Team ID of the revoked dev account is:
Maria Robinson (4DNKNBX6DS)
The following SHA-256 file hashes belong to known OSX/MacOffers files associated with this malware campaign. All of these samples are available to registered VirusTotal users with malware researcher accounts.
DMG disk image files: 10495e1bf0f7fc895c832532feab47311f9084a428454793e3160e644c385bdd 37b833b0b7a19723b5532e71352b9d6699b7be8086acf4ea225f9d639566a613 4e24d9f28668780c58082b605769e774e881f0dff8863e6ec920352e6bcc219d 651d16f01892b51817986689d2ff432e354b722d2e67fda2cfea3aee05fa9fcd 9c540d3cd6858d9e27c9e94e8d6d0528828e3e56c9153f08958fa8e413c31c51 e4b9a43e114aae4a706f757d190dc4be5560ef643bcfb9fd37290db8c8fb9fb0 Mach-O first-stage executable: 64ad034cc793d6cad9a0e0d0ffe3dc840169cd0dbc164cd2188bb2f6684a6de9 Mach-O second-stage payload: 9fefc4d588b6e9f667a77eb9cd0c5e86ac0b6083845e84a1dcba1791211ef419
The following domain has been observed distributing this malware, and is also found in a hidden .Info.plist file on the mounted disk images:
www.jurisdiction[.]world
Any recent network traffic to or from this domain should be considered a possible sign of an infection.
How can I learn more?
 We discussed the latest Apple-notarized malware (as well as two malware families recently ported to Mac) on episode 158 of the Intego Mac Podcast. Be sure to subscribe to make sure you don’t miss any episodes. You’ll also want to subscribe to our e-mail newsletter and keep an eye here on The Mac Security Blog for the latest Apple security and privacy news.
We discussed the latest Apple-notarized malware (as well as two malware families recently ported to Mac) on episode 158 of the Intego Mac Podcast. Be sure to subscribe to make sure you don’t miss any episodes. You’ll also want to subscribe to our e-mail newsletter and keep an eye here on The Mac Security Blog for the latest Apple security and privacy news.
You can also follow Intego on your favorite social and media channels: Facebook, Instagram, Twitter, and YouTube (click the 🔔 to get notified about new videos).
Acknowledgements
In addition to Intego’s malware analysis team, the author would like to thank Matt Muir for sharing details with us about his malware discovery, and Thomas Reed for additional contributions to this research.