Ad-injecting Mac malware rediscovered: SearchPageInjector/SearchAwesome
Posted on
by
Joshua Long
Most people assume that there’s little, if any, Mac malware out there in the wild. Unfortunately, that notion is merely wishful thinking.
Malware analysts—even those focused on Mac malware—process so many malware samples that not every new piece of malware necessarily gets its own dedicated article or press release.
Such was the case with OSX/SearchPageInjector, Mac malware that Intego has been detecting since January 2018. OSX/SearchPageInjector recently came back on our radar after Thomas Reed wrote up a piece about it under the name OSX.SearchAwesome.
Since it has been in the news recently, let’s take a look at what this malware does and how to avoid it.
What Is OSX/SearchPageInjector?
OSX/SearchPageInjector is Mac malware designed to inject remotely hosted JavaScript code into every Web page the victim visits.
The JavaScript code has been observed to inject advertisements, but it could also potentially be used for cryptojacking—i.e. hijacking the Mac’s processing power to mine cryptocurrency on behalf of the attacker; see our audio podcast and our YouTube video on cryptojacking—or more sinister purposes such as stealing usernames and passwords.
OSX/SearchPageInjector makes use of open-source man-in-the-middle proxy software to inject the attacker’s JavaScript code into all Web sites—even those delivered over HTTPS, the more secure HTTP alternative that’s used by most popular Web sites.
How Do Macs Get Infected With OSX/SearchPageInjector?
This malware comes as a second-stage infection after a user downloads a supposedly “cracked” version of an app from a torrent.
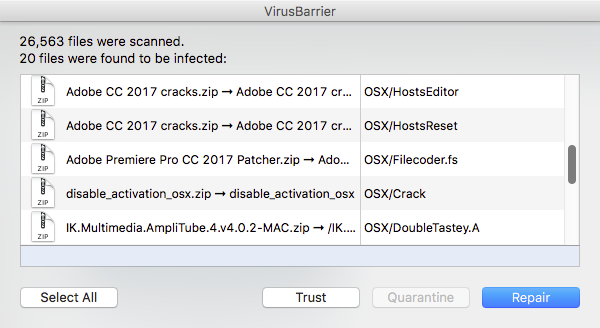 Apps downloaded from torrents often contain malware.
Apps downloaded from torrents often contain malware.
Thus, to avoid this particular infection, users simply need to avoid the temptation to download illegal copies of software.
How Can I Clean an Infected Mac?
Intego VirusBarrier has been detecting and eradicating OSX/SearchPageInjector since January 2018.
If the malware has been removed from your computer and you know you don’t use the open-source software mitmproxy, then you’ll also want to open the Keychain Access app (found in the /Applications/Utilities folder) and search for and delete the root certificate authority named mitmproxy.
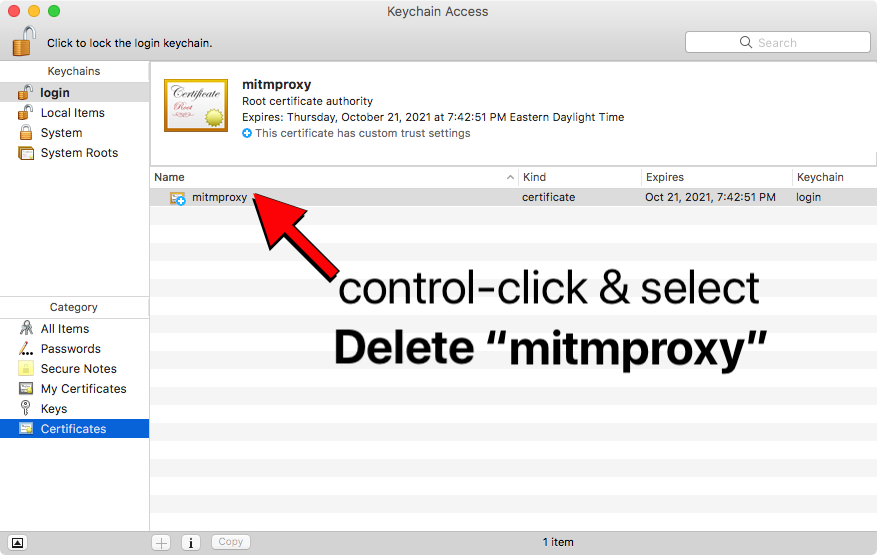 If you didn’t install mitmproxy, delete its root CA in Keychain Access. Screenshot: Reed
If you didn’t install mitmproxy, delete its root CA in Keychain Access. Screenshot: Reed
Where Can I Learn More?
We briefly discussed OSX/SearchPageInjector on the November 2 edition of the Intego Mac Podcast; be sure to subscribe to make sure you don’t miss future episodes!
For additional technical details about OSX/SearchPageInjector, you can refer to Reed’s write-up.