Apple notarizes dozens of Mac malware samples
Posted on
by
Joshua Long

From mid-to-late August, Apple has inadvertently enabled dozens of malware samples to run more easily on Macs.
The malware samples are related to the OSX/Bundlore and OSX/Shlayer families. Intego VirusBarrier customers are protected from these threats.
Let’s explore what happened, and why it’s important to not rely entirely on Apple’s attempts to protect Mac users from malware.
What is notarization?
In 2019 Apple debuted a software notarization process. A developer submits their app to the Apple notary service, and Apple runs automated scans to check for malicious content. If the software appears to be clean and legitimate, Apple will notarize it.
After Apple notarizes an app, it’s much easier for users to run the app on macOS Mojave, macOS Catalina, and future versions including macOS Big Sur.
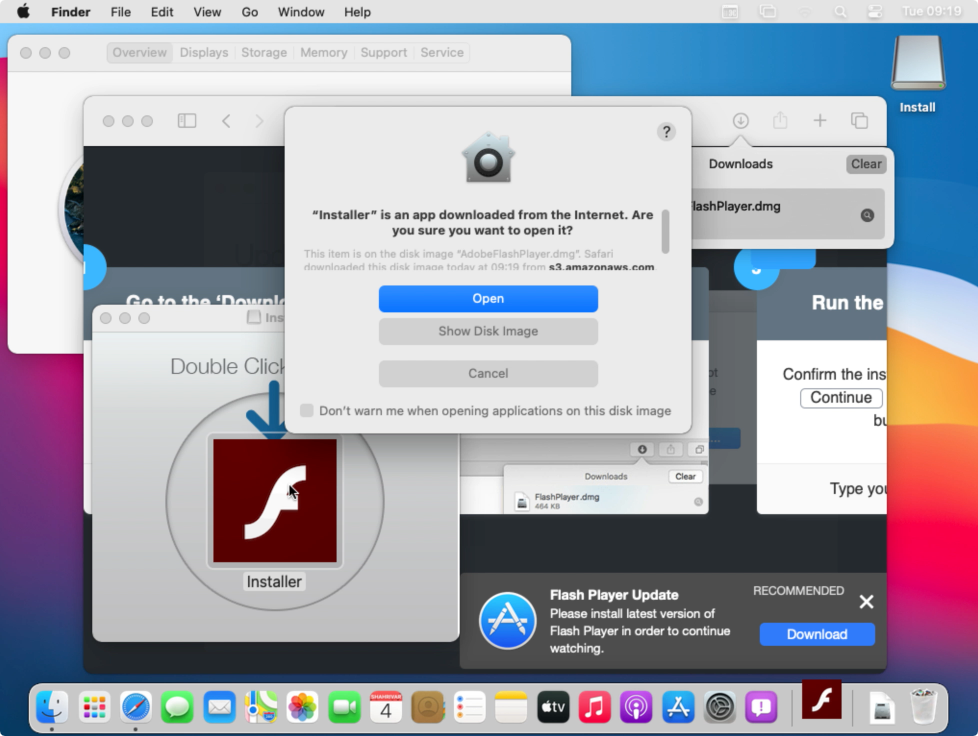
Notarized apps, like this malware, are blessed with an Open button when double-clicked for the first time. Image: Wardle
Notably, notarization is not as comprehensive as the App Review process that Apple employs before accepting apps into its App Stores. App Review employs both automated and manual human reviews of software to ensure compliance with Apple’s policies.
Why did Apple notarize malware?
Presumably, Apple’s automated notarization process failed to correctly determine that the malware submissions were malicious.
At least three different Apple Developer IDs were used to code-sign more than 40 unique malware samples associated with this campaign.
How was the malware distributed?
The malware distributors registered the domain homebrew[.]sh, hoping to ensnare victims looking for Homebrew, legitimate Mac software which has its actual homepage at brew.sh. (This is known as a typosquatting attack.)
Instead of reaching the Homebrew homepage, victims were taken to a page with a fake Adobe Flash Player updater—a Trojan horse that installs adware. Mac users should avoid downloading or installing anything that claims to be Flash Player.
See also:
Adobe Flash Player is dead, yet 10% of Macs are infected with fake Flash malware
Why are Apple’s protection attempts insufficient?
Apple employs a number of technologies and procedures to attempt to thwart Mac malware, including XProtect, Gatekeeper, notarization, and more.
And yet, time and time again, in spite of Apple’s best efforts, malware makers continue to find ways to circumvent these measures and infect Macs.
A significant percentage of Mac users don’t bother to use third-party endpoint protection software, such as realtime anti-malware protection or outbound firewalls. Many users probably have heard the myth that “Macs don’t get malware,” or perhaps they’ve heard of XProtect or other Apple technologies and assume that they will be protected.
Because of this, malware makers generally need to merely bypass Apple’s built-in protection measures, which unfortunately is not very difficult to do.
We recommend taking a layered approach to securing your Mac, and not relying alone on Apple’s often ineffectual attempts to protect Mac users.
See also:
How can one stay safe from this Apple-notarized malware?
Apple eventually revoked the malware developer’s known certificates, which should help prevent new infections of the known 40+ samples. However, this certificate revocation doesn’t necessarily help Macs that have already become infected. It also doesn’t prevent the malware maker from registering new Apple Developer IDs and attempting to get new malware samples notarized.
 Thankfully, we’ve got you covered. Intego VirusBarrier X9, included with Intego’s Mac Premium Bundle X9, can protect against, detect, and eliminate this malware.
Thankfully, we’ve got you covered. Intego VirusBarrier X9, included with Intego’s Mac Premium Bundle X9, can protect against, detect, and eliminate this malware.
Note: Customers running VirusBarrier X8, X7, or X6 on older versions of Mac OS X are also protected. It is best to upgrade to the latest version of macOS if possible to ensure your Mac gets all the latest security updates from Apple.
How can I learn more?
For a more technical analysis of this malware, you can refer to Patrick Wardle’s write-up.
We discussed the Apple-notarized malware on episode 151 of the Intego Mac Podcast—be sure to subscribe to make sure you don’t miss any episodes. You’ll also want to subscribe to our e-mail newsletter and keep an eye here on The Mac Security Blog for the latest Apple security and privacy news.
You can also follow Intego on your favorite social and media channels: Facebook, Instagram, Twitter, and YouTube (click the 🔔 to get notified about new videos).