VeryMal Mac attack hides data within a picture
Posted on
by
Joshua Long
 A recent malware distribution campaign dubbed “VeryMal” leverages an ancient technique called steganography—the hiding of secret information in plain sight—to distribute Mac malware.
A recent malware distribution campaign dubbed “VeryMal” leverages an ancient technique called steganography—the hiding of secret information in plain sight—to distribute Mac malware.
The VeryMal campaign was caught distributing OSX/Shlayer, which was originally discovered by Intego researchers one year ago.
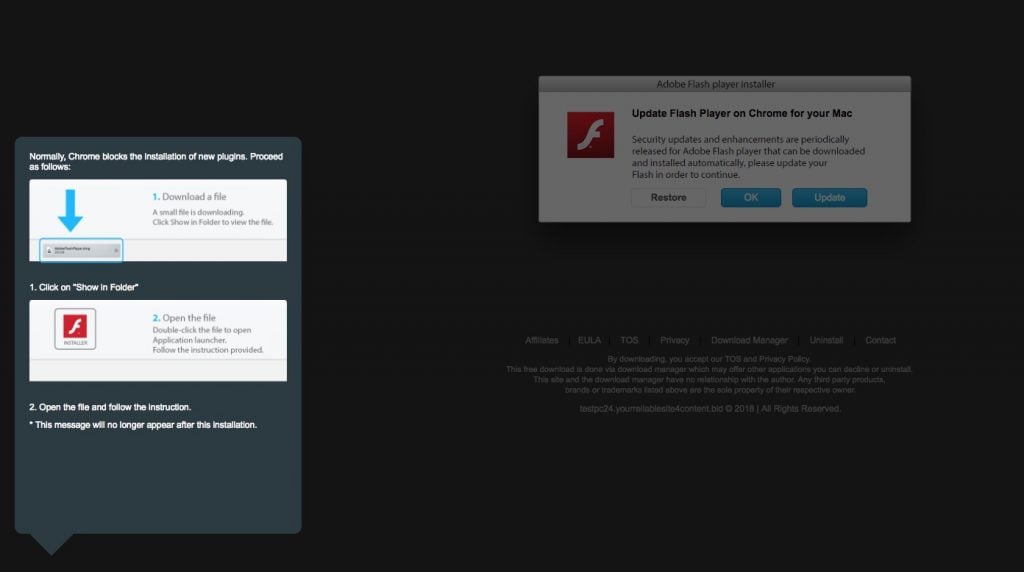
OSX/Shlayer malware still masquerades as a fake Flash Player.
What makes this malware campaign unique?
Although the concept of steganography has been around for hundreds of years, it is not something we see in a lot of Mac malware campaigns.
The VeryMal campaign used some cleverly crafted JavaScript code to look for secret information stored within a seemingly innocuous JPEG image file. The hidden data tells the site where to go to find the malware.
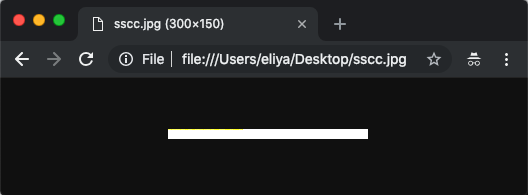
To the naked eye, the image looks like a plain, white rectangle. Credit: Stein
Why go to all this trouble? In theory, using steganography or other obfuscation techniques makes it more difficult for endpoint protection and network monitoring software to determine that something suspicious might be happening.
In practice, however, this tricky tactic does not prevent well-designed antivirus software like VirusBarrier X9 from keeping users safe.
Is my Mac infected?
Users of Intego VirusBarrier X9 (part of Intego’s Mac Premium Bundle X9 suite) or Flextivity were already protected from this threat before the discovery of the VeryMal campaign.
If you aren’t a VirusBarrier X9 user and you think you might have downloaded a fake Flash Player, you can scan your Mac with VirusBarrier Scanner (available for free on the Mac App Store) to check for any infections. After you scan your Mac, your best bet to prevent future infections is to get VirusBarrier X9, which includes real-time scanning functionality—a critical feature to block malware before it can harm your Mac.
How sysadmins can find potentially infected Macs
If you’re a systems administrator and want to check for potentially infected Macs on your network, you can check whether any Macs phoned home to one of the following sites (remove the space before each .com):
veryield-malyst .com s.ad-pixel .com/sscc.jpg
Any Mac that made contact with those sites around mid-January 2019 may be infected with Shlayer malware.
How can I learn more?
For more technical details about the malware, you can read Eliya Stein’s write-up.
 Each week, we talk about the latest Apple security news on the Intego Mac Podcast, so be sure to subscribe to make sure you don’t miss any episodes. You’ll also want to subscribe to our e-mail newsletter and keep an eye here on The Mac Security Blog for updates.
Each week, we talk about the latest Apple security news on the Intego Mac Podcast, so be sure to subscribe to make sure you don’t miss any episodes. You’ll also want to subscribe to our e-mail newsletter and keep an eye here on The Mac Security Blog for updates.